HIPAA Compliance Checklist for 2025

More than 70% of employees admit to using SaaS applications that IT has never approved. That single data point explains why Shadow IT has become one of the hardest problems for security, compliance, and IT teams to control today.
This isn’t because employees are reckless. It’s because SaaS has changed how work happens. Anyone can sign up, invite teammates, upload data, and start working in minutes. Governance, on the other hand, still moves at enterprise speed.
That gap is where Shadow IT grows. Quietly. Persistently. And dangerously.
Organizations that continue to treat Shadow IT as a visibility issue will always be reacting. The ones that move toward Zero Trust SaaS, backed by continuous SaaS security governance and SaaS access management, are the ones that actually get ahead of risk.
TL;DR
- Shadow IT has become a permanent SaaS risk as teams adopt tools faster than governance can keep up.
- Most SaaS and AI tools enter organizations without ownership, access reviews, or security validation.
- Unmanaged SaaS access is now a leading cause of data exposure and audit failures.
- Zero Trust SaaS shifts access control from one-time approval to continuous verification.
- CloudEagle.ai enables continuous SaaS governance by unifying Shadow IT discovery, access control, and spend visibility.
Step 1: Understand Why Shadow IT Exists in Your Organization
Shadow IT does not exist because policies are ignored. It exists because policies are misaligned with how teams actually work.
A. Business speed consistently outpaces IT and security workflows
- Teams are measured on delivery timelines, not governance adherence
- Procurement and security reviews often take weeks
- SaaS tools can be adopted in under 10 minutes
When faced with deadlines, employees choose progress over process. Gartner predicts that by 2027, 75% of employees will acquire or modify technology outside IT visibility, making Shadow IT a structural reality, not an exception.
B. SaaS removes the friction that governance depends on
- Free trials eliminate budget approvals
- Subscription pricing avoids capital expenditure reviews
- Browser-based access requires no admin rights
Traditional SaaS security governance assumed centralized control. SaaS adoption has made decentralization the default.
C. Lack of clarity around approved tools and access ownership
- Employees do not know which apps are sanctioned
- Managers assume access is already reviewed
- IT lacks a real-time view of the SaaS stack
When SaaS access management is unclear, Shadow IT becomes the easiest path forward.
Step 2: Identify How Shadow IT Enters Your SaaS Environment
Shadow IT enters through predictable, repeatable paths. Understanding these paths is critical before applying Zero Trust SaaS controls.
A. Teams adopting SaaS tools without formal approval
- Team leads purchase tools to solve immediate problems
- Access is granted via email invites instead of IAM workflows
- No owner is accountable for security or compliance
CSO Online reports that over 80% of employees use at least one SaaS app not explicitly approved by IT, creating massive blind spots across the organization.
The risk compounds quickly:
- Access spreads laterally
- Permissions are rarely reviewed
- Data moves outside monitored systems
This is how Shadow IT scales silently.
B. Free trial is turning into along-term paid application
- Employees sign up for trials without reviews
- Tools become embedded in daily workflows
- Auto-Renewals convert trials into production systems
Industry research shows nearly 30% of enterprise SaaS applications started as free trials. These apps often lack owners, documentation, or access reviews, making them persistent Shadow IT risks.
C. AI-driven tools accelerating unsanctioned adoption
- Employees upload sensitive data into AI tools
- AI platforms bypass traditional DLP controls
- Data usage policies are unclear or undefined
Step 3: Assess the Security and Compliance Risks Created by Shadow IT
Once Shadow IT enters your SaaS environment, risk does not stay localized. It spreads horizontally across users, data, and access paths, often without triggering any immediate alarms.
The danger of Shadow IT is not just that tools are unknown. It’s that access and data move without governance, creating risks that only surface when it’s too late.
A. Sensitive data shared through unmanaged SaaS apps
Most Shadow IT risk starts with data movement, not malware or exploits.
In real SaaS environments:
- Employees upload customer data into productivity tools
- Contracts and financial documents are shared externally
- Internal credentials and API keys are stored in unsecured apps
Without SaaS security governance, data leaves controlled environments silently.
B. Compliance gaps that surface only during audits
Shadow IT almost never triggers compliance alarms in real time. It shows up during audits.
Common audit failures include:
- Incomplete access reviews because unknown apps are excluded
- Inability to prove least privilege
- Missing ownership for access controls
According to audit advisory data, nearly 25 percent of failed SOC 2 and ISO 27001 access controls are tied directly to unmanaged SaaS applications.
C. Increased exposure from uncontrolled SaaS access
Access risk is where Shadow IT becomes dangerous.
Typical scenarios include:
- Former employees retaining access to tools that IT never tracked
- Contractors accumulating permissions across multiple apps
- Privileged access is going unreviewed for months
CloudEagle’s IGA analysis shows that 1 in 4 SaaS users retains access they no longer need after a role change, creating persistent identity risk.
Shadow IT risks are ultimately access risks.
Step 5: Define What Zero Trust Looks Like for SaaS Applications
Zero Trust SaaS is not a philosophy. It is an operating model for how access decisions are made in dynamic SaaS environments.
Traditional models assume access is static. SaaS reality proves it is not.
A. Access is verified continuously, not granted permanently
In most organizations, access is granted once and trusted indefinitely.
Zero Trust SaaS changes this by:
- Treating access as temporary, not permanent
- Revalidating permissions based on context
- Triggering reviews when risk changes
This matters because:
- Roles evolve faster than access policies
- Long-standing access becomes outdated
- Shadow IT access persists without challenge
Continuous verification limits how long Shadow IT risks can exist unnoticed.
B. Permissions are aligned to roles and actual usage
Over-permissioning is one of the biggest contributors to SaaS risk.
Zero Trust SaaS enforces:
- Role-based access aligned to job function
- Usage-based entitlement reviews
- Removal of dormant or unused permissions
CloudEagle IGA benchmarks show organizations that right-size access using usage data reduce overall SaaS security exposure by over 35 percent within six months.
This turns SaaS access management from assumption-driven to evidence-driven.
C. Access decisions consider both identity and behavior
Identity alone is no longer sufficient.
Zero Trust SaaS evaluates:
- Login patterns and locations
- Frequency and depth of usage
- Abnormal behavior compared to baseline
When behavior deviates, trust is reduced automatically.
This makes Shadow IT risks visible before they escalate into incidents.
Step 6: Discover All SaaS Applications and Access Points
Discovery is not a one-time exercise. It is the foundation of sustainable SaaS security governance.
You cannot govern what you cannot see, and most organizations are flying blind.
A. Identify sanctioned and unsanctioned SaaS applications
Shadow IT hides across multiple channels:
- Expense systems reveal card-based purchases
- SSO logs show unmanaged authentication
- Browser activity exposes direct signups
Gartner estimates that enterprises underestimate their SaaS footprint by 40–50 percent, meaning nearly half of their SaaS environment operates outside governance.
B. Map users, access levels, and entitlements
Knowing an app exists is not enough.
Effective discovery also answers:
- Who has access
- What level of access do they have
- Whether access is justified
This includes:
- Admin and super-user roles
- Shared and service accounts
- External collaborators
Without this mapping, SaaS access management remains superficial.
C. Establish a baseline of SaaS usage
Baselines create context.
They help teams understand:
- Normal usage patterns
- Expected access behavior
- Early indicators of risk
Once a baseline exists, new Shadow IT stands out immediately instead of blending in.
Step 7: Enforce Zero Trust Controls Across Your SaaS Stack
Visibility without enforcement creates a false sense of security.
Zero Trust SaaS only works when controls are applied consistently across all applications.
A. Apply least privilege access across all SaaS apps
Least privilege reduces risk by design.
This includes:
- Removing default admin access
- Limiting sensitive actions
- Enforcing role-based permissions
When Shadow IT exists, least privilege minimizes damage.
B. Remove access automatically when roles change
Manual access removal does not scale.
Zero Trust SaaS relies on:
- HR-driven lifecycle automation
- Immediate deprovisioning on exit
- Automatic access adjustment on transfers
CloudEagle IGA data shows organizations that automate deprovisioning reduce access-related audit findings by over 40 percent.
This is one of the highest-impact governance actions.
C. Monitor SaaS usage continuously
SaaS environments change daily.
Continuous monitoring helps:
- Identify dormant accounts
- Detect abnormal behavior
- Surface new Shadow IT tools early
This is how Zero Trust SaaS stays relevant over time.
Step 8: Move from Visibility to Continuous Governance
The biggest mistake organizations make is treating Shadow IT as a cleanup task.
It is not. It is an ongoing condition.
A. Review access and usage on an ongoing basis
Effective governance includes:
- Quarterly or event-driven access reviews
- Usage-based validation of permissions
- Risk-triggered reassessments
This keeps SaaS access management aligned with reality.
B. Align security, IT, and compliance teams
Shadow IT thrives in silos.
Continuous governance requires:
- A shared system of record
- Clear ownership of access decisions
- Coordinated remediation workflows
When teams operate in isolation, Shadow IT persists.
C. Treat SaaS governance as an operating process
Governance must be embedded into daily operations:
- Automated wherever possible
- Measured by outcomes, not effort
- Continuously improved
This is what separates mature SaaS security governance from reactive firefighting.
How CloudEagle.ai Supports the Shadow IT to Zero Trust Journey?
Moving from Shadow IT chaos to Zero Trust SaaS is not a single control or tool change. It requires continuous visibility, identity-aware access enforcement, and governance that extends beyond traditional IAM boundaries.
This is where CloudEagle enables the transformation by unifying discovery, access governance, and spend control into a single operating layer.
A. Identify and Eliminate Shadow IT at Scale
CloudEagle provides real-time visibility into all SaaS and AI applications, whether they are approved, unapproved, or completely unknown to IT.
Instead of relying on one signal, CloudEagle cross-verifies multiple sources to uncover true Shadow IT.
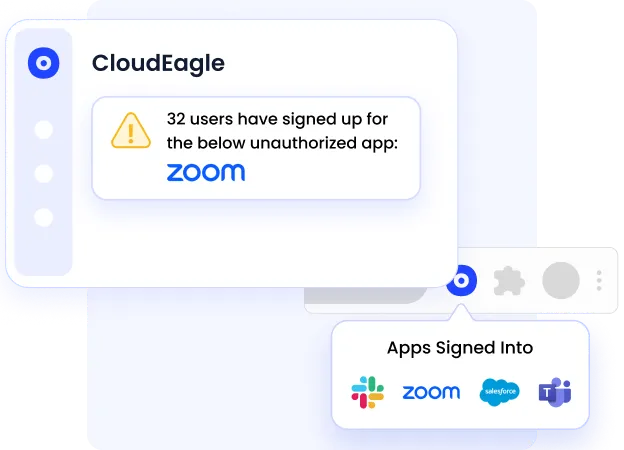
CloudEagle discovers Shadow IT by analyzing:
- SSO and login activity from platforms like Google Workspace and Okta
- Financial data, including corporate cards, invoices, and expense tools
- Browser usage patterns that reveal direct sign-ups and shadow adoption
B. Automate Access Governance and Reduce Risk
Discovery alone does not reduce risk. CloudEagle applies Zero Trust SaaS principles to ensure access is controlled, justified, and continuously reviewed.

CloudEagle enables:
- Role-based access control through employee-facing app catalogs
- Zero-touch provisioning and deprovisioning, even for apps outside SSO
- Time-bound access for contractors, temporary staff, and elevated roles
- Just-in-time (JIT) privileged access to reduce standing permissions
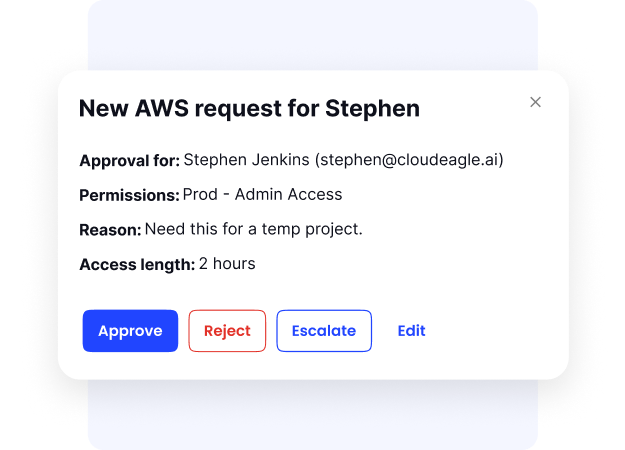
C. Close the Governance Gap Left by Legacy IAM Tools
Traditional IAM platforms like Okta and SailPoint were designed for a world where applications lived behind SSO. That assumption no longer holds true.
CloudEagle extends governance beyond IAM by:
- Discovering and governing apps outside the identity provider
- Automating access workflows where IAM controls do not reach
- Providing SOC 2–ready audit logs and centralized dashboards
D. Reduce Spend and Risk Simultaneously
Zero Trust SaaS is not just a security initiative. It is also a financial control lever.
CloudEagle reduces risk while delivering measurable cost savings by:
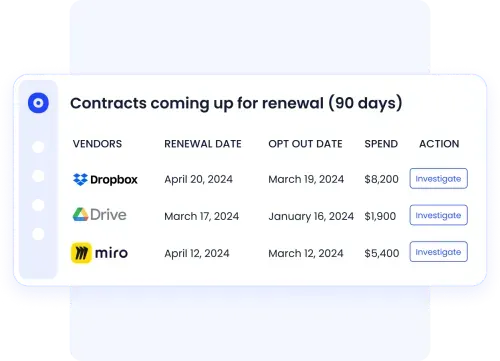
- Automatically reclaiming unused and underutilized licenses
- Identifying duplicate tools using AI-based app categorization
- Preventing surprise renewals through renewal calendars and benchmarks
Organizations using CloudEagle typically achieve:
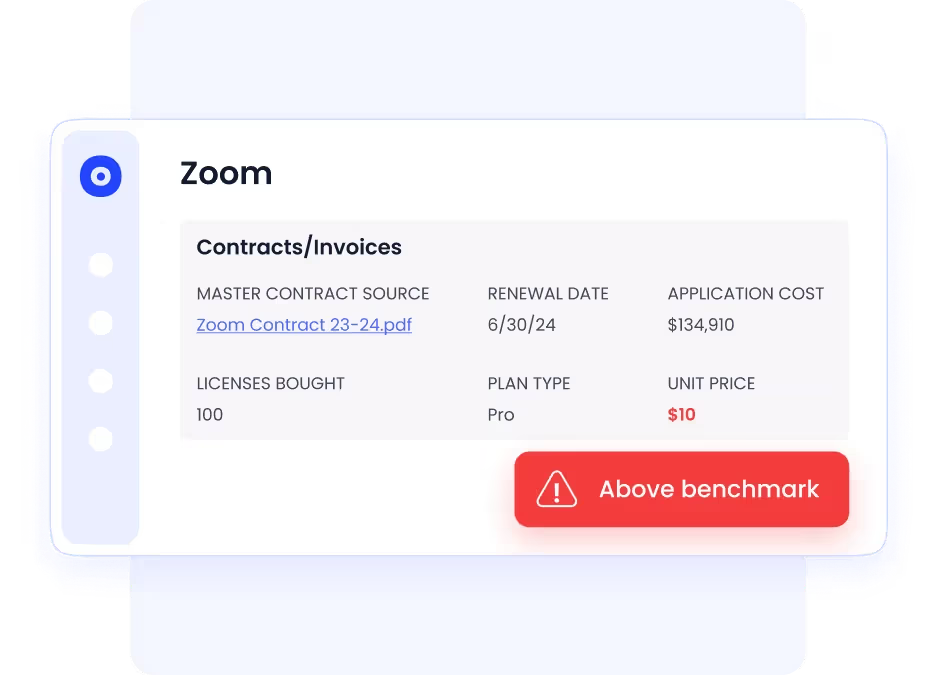
- 10–30% reduction in SaaS spend
- Up to 80% faster compliance preparation
Security improvements and cost optimization happen together, not in tradeoff.
E. Centralize Identity, Access, and Spend Data
CloudEagle acts as a centralized SaaS governance hub by integrating with 500+ platforms, including Okta, Microsoft AD, Netskope, Coupa, Ironclad, Slack, and Jira.
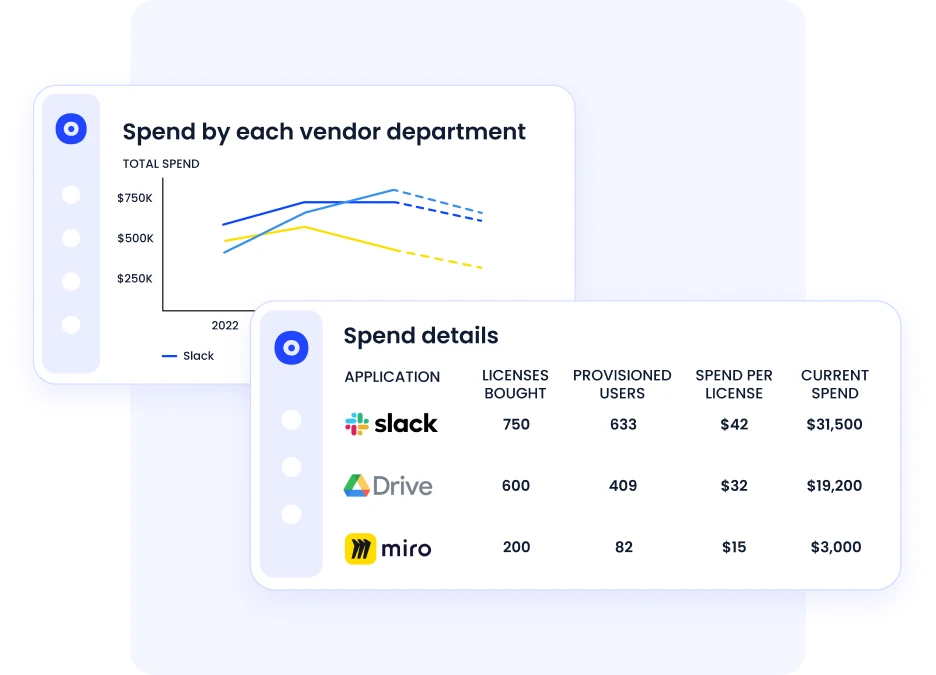
This unified view supports Zero Trust SaaS across teams:
- Security teams reduce breach risk and audit failures
- IT teams automate onboarding and offboarding
- Procurement teams optimize contracts, usage, and renewals
Customers such as RingCentral, Shiji, and RecRoom report significant security posture improvements and six- to seven-figure savings within months, proving that continuous SaaS governance delivers tangible outcomes.
In A Nutshell
Shadow IT has become a permanent condition of modern SaaS environments, driven by decentralized purchasing, self-serve adoption, and the rapid spread of AI tools.
Addressing this shift requires moving beyond static approvals and periodic reviews toward Zero Trust SaaS models built on continuous verification, usage-based access, and always-on governance.
CloudEagle.ai enables teams to enforce Zero Trust across the full SaaS and AI stack by unifying Shadow IT discovery, access governance, and spend intelligence in one system of record.
Book a free demo to see how CloudEagle helps you govern SaaS access continuously without slowing the business.
Frequently Asked Questions
1. What is meant by “Shadow IT”?
Shadow IT is the use of SaaS or AI tools without IT approval or visibility, often through free trials, direct sign-ups, or card purchases.
2. What is SaaS governance?
SaaS governance is the ongoing control of SaaS applications, access, usage, and compliance to reduce security, cost, and audit risks.
3. What are the principles of SaaS security?
SaaS security focuses on identity, least-privilege access, continuous verification, full app visibility, and automated access control.
4. What are the five pillars of Zero Trust?
The five pillars are identity, device, application/workload, data, and network, all designed to eliminate implicit trust.
5. What is an example of a Shadow IT policy?
A Shadow IT policy allows tool adoption but requires registration, clear ownership, role-based access, and periodic reviews.

%201.svg)










.avif)




.avif)
.avif)




.png)









