HIPAA Compliance Checklist for 2025

Managing SaaS compliance risks is one of the biggest challenges IT and security teams face today. As organizations adopt more cloud applications, the complexity of maintaining compliance across hundreds of tools continues to grow exponentially.
According to Gartner, global SaaS spending is expected to exceed $195 billion in 2023. With that massive adoption comes equally massive SaaS compliance challenges that require immediate attention and structured approaches to SaaS governance.
Whether you're dealing with GDPR, SOC 2, HIPAA, or industry-specific regulations, understanding SaaS compliance risks and implementing effective risk management strategies is critical for protecting your organization from regulatory penalties and data breaches.
TL;DR
- Shadow IT creates blind spots exposing organizations to unauthorized data sharing and regulatory violations through unapproved applications
- Data residency issues arise when SaaS vendors store information in regions conflicting with compliance and sovereignty requirements
- Third-party vulnerabilities mean your security posture is only as strong as your weakest vendor integration point
- Access control sprawl happens when employees retain permissions long after needed, creating security and audit nightmares
- Fragmented governance leaves compliance monitoring scattered across departments with no centralized oversight or accountability
Risk 1 : How Does Shadow IT Create Compliance Vulnerabilities?
Shadow IT happens when employees adopt SaaS applications without official approval. Your marketing team signs up for a social media scheduling tool, your sales team tries a new prospecting platform, or engineers experiment with development tools, all storing company data outside IT's visibility.
A Cisco study revealed organizations use 10 times more cloud services than IT departments know about. Most IT teams believe they manage 30-40 applications when the actual number exceeds 300-400.
Shadow IT compliance challenges include:
- Unknown data flows you can't protect or monitor
- Unvetted security practices creating vulnerability gaps
- Audit failures when examiners discover undocumented applications
- Regulatory violations from storing sensitive data in non-compliant systems
- Lack of vendor management oversight and contract controls
This creates massive SaaS governance risks because you can't enforce compliance policies on applications you don't know exist.
Risk 2: Data Residency and Sovereignty Risk
Where your data physically resides matters significantly for SaaS data compliance. If you're subject to GDPR and your vendor stores EU customer data on US servers without proper safeguards, you've violated regulations.
Many SaaS vendors operate multi-tenant environments where customer data shares infrastructure. They might replicate information across regions for redundancy without explicit consent or notification to clients.
Critical data residency concerns:
- Cross-border transfers triggering different regulatory requirements
- Vendor transparency gaps about storage and processing locations
- Dynamic infrastructure shifting workloads between data centers
- Conflicting regulations between jurisdictions
- Data sovereignty requirements varying by industry and region
According to IDC research, 80% of organizations will face penalties for non-compliance with data sovereignty regulations by 2024 without proper data governance controls.
Risk 3. Third-Party and Integration Risk
Your SaaS applications operate within complex ecosystems. They integrate with other tools, connect to APIs, and share data across your entire tech stack. Each integration point represents a potential SaaS governance risk.
Consider this: Your CRM integrates with an email platform, which connects to a data enrichment service, which pulls from public databases. That's four vendors touching customer data, all requiring compliance verification.
Third-party compliance risks include:
- Shared responsibility confusion when data breaches occur during transfers
- Integration vulnerabilities through APIs and webhooks
- Vendor risk extending through supply chains
- Outdated security certifications needing continuous verification
- Lack of standardized security assessments across vendors
Maintaining a comprehensive vendor registry with current compliance documentation helps manage these interconnected risks effectively.
Risk 4. Access Control Sprawl
Employee turnover creates access control nightmares. When someone leaves, their SaaS access often remains active. That former employee from six months ago might still access your project management tool, shared drives, and customer databases.
Research from Varonis shows 58% of companies have over 500 employees with inappropriate access to sensitive files. That's not just security risk, it's a compliance violation waiting to surface during audits.
Access control challenges:
- Orphaned accounts remaining active after employee departures
- Excessive permissions beyond role requirements
- No systematic access reviews or recertification processes
- Shared credentials preventing individual accountability tracking
- Missing automated offboarding workflows to revoke access
Implementing proper identity management and access governance prevents these issues from escalating into major compliance violations.
Risk 5. Fragmented Governance and Ownership Gaps
Most organizations manage SaaS risk management reactively across silos. IT handles security, finance tracks spending, departments approve tools independently. Nobody maintains complete visibility into the entire SaaS portfolio.
This fragmented approach creates dangerous blind spots:
- No single source of truth for approved applications
- Inconsistent vetting processes across departments
- Duplicate tools wasting budget on similar capabilities
- Compliance gaps as requirements fall between departments
- Audit chaos when documentation is scattered
A Deloitte survey found 68% of executives believe their organizations face more compliance risk today than five years ago, primarily from cloud services complexity.
Establishing centralized SaaS management with cross-functional oversight addresses these governance challenges systematically.
Risk 6. Audit Readiness Risk
When auditors request documentation about your SaaS environment, can you provide it immediately? Most organizations scramble to compile information about applications, vendors, data flows, and access controls because they lack centralized documentation.
Audit readiness challenges include:
- Missing vendor contracts and data processing agreements
- Incomplete security questionnaires and compliance certifications
- No documented approval workflows or risk assessments
- Scattered evidence across departments and systems
- Inability to demonstrate continuous monitoring and controls
Without proper audit preparation, organizations face extended audit timelines, qualification letters, and potential compliance failures that damage reputation and customer trust.
Risk 7. Data Leakage and Misconfiguration Risk
SaaS applications offer powerful sharing and collaboration features, but these same capabilities create data leakage risks. Employees accidentally share sensitive files publicly, misconfigure permissions, or sync data to personal devices.
Common data leakage scenarios:
- Public link sharing for documents containing sensitive information
- Overly permissive default sharing settings in collaboration tools
- Data synchronization to unmanaged personal devices
- Lack of data classification preventing appropriate handling
- Missing data loss prevention controls in cloud applications
These misconfigurations often go undetected until a breach occurs, making proactive monitoring and controls essential for SaaS security compliance.
How to Mitigate SaaS Compliance Risks
a. Improve SaaS Visibility
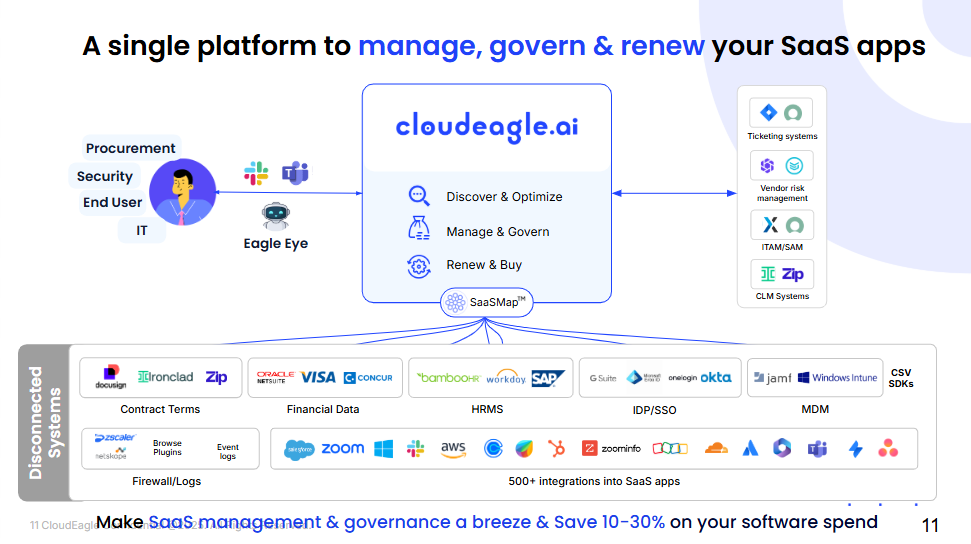
You can't manage SaaS compliance risks you can't see. CloudEagle's automated SaaS discovery continuously scans your environment by analyzing SSO logs, browser extensions, expense reports, and network traffic to surface every application in use including unauthorized ones.
Instead of relying on manual surveys or guesswork, you get a real-time, comprehensive inventory with compliance status for each tool, giving your team the visibility needed to make informed decisions fast.
b. Visibility strategies:
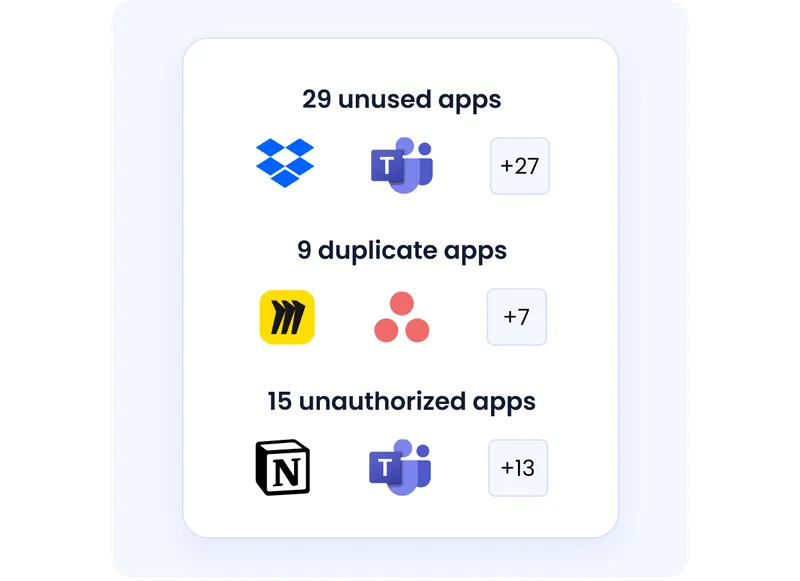
Fragmented approval processes are an open invitation for shadow IT. CloudEagle's procurement and governance workflows let you build tiered approval processes based on risk level, lightweight for low-risk tools, and rigorous for applications touching sensitive data.
All contracts, security questionnaires, and compliance certifications are stored in a centralized repository that becomes your single source of truth, making audits faster and eliminating the chaos of documentation scattered across departments.
c. Centralize Governance and Ownership
Compliance only works when everyone knows their role. CloudEagle supports cross-functional governance by giving each stakeholder CISO, SaaS Ops, IT, Legal, Finance, and department managers, role-appropriate visibility and controls within a single platform.
Rather than siloed tools and email threads, every team works from the same data, with clear accountability built into workflows from day one.
d. Automate Access Management
Manual access management simply doesn't scale. CloudEagle automates the entire access lifecycle, provisioning the right permissions during onboarding, instantly revoking access when employees leave, and automatically adjusting permissions during role changes.
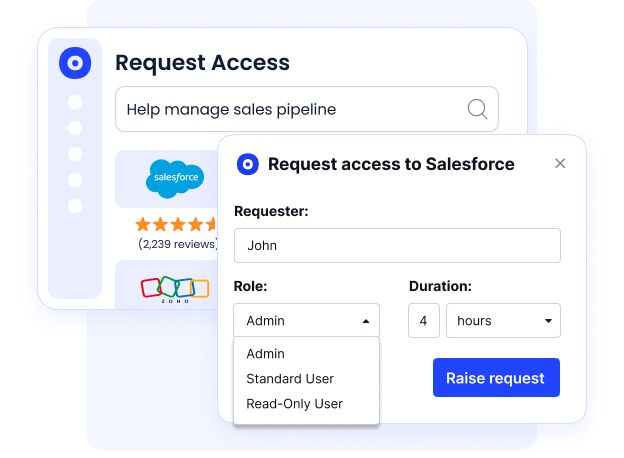
Combined with SSO integration, it enforces consistent access policies across your entire SaaS stack while triggering periodic access certification campaigns so managers regularly review who has access to what.
e. Strengthen Vendor Risk Management
Your compliance posture is only as strong as your weakest vendor. CloudEagle's vendor risk management module keeps you ahead of expiring certifications and shifting vendor practices with structured review cadences, quarterly compliance checks, annual risk assessments, monthly access audits, and bi-annual integration reviews.

A built-in vendor scoring system helps you prioritize which applications need immediate attention based on data sensitivity, user base size, and integration depth.
f. Implement Cloud-Native Data Protection
Traditional perimeter-based DLP tools weren't built for SaaS. CloudEagle provides cloud-native data protection with content inspection, sensitive data classification, policy enforcement, and geographic transfer restrictions, all operating within your cloud applications and in transit. This means accidental public sharing, overly permissive defaults, and unauthorized data movement get flagged before they become breaches, not after.
Conclusion
Organizations that handle SaaS compliance best treat it as a business enabler, not a blocker. They build lightweight processes that give teams the tools they need while maintaining appropriate controls.
Your SaaS stack will grow more complex and compliance requirements will get stricter, getting ahead of these risks now means building on solid ground instead of scrambling to fix problems later.
CloudEagle gives you the visibility, automation, and governance controls to stay ahead.
Start your compliance journey today →
Frequently Asked Questions
- What are the biggest SaaS compliance risks today?
Shadow IT, data residency issues, third-party security gaps, access sprawl, and fragmented governance create the most significant compliance exposures for modern organizations managing cloud applications.
- How do you mitigate SaaS security risks?
Implement discovery tools for visibility, establish governance policies, automate access controls, conduct regular vendor audits, and build centralized compliance documentation.
- Who should manage SaaS compliance programs?
A dedicated SaaS Operations team should coordinate between CISO, IT, security, legal, finance, and department managers with clear ownership and shared accountability.
- What tools help with SaaS compliance management?
SaaS discovery platforms, identity management systems, automated provisioning tools, compliance documentation hubs, and vendor risk assessment solutions streamline compliance workflows.
- How often should organizations review SaaS vendors?
Conduct quarterly certification checks, annual risk assessments, monthly access audits, and bi-annual integration reviews based on the application's risk level and data sensitivity.

%201.svg)









.avif)




.avif)
.avif)




.png)









