HIPAA Compliance Checklist for 2025

Today, enterprises use hundreds of SaaS apps, cloud tools, and remote accounts, making it crucial for IT and security teams to regularly check who has access and why.
According to CloudEagle.ai's IGA report, 95% of organizations rely on manual access reviews.
The manual access review process is becoming slow and prone to mistakes. This is where user access review tools help. These tools simplify the process by connecting with Identity Providers (IDPs) like Okta, Azure AD, and Google Workspace, making the review faster and more accurate.
Let’s explore how these tools integrate with IDPs, what features to look for, and how to use a user access review checklist to stay organized.
TL;DR
- Manual access reviews are inefficient and error-prone, especially with many SaaS apps in use.
- User access review tools automate the process by integrating with IDPs like Okta, Azure AD, and Google Workspace.
- These tools provide real-time access to insights, ensuring accurate and up-to-date information.
- They simplify compliance with standards like SOC 2 and ISO 27001 by generating audit-ready reports.
- Automating reviews reduces security risks, saves time, and improves overall access management.
Why User Access Reviews Matter?
User access reviews are essential for maintaining security, compliance, and operational efficiency in today’s fast-paced digital world.
Here’s why they should be a priority:
1. Security Risks: Without regular reviews, employees can gain unnecessary privileges over time, known as privilege creep. This increases the risk of unauthorized access and potential data breaches. Regular reviews help identify and remove excessive access, keeping your data secure.
2. Compliance Requirements: Many industries must comply with standards like SOC2, ISO 27001, GDPR, and HIPAA. Regular access reviews ensure that only authorized personnel have access to sensitive information, helping you stay compliant and avoid penalties.
3. Managing Growing Complexity: As businesses adopt more SaaS tools and software, it becomes harder to track who has access to what. Regular reviews help streamline the process, keeping access aligned with business needs and up to date.
4. Preventing Insider Threats: Some of the biggest security risks come from insiders who already have access. Regular reviews help spot discrepancies and prevent both intentional and unintentional insider threats.
5. Streamlining Onboarding & Offboarding: When employees join or leave the company, access needs to be quickly granted or revoked. Regular access reviews ensure new hires get the right permissions and former employees lose access immediately.
6. Audit-Ready Evidence: Up-to-date access reviews create a clear audit trail, making it easier to demonstrate compliance and show that your organization follows best practices during internal and external audits.
7. Reducing Human Error: Manual processes can lead to mistakes, such as granting excessive access or missing inactive accounts. Automating access reviews reduces human error and enhances security and efficiency.
What Are the Limitations of IDPs for Access Reviews?
Identity Providers help manage login and provisioning. However, they are not built to support the full user access review process. If teams rely only on an IDP, they can miss key compliance needs, lose visibility, and face governance risks, especially when managing many SaaS apps.
Here are the most common limitations of IDPs:
1. Only Cover Apps Behind SSO
IDPs manage access only for apps integrated through Single Sign-On (SSO). Many SaaS tools, especially free-tier or departmental apps, aren’t connected to the IDP. As a result, user access review tools need to fill the gap by discovering and monitoring off-SSO applications.
2. No Visibility into Direct-to-App Logins, Shadow IT, or Free-Tier Tools
Shadow IT, unauthorized or unapproved apps, remains one of the biggest blind spots for IDPs. They can’t detect direct logins or personal account usage, meaning risky access often goes unnoticed. User access review software adds visibility into these unmanaged environments to reduce security and compliance risks.
3. Lack of Feature-Level or Usage-Based Access Insights
While IDPs track who has access, they don’t show how that access is being used. They lack insights into feature-level permissions, activity patterns, or license utilization. Advanced user access review tools integrate usage data, helping reviewers make context-aware decisions during audits.
4. No Built-In Workflows for Periodic, Risk-Based Reviews
IDPs don’t provide automated workflows for quarterly or risk-based reviews. Compliance standards like SOC 2 and ISO 27001 require periodic reviews; something only specialized user access review software can automate with reminders, delegation, and audit tracking.
5. No Integration with Finance Data (for Budget Alignment)
Access governance isn’t just about security; it’s also about cost control. IDPs lack integration with finance or procurement data, making it hard to align licenses with budgets. A user access review tool that includes spend visibility helps organizations connect access, risk, and cost.
CloudEagle.ai’s Seamless Integration with IDPs for User Access Reviews?
In the past, teams used spreadsheets or email approvals for user access reviews, which were time-consuming and prone to mistakes. Today, modern user access review software connects with IDPs like Okta, Azure AD, and Google Workspace to automatically collect data.
Reflecting on her experiences, Nidhi Jain, CEO and Founder of CloudEagle.ai, shares:
“I’ve seen it happen too many times, an employee changes roles, yet months later, they still have admin access to systems they no longer need. Manual access reviews are just too slow to catch these issues in time. By the time someone notices, privilege creep has already turned into a serious security risk.”
Here’s why this integration matters:
CloudEagle.ai works seamlessly with your Identity Providers (IDPs) like Okta and Microsoft AD to simplify user access reviews and improve security. Here's how this integration benefits your organization:
1. Real-Time Synchronization
CloudEagle.ai automatically syncs with your IDP to pull in the most current user data, roles, and access permissions. This ensures that the information is always up to date, so you can be sure that only authorized users have access to the right applications.
2. Automated Access Review Workflows
CloudEagle.ai automates the process of reviewing user access across all your connected apps. Set up workflows to regularly prompt key people (like IT or department heads) to review who has access to what, making sure that only the right people have the right permissions. This saves time and reduces human error.
3. AI-Powered Risk Detection
CloudEagle.ai uses AI to analyze user access patterns and flag any potential risks, like users having too much access (over-privileged) or behaving in ways that don't align with your security policies. The AI catches issues automatically, so you don’t have to rely on manual checks.
4. Granular Permission Control
CloudEagle.ai gives you clear visibility into user roles and permissions. This helps you spot users with excessive or outdated access, ensuring that your access control is always in line with your company’s security policies.
Key Benefits of Integrating CloudEagle.ai with IDPs for UAR
Integrating CloudEagle.ai with your Identity Providers (IDPs), such as Okta and Microsoft AD, delivers numerous advantages that help streamline User Access Reviews (UAR) and enhance both security and operational efficiency. Here's how:
1. Efficient Compliance
CloudEagle.ai automates user access reviews, helping ensure compliance with frameworks like SOC2, ISO 27001, HIPAA, and GDPR. Automated reviews and pre-configured audit trails reduce audit preparation time by up to 80%, making compliance checks faster and more consistent.
2. Reduced Security Risks
CloudEagle.ai continuously monitors user access, identifying over-privileged users or suspicious behavior. Real-time alerts help teams act quickly to prevent potential security threats, ensuring sensitive data is protected.
3. Improved Operational Efficiency
By automating user access reviews, CloudEagle.ai eliminates manual, error-prone processes, saving IT teams time and reducing administrative work. This ensures permission updates are made efficiently and without delays.
4. Audit-Ready Evidence
Every access review is automatically tracked and logged, providing clear, audit-ready evidence for internal and external audits. This helps maintain transparency and proves compliance during audits.
5. Customizable Workflows
CloudEagle.ai offers customizable workflows for user access reviews, allowing you to set up processes that fit your organization’s needs, ensuring reviews align with compliance schedules or trigger based on user activity.
How CloudEagle.ai Automates and Enhances Access Reviews?
While Identity Providers (IDPs) like Okta and Azure AD manage authentication, they struggle with automating periodic access reviews and handling non-SSO apps. CloudEagle.ai fills this gap by integrating with your IDP, automating and streamlining user access management across all apps.
The platform offers:
1. Contextual Governance Beyond IDP
CloudEagle.ai integrates seamlessly with identity providers like Okta and Azure AD. It discovers and manages access to all SaaS apps, including those outside of SSO, like free tools and AI apps. Pulling data from finance, browser activity, HRIS, and authentication systems, it helps IT and Security teams easily manage user access across the whole organization.
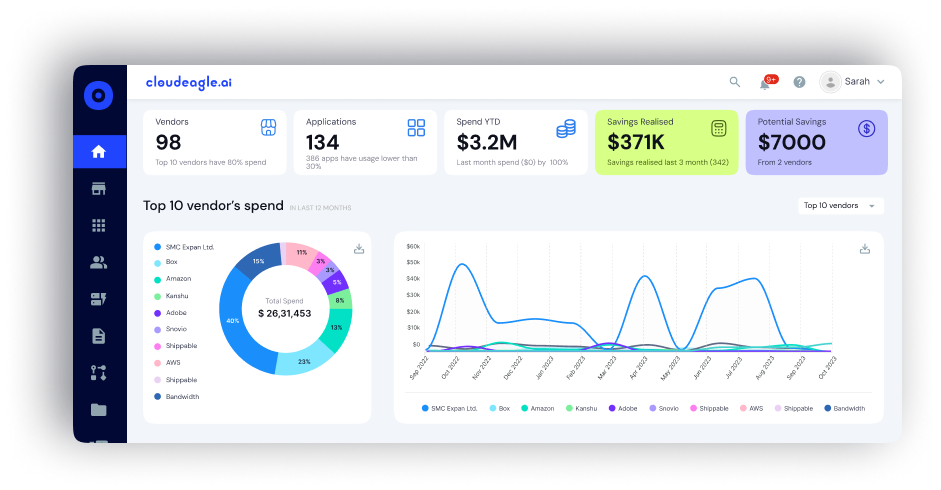
How it helps:
- Builds a single source of truth across IDP + non‑IDP apps
- Eliminates manual data gathering before reviews
- Ensures entitlements stay up to date
- Reduces identity/role inconsistencies
- Speeds up review readiness
2. Access Review Alerts and Notifications
CloudEagle.ai automates periodic user access certifications across all SaaS apps. You choose the cadence, quarterly, semi-annual, or annual, and reviewers receive context-rich records showing who has access and why.

Instead of digging through spreadsheets, reviewers only need to approve or revoke. This dramatically cuts review time and strengthens compliance for audits.
How it helps:
- Eliminates spreadsheet‑driven processes
- Simplifies SOC2/ISO‑aligned reviews
- Reduces review fatigue & time commitment
- Ensures every user’s access is verified regularly
- Improves compliance audit outcomes
Know how Dezerv automated its app access review process with CloudEagle.ai
3. Usage‑Aware Review Decisions
Instead of asking reviewers to guess whether access is still needed, CloudEagle.ai enriches access records with usage data, showing last login, activity levels, and license cost so reviewers can make smarter decisions.

How it helps:
- Prevents unnecessary permissions
- Enables intelligent decision‑making by reviewers
- Reduces over‑provisioning and license waste
- Highlights dormant accounts instantly
- Improves the accuracy of access recertification
4. Zero‑Touch Provisioning & Deprovisioning
CloudEagle.ai automates user lifecycle management using HR and IT workflows. Access is granted automatically based on the user’s role or department, regardless of whether the app sits behind your IDP.
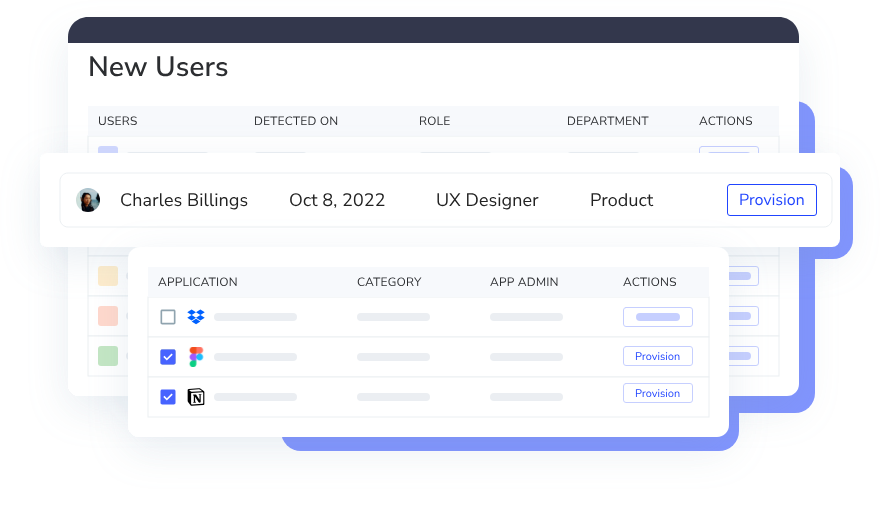
When the user changes roles or leaves the company, CloudEagle.ai instantly revokes access to prevent privilege creep and reduce security risk. This ensures clean, consistent access throughout the employee lifecycle.
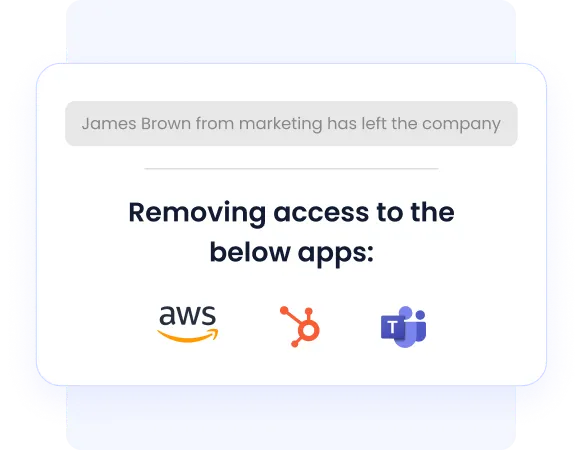
How it feels:
- No manual work for onboarding or offboarding
- Stops ex-employees from having access
- Cuts provisioning time from days to minutes
- Keeps license counts accurate, avoiding waste
- Helps employees start work productively on day one
5. Just‑In‑Time Access
CloudEagle.ai provides just-in-time access for contractors, interns, or short-term users. Access automatically expires, lowering the risks of excess permissions.
CIO, Red Hat, Jim Palermo, says:
“Adopting just-in-time access is the closest thing to a 'never trust, always verify' model for user permissions. If you’re still leaving standing privileges unchecked, you’re giving attackers exactly what they need to exploit your systems.”

How it feels:
- No unnecessary or always-on privileges
- Reduces insider threats
- Minimizes wasted licenses
- Adds protective guardrails for temporary users
Enforces least-privilege policies easily
6. Audit-Ready Logs
Every approval, revocation, and modification is logged automatically with timestamps and reviewer details. Audit‑ready reports can be exported anytime.
How it helps:
- Speeds up SOC2/ISO audit requests
- Eliminates manual evidence collection
- Improves traceability and accountability
- Reduces time spent preparing for audits
- Makes governance continuous and proactive
Check out this episode of CloudEagle.ai's SaaS Masterminds podcast, as Karl Haviland dives into AI, governance, and strategies for scaling innovation responsibly.
Conclusion
Integrating user access review tools with Identity Providers (IDPs) is essential for effective identity governance. While IDPs like Okta and Azure AD manage authentication, they lack the automation, visibility, and reporting needed for thorough access reviews.
By pairing IDPs with user access review software, organizations gain a single, comprehensive view of users, roles, and permissions across all apps, including those outside SSO. This improves accuracy, reduces manual effort, and lowers security and compliance risks.
The right platform automates review cycles, maintains audit-ready records, and ensures least-privilege access at scale, turning access reviews into a proactive security measure.
Ready to simplify your user access review process?
Schedule a demo with CloudEagle.ai to streamline your user access review process.

%201.svg)










.avif)




.avif)
.avif)




.png)









