HIPAA Compliance Checklist for 2025

Cyberattacks are evolving faster than ever. In 2024 alone, over 82 % of data breaches involved human error or excessive access privileges (Verizon DBIR 2024). As organizations migrate deeper into cloud-based and SaaS ecosystems, the question isn’t if your environment will be tested; it’s how prepared you are when it happens.
That’s where the debate of Zero Trust vs Least Privilege becomes critical. Both are cornerstone frameworks for modern cybersecurity and SaaS governance, yet they address risk from different angles.
Zero Trust operates on the principle of “never trust, always verify”, continuously authenticating every access request in real time. Least Privilege, on the other hand, enforces the idea of “only what’s necessary”, granting users the bare minimum permissions needed to perform their tasks.
Many IT and security leaders treat SaaS management and identity governance as separate priorities but in reality, they’re two halves of the same strategy. When aligned, they not only strengthen your security posture but also streamline access control, cut SaaS waste, and ensure compliance across IT, Security, Procurement, and Finance.
TL;DR
- Zero Trust = “Never trust, always verify.” It continuously authenticates users and devices before granting access.
- Least Privilege = “Only what’s necessary.” It limits user permissions to the bare minimum needed for their roles.
- Combined, they cut data breach risk by up to 74 % (IBM Security 2024) and reduce insider threat impact by 60 %.
- Zero Trust secures the environment; Least Privilege secures the user and permissions.
- Together, they’re the foundation of modern SaaS security — and CloudEagle.ai helps operationalize both seamlessly.
1. What Is Zero Trust Security?
Zero trust is a security model that operates on the principle of "never trust, always verify," requiring strict identity verification for every person, device, or application trying to access resources on a network, regardless of their location.
A. Why “never trust, always verify” changed the game
According to Gartner, > 70 % of organizations are adopting or planning to adopt a Zero Trust framework by 2025. The reason? Traditional perimeter security assumes users inside the network are trustworthy — a fatal flaw in today’s cloud-first, hybrid-work world.
Zero Trust assumes breach by default. Every access request — from a user, device, or app — must be authenticated, authorized, and continuously validated.
B. Core principles of Zero Trust
- Verify explicitly – Validate identity, device health, and context for every request.
- Assume breach – Design systems as if attackers already have limited access.
- Least-privilege access – Limit access rights to necessary data or systems.
- Continuous monitoring – Use behavioral analytics and AI for real-time risk scoring.
“Zero Trust isn’t a product; it’s a paradigm shift in how we think about security.” — Forrester Research
C. Why it matters for SaaS security
In SaaS ecosystems, multiple users and third-party integrations expand the attack surface. Zero Trust ensures each connection between users, SaaS apps, and APIs is continuously verified. It’s no longer “once verified, always trusted.”
2. What Is the Principle of Least Privilege (PoLP)?
The Principle of Least Privilege (PoLP) is a foundational security concept that ensures users, applications, and systems are granted only the minimum level of access or permissions necessary to perform their specific tasks. By limiting access rights to the bare essentials, PoLP reduces the attack surface, minimizes the potential impact of breaches or human errors, and strengthens overall security posture across the organization.
Think of it as enforcing need-to-know access across your SaaS stack.
B. Why PoLP matters
- Reduces attack surface: Over-permissioned accounts are prime targets.
- Mitigates insider threats: Users can’t abuse access they don’t have.
- Improves compliance: Regulations like SOC 2, ISO 27001, HIPAA require strict access control.
Stat: 74 % of data breaches involve a human element — often excessive access rights (Source: Verizon DBIR 2024).
C. PoLP in SaaS environments
In large SaaS portfolios, applying PoLP means:
- Revoking dormant or unused licenses
- Adjusting role-based access in apps
- Controlling admin privileges
- Automating provisioning and de-provisioning
CloudEagle.ai helps achieve this at scale by connecting to 500 + SaaS apps and orchestrating access governance automatically.
3. Zero Trust vs Least Privilege: What’s the Real Difference?
Though often used together, these are not interchangeable. They operate at different layers of the security stack.
A. How Each Model Applies Access Controls
Zero Trust enforces access through identity validation, context awareness, and network micro-segmentation. Least Privilege dictates “who gets what” once trust is established.
B. Role of Identity and Verification
Zero Trust relies heavily on real-time authentication (MFA, device posture, location). PoLP relies on accurate role definitions and access reviews.
C. Reactive vs Proactive Enforcement
Zero Trust = Proactive security via continuous verification.
PoLP = Reactive fine-tuning via periodic audits and revocations.
4. Choosing Between Zero Trust and Least Privilege
A. Which Model Fits Your Organization’s Needs?
- Small/medium SaaS-first companies: Start with Least Privilege — map permissions and tighten roles.
- Enterprises with complex hybrid environments: Implement Zero Trust — focus on identity and device verification.
- Heavily regulated industries: Use both — PoLP for compliance, Zero Trust for continuous risk management.
B. Why a Combined Strategy Works Best
According to Cybersecurity Insiders (2024), organizations combining Zero Trust + PoLP experience a 45 % lower incident rate than those using either alone.
Implement Zero Trust as the macro policy; PoLP as the micro enforcer.
Example
- A user logs into Salesforce → Zero Trust verifies identity and device.
- Within Salesforce, PoLP limits that user to marketing records only.
5. Security Benefits of Combining Zero Trust and Least Privilege
A. Reduced Risk from Insider and External Threats
Implementing both models can reduce breach impact by up to 80 % (Source: IBM Security Cost of a Data Breach Report 2024).
B. Improved Compliance and Audit Readiness
Regulatory frameworks like GDPR, PCI DSS and SOC 2 mandate tight access controls and auditing. Zero Trust and PoLP make evidence collection automated and traceable.
C. Enhanced Operational Efficiency
Access requests, approvals, and revocations become automated, reducing manual work for IT teams by 35–50 %.
D. Better Governance Across SaaS Ecosystems
Together they improve visibility into “who has access to what and why,” a core metric for SaaS governance and renewal readiness.
6. Challenges When Implementing Zero Trust and Least Privilege
A. Common Missteps
- Privilege creep — not revoking access when roles change.
- Over-complication — treating Zero Trust as a tool instead of a framework.
- Siloed ownership — security vs procurement vs IT not aligned.
B. Tech Stack & Integration Complexities
Adopting Zero Trust requires integrating IAM, PAM, ZTNA and SaaS management tools. Platforms like CloudEagle.ai help consolidate visibility across 500 + apps, automating PoLP and Zero Trust enforcement.
C. Cultural and Organizational Alignment
Zero Trust demands a shift from “trust but verify” to “never trust.” IT and business leaders must balance security with user experience through automation and policy clarity.
7. How CloudEagle.ai Helps You Operationalize Zero Trust and Least Privilege
CloudEagle.ai helps organizations operationalize Zero Trust and Least Privilege by offering a comprehensive suite of features that empower IT, security, and procurement teams to enforce strict access controls while optimizing SaaS spend. Here's how the platform aligns with these two critical security principles:
1. Discover: Full Visibility and Continuous Monitoring

Zero Trust Visibility: CloudEagle ensures that no user or device is trusted by default. It gives you 100% visibility into your entire SaaS, AI, and Shadow IT ecosystem. This includes both sanctioned and unsanctioned tools, allowing for real-time identification of unauthorized or risky apps.
AI and SaaS Discovery: With over 500 integrations and AI-powered analysis, CloudEagle uncovers every tool in use, regardless of how it was procured. This helps mitigate the risk of Shadow IT and unauthorized access, which are major security concerns in the Zero Trust model.
Key Benefits:
- Detects unauthorized or rogue applications in real time.
- Maps app usage, login activity, and user roles to identify risky behavior.
- Provides a live system of record, ensuring that your security posture is continuously updated.
2. Govern: Enforce Least Privilege Access Controls
Automated Access Management: CloudEagle enforces Least Privilege by ensuring users have access only to the tools they need for the right duration. It leverages Role-Based Access Control (RBAC), Just-In-Time (JIT) access, and time-bound access for contractors and temporary roles.

Access Reviews and Remediation: Periodic access reviews are automated to ensure that users retain only the permissions necessary for their role. This prevents privilege creep, where users accumulate unnecessary access rights over time, reducing security risks.
Key Benefits:
- Automates user provisioning, deprovisioning, and role-based access management.
- Flags and remediates privilege creep, reducing the risk of excessive or outdated permissions.
- Ensures compliance with audit-ready logs and access reviews, such as SOC2.
3. Renew: Streamline Renewals with Security and Compliance
Automated Renewals: CloudEagle integrates access reviews with renewal workflows, ensuring that only necessary tools and users are renewed, and that these renewals comply with Zero Trust principles.

Contract and Vendor Management: CloudEagle helps to centralize vendor contracts and renewals, linking them with access reviews to ensure that apps are only renewed when they align with the security policies in place.
Key Benefits:
- Automates renewal workflows and triggers access reviews for compliance.
- Ensures that vendors comply with security policies before renewals are processed.
- Prevents renewing tools that pose security risks or are no longer needed.
4. Optimize: Reduce SaaS Waste and Enforce Better Security Hygiene
License Harvesting and App Rationalization: CloudEagle helps reduce unnecessary SaaS spend by identifying unused licenses and duplicate apps across departments. By reclaiming these licenses, organizations can optimize costs without compromising security.
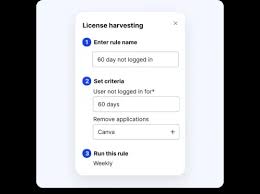
Security-First Spend Optimization: The platform ensures that optimization efforts do not compromise security by maintaining proper access controls and ensuring that unused apps and features are either downgraded or deprovisioned.
Key Benefits:
- Reduces SaaS spend by eliminating waste and optimizing licenses.
- Enhances security by deactivating unused or redundant apps and licenses.
- Maintains alignment with Zero Trust by continuously evaluating and managing access.
8. Conclusion
Zero Trust and Least Privilege aren’t competitors — they’re complements.
Zero Trust builds the walls of verification; Least Privilege locks the doors of permissions. Together, they reduce attack surfaces, tighten governance and save costs in SaaS operations.
With CloudEagle.ai’s platform, you can discover hidden apps and users, Govern access with automated PoLP, Renew securely and compliantly, Optimize spend while maintaining Zero Trust security.
Book a CloudEagle.ai demo and see how AI-driven automation can bring Zero Trust and Least Privilege to life across your entire SaaS stack.
Frequently Asked Questions
1. What is the disadvantage of Zero Trust?
Implementation can be complex and resource-intensive, especially for legacy systems or organizations without centralized identity management.
2. What’s the difference between ZTNA and PAM?
ZTNA controls network/app access based on identity and context; PAM controls privileged admin accounts and credentials.
3. What is Zero Trust privilege?
It’s the combination of Zero Trust verification and Least Privilege permissions — dynamic access with minimal rights.
4. What is zero trust minimum access
The concept of granting the least permissions possible within a Zero Trust framework.
5. What is the least privilege access in ZTA?
It means even after verifying identity and device, users only get the minimal access required for their task.

%201.svg)








.avif)




.avif)
.avif)




.png)









