HIPAA Compliance Checklist for 2025

Enterprises now run hundreds of SaaS applications. Most security teams still rely on periodic reviews, static policies, and fragmented tooling.
That model is breaking.
SaaS Security Posture Management is no longer optional. In 2026, SSPM defines whether your SaaS risk management is proactive or reactive.
In this guide, you’ll learn what SSPM really means, why traditional SaaS security controls fail, and the exact SSPM checklist enterprises should enforce.
TL;DR
- Traditional SaaS security models cannot keep pace with SaaS and AI growth.
- Identity sprawl and misconfigurations are the biggest SSPM risk drivers.
- SSPM must combine discovery, access governance, and configuration monitoring.
- Alerts without remediation create security noise, not protection.
- Unified visibility and automation are essential for SaaS risk management in 2026.
1. What Is SaaS Security Posture Management (SSPM)?
SaaS Security Posture Management (SSPM) is the continuous monitoring and enforcement of security configurations, access controls, and risk exposure across SaaS applications.
Unlike traditional security reviews, SSPM focuses on:
- Configuration hygiene
- Identity and privilege exposure
- OAuth and third-party integrations
- Continuous risk scoring
- Real-time posture monitoring
SSPM strengthens SaaS security controls by ensuring apps remain secure after deployment, not just at onboarding.
The global SSPM market is projected to reach $3.53 billion by 2030, expanding at a CAGR of 48.7%, reflecting the rapid enterprise shift toward continuous posture management.
SSPM shifts SaaS security from point-in-time assessment to continuous enforcement.
2. Why Are Traditional SaaS Security Models Breaking?
Legacy SaaS security approaches were built for smaller environments.
Enterprise SaaS in 2026 looks very different.
A. SaaS Adoption Outpaces Security Reviews
Departments adopt tools faster than security can review them.
Free plans, embedded AI features, and departmental purchases expand your SaaS footprint overnight.
Security reviews often happen:
- After adoption
- During audit season
- Or after an incident
That lag creates blind spots in SaaS risk management.
B. Identity Sprawl Creates Hidden Risk
Each SaaS app introduces:
- Admin roles
- API tokens
- OAuth integrations
- Third-party connectors
As identities multiply, privilege exposure increases.
Overprivileged users and orphaned accounts become the most common attack vector in SaaS environments.
C. Misconfigurations Go Unnoticed
Even secure SaaS platforms become risky when:
- MFA is disabled
- External sharing is unrestricted
- Logging is turned off
- Admin roles proliferate
Configuration drift happens quietly over time.
Without continuous posture monitoring, these gaps remain invisible.
3. What Should Be in Your 2026 SSPM Checklist?
An SSPM checklist in 2026 is not a one-time security review.
It is a continuous SaaS security control model that monitors identity, configuration, integrations, and risk signals in real time.
Below are the core pillars enterprises must enforce.
A. SaaS Discovery and Ownership Mapping
You cannot secure SaaS you cannot see.
Real SSPM begins with full-stack discovery, including shadow apps and AI tools.
Key controls:
- Real-time SaaS inventory across SSO, finance, and browser signals
- Detection of unsanctioned and OAuth-connected apps
- Data sensitivity classification per application
- Assigned business and security owners for every tool
If ownership is unclear, posture degrades silently.
Why it matters: Visibility defines your SaaS risk management boundary.
B. Privileged Access and Role Monitoring
Most SaaS breaches originate from overprivileged accounts.
SSPM must treat admin exposure as a live risk factor, not a quarterly review item.
Key controls:
- Continuous monitoring of admin and super-admin roles
- Alerts for new privileged account creation
- Separation of admin and standard identities
- Detection of dormant or inactive privileged users
- Enforcement of least privilege principles
CloudEagle's 2025 IGA Report found that 48% of former employees still have app access months after leaving, highlighting the critical need for continuous privilege monitoring and automated deprovisioning.
Why it matters: Identity is now the control plane of SaaS security.
C. Configuration and Security Setting Reviews
Secure defaults do not stay secure.
Configuration drift happens through small, incremental changes that expand risk over time.
Key controls:
- MFA enforcement across all critical SaaS apps
- Monitoring of external sharing settings
- Logging and audit trail validation
- Session timeout and authentication policy checks
- Alerts for high-impact configuration changes
Why it matters: Misconfiguration is one of the leading SaaS attack vectors.
D. OAuth and Third-Party App Controls
OAuth integrations create invisible data pathways.
Employees often connect automation tools, AI apps, and plugins without understanding the permission scope.
Key controls:
- Inventory of all connected third-party applications
- Review of granted permission scopes
- Detection of high-risk data access levels
- Removal of stale or unused integrations
- Policy enforcement for sensitive app connections
Why it matters: OAuth exposure expands your attack surface beyond core apps.
E. Continuous Risk Scoring and Alerts
Dashboards alone do not reduce risk.
SSPM must translate posture signals into prioritized, actionable intelligence.
Key controls:
- Dynamic risk scoring based on exposure and sensitivity
- Prioritized alerts based on business impact
- Automated remediation workflows
- Escalation of high-severity risks
- Tracking of remediation status
Why it matters: Alerts without prioritization create fatigue, not security.
F. Ongoing User and Access Reviews
Automation strengthens monitoring. Reviews reinforce accountability.
Structured access validation remains critical for high-risk SaaS apps.
Key controls:
- Risk-tiered review cadence
- Business owner certification of access necessity
- Admin role revalidation
- Removal of inactive accounts
- Audit-ready documentation retention
Why it matters: SSPM supports governance. Governance sustains security.
4. What Are Some Common SSPM Gaps in Enterprises?
Most enterprises believe they have SaaS security controls in place.
The issue is not the absence of tooling. It is a fragmented execution.
Below are the most common SSPM gaps seen in large SaaS environments.
A. Shadow AI Tools Bypass Security
AI adoption is moving faster than SaaS governance.
Employees connect AI tools directly to core business apps without a security review. These integrations often inherit broad data permissions instantly.
Common gaps include:
- AI tools connected via OAuth without risk assessment
- Sensitive data exposed to external AI platforms
- No policy enforcement on AI usage
- No visibility into AI-driven data exports
Shadow AI expands risk beyond traditional SaaS boundaries.
CloudEagle's research shows that 60% of enterprise SaaS and AI applications now operate outside IT's visibility, creating blind spots that traditional SSPM tools cannot address.
Reality: If AI integrations are not monitored, your SSPM program has blind spots.
B. Alerts Without Remediation
Many organizations generate posture alerts but fail to close the loop.
Security dashboards fill up with configuration warnings and privilege flags, yet remediation is manual, delayed, or unclear.
Common gaps include:
- No defined owner for resolving alerts
- Alert fatigue due to low prioritization
- High-risk issues sitting unresolved
- No workflow connection between detection and action
Detection without remediation does not reduce SaaS risk.
Reality: SSPM must connect posture monitoring to enforceable workflows.
C. No Link Between Security and Access
SaaS security and identity governance often operate in silos.
Security teams monitor configurations. IT manages provisioning. Compliance handles reviews. None shares a unified risk view.
Common gaps include:
- Access granted without a risk context
- Privileged roles not tied to sensitivity level
- Configuration changes not linked to identity exposure
- Reviews performed without posture intelligence
When identity and posture are disconnected, exposure increases quietly.
Reality: SaaS security posture management must integrate identity, configuration, and risk into one control model.
5. How CloudEagle.ai Supports SSPM?
SaaS Security Posture Management requires more than configuration scanning.
It requires visibility, identity governance, risk prioritization, and enforceable remediation workflows across every SaaS and AI tool in use.
CloudEagle.ai supports SSPM by combining discovery, access control, posture monitoring, and spend intelligence into one unified control model.
A. Shadow IT Discovery and Risk Remediation
SSPM fails without complete visibility.
CloudEagle detects unsanctioned SaaS and AI tools using signals from:
- SSO and Google Workspace login activity
- Finance and expense systems
- Browser-level telemetry
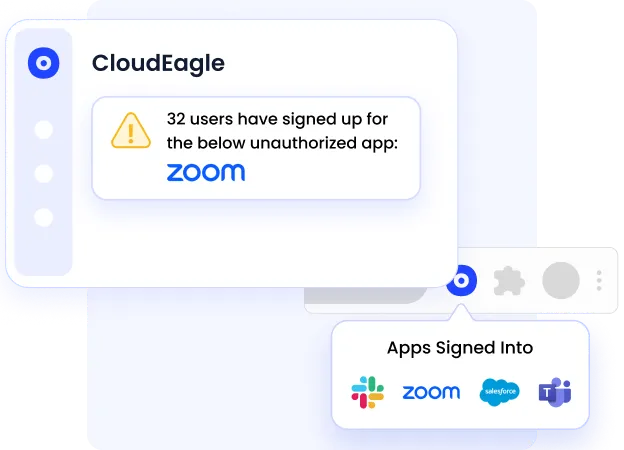
It maps discovered tools to known vendors and flags high-risk applications for remediation through structured workflows.
This eliminates rogue, duplicate, and unmanaged applications before they expand your attack surface.
SSPM impact: Closes visibility gaps across the SaaS stack.
B. Access Governance and Privilege Management
Identity is the control plane of SaaS security.
CloudEagle automates access reviews, enforces least privilege, and continuously monitors for privilege creep, especially when users change roles but retain elevated permissions.

It supports:
- Just-in-time access
- Time-bound permissions
- Automated deprovisioning across apps, even those outside traditional IDPs such as Okta or Azure AD
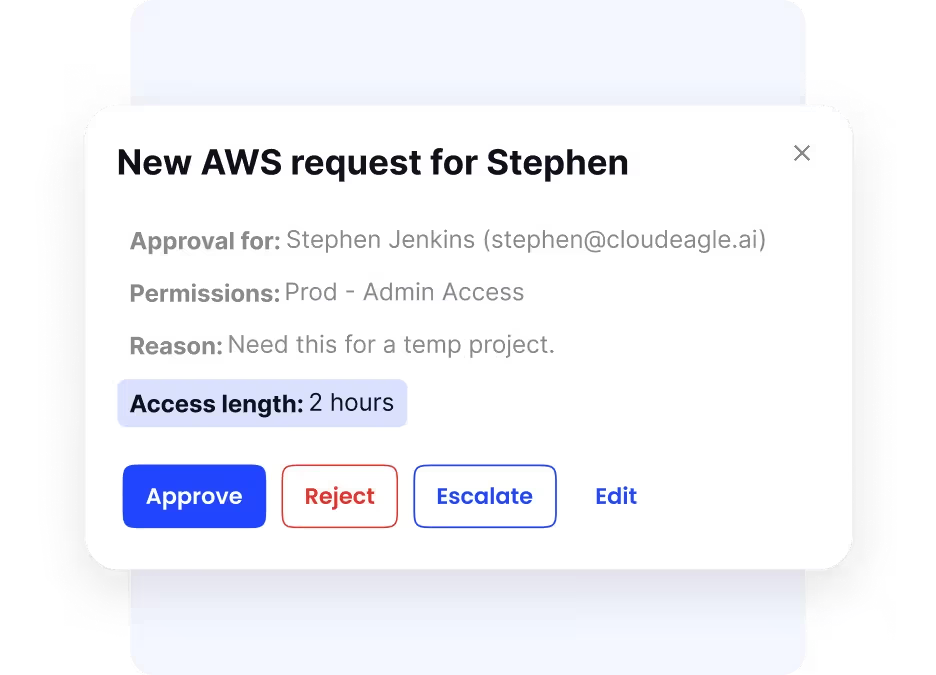
SSPM impact: Reduces attack surface and insider threat exposure.
C. Centralized Visibility Across SaaS Applications
Fragmented dashboards create fragmented risk awareness.
CloudEagle provides a unified view showing:
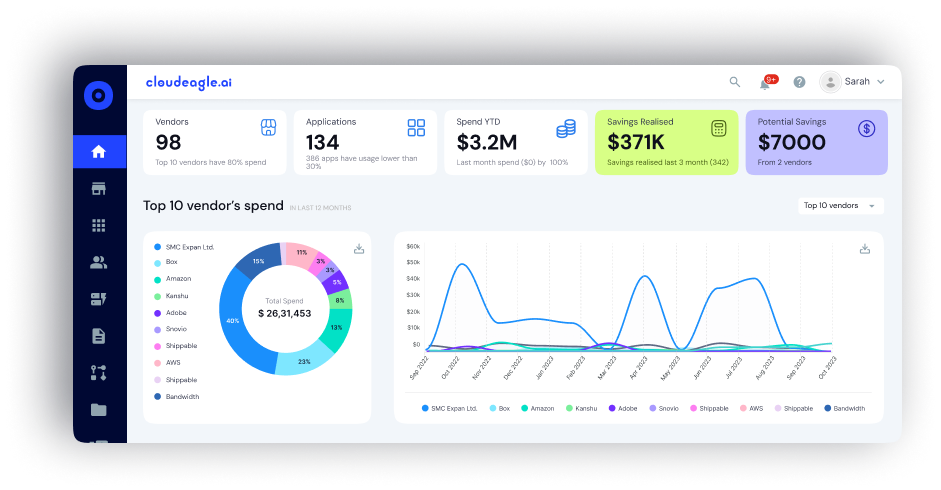
- Who has access to which applications
- Application-level risk indicators
- Integrations across HRIS, SSO, and ITSM systems
This enables real-time monitoring of both human and machine identities across the SaaS ecosystem.
SSPM impact: Enables risk-aware governance and posture transparency.
D. Audit-Ready Reporting and Compliance Alignment
SSPM must support compliance, not operate separately from it.
CloudEagle exports SOC 2–ready audit logs and monitors vendor alignment with frameworks such as GDPR and SOC 2.
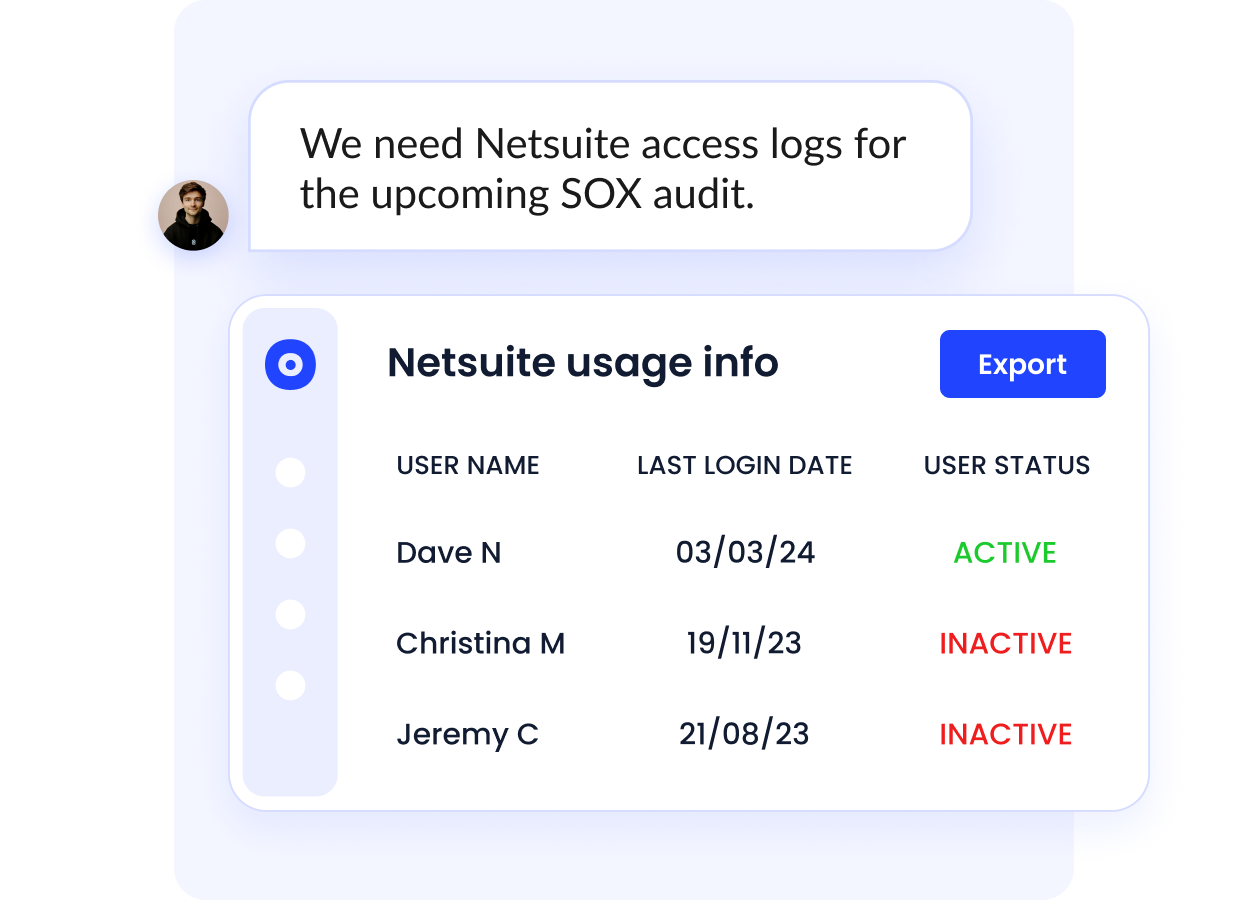
It centralizes metadata from:
- Contracts
- Access logs
- Usage records
This significantly reduces audit preparation time and strengthens continuous compliance.
SSPM impact: Improves audit readiness and reduces compliance overhead.
E. SSPM Plus Spend Optimization
Traditional SSPM vendors focus only on security posture.
CloudEagle uniquely connects posture risk with license and spend intelligence.
It detects:
- Unused or underutilized licenses
- Applications that are both insecure and redundant
- Overprovisioned access is tied to unnecessary spending
It then enables workflows such as downgrade, deprovision, renew, or consolidate.
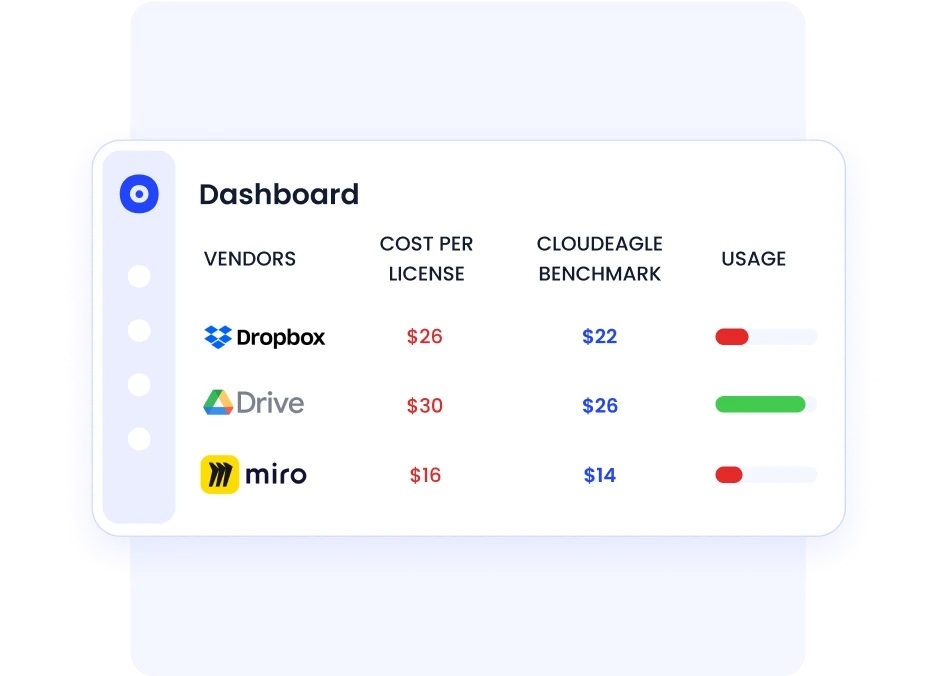
This allows Security, IT, and Procurement to collaborate on decisions that reduce both risk and cost.
CloudEagle customers have saved over $2B in software costs while simultaneously strengthening security controls, proving that SSPM and spend optimization are not competing priorities.
SSPM impact: Aligns security posture management with measurable ROI.
In a Nutshell
SaaS Security Posture Management in 2026 is no longer optional. As SaaS and AI adoption accelerate, misconfigurations, privilege exposure, and OAuth risk expand faster than traditional security reviews can handle.
An effective SSPM checklist shifts security from periodic assessment to continuous enforcement. By combining discovery, identity governance, configuration monitoring, and risk prioritization, enterprises strengthen SaaS security controls and reduce operational blind spots.
CloudEagle.ai enables unified SSPM by connecting visibility, access governance, posture intelligence, and spend optimization into one enforceable model. Instead of reacting to incidents or audit findings, organizations stay ahead of SaaS risk.
Book a free demo to see how CloudEagle.ai turns SSPM into continuous, enforceable control.
Frequently Asked Questions
- What is SSPM in cybersecurity?
SSPM, or SaaS Security Posture Management, continuously monitors SaaS configurations, access controls, and integrations to reduce security risk and misconfiguration exposure.
- Why is SaaS Security Posture Management important?
SaaS adoption grows faster than manual reviews. SSPM helps detect misconfigurations, privilege creep, and shadow apps before they create breaches.
- How is SSPM different from CSPM?
CSPM focuses on cloud infrastructure security, while SSPM manages SaaS application configurations, identity exposure, and third-party integrations.
- What risks does SSPM address?
SSPM addresses misconfigurations, overprivileged users, OAuth exposure, shadow IT, identity drift, and compliance gaps across SaaS apps.
- What should an SSPM checklist include?
An SSPM checklist should cover SaaS discovery, privileged access monitoring, configuration reviews, OAuth controls, risk scoring, and continuous access validation.

%201.svg)










.avif)




.avif)
.avif)




.png)









