HIPAA Compliance Checklist for 2025

Managing employee access, privileges, and security within an organization is a complex task. According to IBM Security 2024, over 80% of data breaches involve compromised employee credentials, which makes controlling access from day one more critical than ever.
The Joiner-Mover-Leaver process, commonly referred to as the JML process in IT, is a structured approach to ensure that new employees, existing employees who change roles (movers), and departing employees (leavers) are handled efficiently.
According to Gartner, enterprises that automate the JML process reduce identity-related risks by up to 60%. Implementing a robust JML process framework not only safeguards sensitive information but also enhances operational efficiency, supports compliance, and reduces security risks.
In this guide, we’ll walk through each phase of the JML process, the benefits, challenges, and how automation and modern tools like CloudEagle.ai can simplify the process.
TL;DR
- The Joiner-Mover-Leaver (JML) process manages user identities across onboarding, role changes, and offboarding.
- Without JML, organizations risk security gaps, compliance issues, and wasted SaaS spend.
- It strengthens security, boosts efficiency through automation, and ensures audit-ready compliance.
- Manual errors, HR-IT misalignment, and unmanaged SaaS access create vulnerabilities.
- CloudEagle.ai automates JML, cutting SaaS costs by 10–30% and reducing manual work by up to 80%.
What is the Joiner-Mover-Leaver (JML) Process?
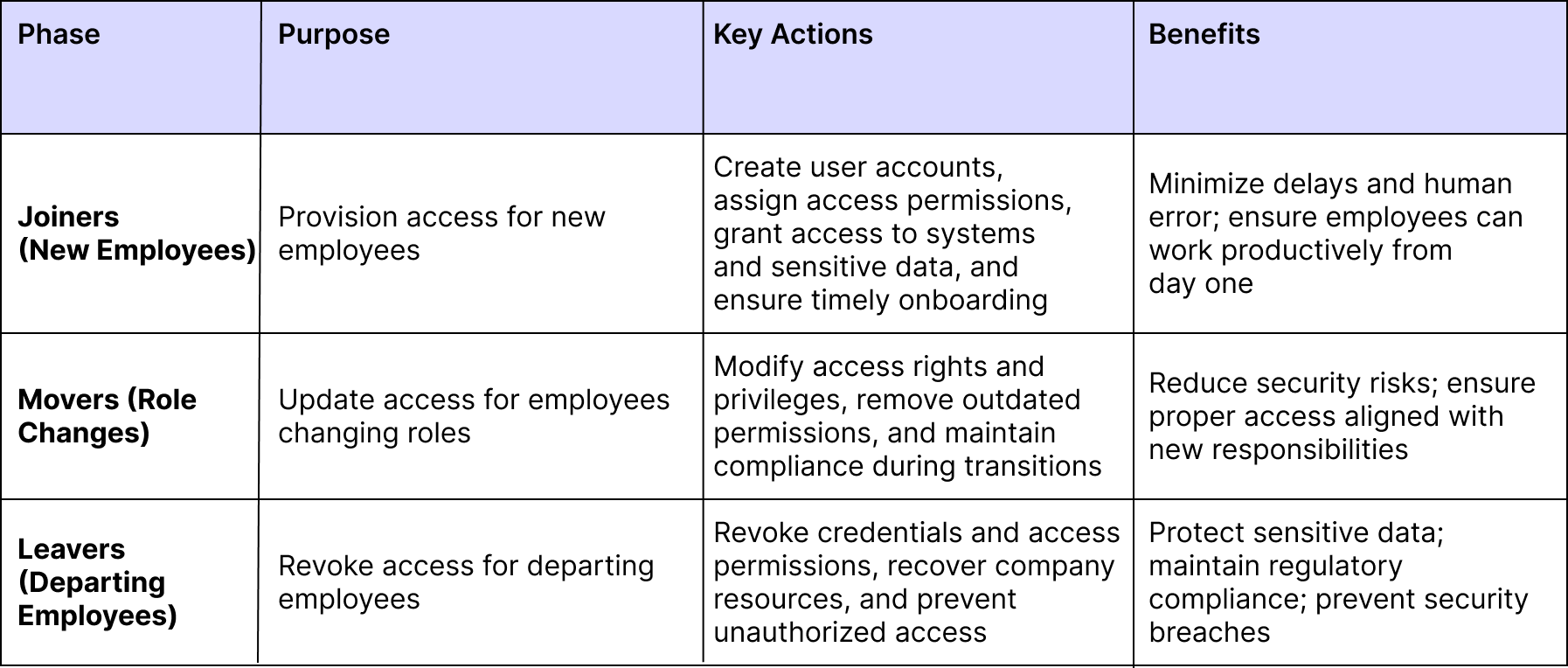
The Joiner-Mover-Leaver (JML) process manages an employee’s digital identity and access throughout their tenure. It covers Joiners (provisioning access), Movers (updating access for role changes), and Leavers (revoking access).
- Joiners (New Employees):
- Provision user accounts and assign appropriate access permissions
- Grant access to systems, applications, and sensitive data needed for their role
- Ensure timely onboarding to minimize delays and human error
- Movers (Employees Changing Roles):
- Update access rights and privileges according to new responsibilities
- Remove outdated permissions from previous roles
- Maintain compliance and reduce security risks during transitions
- Leavers (Departing Employees):
- Revoke credentials and access permissions promptly
- Recover company resources like devices and software licenses
- Prevent unauthorized access and support regulatory requirements
In fact, the average global cost of a data breach has reached $4.88 million. Organizations that neglect the JML process in IT risk, security breaches, compliance violations, and operational inefficiencies.
How Does the JML Process Framework Work?
The JML process framework manages user identities and access throughout an employee’s lifecycle. Joiners get initial access, movers have permissions updated for new roles, and leavers have access removed. Automation improves security, efficiency, and reduces risks like privilege creep and data breaches.
The Joiner Phase – Onboarding New Employees
During the joiners process, new users are provisioned access to company systems based on their role attributes and departmental needs. This phase often involves:
- Creating user accounts in Active Directory or other IAM platforms
- Assigning access rights and access permissions to necessary resources
- Integrating HR system data for accurate information on new responsibilities
The Brandon Hall Group found that organizations with effective onboarding programs can boost new hire productivity by over 70%.
Effective onboarding reduces delays and prevents human error that can cause access gaps or security risks. Modern solutions automate provisioning, ensuring users access only what they need, enhancing operational efficiency.
The Mover Phase – Role Changes and Access Updates
When employees change roles or move to different departments, their access permissions need to be updated accordingly. The JML process helps ensure these changes are made properly, reducing the risk of shadow IT and keeping the organization compliant. Key actions include:
- Updating access permissions for sensitive information
- Removing outdated privileges from previous roles
- Triggering automated access reviews to validate ongoing authorization
Proper handling of movers prevents unauthorized access and ensures collaboration is uninterrupted.
The Leaver Phase – Offboarding and Access Removal
The leaver processes are critical for security and compliance. When employees leave the organization, their user accounts, credentials, and privileges must be revoked promptly. Essential steps include:
- Terminating access rights across all platforms, including SaaS applications
- Recovering company resources like laptops and mobile devices
- Ensuring compliance with SOX, HIPAA, and other data protection regulations
Failing to manage leavers properly increases the risk of security breaches, data leaks, and regulatory penalties.
What Are the Benefits of the Joiner-Mover-Leaver Process?
The Joiner-Mover-Leaver (JML) process enhances security by managing access privileges, boosts efficiency through automation, and ensures compliance by standardizing access changes. It streamlines onboarding and offboarding, reduces insider threats, minimizes human error, and provides an audit trail to protect sensitive data.
The ability to automate these tasks is more critical than ever due to a persistent industry challenge: the security skills gap. Additionally, in 2024, 53% of organizations that experienced a data breach reported significant shortages in their security staff.
In security, everything starts with identity – knowing who the users are... From there, you must look at what those users can do (authorization) and then monitor what they did (accounting/auditing).
-Heidi Bullock, CMO, Identity Management Day
Here’s a closer look at the key benefits:
1. Stronger Identity and Access Management (IAM)
Implementing a Joiner Mover Leaver process strengthens identity governance and ensures users access only the systems and sensitive data required for their role. Key benefits include:
- Improved access control: Automated access requests and access changes reduce human error.
- Better visibility: Track user identities, credentials, and privileges in real time.
- Efficient onboarding and offboarding: Manage joiners, movers, and leavers without delays.
- Enhanced operational efficiency: Streamlined workflows reduce manual effort and errors in access management.
2. Compliance with IT Security Requirements
A structured JML process framework helps maintain regulatory compliance by documenting onboarding and offboarding processes and performing regular audits. Key benefits include:
- SOX and HIPAA compliance: Ensure that sensitive information is only accessible to authorized users.
- Audit readiness: Simplify reporting. for auditors with clear logs of access reviews
- Reduced risk of violations: Automated tracking of access permissions helps prevent unauthorized access.
- Regulatory confidence: Maintain compliance with data protection regulations and internal policies.
3. Reduced Insider Threat and Data Risks
Consistently applying access reviews and controlling access permissions minimizes security risks and potential breaches. Key benefits include:
- Proactive privilege management: Leavers, movers, and joiners have their access rights updated accurately.
- Prevention of breaches: Reduce the chance of unauthorized access to sensitive information.
- Improved data protection: Ensure only authorized users can access critical resources.
- Enhanced security posture: Automated JML workflows limit human error and security cracks in the system.
What Are the Common Challenges in JML Process Management?
Common challenges in the JML (Joiner-Mover-Leaver) process include manual workflows, HR–IT coordination gaps, managing access across multiple platforms, weak change management, and a lack of automation. These issues can cause security vulnerabilities, wasted licenses, administrative inefficiencies, and a poor employee experience.
1. Manual Tracking of Access Rights
Relying on spreadsheets or manual logs for access management can lead to mistakes and delays. Challenges include:
- Human error: Manual updates to access permissions can result in unauthorized access.
- Delayed provisioning: Joiners or movers may experience delays in getting the resources they need.
- Incomplete records: Lack of centralized tracking reduces visibility of user identities.
- Compliance risk: Harder to maintain regulatory compliance without automated access reviews.
For context, manual audit processes for user identities can take over half an hour per identity, which, for a mid-size organization, can add up to 7,376 hours (307 days) annually.
2. Lack of HR–IT Integration
Poor integration between the HR system and IT platforms can create inconsistencies. Challenges include:
- Outdated information: Changes in new roles or termination events may not reflect in access management.
- Operational inefficiency: IT teams spend more time manually reconciling user accounts and credentials.
- Increased security risks: Movers may retain access to sensitive data from prior roles.
- Audit complications: Inconsistent data makes audits and reporting more difficult for auditors.
3. Shadow IT and Unmonitored Applications
Unapproved apps and platforms used by employees can bypass JML process workflows, creating vulnerabilities. Challenges include:
- Unauthorized access: Employees may gain access permissions outside official channels.
- Security breaches: Lack of monitoring increases security risks and exposure of sensitive information.
- Limited visibility: IT teams cannot track users' access across all platforms and resources.
- Compliance gaps: Regulatory compliance may be compromised if access rights aren’t enforced consistently.
How to Automate the JML Process in IT?
Automation is the key to a fast, secure, and error-free JML process. By leveraging modern IAM tools and workflow automation, organizations can manage joiners, movers, and leavers efficiently while maintaining compliance.
Role of Identity and Access Management Tools
Modern IAM platforms act as a central hub to manage user identities and access rights across all systems. These tools allow you to:
- Automatically provision new employees with the right access permissions and resources.
- Trigger role-based access updates for movers, ensuring outdated privileges are removed.
- Revoke leavers’ credentials instantly to prevent unauthorized access.
Organizations with fully deployed AI and security automation, for instance, experienced breach costs $2.2 million lower than those without such systems
The result is reduced human error, improved visibility into user accounts, and consistent access governance.
Automating Onboarding and Offboarding Workflows
Automation simplifies every step of the joiners and leavers processes. Key features include:
- Joiners process: Immediate creation of user accounts, assignment of access rights, and provisioning of required resources.
- Movers process: Automatic updates to privileges and access changes with notifications to relevant stakeholders.
- Leavers process: Swift revocation of credentials, recovery of company assets, and enforcement of compliance policies.
This approach eliminates delays, minimizes security cracks, and ensures that sensitive information is protected throughout the identity lifecycle management.
Continuous Monitoring and Access Governance
Automation doesn’t stop at provisioning and deprovisioning. Continuous oversight ensures ongoing security and compliance:
- Regular access reviews verify users' access and prevent the accumulation of excessive privileges.
- Real-time monitoring identifies unauthorized access or abnormal access requests.
- Integration with advanced IAM solutions and platforms like CloudEagle.ai ensures full visibility over user identities and access changes.
- Maintains adherence to SOX, HIPAA, and other data protection regulations automatically.
By combining automated workflows with continuous monitoring, organizations can streamline the JML process, reduce human error, and mitigate security risks, all while keeping operational efficiency high.
How CloudEagle.ai Simplifies the JML Process?
Managing the Joiner-Mover-Leaver process manually can be slow, error-prone, and risky, especially in organizations with many SaaS apps. Delays in onboarding and offboarding, poor access visibility, and inconsistent permissions increase security risks and compliance challenges.
CloudEagle.ai solves this by centralizing and automating the JML process, ensuring employees get the right access at the right time while improving efficiency and maintaining compliance.
Zero-Touch Onboarding and Offboarding
CloudEagle automates provisioning & deprovisioning for joiners and leavers, ensuring employees can start work immediately or have access removed completely when they depart. This covers both apps managed via an identity provider (IDP) like Okta and those outside of it, eliminating gaps in access.
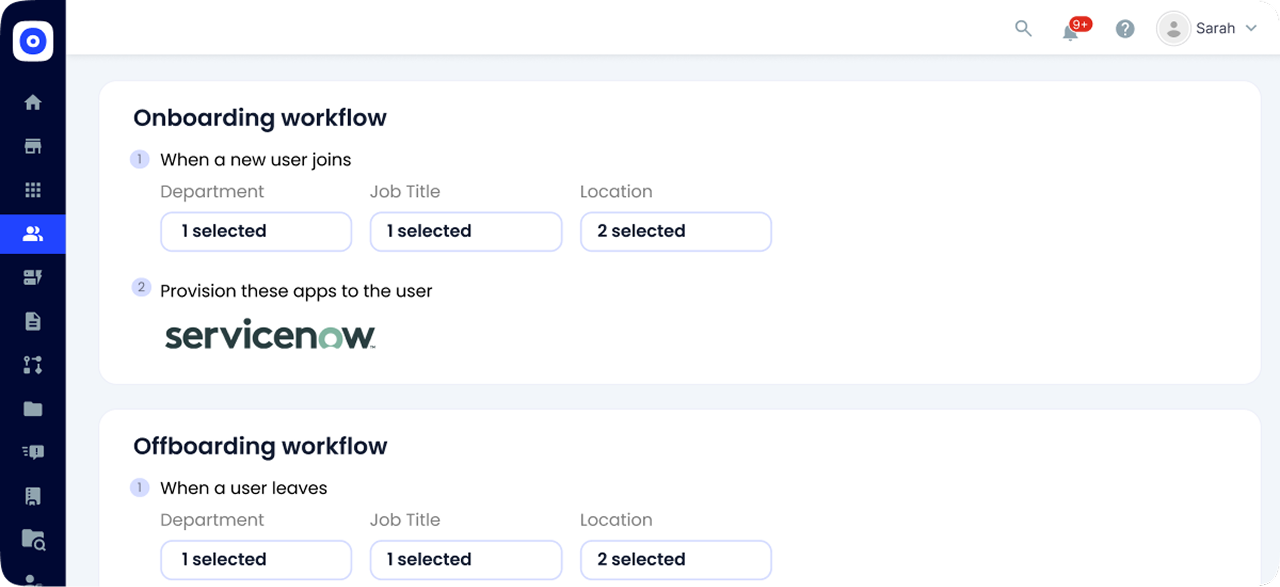
By automating these processes, organizations can:
- Reduce delays in onboarding and offboarding
- Eliminate lingering access rights that pose security risks
- Ensure new users get the right resources and privileges instantly
- Maintain compliance by having a structured, consistent process
Centralized Employee App Catalog
CloudEagle provides a centralized app catalog that simplifies access requests. Employees can request apps through a single interface, which ensures proper approvals and keeps shadow IT under control.
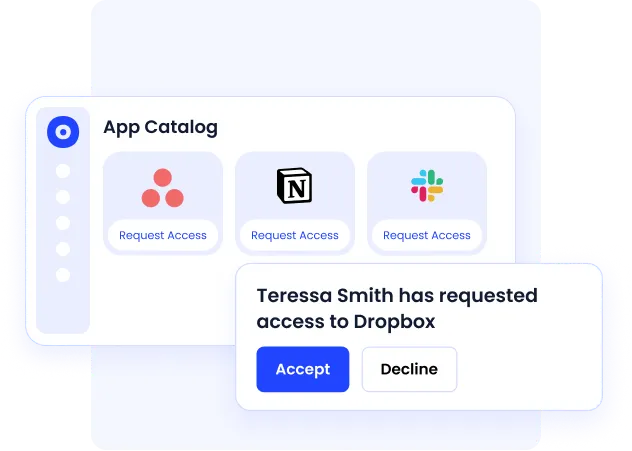
IT teams benefit from:
- A structured, consistent workflow for access requests
- Clear tracking of users' access and credentials
- Better alignment with regulatory compliance and internal policies
- Reduced operational overhead and simplified support for new roles
Automated Access Reviews
Keeping track of access permissions across multiple SaaS apps can be overwhelming. CloudEagle automates access reviews, helping organizations verify and remove unnecessary privileges periodically.
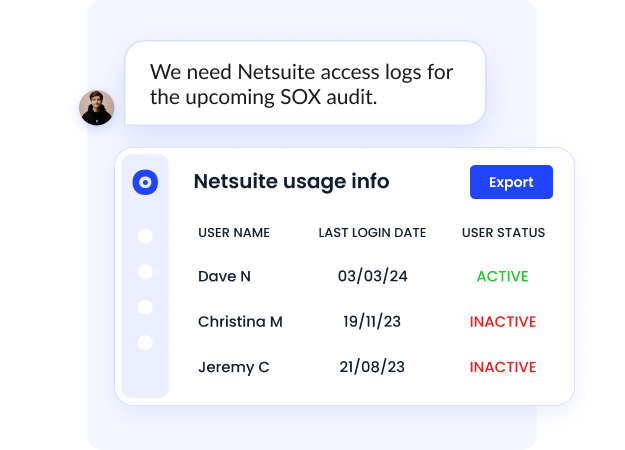
Key advantages include:
- Real-time visibility into user identities and access rights
- Audit-ready logs for auditors and compliance reporting (SOC2, SOX)
- Prevention of unauthorized access or lingering permissions
- Streamlined management of movers, ensuring role changes are reflected accurately
License Harvesting and Optimization
Unused or underutilized licenses often result in wasted SaaS spend. CloudEagle automatically tracks license usage and reclaims licenses when employees move roles or leave, optimizing software investment.
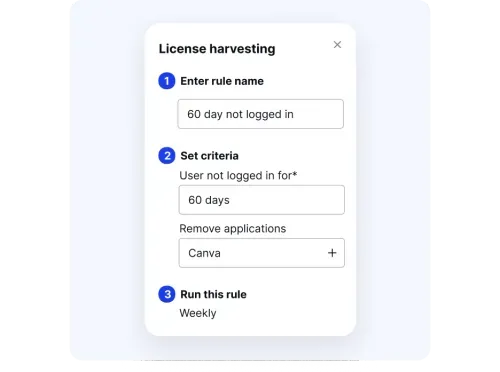
Benefits include:
- Reduction of unnecessary SaaS spend by 10–30%
- Automatic reclamation of licenses without manual intervention
- Better control over resources and access permissions
- Increased operational efficiency and reduced administrative workload
Read the full RingCentral case study to see how CloudEagle.ai saved $1.2M by harvesting unused licenses.
Full Visibility Across SaaS Apps and Spend
CloudEagle has 500+ integrations with SaaS platforms, providing full visibility into applications, usage patterns, and spend.
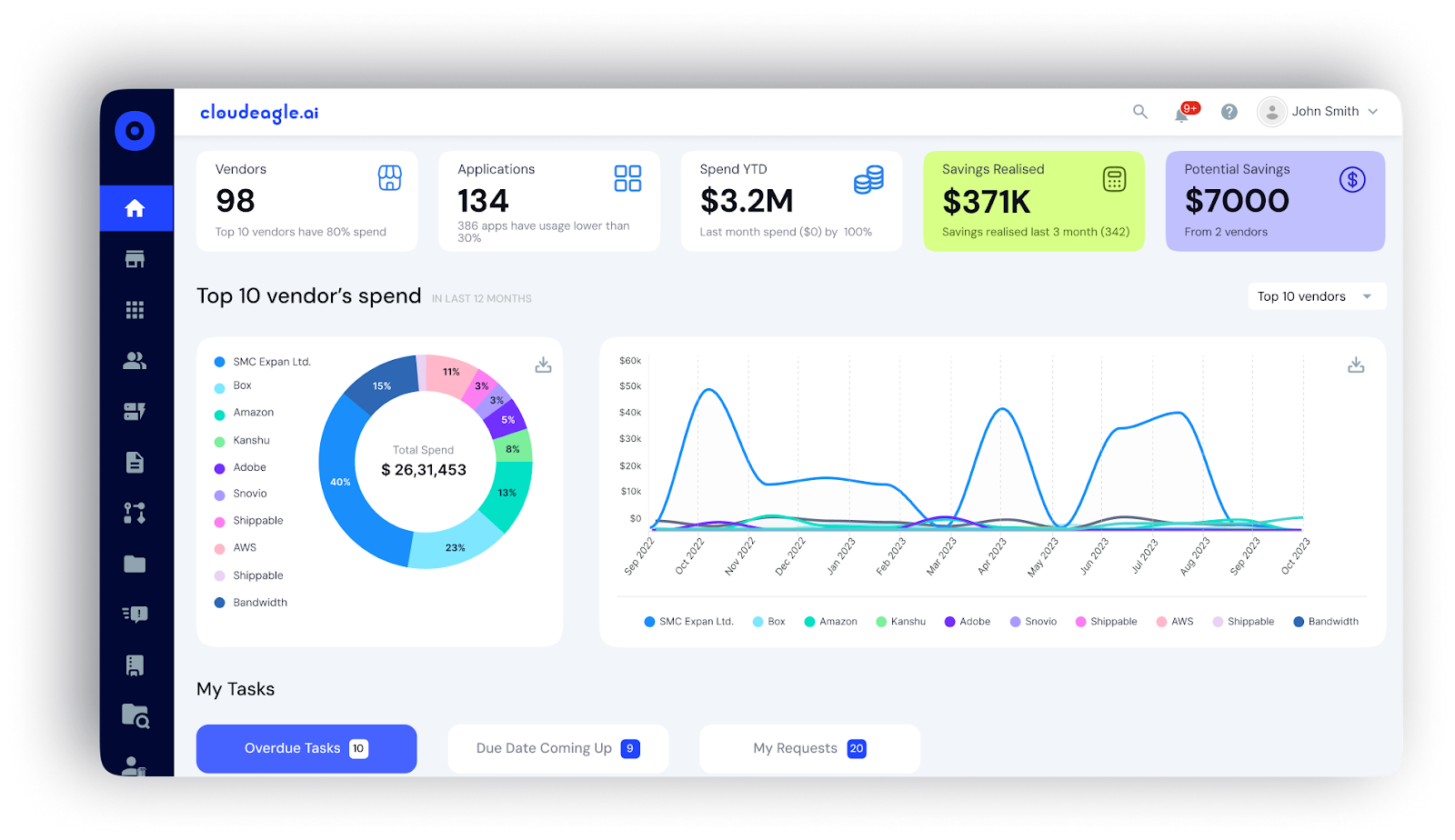
IT and procurement teams can:
- Detect duplicate or unused apps
- Monitor users' access and ensure proper privileges
- Make data-driven decisions for renewals and vendor negotiations
- Prevent overspending and optimize SaaS utilization
Impact of CloudEagle.ai on the JML Process
By automating the Joiner-Mover-Leaver process, CloudEagle delivers measurable improvements across security, efficiency, and spend:
- Up to 80% reduction in time spent on manual onboarding and offboarding workflows
- 10–30% savings on SaaS spend through license optimization and reclamation
- Full visibility into user identities, access rights, and resources, strengthening access management
- Reduced security risks and unauthorized access incidents
- Audit-ready logs for simplified compliance reporting and regulatory adherence
Final Thoughts
The Joiner-Mover-Leaver (JML) process is vital for managing user identities, access rights, and resources efficiently, ensuring operational efficiency, compliance, and lower security risks.
Automated workflows for joiners, movers, and leavers prevent unauthorized access, reduce human error, and streamline onboarding and offboarding, while regular access reviews strengthen identity governance.
CloudEagle.ai simplifies the entire JML process with AI-driven automation, centralized visibility, and real-time access management, helping organizations save time, reduce risks, and optimize SaaS spend.
Take control of your employee lifecycle management today. Book a free demo with CloudEagle.ai and experience seamless automation.
Frequently Asked Questions
1: What is the joiners movers and leavers policy?
A policy that defines how organizations manage joiners, movers, and leavers, ensuring proper access, resources, and security throughout the employee lifecycle.
2: What is the joiner mover leaver lifecycle?
The JML lifecycle tracks an employee’s journey: joiners get access provisioned, movers have roles and permissions updated, and leavers have access revoked securely.
3: What is the difference between offboarding and onboarding?
Onboarding provides new employees access, tools, and resources; offboarding revokes access, retrieves assets, and secures sensitive data when employees leave.
4: What are the 5 stages of the onboarding process?
The 5 stages: Preboarding, Orientation, Training, Integration, and Feedback & Support, ensuring smooth transition and employee readiness.
5: What are the 5 C's of onboarding?
The 5 C's: Compliance, Clarification, Culture, Connection, and Check-back, guiding employees to adapt, comply, and engage effectively.

%201.svg)









.avif)




.avif)
.avif)




.png)









