HIPAA Compliance Checklist for 2025

On paper, SaaS compliance often looks fine.
Vendors have certifications. Policies exist. Audits are passed. Reports are filed.
But real SaaS environments don’t stay still.
Every month, new tools are added. Employees sign up for apps without telling IT. Integrations connect systems silently. Access grows, permissions pile up, and ownership gets blurry.
This is where poor SaaS compliance becomes risky. Not because teams don’t care, but because visibility disappears faster than anyone expects.
The most dangerous SaaS compliance risks don’t trigger alerts. They sit quietly in the background until an audit fails, a breach happens, or a regulator starts asking uncomfortable questions.
TL;DR
- SaaS compliance often looks fine on paper but breaks down in fast-changing, SaaS-heavy environments.
- Hidden risks live in unmanaged access, shadow IT, and inconsistent policy enforcement.
- Poor SaaS compliance directly increases security and data breach risks through over-permissioned accounts and blind data flows.
- Traditional audit-driven compliance can’t keep up with decentralized SaaS adoption and constant change.
- Continuous visibility and governance, enabled by platforms like CloudEagle.ai, are critical to reducing SaaS compliance and security risks.
1. What Are You Missing When You Think Your SaaS Is “Mostly Compliant”?
Poor SaaS compliance usually isn’t caused by negligence. It’s caused by lack of visibility and fragmented ownership.
a. Access Sprawl You Can’t Fully Explain
Every SaaS app creates users, roles, and permissions. Over time, people change roles, teams restructure, vendors come and go, but access rarely gets cleaned up properly.
Former employees still have accounts. Contractors retain access long after projects end. Admin privileges get handed out “temporarily” and never revoked.
When auditors ask a simple question like “Who has access to sensitive data and why?”, many teams struggle to answer with confidence.
This is one of the most common SaaS compliance risks. And it directly impacts access control, least privilege, and access review requirements.
b. Shadow IT That Compliance Never Sees
Shadow IT compliance risks are no longer limited to obscure tools. Teams now use well-known SaaS apps without IT approval, often signing up with company email addresses and syncing real business data.
From a compliance perspective, these apps might as well not exist.
No vendor review. No data classification. No access controls. No idea where sensitive information is being stored or shared.
When organizations don’t actively discover and monitor shadow SaaS, they lose control of their compliance perimeter without even realizing it.
c. Policies That Look Good but Aren’t Enforced
Most companies have security and compliance policies. The problem is enforcement across SaaS tools.
One app enforces MFA strictly. Another makes it optional. Some apps have audit logs enabled, others don’t. Data retention settings vary widely across the stack.
This inconsistency creates serious SaaS governance risks. Compliance becomes uneven, and security gaps form in the places teams least expect.
2. How Does Poor SaaS Compliance Quietly Increase Security and Breach Risk?
SaaS compliance and SaaS security risks are tightly linked.
When compliance is weak, attackers don’t need sophisticated zero-day exploits. They simply exploit what already exists.
And when regulators or auditors investigate, the same weaknesses that enabled the breach often trigger audit failures.
a. Over-Permissioned Accounts Become Easy Targets
Most SaaS breaches don’t start with malware. They start with valid credentials.
When users have more access than they need, compromised accounts cause far more damage. Admin roles, broad OAuth permissions, and long-lived API tokens give attackers exactly what they want.
Without regular access reviews and centralized visibility, these risks stay hidden.
This makes maintaining SaaS data security compliance nearly impossible, especially for regulated data like customer records, financial information, or employee data.
b. No Clear View of Where Data Is Flowing
Data moves constantly between SaaS tools. Files are shared externally. Records sync automatically. AI features pull data into models.
Poor SaaS compliance means teams don’t know which apps hold sensitive data, which integrations access it, or who outside the organization can see it.
When a data exposure happens, response teams scramble to figure out scope and impact. That delay increases regulatory risk, legal exposure, and reputational damage.
c. Security Signals Get Missed
Many SaaS apps generate logs and alerts. But when compliance is fragmented, logs aren’t centralized or reviewed consistently.
Suspicious logins blend in. Unusual access patterns go unnoticed. Incidents are detected late, if at all.
From both a security and compliance standpoint, this is a serious failure. Monitoring and incident readiness are core requirements, yet SaaS environments often lack them in practice.
d. Audit Failures Become Inevitable — Not Accidental
Here’s the major risk leaders underestimate:
Poor SaaS compliance doesn’t just increase breach likelihood. It almost guarantees recurring audit findings.
Common SaaS-related audit failures include:
- Incomplete or outdated SaaS inventories
- Lack of documented app owners
- Inconsistent access review evidence
- Delayed deprovisioning timelines
- No formal third-party app approval process
Auditors now expect evidence of continuous control execution, not policies stored in a shared drive.
When organizations cannot produce automated, time-stamped proof of reviews and access changes, findings repeat year after year.
Recurring audit exceptions erode board confidence and increase scrutiny in future audits.
e. Breach Impact Multiplies Due to Hidden Exposure
In poorly governed SaaS environments, blast radius is rarely contained.
Because apps are interconnected:
- A compromised Google account exposes downstream SaaS apps
- A breached HR tool reveals payroll, identity, and benefits data
- A leaked API token provides backend system access
Without centralized SaaS visibility, organizations don’t understand how deeply integrated their ecosystem is until after an incident.
This is where breach impact multiplies:
- Broader data exposure
- Higher regulatory penalties
- Increased cyber insurance scrutiny
- Longer remediation timelines
In short, weak SaaS compliance creates invisible compounding risk.
The real danger isn’t one missed access review.
It’s the systemic lack of visibility that allows risk to scale silently — until either attackers or auditors expose it.
3. Why Do Traditional Compliance Programs Break Down in SaaS-First Companies?
Most compliance programs weren’t designed for SaaS-first organizations.
a. SaaS Buying Is Decentralized by Design
Teams buy tools directly to move faster. Marketing, sales, HR, and finance don’t wait for long approval cycles anymore.
Traditional compliance assumes centralized control. SaaS operates on distributed ownership.
Without a modern SaaS governance approach, no single team has full visibility. Security owns policies. IT manages integrations. Finance sees spending. Legal reviews contracts. None of them see the whole picture.
b. SaaS Changes Too Fast for Periodic Audits
SaaS environments change daily. Users are added. Permissions change. Integrations appear overnight.
Annual or quarterly audits can’t keep up. By the time a review finishes, the environment has already shifted.
This constant gap between reality and documentation is why SaaS compliance risks keep growing even in mature organizations.
4. How Can Teams Regain Control Without Slowing the Business? Where CloudEagle.ai Fits In
In today’s SaaS- and AI-heavy enterprise environments, regaining control doesn’t mean throttling innovation, it means enabling it safely. This is exactly where CloudEagle.ai becomes a strategic ally, delivering continuous, AI-powered SaaS governance that adapts to how modern businesses operate.
Continuous SaaS Visibility and Shadow IT Discovery
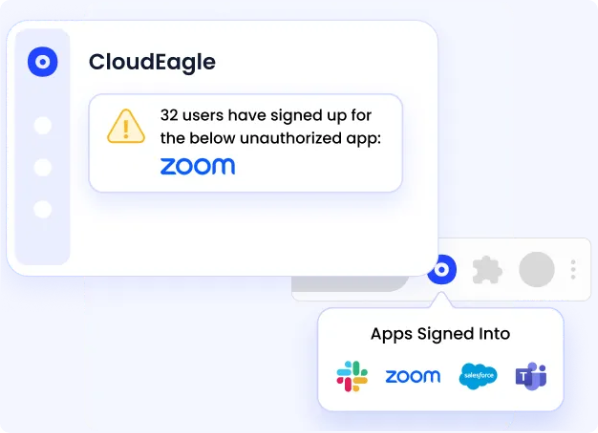
CloudEagle.ai offers a unified, real-time view across all SaaS applications, including those outside IT's purview, so called Shadow IT. It detects unsanctioned tools via login data (SSO, browser, and card transactions), then cross-verifies them against financial systems to highlight risky, duplicate, or unnecessary tools. Shadow IT reports can be generated automatically, and built-in workflows (Slack, email) let you act quickly.
📊 60% of SaaS apps operate outside IT's visibility, making discovery essential.
Streamlined Access Reviews & Least Privilege Enforcement
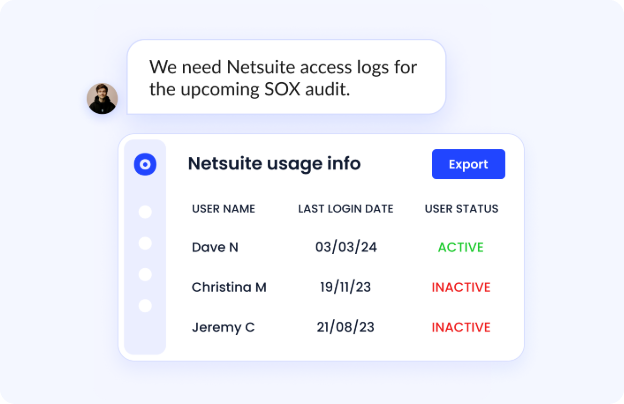
CloudEagle automates access reviews and risk-based deprovisioning across your SaaS environment. You can enforce time-bound access for contractors, identify privilege creep, and run SOC2-ready access reviews on autopilot. Unlike quarterly, manual audits, CloudEagle supports continuous, AI-assisted governance, dramatically reducing risk and compliance effort.
✅ 80% of companies reported incidents tied to privileged access in 2025.
Zero-Touch Provisioning and Smart Offboarding
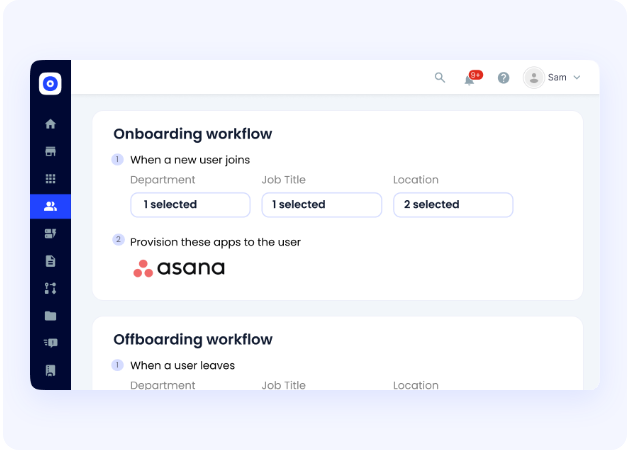
CloudEagle's Zero-Touch Onboarding automatically provisions apps based on employee roles, departments, or locations. It also detects exits from HRIS/ITSM and auto-revokes access, even for tools outside Okta or SailPoint. This ensures day-one productivity and last-day security without delays or gaps.
⚠️ 48% of ex-employees still retain app access post-termination without solutions like CloudEagle.
License Management and Cost Optimization
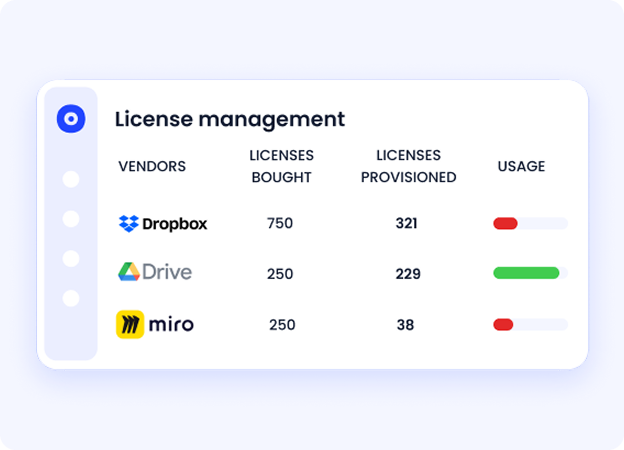
With automated usage tracking and license harvesting, CloudEagle helps identify inactive users, reclaim unused licenses, and downgrade underused subscriptions. It integrates contract data, user provisioning, and deep usage metrics to drive real-time SaaS cost savings, typically 10–30% annually.
AI Tool Governance
As AI tools proliferate, CloudEagle extends governance to employee-adopted AI apps like ChatGPT and Midjourney, flagging unapproved usage and policy violations. With dedicated dashboards and DLP-integrated workflows, organizations can enjoy AI productivity without introducing compliance and data leakage risks.
5. What’s the Real Cost of Ignoring SaaS Compliance Risks?
When SaaS compliance fails, the impact isn’t theoretical.
Regulatory audits take longer and cost more. Security incidents become harder to contain. Vendor negotiations weaken when gaps surface late. Trust with customers and partners erodes quickly.
Most damaging of all, teams spend months reacting to problems that could have been prevented with better visibility and governance.
Frequently Asked Questions
1. What are the biggest risks of poor SaaS compliance?
The biggest SaaS compliance risks include uncontrolled access, shadow IT usage, inconsistent security policies, limited visibility into data movement, and ongoing vendor compliance drift.
2. How does poor SaaS compliance impact security?
Poor SaaS compliance increases SaaS security risks by allowing excessive permissions, unmanaged identities, weak monitoring, and uncontrolled integrations, all of which expand the attack surface.
3. Why is SaaS governance critical for compliance?
SaaS governance ensures consistent access controls, policy enforcement, and risk management across all applications. Without it, compliance efforts remain fragmented and reactive.
4. How does shadow IT increase SaaS compliance risks?
Shadow IT increases SaaS compliance risks by introducing unapproved applications that store and process company data without security reviews, access controls, or monitoring.
5. What is the best way to manage SaaS compliance at scale?
The most effective way to manage SaaS compliance at scale is through continuous SaaS risk management. This includes discovering all SaaS applications, monitoring user access and permissions, enforcing consistent security policies.

%201.svg)








.avif)




.avif)
.avif)




.png)









