HIPAA Compliance Checklist for 2025

In today’s rapidly evolving digital world, identity has become the new perimeter in cybersecurity. The old ways of protecting IT systems based on fixed network boundaries are no longer enough.
With more people working remotely, the increasing use of cloud services, and the explosion of SaaS apps, protecting digital identities is now the most critical line of defense. Understanding what identity security means and how it safeguards systems is essential for every organization.
According to reports, 82% of all data breaches in recent reports involve stolen or compromised credentials, highlighting identity as the prime attack vector.
Identity security shifts the focus from where access comes from to who is requesting it. This inward-looking defense makes cyber identity the central control point. When identity is the new perimeter, managing and securing user identities builds the foundation for a strong security strategy.
This approach reflects the need for businesses to adapt to a borderless digital landscape where attacks target identities directly. By making identity the core defense, enterprises can better reduce access risks, protect sensitive data, and meet compliance requirements.
Let’s explore why identity is the new perimeter, the role of cyber identity, and practical steps to secure your enterprise’s next perimeter through effective identity security strategies.
TL;DR
- Identity security has replaced the traditional network perimeter. With cloud, SaaS, and remote work, securing just the network edge is no longer enough; identity is now the central point of control.
- Identity security focuses on verifying who is accessing resources rather than where access comes from, making identity and access management the new defense line.
- All types of identities, such as workforce, customers, machines, and third parties must be secured in today’s distributed IT environments.
- Workforce, customer, machine, and third-party identities all need protection. Securing all types of cyber identities is critical in modern, distributed IT environments.
- Strong identity-first defense uses MFA, adaptive policies, continuous monitoring, and governance. These pillars help enterprises defend against identity-based cyberattacks and ensure compliance.
Why Identity Replaced the Network Perimeter?
As IT environments become more complex and distributed, identity has taken over as the main focus of cybersecurity. Securing just the network boundary is no longer enough.
According to CloudEagle.ai’s IGA report, Chetna Mahajan, Global CDO & CIO at Webflow, believes:
“IAM is often the most underfunded yet mission-critical part of security. But those taking a proactive approach, starting with automation and AI-driven governance, are not just reducing risk, they’re unlocking efficiency and long-term cost savings.”
Today, identity is the new perimeter that every enterprise must protect, as:
Cloud, SaaS, and APIs Dissolved Boundaries
The rise of cloud computing, SaaS applications, and APIs has dissolved traditional network boundaries. Enterprise resources now span multiple platforms and locations, making it impossible to enforce security solely at a fixed network edge. This shift means the next perimeter is no longer a place but an identity.
Remote Work Made the Edge Everywhere
Remote work transformed the security landscape further by turning every device and location into a potential entry point. With employees and contractors accessing critical systems from home, coffee shops, and beyond, the network edge effectively became everywhere. Securing identity is the only way to maintain control in this decentralized environment.
Attackers Target Identities Before Networks
Attackers recognize this reality and increasingly target identities before they attempt to breach networks. Using tactics like credential theft, phishing, and social engineering, cyber criminals compromise user accounts to gain access. This approach bypasses traditional network defenses, making identity the prime target.
Core Concepts to Align On
When discussing why identity is the new perimeter, it’s essential to understand several foundational concepts in identity security.
Identity Vs. Account Vs. Credential
Identity is who a person or system is in the digital world. It represents a unique presence or profile in cybersecurity. An account is the digital profile linked to that identity in a specific system or application. It’s how the identity appears in that system.
Credentials are the proof used to confirm identity when accessing a system. These could be passwords, biometric data (like fingerprints), or security tokens. Knowing the difference between identity, account, and credential helps organizations build stronger security and avoid confusion in managing access.
Authentication, Authorization, And Governance
Authentication is the process of verifying that an identity is real, usually by checking credentials. Authorization happens after authentication and decides what resources or data an authenticated identity is allowed to access.
Governance means setting policies and continuously monitoring to make sure access follows the rules and complies with regulations. Together, these three form the foundation of identity security, ensuring the right people have the right access at the right time.
How Zero Trust Anchors Identity-first Security
Zero Trust means never automatically trusting any user or device, even inside the network.
Instead, every access request requires continuous identity verification.
By combining ongoing authentication and strict authorization, Zero Trust puts identity at the center of modern cybersecurity. This helps organizations protect their IT environments against today’s evolving threats.
The New Identity Landscape
Today’s identity landscape is more varied and complex than ever before. It includes not only employees but also contractors who need different levels of access across many systems. Managing all these identities is vital because identity is now the main way to protect company resources.
Workforce Identities: Employees And Contractors
The modern identity landscape includes diverse workforce identities—not just employees but contractors as well. Both groups need controlled access to multiple systems and resources. This broad range of identities is crucial because identity is the new perimeter protecting corporate assets.
Managing these identities effectively demands strong identification cyber security practices. Ensuring each user’s cyber identity is authenticated and authorized properly minimizes risks and supports secure productivity.
Customer Identities And CIAM Needs
Customer identities now play a significant role in the identity security landscape. Organizations depend on Customer Identity and Access Management (CIAM) solutions to securely onboard and manage millions of users.
CIAM balances the need for seamless digital experiences with strong privacy controls and compliance. Securing customer cyber identity is vital for preventing fraud and building trust in today’s digital economy.
Machine Identities: Apps, Bots, And Workloads
Non-human identities, such as applications, bots, and workloads, have surged with cloud and automation growth. These machine identities often have privileged access, posing significant security challenges.
Effective identity security requires continuous discovery, lifecycle management, and policy enforcement for machines. Protecting these cyber identities is a critical part of defending the next perimeter.
Third-party And Supply Chain Access
The scope of identity security now extends beyond internal users to include third-party vendors and the supply chain. These external identities need monitored, limited access to reduce the risk surface.
Controlling third-party cyber identity is key to preventing supply chain attacks and securing extended ecosystems where identity is the new perimeter, guarding all access points.
Pillars of an Identity-First Defense
91% of enterprises reported at least one identity-related cyber incident in the last year, showing the increasing targeting of digital identities.
Building a strong identity-first defense requires focusing on several key pillars that together protect modern IT environments effectively. These pillars ensure that identity is the new perimeter, securing every access point with robust controls and continuous monitoring.
Phishing-Resistant MFA and Passwordless Options
Multi-factor authentication (MFA) that resists phishing attacks is essential to prevent credential theft. Passwordless options further enhance security by removing the risks associated with weak or stolen passwords. Using phishing-resistant MFA reduces compromise risks and reinforces why identity is the new perimeter in cybersecurity.
Device Trust And Posture Checks At Login
Device trust involves checking the security posture of devices before granting access to resources. Posture checks look for compliance factors such as current patches, encryption status, and anti-malware protection. Incorporating device trust extends identity security beyond users to their devices, securing the next perimeter at the point of login.
Adaptive, Risk-Based Access Policies
Access policies that adapt based on risk signals like location, device health, and user behavior provide context-aware security. This flexibility improves security without hampering user productivity. Adaptive, risk-based policies are core to what identity security is in today’s dynamic threat landscape.
Least Privilege With Just-in-time Elevation
Limiting user access to the minimum necessary reduces attack surfaces. Just-in-time elevation grants temporary elevated rights only when required for specific tasks. This approach keeps cyber identity management tight, significantly lowering the risk of access misuse.
Continuous Monitoring And ITDR
Ongoing monitoring observes user activity for unusual behavior that may indicate threats. ITDR solutions detect and respond to identity attacks quickly to prevent breaches. Continuous monitoring is vital for maintaining a resilient identity-first defense, protecting cyber identity at every stage.
Governance: Reviews, Sod, And Certifications
Regular access reviews and audits ensure that permissions remain appropriate and compliant with policies. Segregation of duties prevents conflicting roles that could lead to fraud, while certifications enforce adherence to security standards. Good governance provides accountability and control, completing the pillars needed to defend the next perimeter.
Architecture Blueprint: Identity as the Control Plane
To secure modern IT environments effectively, identity must serve as the control plane—the central layer managing and enforcing access across all systems. This approach aligns with the idea that identity is the new perimeter and the next perimeter of defense.
HRIS And Directory As The Source Of Truth
Human Resource Information Systems (HRIS) and directories like Active Directory act as authoritative sources for identity data. They provide the base profile information used to create and manage workforce identities.
Accurate, up-to-date identity records ensure consistent identification cyber security and prevent erroneous access by leveraging trusted information sources.
Central IdP With SSO And Federation
A Central IdP enables Single Sign-On (SSO) and access federation services, allowing users to authenticate once and gain secure access to multiple applications. This reduces password fatigue and improves user experience.
Leveraging a central IdP strengthens what is identity security by unifying identity management and streamlining access control across the organization’s ecosystem.
Policy Engine For ABAC And Context Signals
Policy engines enable attribute-based access control by evaluating user attributes, device posture, location, and other context signals in real time. This dynamic approach to access decisions improves security.
ABAC policies enforce least privilege and adaptive security postures, helping maintain robust cyber identity governance at the next perimeter.
Data Protection And DLP Tied To Identity
Data Loss Prevention (DLP) and other data protection technologies must integrate with identity management to control who accesses sensitive information. Identity-aware data protection ensures that data usage complies with policies and regulations.
How CloudEagle.ai Helps With Identity and Access Management?
CloudEagle.ai is a sophisticated platform designed for SaaS management and access governance, empowering IT and security teams with complete visibility, streamlined automation, and compliance assurance—all while cutting costs and saving valuable time.
This platform seamlessly integrates with over 500 SaaS applications, effortlessly connecting with existing IAM, SSO, and security infrastructures. This ensures that organizations can secure their cloud environments efficiently without disrupting their current IT ecosystems.
Here’s how the platform simplifies IAM:
Comprehensive Visibility Across SaaS and AI Applications
Most enterprises are unaware of the sheer number of tools their workforce uses. While many apps are approved by IT, countless others are adopted independently by employees or departments, creating what’s known as Shadow IT.
Shadow IT introduces substantial security vulnerabilities and compliance concerns while inflating software expenses. CloudEagle.ai automatically detects every SaaS and AI tool used within the organization, consolidating data on usage, spending, and login activity into a single, intuitive dashboard.
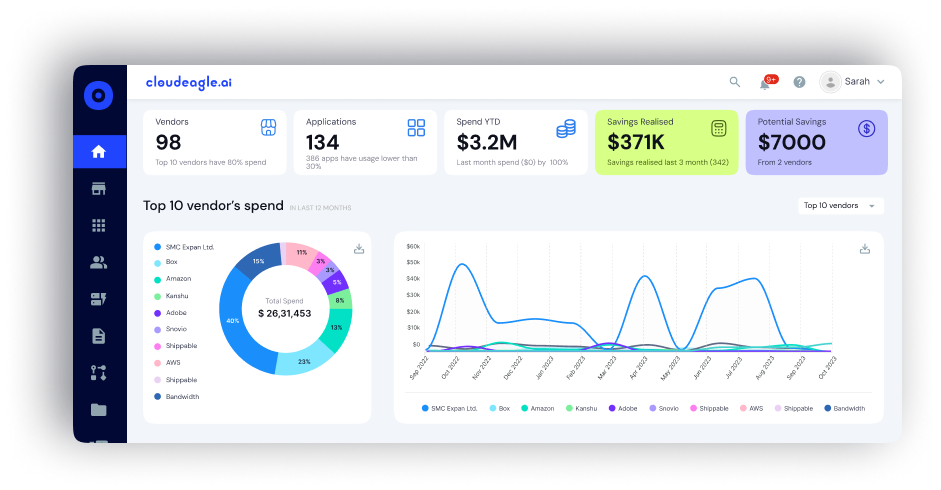
With this holistic insight, IT teams can close blind spots, reduce redundancies, and strengthen governance across all software assets.
Enforcing the Principle of Least Privilege
CloudEagle.ai helps enforce least privilege access policies by ensuring employees only retain the permissions they genuinely require. Over time, users often accumulate excessive privileges, such as admin rights, which elevate security risks.
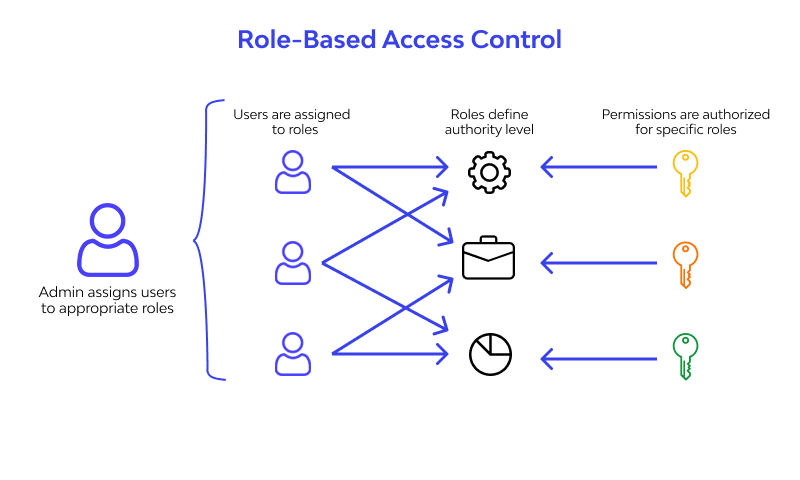
By continuously auditing and adjusting access rights, CloudEagle.ai combats privilege creep effectively, helping organizations protect sensitive information, minimize insider threats, and maintain regulatory compliance.
Automated Onboarding and Offboarding Made Easy
Managing user access during onboarding and offboarding is critical but prone to delays and mistakes when handled manually. CloudEagle.ai automates these workflows, delivering new hires instant access to the right applications from day one.

Similarly, when employees depart, the platform immediately revokes all access to apps, closing off potential security gaps and ensuring audit readiness.
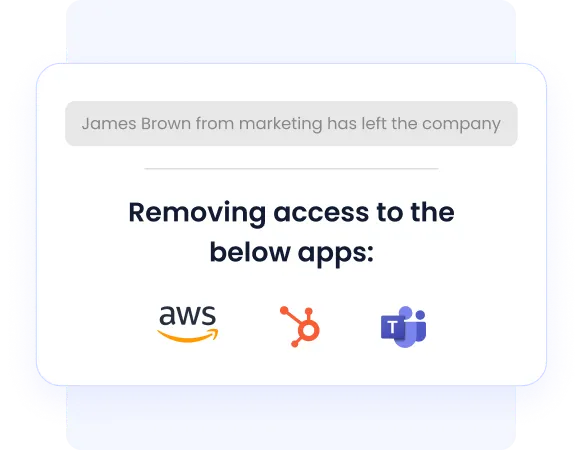
Know how JoVe streamlined employee onboarding and offboarding with CloudEagle.ai.
Streamlining Access Reviews and Compliance
Manual access reviews are labor-intensive and often inaccurate, increasing compliance risks with standards like SOC2, GDPR, and ISO. CloudEagle.ai automates ongoing access certifications using advanced AI-driven monitoring.
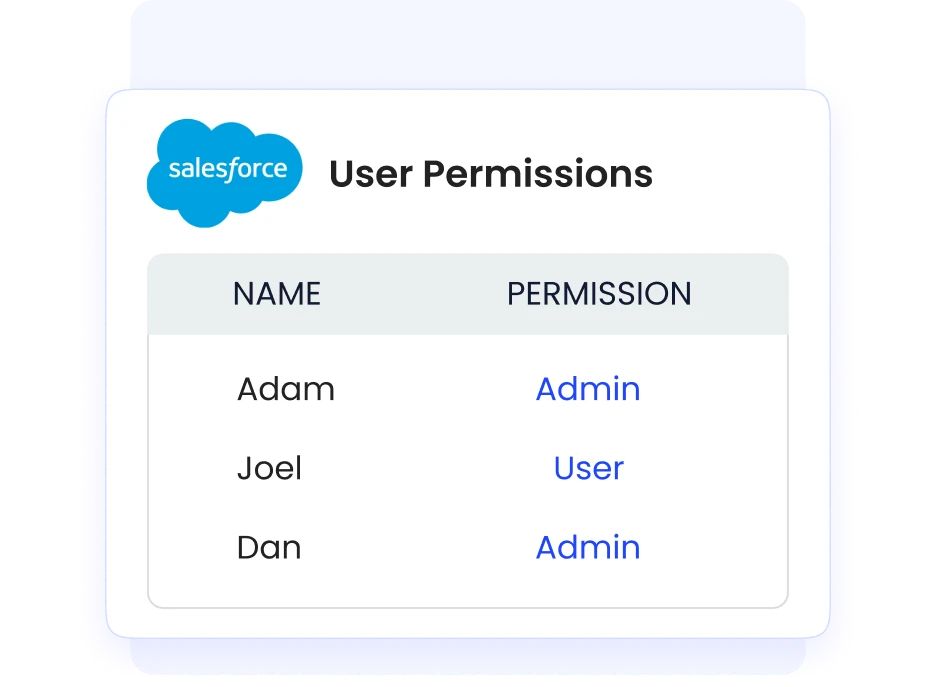
This capability generates audit-ready reports on demand, reducing audit preparation time while ensuring no outdated or excessive permissions persist undetected.
Centralized Compliance Management and Governance
Managing compliance across a sprawling SaaS landscape can be overwhelming, especially when access requests and approvals are fragmented across emails, spreadsheets, or ticketing systems.

CloudEagle.ai centralizes policies and workflows on a single platform. Automated governance enforces access controls consistently, while detailed logging delivers clear audit trails. This approach eases workloads for IT and compliance teams and guarantees audit preparedness year-round.
Role-Based Access for Efficient Control
Instead of assigning application access individually, CloudEagle.ai enables enterprises to set permissions based on roles, departments, or seniority levels. For instance, a sales manager can receive access to Salesforce, Gong, and Zoom by default, while a new developer obtains their required tools automatically on their start date.
Once defined, role-based policies are enforced consistently company-wide, reducing administrative burden, eliminating errors, and speeding up access provisioning.
Just-in-Time (JIT) Access for Temporary Permissions
Temporary workers, contractors, or project staff often retain access longer than necessary, opening security gaps. CloudEagle.ai supports just-in-time access, granting time-limited permissions that expire automatically once the task or contract ends. It minimizes unnecessary exposure and reduces privilege creep, all without sacrificing operational agility.
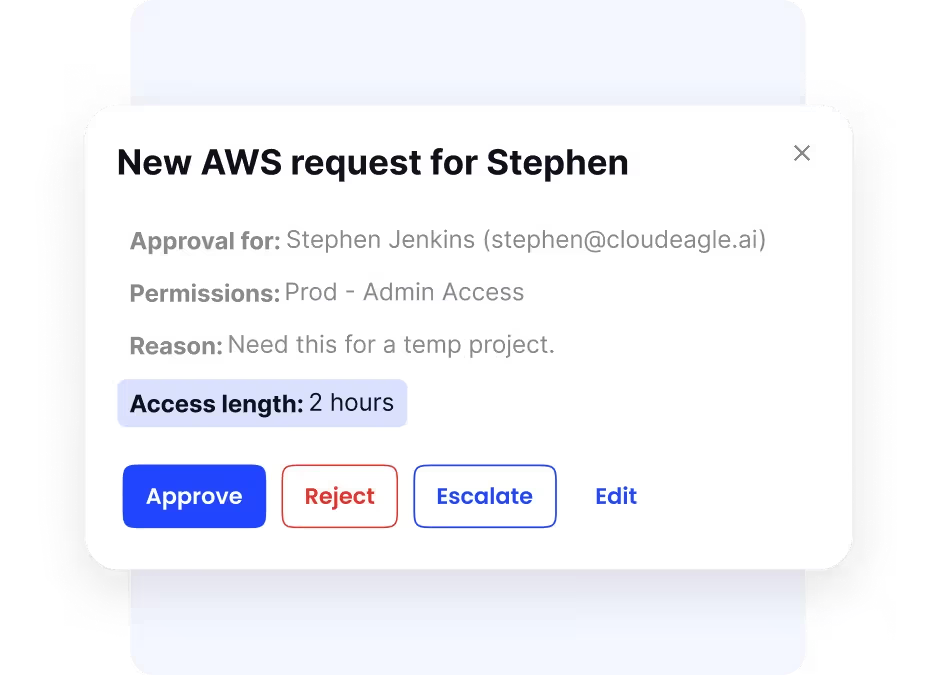
Centralized Employee Self-Service App Catalog
Employees frequently struggle to discover what applications are available or how to request access. Such requests are often scattered across chats, emails, or ticketing platforms, complicating approvals and compliance.

CloudEagle.ai resolves this with a centralized self-service app catalog, where employees can easily browse available tools and request access. Automated workflows route approvals correctly, while IT gains transparent visibility into all access activities.
Take a look at this testimonial from Alice Park at Remediant, where she shares her experience with CloudEagle.ai. She describes how the platform simplified their access management and enhanced security.
Conclusion
In today’s fast-changing IT world, identity is the new perimeter. To protect digital systems well, enterprises need to focus on identity-first security. This means securing the identities of employees, customers, machines, and partners.
According to CyberArk reports, Machine identities now outnumber human identities by 82:1, expanding the perimeter to include non-human identities and requiring advanced identity governance.
By using strong tools like phishing-resistant login methods, smart access policies, ongoing monitoring, and good governance, companies can stay ahead of growing cyber threats targeting identities.
CloudEagle.ai provides an advanced, AI-driven identity and access management platform that makes securing your identity perimeter easier. With features like automated onboarding and offboarding, centralized access control, privileged access management, and continuous compliance checks, CloudEagle.ai helps reduce risks and improve efficiency.
Ready to boost your identity-first security and protect your IT environment?
Schedule a demo with CloudEagle.ai and discover how it can transform your access governance.
FAQs
1. What is the identity-based perimeter?
The identity-based perimeter focuses on verifying who is accessing systems, regardless of location or device. It shifts security to controlling identity access rather than physical network borders.
2. What are the 5 D's of perimeter security?
The 5 D's include Detect, Deny, Delay, Defend, and Deter. These principles guide how security systems monitor, block, and respond to threats at the perimeter.
3. What are the 4 A's of security?
The 4 A’s are Authentication, Authorization, Accounting, and Auditing—key processes that ensure users are verified, granted appropriate access, tracked, and reviewed.
4. What is an identity security platform?
An identity security platform manages user identities, credentials, and access rights to protect against unauthorized access. It enforces policies that safeguard the new security perimeter.
5. What is the purpose of identity security?
Identity security aims to protect digital identities from being compromised. This prevents unauthorized access, reduces breaches, and ensures that only trusted users can reach sensitive resources.

%201.svg)








.avif)




.avif)
.avif)




.png)









