HIPAA Compliance Checklist for 2025

Imagine a workplace where every employee has easy access to the resources they need, exactly when they need them - no more, no less.
An effective workplace is one where security risk is minimal and productivity grows. Proper identity lifecycle management can achieve these results.
Managing employee accounts and access privileges becomes increasingly complex as your company grows. User lifecycle management helps streamline this process. It enhances security by ensuring that only authorized workers can access sensitive data.
Also, it can save time for IT teams, as user lifecycle management will enable them to automate tedious tasks like user provisioning and deprovisioning, freeing up time for more critical tasks.
A well-implemented user lifecycle management strategy can transform your workplace into a highly efficient and secure environment.
What Is User Lifecycle Management?
User Lifecycle Management (ULM) is the process of managing a user’s access and permissions from the moment they join an organization to the time they leave. It covers everything from onboarding and setting up access, to updating permissions as roles change, and securely offboarding users by revoking access when they depart.
It includes all stages, from initially creating a new user account when an employee joins to modifying access rights as roles change and terminating the account upon departure.
It governs the entire process of a user's digital identity and corresponding permissions. When you implement user lifecycle management the right way, you can ensure that only authorized workers can access the resources they need to perform their duties effectively.
Simultaneously, you mitigate potential security risks by promptly revoking access when it's no longer needed. This process ultimately helps enhance security and productivity within your organization.
Importance of User Lifecycle Management for IT Teams
As stated, it helps enhance security by ensuring only active employees have access to company resources. This tailored access helps minimize the risk of data breaches or unauthorized access.
Next, you can streamline onboarding processes, allowing new hires to quickly receive the necessary accounts, access, and permissions to be productive from day one.
The CloudEagle.ai 2025 IGA Report reveals that 48% of ex-employees retain access to business applications post-termination, posing significant security risks such as unauthorized data access or insider threats.
It helps automate access modifications when employees change roles or responsibilities, reducing manual effort and errors.
And finally, it will enable your team to simplify offboarding process when employees leave, immediately revoking access to protect sensitive data while maintaining audit trails for compliance.
By implementing the best practices using a user lifecycle management solution, IT teams can improve the organization's efficiency, security, and regulatory compliance.
What Are the Key Stages of the User Lifecycle?
Here are the main stages of the user lifecycle:
User Onboarding (Provisioning)
When a new employee joins your organization, you must provision new users by creating their user accounts and granting them the necessary access rights to perform their jobs effectively.
This stage is crucial because it helps ensure new hires can hit the ground running from day one without productivity delays.
User provisioning can be driven by your HR or IT department, automatically triggering the account creation process upon hiring. Automation helps streamline this onboarding phase, reducing manual inputs and potential errors.
Also, it enables you to consistently apply access policies, ensuring new users only receive the appropriate level of permissions based on their roles and responsibilities.
User Management
Throughout an employee's tenure, user access management is pivotal in ensuring they have the right level of access at all times. As their roles and responsibilities evolve, their permissions must adapt accordingly.
This stage involves periodically reviewing and modifying user accounts to grant or revoke access to specific resources.
Additionally, you can leverage group provisioning to streamline access management. By assigning users to predefined groups based on their roles, you can collectively manage access rights for entire teams or departments.
Role-based access control further enhances this process, allowing you to define granular permissions aligned with job functions.
Change Management
Change is inevitable; you must manage your user lifecycle to adapt accordingly. As your employees' roles and responsibilities shift, their access needs will change.
An effective user lifecycle management strategy allows you to promptly modify user privileges, granting or revoking access to specific resources as required. This ensures your workforce can easily transition without hampering productivity.
Another crucial aspect is implementing system updates and upgrades. As new features or security patches are released, user lifecycle management helps ensure you facilitate provisioning these changes across user accounts.
This helps enhance functionality and also strengthens the overall security posture.
User Offboarding (Deprovisioning)
When employees leave your organization, user offboarding or deprovisioning is essential.
Deprovisioning refers to revoking all access rights and terminating user accounts across your company's systems and applications. This stage helps mitigate potential security risks.
Failing to deprovision inactive user accounts exposes your organization to vulnerabilities. Former employees may still retain access to sensitive data, posing a threat of data breaches or unauthorized activities.
In a survey of about 500 IT professionals from security company OneLogin, 20% said their organizations had experienced data breaches by ex-employees. Moreover, you risk non-compliance with industry regulations and internal policies governing access control.
When you promptly deprovision departing users, you eliminate the risks of unauthorized access and safeguard your organization's digital assets.
Automation will also help you streamline this process. It will ensure no inactive accounts slip through the cracks, maintaining a secure and compliant environment.
Benefits of Effective User Lifecycle Management
Effective User Lifecycle Management (ULM) brings several key benefits: stronger security, better efficiency, and lower costs. By automating onboarding and offboarding, organizations can reduce manual errors, ensure consistent access control, and streamline workflows, creating a more secure and productive setup.
- Enhanced productivity: By ensuring employees have the right access at the right time, they will focus on their tasks without unnecessary delays or roadblocks. Automated provisioning and deprovisioning help eliminate productivity bottlenecks.
- Better resource allocation: Proper access management helps optimize resource utilization by granting permissions only when required. It also helps prevent the underutilization or overprovisioning of costly software licenses and hardware assets.
- Improved security: Promptly revoking access for inactive users and consistently applying access policies help minimize security risks. It helps safeguard your organization's sensitive data and intellectual property.
- Increased efficiency and reduced IT burden: Automating user lifecycle processes helps streamline workflows, reduces manual effort, and minimizes human errors. It allows your IT team to focus on more strategic initiatives.
- Enhanced user experience: Seamless onboarding, efficient access modifications, and centralized self-service portals create a frictionless employee experience, boosting satisfaction and engagement.
Challenges in User Lifecycle Management
User Lifecycle Management (ULM) comes with several challenges, especially when it comes to managing user identities and access across their entire journey, onboarding, role changes, and offboarding. Common issues include a lack of automation, weak system integration, and overlooked offboarding. Other key hurdles are maintaining data security, ensuring compliance, and preserving data accuracy throughout the process.
- Manual processes and too many users: Without an automated system, managing user accounts and access rights manually becomes increasingly complex as your organization and employee base grow. This growth will lead to inefficiencies and potential errors.
- Inadequate or inaccurate access to resources: Failure to properly provision or deprovision user accounts can result in employees lacking the necessary access to perform their duties effectively or, conversely, retaining excessive permissions. This poses security risks.
- Increased security risks: Manual processes and data silos increase the risk of unauthorized access, data breaches, and compliance violations. Unmanaged, inactive user accounts can be a security vulnerability.
- Lack of multi-factor authentication and strong password policies: Weak authentication measures, user credentials, and password policies heighten the risk of account compromises. and authorized access, leading to insecure IT environments.
- Scalability as the business and employee base grow: Managing user lifecycle processes manually becomes increasingly challenging as your business expands, hindering your ability to scale efficiently and maintain control over access management.
Automate User Provisioning and Deprovisioning With CloudEagle.ai
As stated, automating user provisioning and deprovisioning is a great advantage, and doing it with CloudEagle.ai helps streamline your user lifecycle management processes. This enhances security and productivity.
As an all-in-one SaaS management platform, CloudEagle.ai offers powerful identity and access management functionalities tailored for IT and HR teams.
Auto-Provisioning Workflow
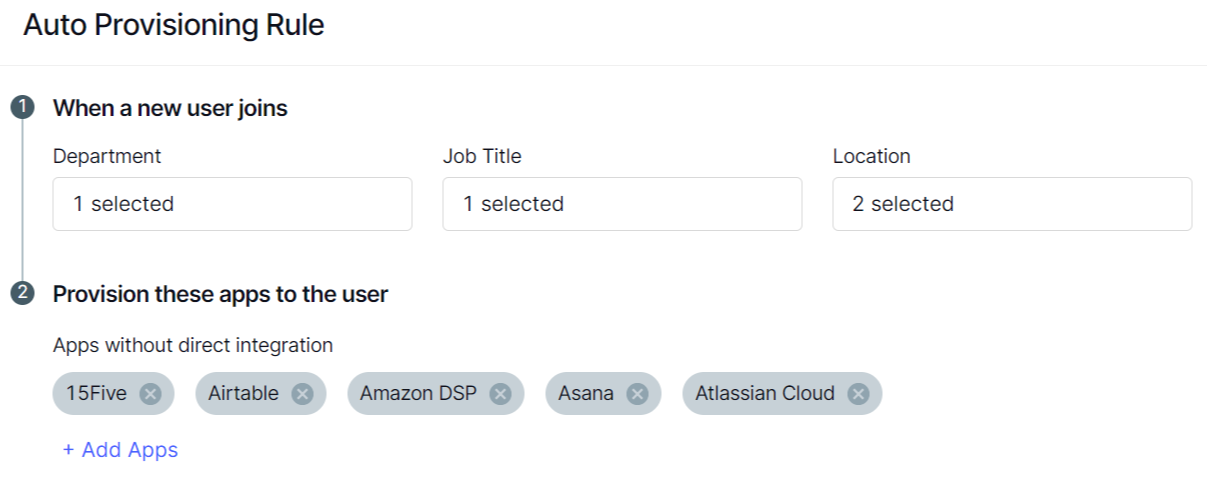
Manually provisioning users can be a time-consuming process; by leveraging CloudEagle.ai's auto-provisioning workflow, you can bid farewell to outdated methods.
Once system integrations are established, CloudEagle.ai consolidates your application stack data, segmenting it by departments like Marketing and Sales.
This segmentation helps you configure seamless provisioning workflows by selecting the department, job title, and location, and assigning relevant applications accordingly.

When new employees join, CloudEagle.ai automatically provisions their user accounts and grants access to the appropriate applications based on their role and department.
This automation helps ensure new hires can hit the ground running without delays, boosting productivity from day one.
Deprovisioning
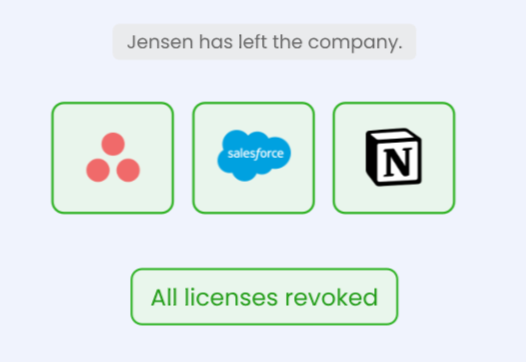
CloudEagle.ai helps simplify the deprovisioning process when employees depart. With a centralized view of all applications, a user has accessed, you can revoke access across multiple systems with just a few clicks.
Like provisioning, you can also configure deprovisioning workflows using CloudEagle.ai to reclaim unused licenses or deprovision terminated users. It has two deprovisioning rules:
- Auto Deprovisioning for Terminated Users
- Auto Deprovisioning for Non-Logged-In Users
You can configure the rules based on your requirements and automatically deprovision users from your system. CloudEagle.ai's system integrations ensure no unauthorized access is left behind, mitigating potential security risks.
When you embrace CloudEagle.ai's onboarding and offboarding modules, you eliminate manual efforts, reduce errors, and maintain a consistent access management strategy.
Moreover, you gain a centralized identity and access management system, streamlining user lifecycle processes while enhancing security and compliance across your organization.
Conclusion
User lifecycle management is the cornerstone for maintaining a secure, productive, and compliant organization.
When you effectively manage user accounts and access rights throughout the employee lifecycle, you can streamline user management, mitigate security risks, streamline workflows, and empower your workforce with the right access at the right time.
Don't let manual processes and inadequate access management hinder your organization's growth. Embrace automation and centralized user lifecycle management with CloudEagle.ai.
Book a demo today to unlock the full potential of secured access and skyrocketing productivity.
Frequently asked questions
1. What is the user lifecycle management method?
User lifecycle management is a method of overseeing users' journey from start to finish. It involves guiding users through stages like onboarding, active use, and offboarding, ensuring smooth transitions throughout.
2. What is the meaning of the ULM project?
The ULM project is about effectively managing user journeys. It aims to ensure employees have secure access, optimize productivity, and streamline processes from beginning to end.
3. What are the responsibilities of user lifecycle management?
In user lifecycle management, your responsibilities include guiding users through stages like onboarding, monitoring their activities, and ensuring smooth offboarding. You guard their journey, ensuring security and efficiency.
4. What are the ALM tools?
ALM (Application Lifecycle Management) tools help manage the entire software development process—from planning and coding to testing, deployment, and maintenance. Examples include Jira, Azure DevOps, and GitLab.
5. What is meant by customer life cycle management?
Customer Lifecycle Management refers to managing a customer's journey from awareness and acquisition to retention and loyalty, using data and strategies to improve engagement and value over time.
6.What do you mean by life cycle management?
Lifecycle management is the process of overseeing a product, user, or system through all its stages, from introduction and active use to updates, changes, and final deactivation or retirement.

%201.svg)







.avif)




.avif)
.avif)




.png)









