HIPAA Compliance Checklist for 2025

Enterprises are running 300+ SaaS applications on average.
Yet most compliance programs still treat SOC 2, GDPR, and HIPAA as separate silos.
That’s exactly where risk multiplies.
The same SaaS app can store customer data, employee data, and health information at the same time. If your controls are fragmented, your compliance posture is too.
In this guide, you’ll learn how to build a unified SOC 2, GDPR, and HIPAA checklist, what breaks at scale, and how to operationalize multi-framework compliance across your SaaS stack.
TL;DR
- Most SaaS apps fall under multiple compliance frameworks simultaneously.
- Separate SOC 2, GDPR, and HIPAA processes create gaps.
- A unified SaaS governance framework strengthens audit readiness.
- Access governance is the most common multi-framework failure point.
- CloudEagle.ai operationalizes SaaS compliance controls across all frameworks.
1. What Is a Multi-Framework SaaS Compliance Checklist?
A multi-framework SaaS compliance checklist is a structured control system that maps one set of operational controls across multiple regulations such as SOC 2, GDPR, and HIPAA.
Instead of running three parallel compliance efforts, you align shared requirements like:
- Access control
- Data classification
- Audit logging
- Vendor oversight
- Evidence collection
This approach reduces duplication and strengthens SaaS risk management across the entire environment.
A unified checklist turns compliance from reactive audit preparation into a repeatable operating model embedded in your SaaS governance framework.
2. Why Enterprises Need a Unified Compliance Checklist
As SaaS environments scale, framework-specific controls break down. Here’s why.
A. Same SaaS Apps Fall Under Multiple Frameworks
One SaaS tool can simultaneously trigger:
- SOC 2 security and availability requirements
- GDPR data protection obligations
- HIPAA safeguards for protected health information
For example:
- Salesforce may store customer data regulated by GDPR.
- Workday can process employee data tied to SOC 2 controls.
- Google Workspace might store PHI if used in healthcare contexts.
If these apps are governed independently, your controls drift.
Multi-framework exposure is the norm, not the exception. Unified oversight reduces blind spots.
B. Manual Audits Do Not Scale With SaaS Sprawl
When compliance teams manage frameworks separately, they often duplicate:
- Access reviews
- Vendor assessments
- Evidence collection
- Control documentation
In an environment with hundreds of SaaS apps, this becomes unmanageable.
Manual audits cannot keep pace with SaaS growth. Framework fragmentation increases operational overhead and audit fatigue.
C. Access Changes Silently Break Compliance
Access governance is where most multi-framework failures occur.
When:
- Employees change roles
- Contractors are onboarded
- Employees leave
- Admin privileges expand
Compliance breaks quietly.
According to CloudEagle's 2025 IGA Report, 48% of former employees still have app access months after leaving, one of the top SaaS compliance risks that crosses all regulatory frameworks.
Without automated identity controls, SOC 2, GDPR, and HIPAA safeguards degrade over time.
3. How Can You Build a SOC 2, GDPR, HIPAA SaaS Compliance Checklist?
A multi-framework checklist is not about doing more.
It’s about enforcing the right SaaS compliance controls once and mapping them across frameworks.
Below is a practical, enterprise-ready checklist that aligns to SOC 2 trust criteria, GDPR accountability principles, and HIPAA safeguards without duplicating effort.
A. Centralized SaaS Inventory With Regulatory Scope
You cannot comply with what you cannot see.
Your SaaS inventory must answer three questions instantly:
- What data does this app process?
- Which regulation applies to it?
- Who owns it internally?
If an auditor asks which applications store EU personal data or PHI, you should not be building that list manually.
Framework overlap:
- SOC 2: Defined system boundaries
- GDPR: Records of processing
- HIPAA: Identification of PHI systems
This is the foundation of your SaaS governance framework.
B. Clear Ownership Beyond Procurement
Compliance fails when apps have no accountable owner.
Every SaaS application must have:
- A business owner is responsible for the necessity
- A technical owner responsible for configuration
- A compliance owner accountable for regulatory alignment
When ownership is unclear, access reviews are skipped, and renewals happen without risk reassessment.
Framework overlap:
All three frameworks require assigned accountability.
C. Enforced Identity and Access Governance
Access is the shared risk layer across SOC 2, GDPR, and HIPAA.
Your checklist should confirm:
- SSO is enforced wherever possible
- Access is role-based, not user-specific
- Admin privileges are limited and monitored
- Offboarding immediately removes access
Former employees retaining SaaS access remains one of the most common multi-framework audit findings.
Framework overlap:
- SOC 2 logical access
- GDPR data minimization
- HIPAA technical safeguards
If access governance is weak, compliance collapses quietly.
D. Risk-Tiered Access Reviews With Evidence
Reviews should not be checkbox exercises.
Instead:
- High-risk or PHI apps are reviewed quarterly
- Admin access reviewed separately
- Reviews are documented with a timestamp and approver
The control is not the review.
The control is the evidence.
Across all frameworks, missing documentation equals missing compliance.
E. Vendor Compliance Validation
Your SaaS vendor becomes part of your compliance boundary.
Before and during use, confirm:
- Valid SOC 2 or equivalent report
- GDPR Data Processing Agreement in place
- HIPAA Business Associate Agreement, where required
Vendor compliance must be re-validated periodically, not assumed indefinitely
F. Logging, Monitoring, and Retention Controls
Multi-framework alignment requires:
- Admin and configuration logging enabled
- Defined data retention periods
- Centralized log retention
- Breach escalation workflows aligned to regulatory timelines
Compliance does not only require prevention. It requires traceability.
G. Continuous Evidence and Audit Readiness
If compliance only activates during audit season, it is already broken.
Your checklist should ensure:
- Evidence for access reviews is continuously stored
- Vendor documentation is centrally maintained
- Inventory and regulatory scope are always current
Compliance must operate continuously inside your SaaS risk management model.
4. Where Multi-Framework Compliance Commonly Breaks?
Multi-framework compliance rarely fails because policies are missing.
It fails because SaaS environments move faster than controls.
Here are the three most common breakpoints.
A. Shadow SaaS Storing Regulated Data
A single unsanctioned app can expand your regulatory scope overnight.
When employees adopt tools outside IT:
- EU personal data may fall under GDPR without safeguards
- PHI may be stored without a Business Associate Agreement
- The app may sit outside your SOC 2-defined system boundary
The risk is not the tool.
The risk is unreviewed data flowing into it.
CloudEagle's research shows that 60% of enterprise SaaS and AI applications now operate outside IT's visibility, creating silent compliance exposure across multiple frameworks.
B. Former Employees Retaining Access
Access drift silently breaks compliance.
When offboarding is manual:
- Accounts remain active
- Admin privileges persist
- Audit logs become fragmented
This single issue can trigger findings across SOC 2 logical access controls, GDPR security of processing, and HIPAA technical safeguards.
It is one of the most common and preventable audit failures.
C. Compliance Treated as an Annual Exercise
Many enterprises prepare for audits once a year. But SaaS environments change daily.
New users. New integrations. New data flows.
If compliance only activates during audit season:
- Inventories are outdated
- Access reviews are rushed
- Evidence is reconstructed retroactively
Across frameworks, documentation gaps quickly become control gaps.
5. How CloudEagle.ai Enables Unified SaaS Compliance
Most enterprises already know what multi-framework compliance requires.
The real challenge is enforcing those SaaS compliance controls continuously across hundreds of apps, users, and AI tools.
CloudEagle.ai turns fragmented, manual identity governance into automated, AI-driven enforcement across your entire SaaS ecosystem.
A. Eliminates Shadow IT and Access Blind Spots
A large portion of SaaS and AI tools operate outside IT visibility, creating silent compliance exposure.
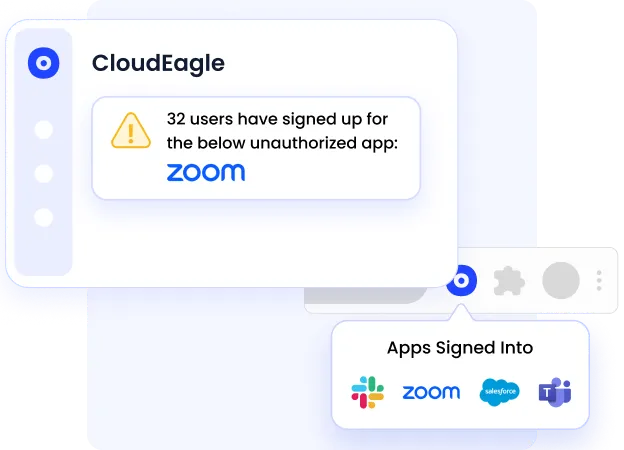
CloudEagle continuously discovers unsanctioned tools through:
- SSO integrations
- Finance and expense data
- Browser activity signals
Once identified, risky apps are routed into automated remediation workflows through Slack, email, or ticketing systems.
For SOC 2, GDPR, and HIPAA, visibility defines scope.
CloudEagle ensures your SaaS inventory reflects reality, not assumptions.
B. Automates Continuous Access Reviews and Zero Trust Enforcement
Quarterly access reviews cannot keep pace with SaaS change.
CloudEagle enables AI-powered, continuous access reviews that:
- Flag excessive privileges in real time
- Revoke unused or risky access
- Enforce just-in-time and time-bound provisioning
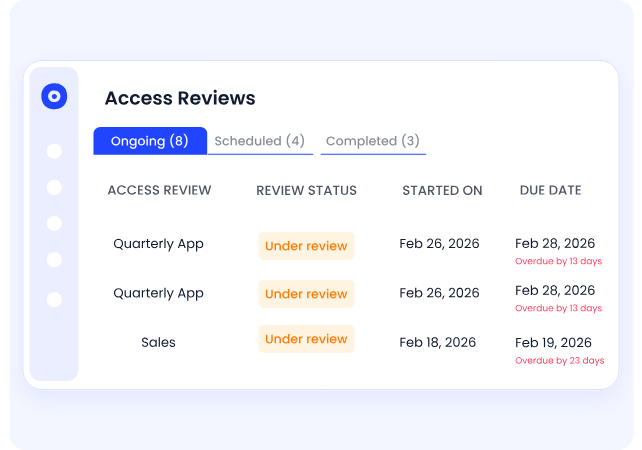
This reduces privilege creep and strengthens:
- SOC 2 logical access controls
- GDPR data minimization principles
- HIPAA technical safeguards

Access governance becomes proactive, not audit-driven.
C. Zero-Touch Onboarding and Offboarding Across 500+ Apps
Manual provisioning creates drift.
CloudEagle automates onboarding and offboarding across more than 500 SaaS applications, including tools outside traditional identity providers.

This ensures:
- New users receive only role-appropriate access
- Departing employees are immediately deprovisioned
- Orphaned accounts are eliminated
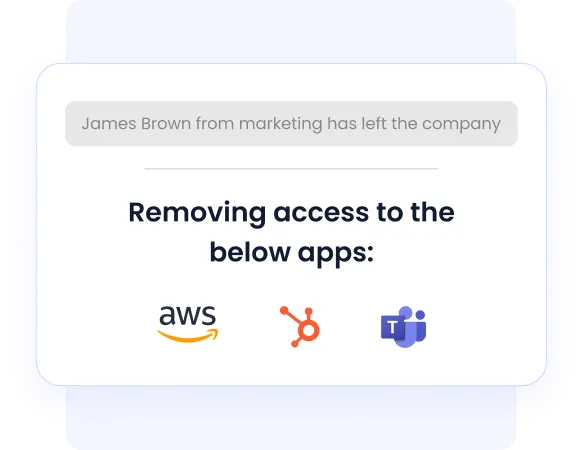
Organizations report significant reductions in audit preparation time because evidence is generated automatically, not reconstructed later.
D. Centralized Compliance Reporting and Audit Evidence
Unified compliance requires unified visibility.
CloudEagle provides a centralized dashboard showing:
- Who has access
- When access was granted
- Who approved it
- Whether it remains necessary
SOC 2–ready audit logs can be exported instantly, reducing last-minute audit scrambles.

Compliance reporting shifts from reactive to continuous.
E. AI-Augmented Identity Scoring and Risk Detection
CloudEagle applies AI-driven identity scoring to detect:
- Risky users
- Anomalous access behavior
- Excessive permissions
- Sensitive tool exposure
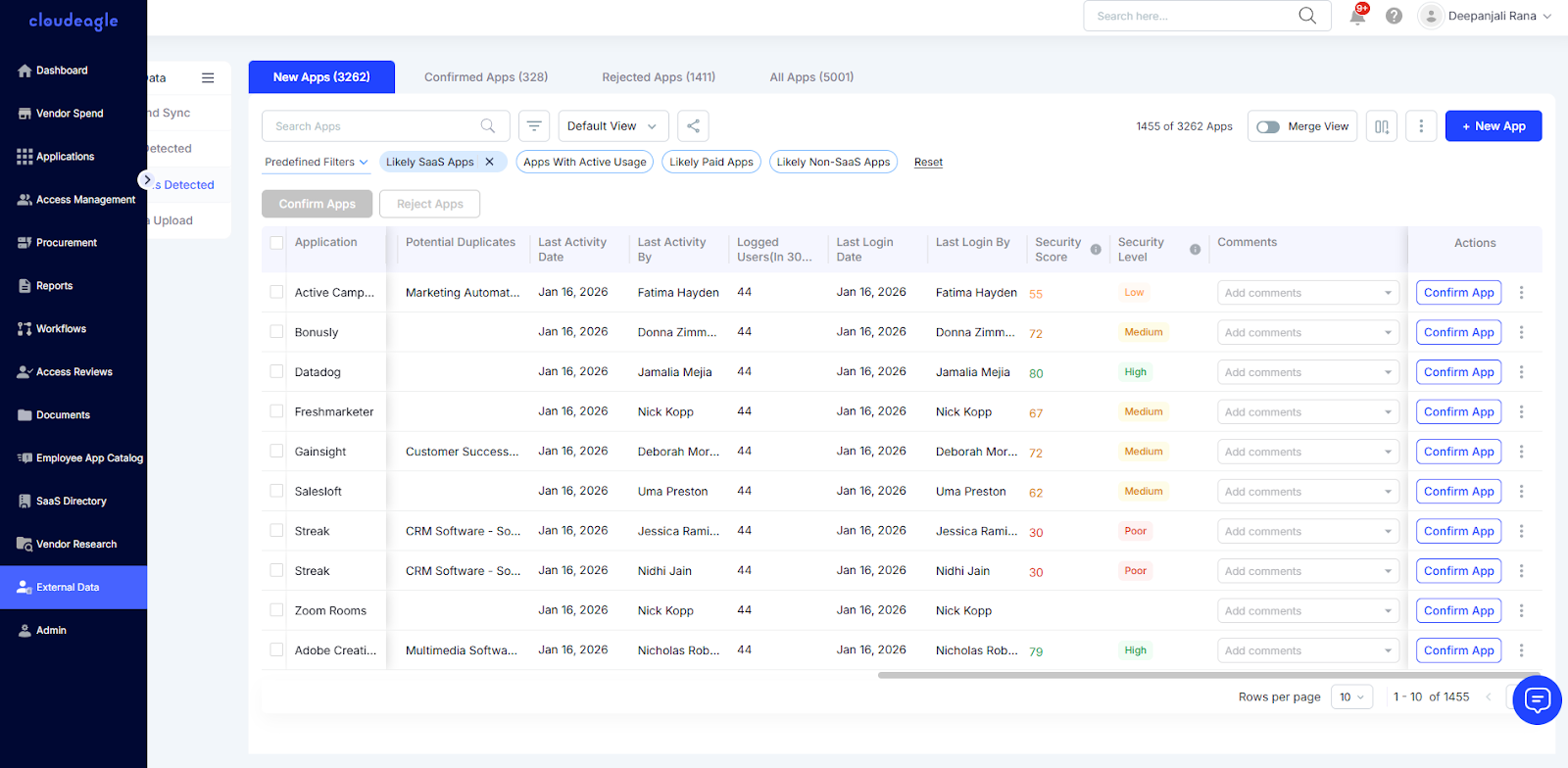
It also enforces policy-based controls for high-risk AI applications, such as:
- ChatGPT
- Midjourney
Given that nearly half of former employees in many organizations retain SaaS access post-departure, automated risk detection and deprovisioning are critical for multi-framework compliance.
CloudEagle customers have saved over $2B in software costs while simultaneously strengthening compliance controls, proving that governance and cost optimization are not competing priorities.
In a Nutshell
Enterprises no longer operate within a single regulatory boundary. The same SaaS application can trigger SOC 2 controls, GDPR obligations, and HIPAA safeguards at the same time. Managing them separately increases risk, duplication, and audit fatigue.
A unified checklist simplifies this complexity. By centralizing inventory, enforcing access governance, validating vendors, and continuously capturing evidence, enterprises strengthen SaaS risk management without multiplying processes.
CloudEagle.ai operationalizes this unified approach by automating discovery, access reviews, and compliance reporting across all SaaS and AI tools. Instead of preparing for audits once a year, organizations stay continuously audit-ready.
Book a free demo to see how unified SaaS compliance becomes enforceable, not theoretical.
Frequently Asked Questions
- What are the types of frameworks?
Common frameworks include SOC 2, GDPR, HIPAA, ISO 27001, and NIST, each defining controls for security and data protection.
- What is an example of a checklist?
A SaaS checklist may include inventory tracking, access reviews, vendor validation, logging, and audit evidence retention.
- What is a compliance checklist?
A compliance checklist lists required controls and processes to meet regulatory or framework obligations.
- What is the SaaS governance model?
A SaaS governance model defines how apps are discovered, approved, accessed, reviewed, and renewed.
- What are the 4 P's of governance?
The 4 P’s are People, Process, Policy, and Platform, working together to enforce governance.

%201.svg)










.avif)




.avif)
.avif)




.png)









