HIPAA Compliance Checklist for 2025

Picture this: an employee logs in once in the morning and gains instant access to 25 business-critical SaaS apps. That’s the power of Single Sign-On (SSO) - fast, seamless, and frictionless.
But here’s the catch: if that single credential is compromised, attackers get the keys to your entire kingdom.
According to the Verizon DBIR 2023, 79% of breaches involve stolen credentials, highlighting the critical need for strong access controls. A single compromised SSO token can bypass multiple layers of security, putting your entire system at risk. Moreover, shadow IT apps connected to SSO often go unnoticed, operating outside of your organization’s official oversight, until it’s too late, leaving your data and systems vulnerable to exploitation.
As enterprises rapidly scale their SaaS ecosystems, SSO security risks are becoming one of the most overlooked vulnerabilities in cybersecurity programs. This blog breaks down the top SSO security challenges, explains why they matter, and shares best practices to protect your identity infrastructure.
TL;DR
- Single Sign-On (SSO) simplifies authentication but creates a single point of failure if not secured.
- Common SSO security risks include weak authentication, token theft, poor RBAC, and Shadow IT.
- Implementing MFA, modern identity standards (SAML/OIDC), granular access policies, and automated offboarding can mitigate threats.
- SaaS management platforms like CloudEagle enhance visibility, detect anomalies, and automate access governance for stronger SSO security.
- Regular audits and real-time monitoring are essential to catch issues early and maintain compliance.
1. What is SSO Security?
Single Sign-On (SSO) security refers to the strategies, protocols, and controls that secure centralized authentication systems. Instead of managing multiple passwords, users log in once to access authorized applications through a trusted Identity Provider (IdP).
From an IT perspective, SSO centralizes identity management. But it also creates a single point of failure — if an attacker compromises SSO, they can move laterally across your environment undetected.
Examples of SSO:
- Corporate SSO via Okta, Azure AD, or Ping Identity
- Google Workspace SSO for SaaS apps
- Internal SSO portals for cloud apps and on-prem services
2. Why SSO Security Matters for Modern Enterprises
Why is SSO important for today’s enterprises? Beyond user convenience, SSO provides centralized control, better compliance, and operational efficiency. But if not secured, it can become the perfect breach vector.
Key reasons SSO security matters:
- Centralized risk: One compromise = many systems exposed.
- Regulatory pressure: Frameworks like SOC 2, ISO 27001, and GDPR require strict access control.
- Hybrid work: Remote employees access dozens of apps daily, increasing the attack surface.
- Rising attacks: Phishing and token theft are surging, targeting IdPs directly.
In short, SSO security is no longer optional - it’s foundational to enterprise cybersecurity.
3. Common SSO Security Risks You Can’t Ignore
A. Weak Authentication Protocols
Using outdated or single-factor authentication (password only) leaves SSO vulnerable to credential stuffing and brute force attacks. Without MFA, one weak password can compromise dozens of apps. MFA is mandated by many compliance frameworks (PCI-DSS, HIPAA), underscoring its role in regulatory adherence.
B. Overreliance on a Single Point of Failure
SSO centralizes access, but if your IdP goes down or is breached, it can lock out users or open floodgates to attackers.
C. Token Theft or Session Hijacking
Attackers can steal SSO tokens through phishing, browser extensions, or malware, gaining long-term access without credentials. Session hijacking is notoriously hard to detect.
D. Poor Identity Federation Practices
Misconfigured SAML or OIDC connections can lead to serious security risks, like attackers impersonating users through forged authentication tokens. For example, a SAML misconfiguration could allow unauthorized access, bypassing security layers. Federation issues are especially risky in multi-cloud environments, where inconsistent protocols can create vulnerabilities.
E. Inadequate Role-Based Access Controls (RBAC)
SSO doesn’t enforce least privilege by default. If RBAC is too broad, users may get unnecessary access, amplifying insider threat risks.
F. Shadow IT & Unauthorized App Access
Employees often connect unauthorized SaaS apps to SSO without IT’s knowledge. These unmanaged apps can lack MFA, monitoring, or encryption — creating dangerous visibility gaps.
4. Challenges in SSO Implementation
A. Legacy System Integration Issues
Many legacy systems lack modern identity standards, making them difficult to integrate with SSO solutions. These older apps often require complex workarounds, which can introduce vulnerabilities. For instance, outdated authentication protocols may allow security gaps, weakening the overall integrity of the SSO infrastructure.
B. Lack of User Training & Awareness
SSO systems are only as strong as the users who interact with them. If users aren't educated about the risks of phishing attacks or the dangers of password reuse, even the most advanced SSO systems can be compromised. Cultivating a strong security culture, where users understand the importance of secure login practices, is crucial to the success of any SSO deployment.
C. Compatibility Across Cloud Environments
In multi-cloud environments, ensuring seamless SSO across different SaaS platforms can be challenging due to varying protocol support. For example, one cloud provider may support SAML, while another supports OIDC. Misconfigurations between these protocols can lead to access issues or gaps in security, leaving sensitive data exposed.
D. Limited Visibility into User Behavior
Traditional SSO solutions often lack comprehensive user behavior analytics. Without the ability to detect anomalies such as impossible travel (e.g., logging in from two locations simultaneously) or odd login hours, security teams may miss signs of a breach. Enhancing SSO with behavioral insights can help identify unusual activities, offering early detection of potential threats.
5. Best Practices to Strengthen SSO Security
A. Enforce Multi-Factor Authentication (MFA)
MFA is a critical layer of defense that enhances the security of your SSO setup. By requiring users to verify their identity through multiple methods such as a password combined with a fingerprint or a time-sensitive code, MFA significantly reduces the risk of account compromise. This additional step is especially important for protecting high-value accounts or accessing sensitive applications.
B. Regularly Audit SSO Logs and Access Patterns
Constant monitoring of SSO logs is essential for identifying suspicious activity. Look for signs of failed login attempts, unusual access times, or logins from unfamiliar devices or IP addresses. Conducting regular audits of access patterns not only helps in detecting and responding to potential threats quickly but also ensures your organization meets compliance requirements for logging and access management.
C. Configure Granular Access Policies
Implementing granular access controls is key to securing your SSO system. Use conditional access policies based on factors like IP restrictions, device compliance, or geolocation to protect sensitive applications. This ensures that only authorized users can access certain systems based on predefined conditions, further tightening the security perimeter.
D. Apply the Least Privilege Principle
The least privilege principle dictates that users should only have access to the resources they need to perform their job functions. By combining SSO with Role-Based Access Control (RBAC) and periodic access reviews, you can prevent privilege creep, where users accumulate unnecessary access rights over time. Regularly reviewing and adjusting access levels helps ensure users are only granted the minimum permissions necessary for their roles.
E. Use Modern Identity Standards (SAML, OIDC, SCIM)
Adopting modern identity standards like SAML, OIDC, and SCIM is crucial for maintaining secure, scalable, and efficient SSO environments. These protocols offer robust encryption, token management, and provisioning capabilities that older, less secure authentication methods lack. By moving away from outdated authentication systems, you ensure that your SSO setup is better equipped to handle current cybersecurity threats.
F. Automate Offboarding for Departed Users
Leaving user accounts active after an employee departs can create a significant security vulnerability. Automating the offboarding process via protocols like SCIM or integrating SaaS management tools can ensure that user accounts are promptly deprovisioned, eliminating the risk of unauthorized access. Regularly updating user access rights and automating offboarding ensures no account is overlooked and minimizes attack surfaces.
6. Tools to Monitor and Mitigate SSO Security Risks
A. Real-Time Threat Detection Platforms
Tools like Microsoft Defender for Identity and Okta ThreatInsight use AI to detect anomalies and stop suspicious logins in real time.
B. SaaS Management Platforms like CloudEagle
CloudEagle.ai adds governance and visibility on top of your SSO. It integrates with 500+ apps, detects Shadow IT, enforces granular access, and automates reviews.
C. Identity & Access Governance Tools
IGA solutions like SailPoint and Saviynt add periodic reviews, SoD checks, and compliance workflows to strengthen SSO security posture.
7. How CloudEagle.ai Enhances SSO Security
Many enterprises already use strong Identity Providers (IdPs) like Okta, Azure AD, or Ping Identity to enable Single Sign-On. But on their own, these platforms often lack deep SaaS visibility, policy automation, and identity governance controls needed to fully secure a modern SaaS ecosystem.
CloudEagle.ai bridges this gap.
It doesn’t replace your existing SSO or IdP stack - it elevates it with real-time monitoring, automated access governance, and Shadow IT detection. By layering governance on top of authentication, CloudEagle.ai turns SSO from a single point of risk into a central pillar of security and compliance.
A. Detect and Prevent Unauthorized Access
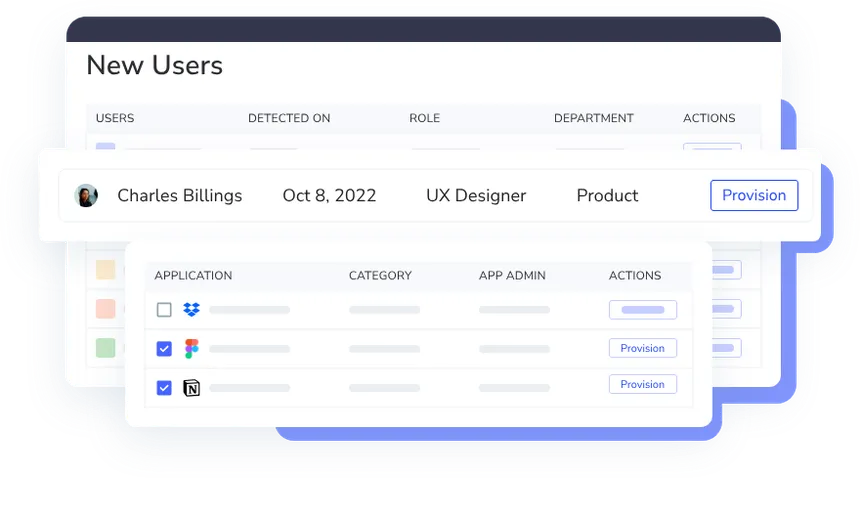
One of the biggest SSO security risks is unauthorized access that goes unnoticed. CloudEagle.ai integrates directly with your SSO and IdP to continuously monitor logins, session activity, and account usage across all connected SaaS and AI apps.
- Detects anomalies in real time — flag unusual login locations, time zones, or device fingerprints.
- Identify inactive or orphaned accounts that still have access through SSO.
- Leverage AI-driven alerts to surface suspicious patterns before they escalate into incidents.
By giving IT and Security teams a unified dashboard, CloudEagle.ai ensures no login or token misuse slips through the cracks.
B. Discover Shadow IT and Unused SaaS Accounts
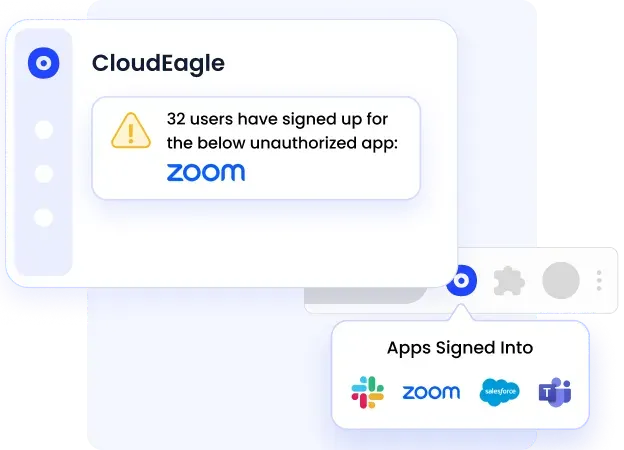
Shadow IT bypasses corporate security controls like MFA and RBAC, creating blind spots that enable data theft and malware infections.
Even with SSO in place, employees often connect unauthorized tools to their corporate identity without IT’s knowledge. These Shadow IT apps bypass formal onboarding, lack MFA enforcement, and often store sensitive data — creating significant compliance and security blind spots.
CloudEagle continuously scans your environment to:
- Identify unmanaged apps connected to SSO that aren’t part of your sanctioned SaaS stack.
- Detect dormant or unused licenses, surfacing waste and reducing the attack surface.
- Map Shadow IT tools back to departments or users for clean remediation.
This proactive discovery tightens your SSO security perimeter, eliminates blind spots, and helps organizations regain control over their expanding SaaS ecosystems.
C. Automate Access Reviews and Policy Enforcement
Periodic access reviews are critical for compliance frameworks like SOC 2, ISO 27001, and GDPR. However, manual reviews are slow, error-prone, and often skipped.
CloudEagle automates this entire process by:
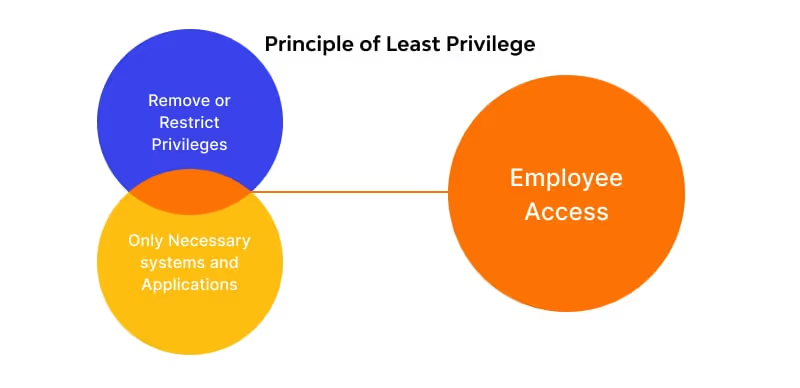
- Scheduling automated, audit-ready access reviews for critical apps.
- Enforcing least privilege policies across roles and departments.
- Automatically notifying app owners and managers to approve or revoke access.
- Generating centralized reports for auditors and compliance teams.
This automation drastically reduces administrative overhead while ensuring access is always accurate, current, and compliant, directly strengthening SSO security governance.
D. Integrate Seamlessly with Your IdP & SSO Stack
Whether you use Okta, Azure AD, Ping Identity, or other IdPs, CloudEagle integrates natively to enhance your existing workflows. There’s no need to rip and replace - instead, CloudEagle extends your IdP’s security capabilities through its 500+ direct SaaS integrations and policy orchestration engine.
A Quick Walkthrough of CloudEagle's Integration Library
With CloudEagle, IT and Security teams can:
- Apply consistent access governance across all connected SaaS apps, not just the ones managed by the IdP.
- Synchronize policies and automate deprovisioning across complex environments.
- Gain a single pane of glass for SSO visibility, identity governance, and SaaS usage insights.
This tight integration means your SSO stack becomes smarter, safer, and fully auditable without disrupting existing infrastructure.
8. Conclusion: Secure SSO or Risk Everything
SSO isn’t inherently risky; poorly secured SSO is.
When properly implemented with MFA, modern identity standards, and governance layers, SSO enhances security and efficiency. But if overlooked, it becomes a single point of catastrophic failure.
Platforms like CloudEagle.ai turn SSO from a vulnerability into a strength by providing granular access control and integrating multi-factor authentication (MFA). CloudEagle.ai ensures secure access with real-time SSO log audits and access pattern insights, quickly identifying suspicious activity.
It automates user offboarding with SCIM integration, ensuring immediate access revocation. By leveraging modern identity standards like SAML and OIDC, CloudEagle.ai enhances encryption and token management, offering a seamless and secure SSO experience across your SaaS ecosystem.
Ready to secure your SSO stack? Schedule a demo today to discover how CloudEagle can help your IT, Security, and Procurement teams protect access at scale.
Frequently Asked Questions
1. What does SSO mean in security?
SSO allows users to access multiple applications with one set of credentials via a trusted identity provider.
2. What are the disadvantages of SSO?
A single compromised SSO account can grant attackers wide access. Downtime can affect all connected apps simultaneously.
3. What are the security risks of concurrent login?
Concurrent sessions make token theft easier and increase the difficulty of monitoring suspicious activity.
4. What is SSO protected?
An SSO-protected resource requires centralized authentication before granting access.
5. What is SSO and SSL?
SSO handles authentication; SSL encrypts the communication channel between the user and the server.

%201.svg)








.avif)




.avif)
.avif)




.png)









