HIPAA Compliance Checklist for 2025

Have you ever wondered how you can seamlessly access multiple applications or services without logging in separately each time? This convenience is made possible by a concept called access federation.
But what exactly is access federation, and why is it becoming a critical element in modern identity and access management (IAM)?
Access federation allows users to log in once and then use many apps or systems without needing separate usernames and passwords for each one.
This is helpful for enterprises that use cloud tools like AWS SSO and lots of SaaS apps. It makes login easier for users, improves security, and helps IT teams manage access more effectively.
Let’s explore what access federation is, how it works, and why it matters for modern cloud-first enterprises.
TL;DR
- Access federation lets users log in once with a trusted identity provider and securely access multiple apps or services across different enterprises without separate credentials.
- It improves security by keeping passwords centralized and reduces password fatigue, making access easier and safer for users.
- Access federation relies on trust between identity providers (IdPs) and service providers (SPs), using protocols like SAML, OAuth, and OpenID Connect to securely share authentication tokens.
- It’s essential for managing access in modern cloud and multi-organization environments, such as B2B partnerships, universities, healthcare, and government agencies.
- By centralizing access control and auditing, access federation simplifies compliance, reduces operational overhead, and helps IT teams maintain strong security across distributed systems.
What Is Access Federation?
Access federation is a system that lets users securely log in once and gain access to multiple applications, websites, or cloud services across different enterprises or domains without needing to remember separate usernames or passwords for each.
Instead of creating and managing many accounts, users authenticate through a trusted identity provider (IdP), and other services, called service providers (SPs), accept that authentication.
This setup relies on a formal trust relationship between the identity providers and service providers, based on common technical standards such as SAML 2.0, OAuth, or OpenID Connect.
These protocols safely transfer authentication information and user attributes, ensuring that access permissions are granted only to authorized users while protecting personal data.
Why Is Access Federation Important?
- Simplifies User Experience: Users sign in once and get easy access to many apps, reducing password fatigue and confusion.
- Enhances Security: Credentials stay with the trusted IdP, reducing password exposure risks at individual service providers.
- Centralized Access Control & Compliance: Enterprises can govern and audit user access centrally through IGA identity (Identity Governance and Administration), ensuring security policies and compliance.
- Supports Modern Cloud and SaaS Environments: As businesses rely more on cloud services and multi-vendor SaaS ecosystems, federated access becomes essential for managing distributed systems efficiently.
Who Uses Access Federation?
Enterprises that use access federation tend to be those with complex IT environments requiring secure, unified access across many systems and services. This includes:
- Large enterprises and corporations that operate numerous applications and cloud services, often across multiple subsidiaries or global locations.
- Businesses are adopting cloud infrastructure, such as those leveraging AWS SSO federation to provide employees with seamless, secure access to AWS resources as well as other SaaS applications.
- Educational institutions and research enterprises frequently collaborate across universities and partner institutions using federated identity solutions to share resources while maintaining strict access controls (for example, projects like the Australian Access Federation enable seamless access for researchers and academics).
- Healthcare providers handling sensitive patient data need strong safeguards but flexible, easy access for authorized medical staff.
- Government agencies are implementing federation via solutions like Active Directory Federation Services (ADFS) and IAM identity federation with AWS to ensure least privilege and secure access for their broad user bases.
How Does Access Federation Work?
Access federation helps users log in just once and then get access to many different apps, websites, or cloud services, even if these belong to different companies or systems. Instead of having to remember separate passwords for each one, the user’s identity is shared safely between trusted parties.
According to CloudEgale.ai’s IGA report, Teza Mukkavilli, CIO/CISO, Tekion Corp, says,
“Relying on passwords alone today is a losing battle. Once credentials are stolen, they grant attackers the same level of access as legitimate users, making breaches almost undetectable until it’s too late. Without stronger authentication and identity controls, businesses are leaving the door wide open for cyber threats.”
Here’s how it usually works step-by-step:
- User Logs in Once: When you use a service, you first log in to your main account, called the Identity Provider (IdP). This is usually your company’s login system or another trusted place where your username and password get checked.
- Identity Provider Confirms Who You Are: After you enter your password (and maybe a code or fingerprint), the Identity Provider confirms your identity and creates a special digital “ticket” (called a token) that proves you have logged in successfully.
- Token Goes to the Other Service: When you want to use another app or cloud service (called the Service Provider (SP)), this service checks the token from the Identity Provider. If the token is valid, the service lets you in.
- Access without Logging in Again: Because the Service Provider trusts your Identity Provider, you don’t need to enter your password again. This lets you move smoothly between different apps and services without logging in over and over.
This whole process is safe because the token is encrypted and only shared with services that trust your Identity Provider. The system uses official methods like SAML or OAuth to make sure the information is secure and only shared with the right people.
Why Is This Useful?
- Simpler for Users: You log in once and get access to many things. No more juggling multiple passwords!
- More Secure: Your password is only entered once with a trusted provider, reducing the chance of it being stolen.
- Easier for IT: Companies can control who has access from one place and make sure rules are followed.
- Works Well in Cloud and Hybrid Systems: Whether apps are on the internet or inside the company, access is smooth and secure.
Why Access Federation Matters?
Access federation is important because it solves several common challenges faced by enterprises and users today:
Eliminates The Need For Multiple Login Credentials
Instead of remembering and managing different usernames and passwords for every app or service, users log in once through a trusted identity provider. This reduces password overload and the risk of weak or reused passwords.
Enhances User Experience Across Connected Apps
With access federation, users enjoy seamless access to all their applications without repeatedly signing in. This smooth, single sign-on (SSO) experience saves time and reduces frustration.
Streamlines Identity Management Across Environments
Modern businesses often use a mix of cloud platforms and on-premises systems. Access federation helps IT teams manage user identities and permissions consistently across these diverse environments, improving security and compliance.
Reduces Operational Overhead And Security Risks
Centralizing authentication through access federation reduces administrative tasks like password resets and account provisioning. It also lowers security risks by minimizing password exposure and enabling better control over who accesses sensitive resources.
Key Benefits of Access Federation
Access federation simplifies login by enabling secure, single sign-on access across multiple systems. Here are the following benefits of Access Federation:
Eliminates Multiple Login Credentials: Access federation lets users log in once through a trusted identity provider (IdP) and access many applications and services without re-entering passwords. This reduces password fatigue and the security risks associated with managing multiple usernames and passwords.
Enhances User Experience: By enabling seamless single sign-on (SSO) across connected apps and domains, access federation makes it easy and fast for users to move between services without repeated logins, improving satisfaction and productivity.
Improves Security: Consolidating authentication through a single trusted IdP lowers potential attack points, enforces consistent security policies (like multi-factor authentication), and reduces password-related vulnerabilities across systems.
Streamlines Identity and Access Management: Centralizing identity control allows IT teams to manage user access across hybrid or multi-cloud environments more efficiently. It simplifies provisioning, deprovisioning, and access auditing, helping enterprises maintain compliance and reduce operational overhead.
Reduces IT Costs and Administrative Burden: Automating identity management lowers the workload for IT support, cuts down on password reset requests, and reduces costs involved in maintaining separate login systems for each service.
Enables Secure Data and Resource Sharing: Federation supports trusted collaboration by allowing enterprises to share data and resources securely without exposing sensitive user credentials, useful for partnerships, research, and multi-entity operations.
Supports Flexibility and Scalability: Federated systems allow enterprises and departments local autonomy while maintaining overall security policies. This flexibility helps businesses quickly adapt to changes and scale their identity management as they grow or integrate new systems.
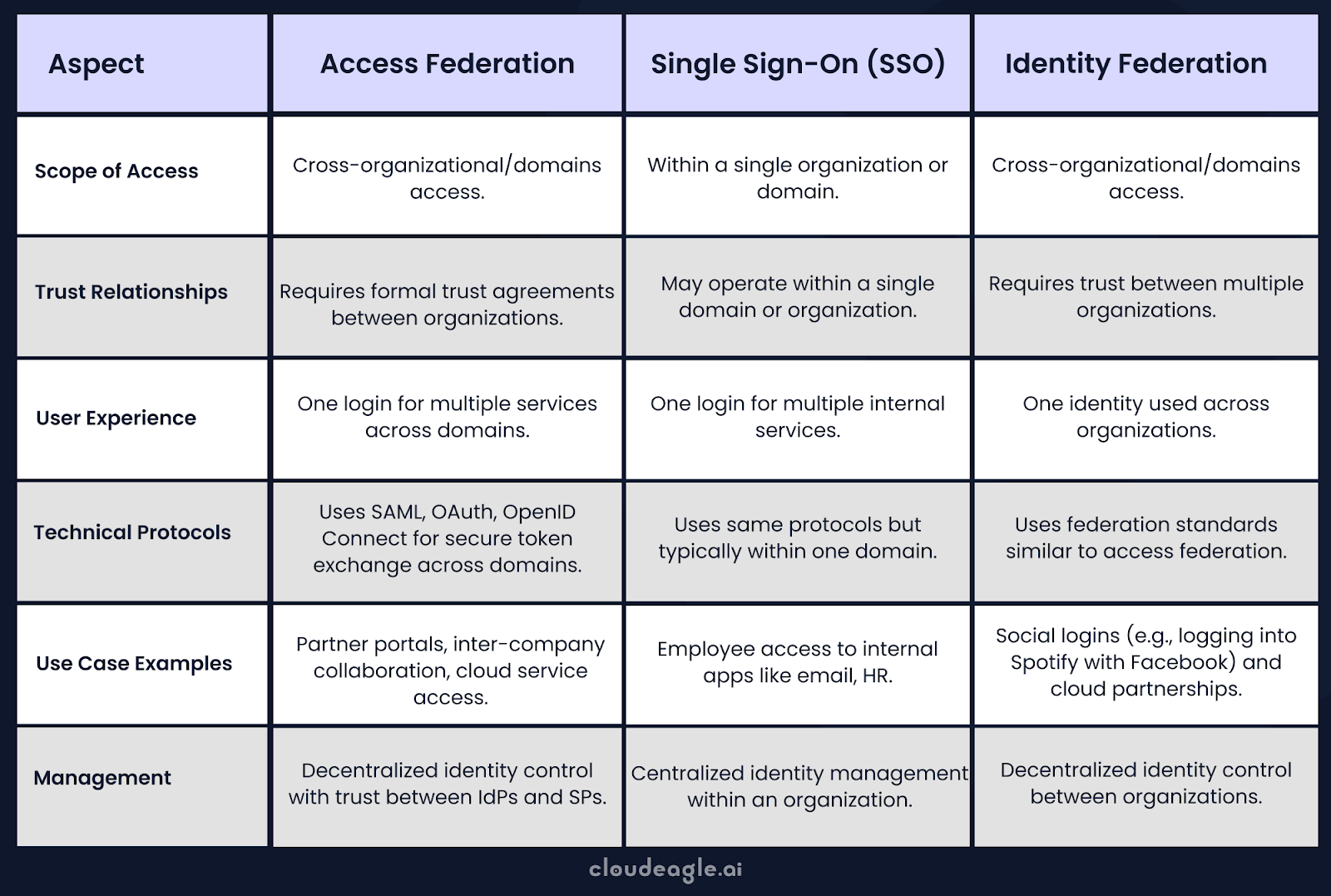
Common Use Cases of Access Federation, SSO, and Identity Federation
Many enterprises today use Access Federation, Single Sign-On (SSO), and Web Identity Federation to make login easier, more secure, and better for users and IT teams.
Each one plays a unique role, depending on how and where people need to access apps.
Access Federation: It lets users from different enterprises access shared apps with one login. For example, partner companies, universities, or hospital networks can share tools without creating separate accounts.
Single Sign-On (SSO): It is used within one organization. Users log in once and access apps like email, HR, and portals without signing in again. It saves time and reduces password fatigue.
Web Identity Federation: It allows users to use their existing login across multiple enterprises, while each group still manages its own user data. Ideal for secure collaboration between businesses or teams.
Access Federation vs. SSO vs. Identity Federation
Challenges and Risks of Access Federation
Access federation offers seamless login and shared identity across multiple systems, but it also introduces several important challenges and risks that enterprises must address to maintain security and compliance.
Expanded Attack Surface: Sharing user data among multiple enterprises increases exposure risks. If a third-party identity provider (IdP) is compromised or misconfigured, attackers can exploit this to gain access to many linked services.
Single Point of Failure: The IdP serves as the gatekeeper in federated environments. If it experiences downtime or is breached, users lose access or attackers may infiltrate all trusted applications relying on that IdP.
Insider Threats: Federated credentials often grant access to many systems. If stolen or leaked, an attacker can move laterally and escalate breaches rapidly across the network.
According to CloudEagle.ai’s IGA report, 28% of enterprises experienced major security incidents due to overprivileged access.
Interoperability Issues: Integrating diverse identity systems, especially mixing legacy and modern applications, can cause compatibility problems and security gaps due to inconsistent standards or policies.
Privilege Creep: Without proper management, users can retain excessive permissions over time due to improper deprovisioning or role changes, increasing risk of misuse or accidental data exposure.
Compliance and Privacy: With data shared across domains, protecting personal information and adhering to regulations like GDPR is complex. Lack of clear controls or accountability can lead to violations and penalties.
Complexity in Management: Establishing and maintaining trust frameworks, onboarding partners, and enforcing unified protocols add operational overhead and increase chances of security lapses.
Monitoring and Auditability: Federated systems often lack comprehensive visibility, making suspicious activity detection and regulatory audit readiness more difficult without advanced monitoring tools.
Legacy System Integration: Older platforms may not support federation standards fully, requiring costly and time-consuming adaptations to fit into the federated environment.
Role of CloudEagle.ai in Access Management
CloudEagle.ai is an AI-powered SaaS management and access governance platform that helps enterprises manage all their SaaS apps in one place. It gives IT, security, and procurement teams complete visibility and control over who has access to what apps at all times.
Instead of relying on manual processes, CloudEagle.ai automates how users are added, managed, and removed from tools, making access management more secure, efficient, and audit-ready.
Now let’s break down the key ways CloudEagle.ai helps with access management:
Unified Dashboard
CloudEagle.ai gives IT and security teams a single place to manage access across all SaaS applications. Instead of switching between tools or spreadsheets, teams get a real-time view of which users have access to which apps and what kind of access they have (admin vs. user).

This clear visibility helps prevent security blind spots and ensures better control over the entire SaaS environment. Teams can quickly identify unnecessary or risky access and take action to maintain a secure, well-managed system.
Automated Provisioning and Deprovisioning
CloudEagle.ai simplifies one of the most critical tasks in access management: making sure users get the right access at the right time, and lose it when they no longer need it.
For provisioning, CloudEagle.ai integrates directly with your HR and IT systems to automatically assign app access as soon as a user joins or changes roles. This eliminates manual setup delays and reduces onboarding friction.

For deprovisioning, CloudEagle.ai ensures no access is left behind when someone exits the enterprise or transitions to a new role. It automatically detects these changes and removes access across all connected SaaS apps, helping prevent security risks like unauthorized access, orphaned accounts, and privilege creep.

Know how JoVe Streamlined Employee Onboarding and Offboarding With CloudEagle.ai
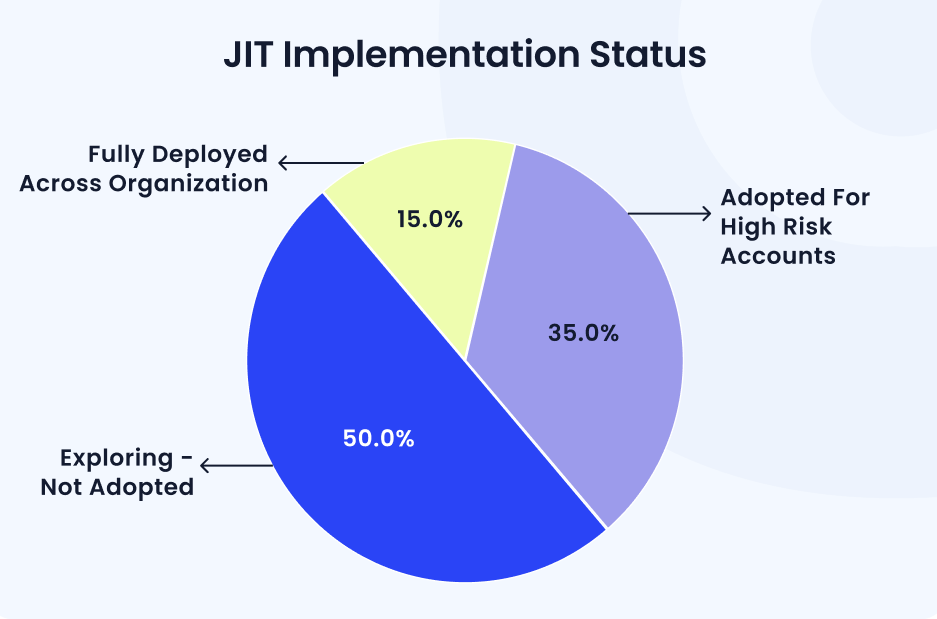
Time-Based and Just-In-Time Access
In many cases, users need access to certain apps or data only temporarily, such as during a specific project or while covering for a colleague. CloudEagle.ai’s Just-In-Time (JIT) access feature grants permissions only for the exact time they are needed and automatically revokes them after a set period.
Giving just-in-time access helps keep systems safe by making sure users only have access when they need it. But according to CloudEagle.ai’s IGA Report, only 15% of companies fully use Just-In-Time (JIT) provisioning; even though it’s a smart way to stay secure and compliant. More businesses should take advantage of it.
By automating these workflows with AI-driven controls, CloudEagle.ai ensures secure, efficient access management tailored to your organization’s needs.
Real-Time Monitoring and Alerts
Security is about being proactive, not just reacting after something goes wrong. CloudEagle.ai provides real-time monitoring of access activity across all connected SaaS tools.
If it detects suspicious behavior (such as failed logins, unusual access times, or changes to admin roles), it sends alerts to IT or security teams right away. It also logs all access-related events so that teams can easily investigate issues or provide documentation during audits.
Role-Based Access Control (RBAC)
CloudEagle.ai easily integrates with your organization’s identity providers like Okta or Azure AD to enforce Role-Based Access Control (RBAC). Each user is assigned a role, such as Sales Rep, HR Manager, or Developer, and given access only to the apps and features needed for that role.

This simplifies management, strengthens security, and follows the least privilege principle, ensuring users have only the permissions they require. By connecting with popular IdPs, CloudEagle.ai gives you centralized visibility and control over user roles and app access across your SaaS ecosystem.
Privileged Access Management
CloudEagle.ai gives IT and security teams a single platform to manage access across all SaaS applications. Instead of switching between tools or spreadsheets, teams get a real-time view of which users have access to which apps and what kind of access they have (admin vs. user).

This clear visibility helps prevent security blind spots and ensures better control over the entire SaaS environment. Teams can quickly identify unnecessary or risky access and take action to maintain a secure, well-managed system.
Automated Audits
Preparing for security audits can be time-consuming and stressful, but CloudEagle.ai simplifies the process by automatically keeping detailed, real-time logs of who accessed what, when, and why. This continuous and accurate tracking eliminates manual effort and reduces risks from oversight.

The platform also quickly generates comprehensive, audit-ready reports tailored for major compliance frameworks such as SOC 2, ISO 27001, and GDPR. These automated reports speed up audit preparation and provide clear evidence to regulators and auditors, proving that your access management policies are consistently enforced and effective.
Explore how Treasure Data Enhanced Access Management and Reporting with CloudEagle.ai.
8. Simplified Governance
Governance isn’t just about having rules; it’s about making sure they are followed consistently. CloudEagle.ai automates access reviews, sends reminders for policy updates, and enforces rules across all your SaaS apps. This reduces manual effort, ensures regular access reviews, and removes outdated permissions.
With CloudEagle.ai, your teams gain peace of mind knowing that access rights are always up to date, your systems stay secure, and you’re ready for audits at any time.
Want to see how automated onboarding and offboarding can help your team? Hear how Alice Park at Remediant leveraged CloudEagle.ai to automate their user provisioning and deprovisioning process.
Conclusion
Access federation allows users to securely log in once and gain seamless access across multiple applications, systems, and SaaS services, without juggling multiple passwords. However, its complexity and security risks require robust identity and access management (IAM) solutions to ensure safety, compliance, and operational efficiency.
CloudEagle.ai addresses these challenges by centralizing access management into a single, intelligent platform. It automates onboarding and offboarding, enforces time-based access controls, manages privileged accounts, and continuously monitors activity with AI-driven insights.
By choosing CloudEagle.ai, enterprises achieve clear visibility into who has access to what, why, and how it’s used, ensuring that the right people get the right access at the right time; protecting sensitive data and resources without slowing down operations.
Secure and simplify your organization's access management with CloudEagle.ai.
Schedule a demo to discover how effortlessly CloudEagle.ai automates access control, boosts security, and simplifies compliance across all your SaaS applications.
FAQs
1. What does it mean to federate access?
Federated access allows users to log in once and securely access multiple systems or apps across different organizations or domains. It enables seamless authentication by sharing user identity and permissions between trusted providers, eliminating multiple usernames and passwords.
2. What is federation access in Teams?
Federation access in Teams refers to enabling users from different organizations to communicate, collaborate, and share meetings or chats seamlessly by establishing trust between their identity systems. This allows cross-organization access without needing multiple accounts.
3. What is an IGA identity?
IGA (Identity Governance and Administration) identity refers to managing users’ digital identities with a focus on ensuring proper access rights, compliance, and security. It includes the processes for provisioning, reviewing, and revoking access across systems.
4. What does IGA mean in identity?
IGA stands for Identity Governance and Administration. It is a discipline that manages and controls user identities, their roles, and access permissions to ensure security policies, regulatory compliance, and minimize unauthorized access risk.
5. What is the IGA solution for identity?
An IGA solution helps companies control who can access which apps and data. It automatically gives access when someone joins, updates it if they change roles, and removes it when they leave. It also checks access regularly and follows security rules to keep the company safe and compliant.

%201.svg)







.avif)




.avif)
.avif)




.png)









