HIPAA Compliance Checklist for 2025

Worried about protecting your sensitive business data from accidental leaks or cyber threats?
You might think your enterprise is completely secure, but there’s a high possibility that it is not. Today, data moves fast and is stored everywhere, such as in the cloud or on employees’ devices. Though it seems secure, different factors, such as internal and external factors, can lead to serious issues like security breaches.
Around 67.7% of businesses experienced significant data loss incidents. This highlights the urgent need for stringent access controls and insider threat mitigation.
Keeping this information safe is more important than ever. That’s why using tools called Data Loss Prevention (DLP) software is essential to protect your customer data.
DLP tools help stop sensitive information from falling into the wrong hands. They monitor and control how data is used and shared, whether it’s stored on a server, transmitted over a network, or accessed by someone inside your company.
Let’s explore the top 10 data loss prevention tools to protect your business, reduce insider threats, and tackle modern security challenges.
TL;DR
- DLP tools help protect your important data by tracking how it is used and shared on computers, networks, and the cloud.
- DLP tools check data across emails, cloud apps, networks, and devices. They automatically apply rules, classify data, monitor user behavior, and send instant alerts if something suspicious occurs to prevent data loss.
- There are three types: Network DLP protects data on networks, Endpoint DLP protects devices, and Cloud DLP protects cloud data. Using all three is best.
- Look for tools that offer strong features, easy use, scalability, integration with your existing systems, and reliable vendor support. The right choice helps secure data efficiently without slowing down work.
- Enterprises should select DLP solutions based on their features, scalability, integration capabilities, ease of use, and vendor support. Implementing strong DLP reduces insider threats, enforces regulations and secures business-critical information efficiently.
What is Data Loss Prevention?
Data Loss Prevention (DLP) is a security strategy and set of tools that help enterprises identify, monitor, and prevent the unauthorized sharing, transfer, or use of sensitive information.
Essentially, DLP solutions work to stop sensitive business data from being lost, leaked, or accessed by unauthorized users, whether that data is stored on-premises, in SaaS environments, or accessed on endpoint devices.
DLP tools enforce policies that control how data is handled, protecting information such as intellectual property, personal customer details, and regulated data like healthcare or financial records.
These tools use methods like content inspection, encryption, user activity monitoring, and alerting to detect risks and block accidental or malicious data exposure. This not only helps prevent costly data breaches but also supports compliance with regulations such as GDPR, HIPAA, and SOX.
According to reports, the global Data Loss Prevention market size is growing rapidly, expected to increase to $3.7 billion in 2025.
How Does Data Loss Prevention Work in Practice?
Data loss prevention (DLP) solutions are essential for safeguarding sensitive business information across various environments and preventing unauthorized access or leaks. Here's how DLP tools work in practice:
- Coverage Across Data States: DLP software protects data in use (on endpoints), in motion (transferred via email, web and APIs), and at rest (stored on file shares, databases, and cloud storage).
- Data Discovery and Classification: The DLP process begins with locating sensitive data—such as personally identifiable information (PII), financial records, or intellectual property—and tagging it according to sensitivity.
- Policy Creation and Enforcement: Security teams set granular policies determining who can access or share specific data types and under what conditions.
- Automated Response: When a policy violation is detected, DLP solutions can block data transfers, quarantine files, encrypt content, or send alerts to users and security teams. All actions are logged for audit and compliance purposes.
- Integration with Identity and Governance: To avoid disrupting everyday work, modern DLP software integrates with identity providers and Single Sign-On (SSO) to enforce role-based access and additional controls as needed.
- Enhanced Cloud Visibility: DLP connects with cloud access security brokers (CASB), SaaS security posture management (SSPM), and governance tools to enable automated access reviews and least-privilege policies.
- Unified Policy Management: By coordinating with identity platforms, DLP solutions enforce consistent security policies and just-in-time permissions across endpoints, networks, and SaaS apps.
What are the Three Different Types of Data Loss Prevention?
The three different types of Data Loss Prevention (DLP) cover distinct areas where sensitive data can be exposed or leaked: network, endpoint, and cloud. Each type focuses on protecting data in different states and environments to ensure a comprehensive defense strategy:
Network Data Loss Prevention (Network DLP)
Network DLP protects sensitive information as it travels across an enterprise’s network. It monitors and controls data in motion to prevent unauthorized transfer or leakage via email, web traffic, file sharing, and other communication channels.
Key elements include:
- Inspecting network traffic in real time using deep packet inspection for sensitive content.
- Enforcing policies like blocking, encrypting, or quarantining unauthorized data transfers.
- Deploying DLP sensors at strategic network points (e.g., gateways, firewalls) to monitor data flows.
- Integrating with other security tools such as firewalls and SIEM systems for centralized monitoring and incident response.
The goal is to block or alert on sensitive data leaving the network in unauthorized ways, ensuring compliance and reducing breach risks.
Endpoint Data Loss Prevention (Endpoint DLP)
Endpoint DLP focuses on devices like laptops, desktops, and mobile devices where data is stored (at rest) or actively used. It monitors and controls actions on endpoints to prevent leaks via USB drives, printing, screen captures, or unauthorized applications.
Key capabilities include:
- Monitoring file transfers and clipboard actions on endpoints.
- Controlling removable media usage and blocking unauthorized application access to sensitive data.
- Enforcing encryption or access controls locally on devices.
- Providing visibility into user behavior that could risk data exposure.
Endpoint DLP helps prevent data loss from insider threats, accidental mishandling, or compromised devices.
Cloud Data Loss Prevention (Cloud DLP)
Cloud DLP protects sensitive data stored, processed, or shared in cloud environments such as SaaS applications (e.g., email, file storage) and cloud platforms. It monitors data in motion to and from the cloud and enforces policies to prevent breaches or improper sharing.
Key features include:
- Scanning cloud content for sensitive information using content inspection and contextual analysis.
- Controlling sharing permissions, downloads, and uploads in cloud apps.
- Applying real-time enforcement, such as quarantine or blocking of risky actions.
- Integrating with cloud access security brokers (CASBs) and identity providers.
Cloud DLP addresses the growing use of cloud services and ensures data stays secure outside traditional network perimeters.
What is a Data Loss Prevention Tool?
A Data Loss Prevention (DLP) tool is a cybersecurity solution that protects an enterprise's sensitive and confidential data from unauthorized access, sharing, or leaks.
These tools monitor, detect, and prevent the inappropriate transmission or use of critical information, whether it is stored, being used on endpoints, or moving across networks and SaaS environments.
DLP tools work by first identifying and classifying sensitive data such as financial records, intellectual property, and personal information. They enforce security policies that define how data should be accessed, shared, or transmitted.
When a potential violation occurs, DLP tools can trigger alerts, block data transfers, encrypt information, or log incidents. They provide real-time monitoring and automated enforcement to stop data loss before it happens.
Key features of data loss prevention tools include:
- Continuous monitoring of data in use, in transit, and at rest,
- Content inspection and contextual analysis to detect sensitive information,
- Enforcement of access and sharing policies based on roles, data types, and compliance requirements
- Automated incident response, such as blocking, quarantining, or encrypting data,
- Detailed reporting and audit logs to support regulatory compliance and forensic analysis.
How CloudEagle.ai Prevents Unwanted Access and Protects Data?
CloudEagle.ai is an advanced SaaS management and governance platform that protects your enterprise’s sensitive data across SaaS applications by managing access and continuously monitoring user activity in real time.
Here’s how it prevents unwanted access and protects data:
Real-Time Monitoring and AI-Driven Alerts
By providing real-time monitoring and AI-driven alerts, CloudEagle.ai keeps your security team informed about suspicious activities, such as unauthorized data downloads or abnormal login attempts, allowing for rapid response to potential threats.

These real-time insights are crucial for maintaining a strong security posture, as they enable enterprises to act swiftly before incidents escalate. By leveraging AI to analyze vast amounts of user behavior data, CloudEagle.ai reduces false positives and focuses your team’s attention on genuine risks.
Automated User Provisioning and Deprovisioning
CloudEagle.ai offers an advanced automated user provisioning and deprovisioning capability. This means when employees join the enterprise, change roles, or leave, their access rights are automatically granted, adjusted, or revoked based on their current job responsibilities.

This automation removes the risk of human error and eliminates delays, which are common in manual access management, thereby reducing the chance of former employees or role-changed staff retaining inappropriate access to sensitive data.

Automating these processes also improves operational efficiency and streamlines onboarding and offboarding, ensuring users always have the right permissions at the right time without compromising security.
Know how Remediant streamlined user provisioning & deprovisioning and saved hundreds of hours in SaaS management.
Role-Based Access Controls (RBAC)
To further control access, CloudEagle.ai implements role-based access controls (RBAC), ensuring that users are only given permissions necessary for their specific job functions. By tightly restricting access based on roles, enterprises minimize the risk of accidental or malicious data exposure caused by unnecessary or excessive permissions.

Just-In-Time (JIT) Access Controls
Complementing RBAC, CloudEagle.ai offers just-in-time access controls, which allow users to gain temporary elevated privileges for specific tasks that expire automatically after a set timeframe. This reduces the window of vulnerability by limiting how long sensitive access is granted.

This feature allows temporary access for users who need elevated permissions only for a limited period. Access is automatically revoked after the set time expires.
Privileged Access Management
Another important aspect is privileged access management, which governs the use of accounts with high-level permissions over sensitive resources. CloudEagle.ai carefully monitors these privileged accounts, ensuring that only authorized individuals can use them, and that all privileged sessions are logged in detail for auditing purposes.
This tight supervision helps prevent abuse of access and insider threats by making privileged account usage transparent and accountable, a common vulnerability in many enterprises.
Centralized Audit Trails and Compliance Reporting
The platform also centralizes audit trails and compliance reporting by logging every user action, access request, and security event within the system. These detailed logs provide transparent records necessary for security reviews and compliance audits, helping enterprises meet standards like SOC 2, HIPAA, ISO 27001, and GDPR.

Automated compliance reporting saves time and increases accountability, making it easier for security teams to demonstrate adherence to regulatory requirements during audits.
Automated Access Reviews and Policy Enforcement
CloudEagle.ai continuously enforces security policies and performs automated access reviews that regularly check whether users still require their assigned permissions. This proactive enforcement prevents users from holding onto outdated or unnecessary access rights, which can become overlooked vulnerabilities in many enterprises.

When excessive or risky access is detected, CloudEagle.ai prompts appropriate actions to revoke or modify permissions promptly, reducing potential security gaps without waiting for manual intervention.
User-Friendly Access Requests and Approvals
The platform offers user-friendly workflows for access requests and approvals. Employees can easily request additional access as needed using the self-service app catalog, and these requests are routed to the right managers or data owners for timely approval or denial.

This streamlined process ensures secure and justified access without unnecessary delays, preventing security risks caused by informal or unauthorized sharing.
Top 10 Most Popular Data Loss Prevention Tools
Protect your sensitive business data with these top 10 most popular data loss prevention tools trusted by enterprises for strong security and compliance.
1. Symantec DLP
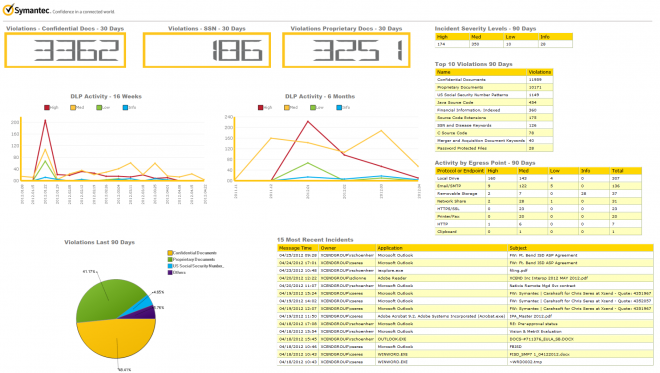
Symantec Data Loss Prevention (DLP) is a comprehensive data loss prevention tool that helps enterprises discover, monitor, and protect sensitive information across endpoints, networks, cloud apps, email, and storage.
Key Features
- Multi-Channel Data Protection: Monitors and controls sensitive data across email, web, endpoints, cloud apps, and storage to prevent unauthorized data sharing and leaks.
- Customizable Policy Engine: Centralized management with pre-built and customizable policies for GDPR, HIPAA, PCI-DSS, enabling tailored data loss prevention solutions.
Pros
- Flexible deployment options supporting on-premises and hybrid cloud environments.
- Advanced data fingerprinting (Exact Data Matching) reduces false positives in detecting sensitive data.
Cons
- Implementation can be complex and resource-intensive, requiring dedicated planning.
- Interface and reporting tools are less modern compared to newer AI-driven DLP tools.
Pricing
- Pricing for Symantec DLP varies based on deployment size, modules selected, and licensing agreements. For detailed pricing, contact Broadcom or authorized resellers directly.
2. Endpoint Protector By CoSoSys
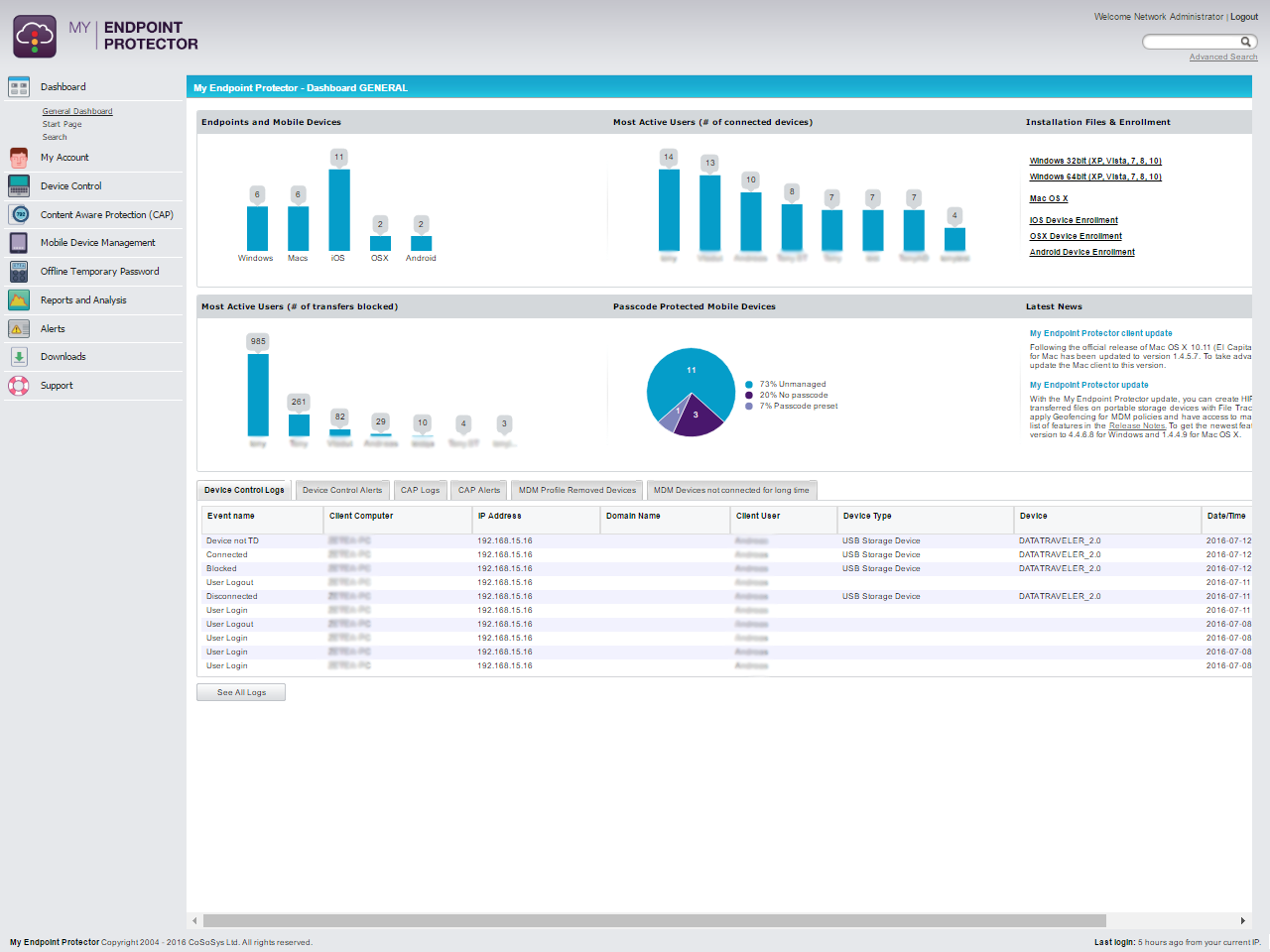
It is a strong data loss prevention tool that protects sensitive data on devices like laptops and desktops. It works on different operating systems to monitor and control data use, enforce rules, and stop unauthorized sharing or theft.
Key Features
- Device Control: Manages and restricts USBs and other peripheral devices to prevent data copying or theft.
- Content-Aware Protection: Scans data in motion, blocking sensitive information transfers based on content and context.
Pros
- Provides real-time alerts and detailed reporting to quickly detect and respond to risks.
- Helps companies meet compliance requirements like GDPR, HIPAA, and PCI-DSS with customizable policies.
Cons
- Integration with other security tools (SIEM or EDR) could be improved for a more unified defense.
- Some advanced data classification features are less automated compared to newer DLP solutions.
Pricing
- Endpoint Protector pricing depends on the deployment scale and modules selected. It is typically offered via enterprise licensing. For specific pricing details, contacting CoSoSys or certified partners is recommended.
3. McAfee
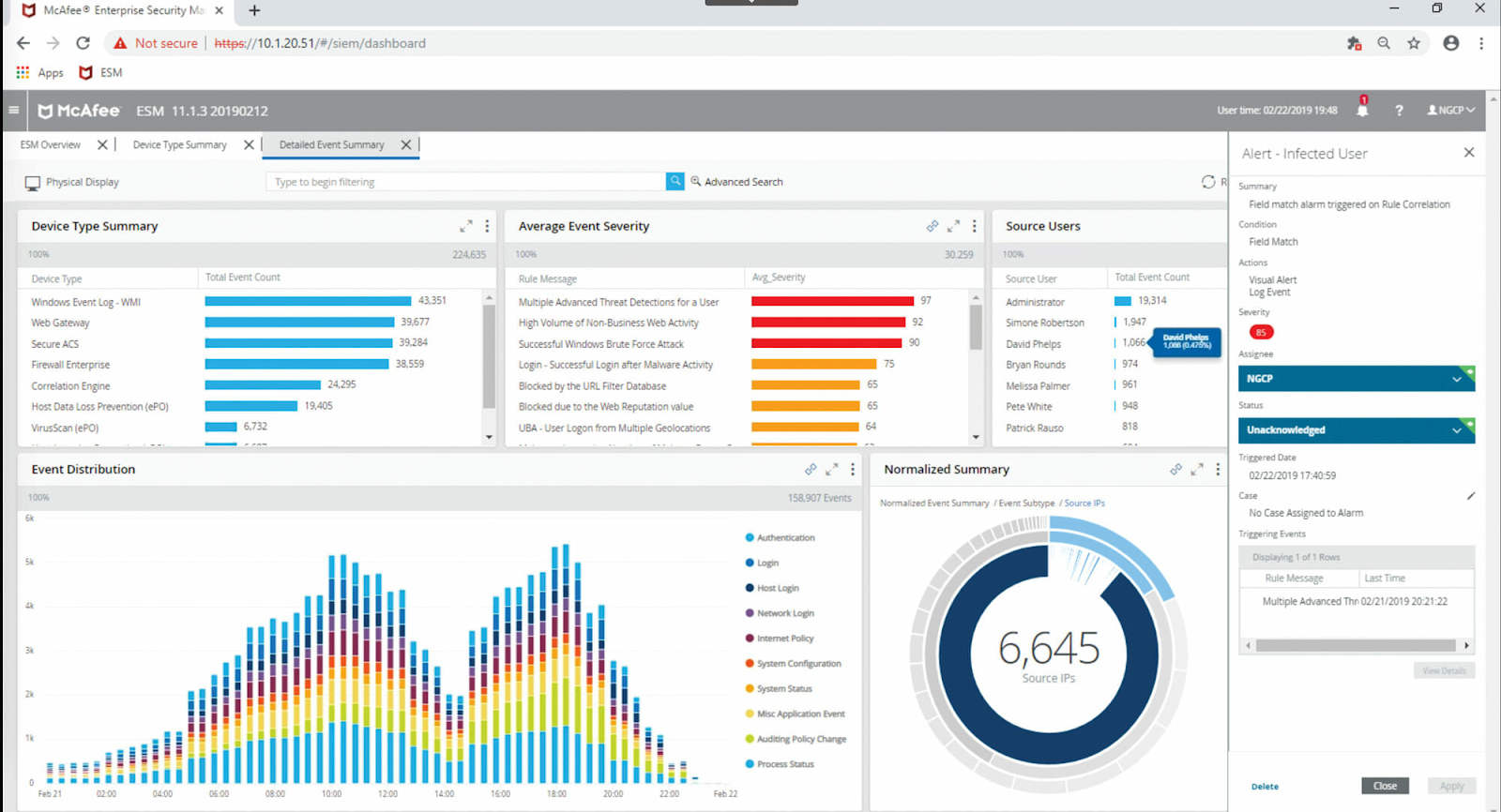
McAfee Data Loss Prevention software helps enterprises protect sensitive data from leaks across endpoints, networks, email, cloud, and removable devices. This data loss prevention tool scans, monitors, and enforces policies to prevent accidental or malicious data loss, supporting compliance and real-time protection of business-critical information.
Key Features
- Comprehensive Data Coverage: Monitors data in use, in motion, and at rest across endpoint devices, network traffic, cloud apps, and removable storage.
- Advanced Data Discovery and Classification: Identifies sensitive data with fingerprinting, classification, and tagging to target what needs protection.
Pros
- Wide-ranging protection covering all major vectors for data loss—network, cloud, endpoints, and email.
- Flexible deployment options with physical, virtual appliances, and endpoint agents.
Cons
- It can be complex to fully configure and manage for smaller teams.
- Some advanced features and integrations may need additional licensing or modules.
Pricing
- Pricing varies based on the number of endpoints, modules chosen, and deployment scale. McAfee typically offers enterprise licensing with tailored quotes. Contact McAfee or authorized resellers for specific pricing.
4. Forcepoint
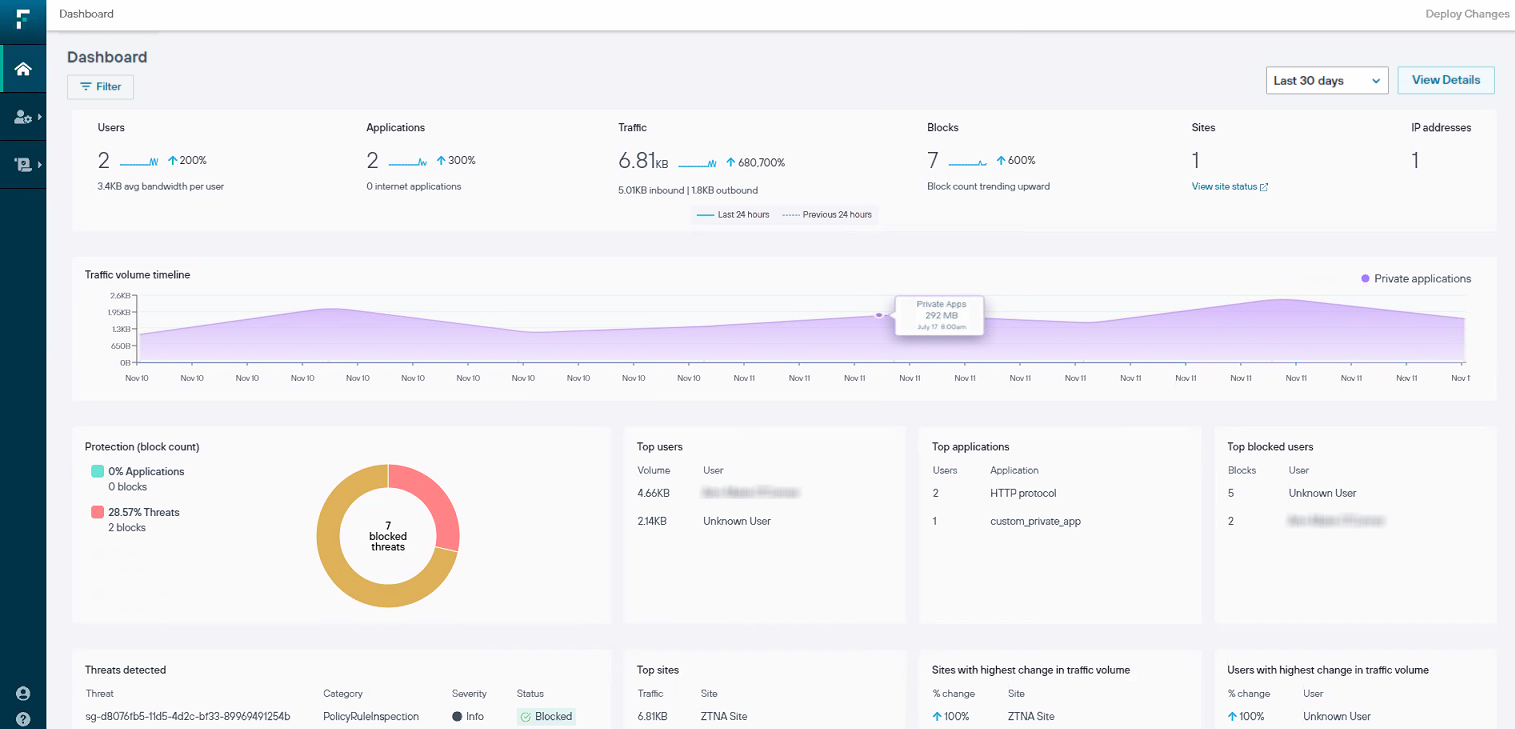
Forcepoint Data Loss Prevention software helps enterprises protect sensitive data by monitoring and controlling information across endpoints, networks, cloud, email, and web channels. It uses advanced analytics and adaptive policies to prevent data loss, detect risks in real time, and ensure compliance with regulations.
Key Features
- Comprehensive Data Coverage: Protects data at rest, in motion, and in use across Windows, Mac, cloud apps (like Office 365, Salesforce), email, and web uploads.
- Adaptive Risk-Based Protection: Uses behavioral analytics and risk scoring to enforce data loss prevention policies dynamically based on user risk levels.
Pros
- Strong integration with cloud applications and on-premises systems for broad data loss prevention coverage.
- Real-time monitoring with AI-powered analytics to detect insider threats and accidental leaks effectively.
Cons
- Initial setup and customization can be complex, requiring careful planning.
- Pricing and licensing details typically require direct vendor engagement, which can be a hurdle for smaller businesses.
Pricing
- Forcepoint pricing varies based on deployment scale, modules selected, and licensing type. It is generally offered as enterprise licensing. Contact Forcepoint directly for detailed quotes and options.
5. Digital Guardian
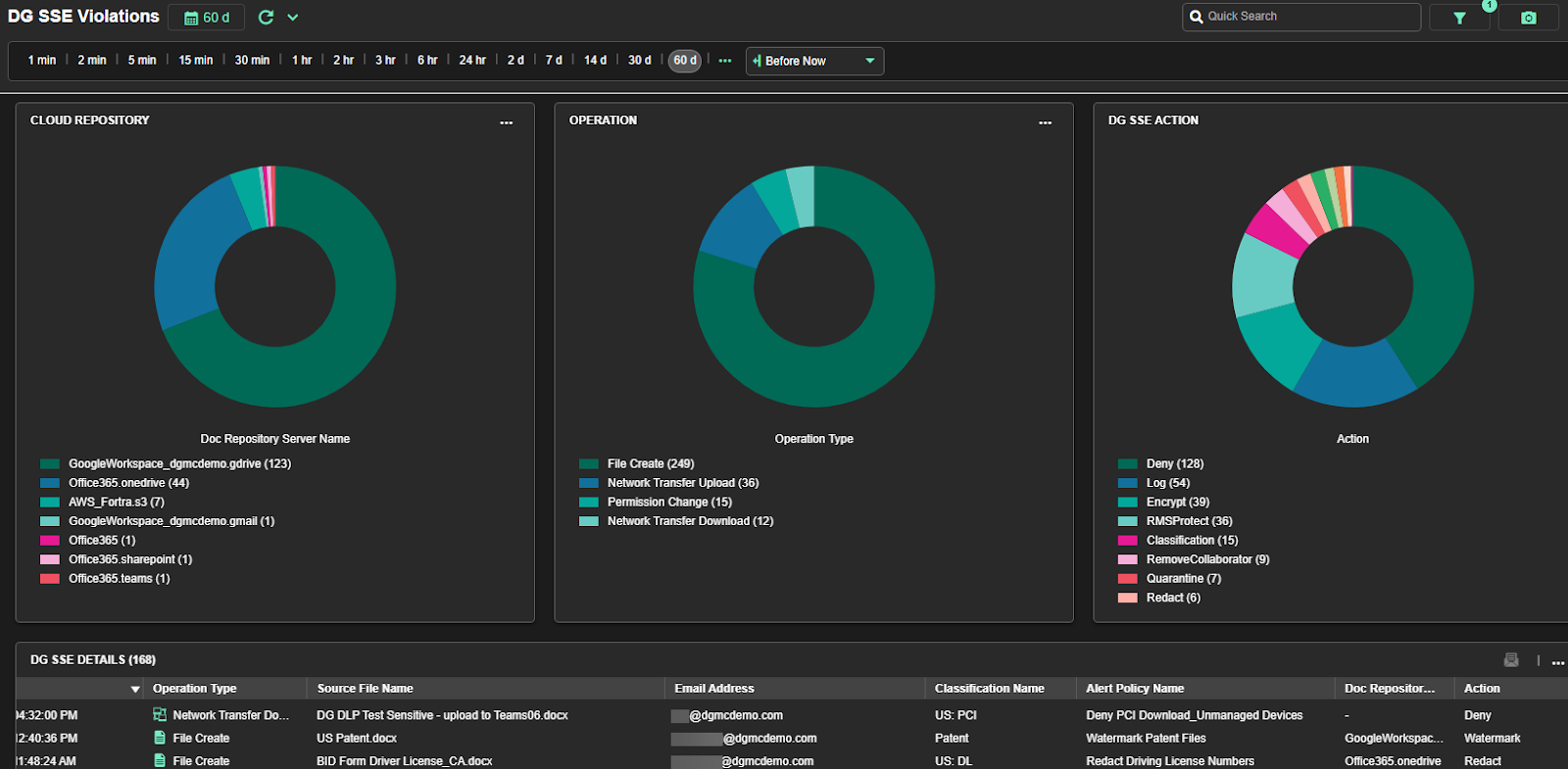
Digital Guardian is a powerful data loss prevention tool that helps enterprises protect sensitive business information by monitoring and controlling data use across endpoints, networks, and cloud environments.
Key Features
- Content and Context-Aware Protection: Controls data based on content, user actions, and context to accurately prevent unauthorized sharing or leakage.
- Comprehensive Visibility: Provides detailed monitoring of user activity, data movement, and risk events with real-time alerts to quickly respond to threats.
Pros
- Strong endpoint data protection that works both on and off the corporate network.
- Pre-built and customizable policies support compliance with GDPR, HIPAA, PCI, and other regulations.
Cons
- May require time and expertise for initial setup and tuning to align with business policies.
- Pricing and detailed licensing can be complex and require direct vendor consultation.
Pricing
- Digital Guardian pricing varies based on deployment size, chosen modules, and licensing type. It is generally provided via enterprise agreements. Contact Digital Guardian or authorized resellers for personalized pricing.
6. SecureTrust
SecureTrust DLP helps businesses find and protect sensitive data across networks, devices, and the cloud. It offers many ready-made policies that can be customized to stop unauthorized access and keep data safe while meeting compliance rules.
Key Features
- Advanced Content Control: Automatically blocks, encrypts, or quarantines communication that violates data policies across web, email, and file transfers.
- Real-Time Identity Matching: Detects risky actions and policy violations quickly by matching data and user identities in real time.
Pros
- User-friendly interface with strong visibility and control options for data loss prevention.
- Extensive predefined risk categories and compliance policies speed up deployment and enforcement.
Cons
- Initial configuration and tuning require expertise and careful setup.
- Integration options with other security tools are somewhat limited compared to some competitors.
Pricing
- Pricing for SecureTrust DLP is custom quoted based on business needs and deployment scale. For detailed pricing, contact SecureTrust directly for a tailored quote.
7. Sophos
Sophos DLP helps enterprises protect sensitive data by monitoring and controlling how information is used on endpoints, email, and removable devices. It is integrated into Sophos Endpoint and Email Protection, making policy creation, monitoring, and enforcement easy and user-friendly.
Key Features
- Content Monitoring and Control: Scans files, emails, and device transfers for sensitive data such as PII, credit card info, and company secrets to prevent unauthorized sharing.
- Endpoint and Email Integration: Embedded in Sophos endpoints and email security, providing seamless protection with alerts, blocking, and reporting on data loss attempts.
Pros
- Easy to deploy within the existing Sophos security ecosystem.
- Offers strong protection without needing additional software.
Cons
- Mostly limited to Sophos products, which may reduce flexibility for multi-vendor environments.
- Advanced DLP features are less extensive compared to standalone solutions.
Pricing
- Sophos offers flexible pricing, often bundled with endpoint or email protection licenses. A free trial is available, and detailed pricing is provided directly by Sophos or authorized resellers.
8. Trend Micro IDLP
Trend Micro IDLP is a data loss prevention tool integrated into Trend Micro’s security suite, designed to protect sensitive business data across endpoints, email, web, and cloud environments.
Key Features
- Comprehensive Data Discovery: Automatically identifies and classifies sensitive data across endpoints, networks, and storage to ensure no critical information is missed.
- Granular Policy Enforcement: Allows creation and enforcement of detailed DLP policies based on user, location, data type, and context to control data movement effectively.
Pros
- Seamless integration with existing Trend Micro security products for simplified management.
- Supports regulatory compliance with built-in templates and customizable policies.
Cons
- Full functionality often requires using other Trend Micro products, limiting flexibility for multi-vendor environments.
- Reporting and some advanced features may need enhancement for deeper analysis and cloud deployments.
Pricing
- Trend Micro IDLP pricing varies based on business size and selected features. It typically starts with a per-user annual licensing model starting around $24 per user. For exact pricing tailored to specific needs, contacting Trend Micro or authorized resellers is recommended.
9. Code42
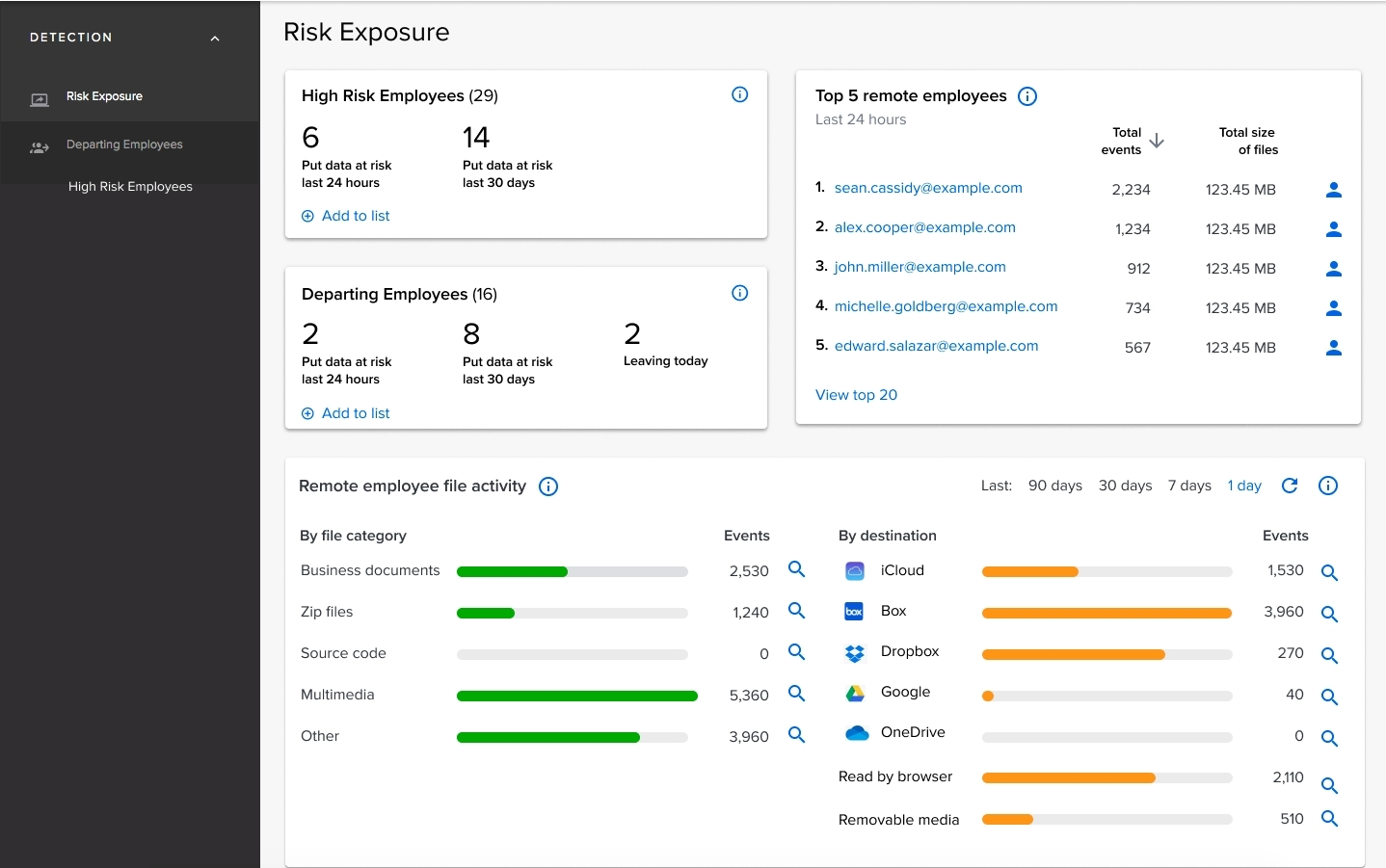
Code42 Next-Gen Data Loss Protection is a cloud-based tool that helps companies quickly find and stop insider threats and data leaks on devices and cloud systems. It gives full visibility into file activities and simplifies compliance with rules like GDPR, HIPAA, and PCI without complex policies or blocking work.
Key Features
- Insider Threat Detection: Continuously monitors file activity and user behavior to spot risky or unauthorized data movement.
- Automated Incident Response: Provides fast alerts and automated actions to quickly contain and remediate data loss incidents with minimal user disruption.
Pros
- Easy to deploy and manage with minimal impact on user productivity.
- Strong focus on insider threat detection and regulatory compliance.
Cons
- Primarily focused on insider threats rather than traditional DLP blocking.
- May require integration with other tools for broader data protection coverage.
Pricing
- Pricing for Code42 is typically subscription-based and varies based on deployment size and features. Contact Code42 or authorized resellers for detailed quotes.
10. Check Point
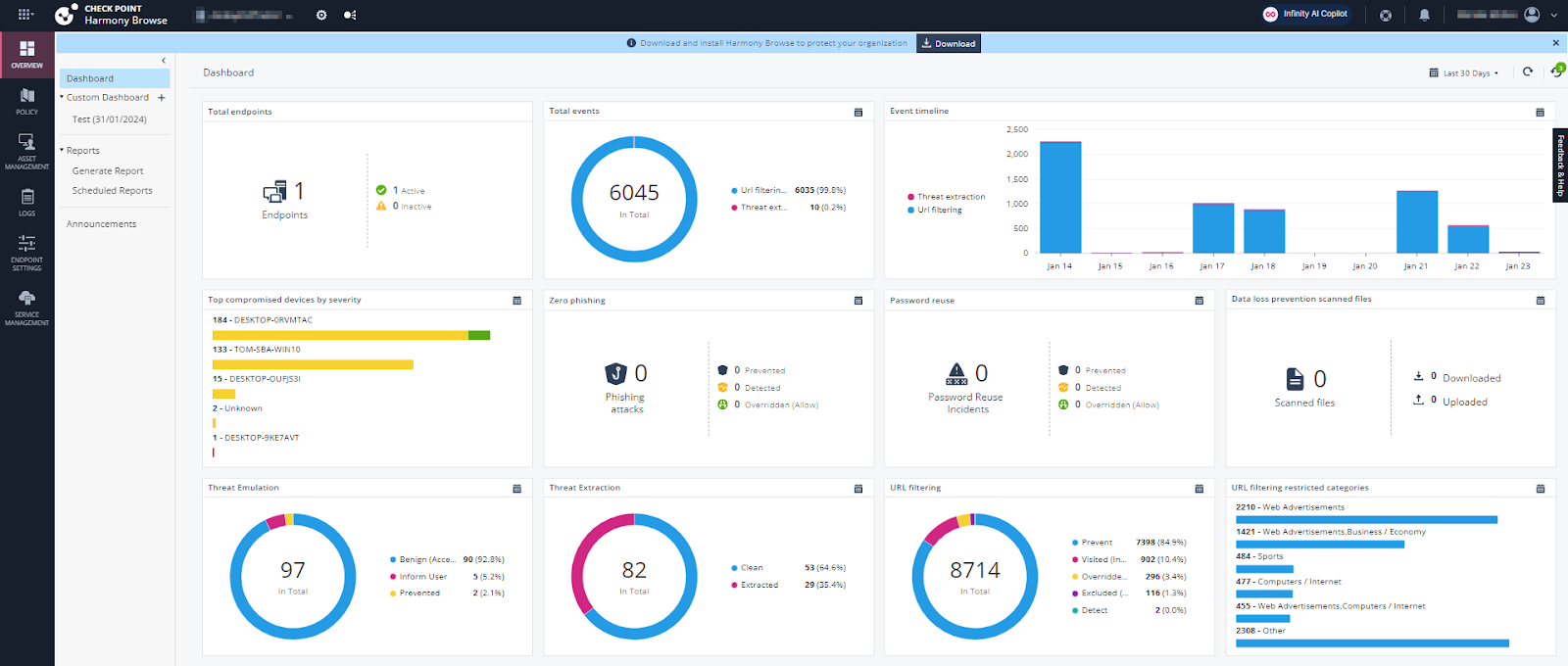
Check Point Data Loss Prevention (DLP) Software Blade combines advanced technology and processes to preemptively protect sensitive business data from accidental or intentional leaks. It uses innovative classification and user education to provide accurate, real-time data loss prevention across networks and endpoints.
Key Features
- MultiSpect™ Data Classification: Combines user, content, and process information to detect sensitive data accurately with minimal false positives.
- Network-Based Protection: Operates inline on existing Check Point gateways to monitor network traffic and enforce DLP policies without affecting performance.
Pros
- Self-educating system that reduces the need for constant IT intervention.
- High accuracy in identifying sensitive and regulated data types.
Cons
- Initial setup and customization can be complex.
- The user interface might feel outdated compared to newer DLP solutions.
Pricing
- Check Point DLP pricing depends on enterprise size, data coverage, and licensing. Contact Check Point directly for customized pricing.
What is the Landscape of Data Loss Prevention in 2025?
As organizations seek to safeguard sensitive business data in 2025, data loss prevention (DLP) solutions are evolving to address complex security challenges through comprehensive, integrated approaches. Below are key trends and considerations for selecting the right data loss prevention software:
- Full-stack coverage is becoming standard—modern DLP solutions protect data across network, endpoint, and cloud environments.
- Artificial intelligence is increasingly used to enhance detection accuracy and reduce false positives.
- Insider-risk analytics help identify unusual file movements and potential data leakage from within the organization.
- Seamless integrations with SaaS platforms enable organizations to enforce least-privilege access and maintain tight governance over sensitive information.
- Unified platforms that combine data loss prevention, access control, identity-driven governance, and cost management are now in demand.
- Enterprises with hybrid deployments benefit from robust, enterprise-grade DLP tools capable of handling complex environments.
- Cloud-first organizations often prefer DLP solutions featuring inline CASB (Cloud Access Security Broker) and API-based controls for visibility and policy enforcement.
- Industries with strict security requirements prioritize tools offering deep content inspection, device control capabilities, and audit-ready reporting to meet compliance objectives.
- Leading data leakage prevention tools achieve a balance between precision, performance, and integration flexibility to support compliance and operational goals.
- Review the top-10 DLP solutions listed below to identify the right fit for your organization's unique needs and security priorities.
Why Do Enterprises Need Data Loss Prevention Solutions?
Enterprises need data loss prevention (DLP) solutions to protect sensitive and critical business data from accidental or malicious loss, unauthorized access, or leaks that can disrupt operations, cause financial loss, and damage reputation.
Key reasons enterprises need DLP solutions include:
- Protecting sensitive data from theft, loss, or accidental exposure, whether data is in use, in transit, or at rest.
- Ensuring compliance with data protection regulations, avoiding fines and legal issues by enforcing policies and maintaining audit trails.
- Reducing financial and reputational risks associated with data breaches, ransomware, insider threats, and human errors.
- Enhancing data visibility and control with comprehensive monitoring, classification, and rapid incident response to mitigate damage quickly.
- Supporting business continuity by preserving data integrity and enabling fast recovery from incidents that would otherwise cause downtime or permanent data loss.
Key Trends Driving Data Loss Prevention Adoption
As organizations rapidly adopt SaaS platforms and embrace remote work, the traditional boundaries that once protected sensitive business information have faded. This shift has made data loss prevention (DLP) solutions essential for monitoring and protecting data across various environments.
Several key trends are driving the adoption and evolution of modern DLP tools:
- The widespread use of SaaS applications and remote workforces is dissolving traditional security perimeters, requiring DLP solutions that can continuously monitor data in use, in motion, and at rest across endpoints, networks, and cloud applications.
- Insider risk is on the rise, as contractors, third parties, and privileged users regularly access sensitive data driving the need for behavior-aware DLP software and granular, context-driven controls.
- Increasingly strict privacy and industry regulations (such as GDPR, HIPAA, PCI-DSS, SOC 2, and ISO 27001) are pushing enterprises to demonstrate robust policy enforcement and maintain audit-ready documentation of their data protection measures.
- DLP is converging with identity and access management, zero trust models, and SaaS governance tools—enabling integrated solutions that combine data loss prevention with dynamic access control, least-privilege principles, and automated access reviews.
- Organizations are seeking unified DLP and data leakage prevention tools that offer streamlined classification, role-based access, just-in-time permissions, and consolidated reporting, resulting in better governance, enhanced user experience, and lower operational costs.
How to Choose the Right Data Loss Prevention Software?
To choose the right data loss prevention (DLP) software, enterprises should consider several key factors that ensure the solution effectively protects sensitive data while fitting their environment and needs. Here are the essential criteria:
Features and Capabilities: Look for core DLP functionalities such as data discovery, classification, monitoring, and encryption. The following advanced features are also increasingly important:
- AI and Machine Learning-driven detection to reduce false positives and understand data context,
- User Behavior Analytics (UBA) to identify insider threats through anomaly detection,
- Real-time alerts with automated risk remediation (blocking, quarantining, encrypting),
- Integration with Digital Rights Management (DRM) for ongoing data protection even post-transfer.
Data Visibility and Classification: The DLP tool must provide comprehensive visibility across data at rest, in use, and transit. Dynamic and context-aware classification based on content, user, and context helps enforce appropriate policies.
Ease of Deployment and Integration: Consider how the DLP software fits with your existing infrastructure (endpoints, cloud apps, network). It should support rapid deployment with manageable complexity and integrate well with identity management and security platforms.
Policy Management and Enforcement: Evaluate the flexibility and granularity of the policy engine. The tool should allow customizable workflows and adapt policies based on varying risk levels, user roles, or locations.
Compliance Support and Reporting: Ensure the solution helps with regulatory compliance (GDPR, HIPAA, PCI-DSS, etc.) by offering audit trails, reporting, and compliance-ready templates.
Scalability and Coverage: The tool should support your business size and growth, covering endpoints, cloud environments, networks, email, and removable devices as needed.
Vendor Support and Cost: Factor in the vendor’s customer support quality, training options, and pricing models. Cost varies by deployment scale and modules selected, so seek transparent licensing options aligned with your budget.
Key Benefits of Implementing Data Loss Prevention Software
Data loss prevention software reduces breach risk by identifying and blocking risky transfers before sensitive data leaves your environment.
By safeguarding regulated information (PII, PHI, PCI) across endpoints, networks, and cloud apps, data loss prevention solutions help avoid fines, protect revenue, and preserve customer trust.
- Improved compliance posture: Prebuilt policies and audit-ready reporting simplify evidence collection, streamline audits, and lower the likelihood of regulatory penalties.
- Visibility into data flows: Continuous discovery and classification across data in use, in motion, and at rest accelerates investigations and cuts incident triage time.
- Stronger insider‑threat detection: User and entity behavior analytics flag anomalous downloads, bulk copies, or USB activity, enabling faster containment and reduced MTTR.
- Secure SaaS adoption: Fine‑grained controls for sharing, downloads, and external collaboration—plus integrations with SSO/CASB—let teams scale cloud tools without introducing data leakage risks.
- Operational efficiency: Centralized policies and automated remediation reduce false positives, shrink alert fatigue, and lower support costs.
For teams evaluating dlp tools and data leakage prevention tools, modern platforms answer what tools combine data loss prevention with access control by integrating with IAM and SaaS governance to enforce least privilege, further minimizing exposure while maintaining productivity.
Data Loss Prevention Best Practices for IT and Security Teams
Build a resilient DLP program with a phased, collaborative approach that protects data across endpoints, networks, and cloud tools while minimizing friction. Use data loss prevention solutions and data leakage prevention tools alongside identity controls to enforce least privilege and reduce risk.
- Discover and classify data first: scan endpoints, network shares, and SaaS apps; tag by sensitivity, residency, owner, and lifecycle.
- Align policies to regulations and business needs: map GDPR/HIPAA/PCI and IP protection to clear rules for channels, locations, and roles.
- Engage stakeholders: create a Security–IT–Legal/Compliance–HR–BU working group with defined RACI for approvals and exceptions.
- Pilot policies to cut false positives: start monitor-only on high-risk use cases (e.g., PII via email/cloud), measure precision, then enforce.
- Integrate DLP with IAM/SSO/IGA and SaaS governance: answer “what tools combine data loss prevention with access control?” by pairing DLP tools with identity workflows to auto-provision/deprovision and enforce least privilege.
- Roll out in phases: email/web gateways, then endpoint agents, then cloud app controls; use templates and adapt by region/role.
- Automate right-sized responses: coach/justify for low risk; encrypt/quarantine for moderate; block and alert for high severity.
- Operationalize: feed alerts to SIEM/SOAR, review KPIs weekly, tune classifiers, and maintain role-based training and incident runbooks.
Reassess classifications quarterly, test controls after SaaS or org changes, and leverage data loss prevention software analytics to continuously improve detection, response, and compliance coverage.
Open Source vs. Paid Data Loss Prevention Solutions
Organizations evaluating data loss prevention solutions often weigh open source options against commercial platforms based on budget constraints, technical resources, and compliance requirements.
Deep integrations with IT, security, finance, and HR platforms become critical factors in this decision, as modern enterprises need DLP tools that seamlessly connect across their technology stack.
Open Source DLP Solutions: Open source DLP solutions offer significant advantages but come with notable limitations:
- Advantages: Zero licensing costs, complete transparency into detection algorithms, and the flexibility to customize policies and workflows
- Limitations: Require substantial in-house expertise for deployment, offer limited out-of-the-box integrations with SSO providers and SaaS applications, and demand manual configuration of policy enforcement rules. Advanced analytics and automated incident response capabilities are often basic or require additional development effort
Commercial Data Loss Prevention Software: Commercial platforms deliver comprehensive capabilities designed for enterprise environments:
- AI-powered automation with no-code workflows that streamline employee onboarding, access reviews, and policy enforcement
- Vendor support and professional services for faster implementation
- Extensive compliance reporting and integration with identity management systems
- Sophisticated behavioral analytics for proactive threat detection
- Higher subscription costs offset by reduced operational overhead and faster time-to-value
Smaller teams with limited IT resources typically benefit more from commercial solutions, while larger, regulated enterprises may choose based on specific integration requirements and total cost of ownership analysis.
Conclusion
The global cost of cybercrime is predicted to hit $10.5 trillion by 2025, while the average cost of a data breach is about $4.88 million in 2024. Thus, Data Loss Prevention (DLP) solutions become vital for protecting sensitive information from leaks, insider threats, and cyberattacks.
The best DLP tools offer smart data discovery, accurate classification, real-time monitoring, and automated protections to stop unauthorized data use while helping businesses meet compliance requirements.
Top solutions like Symantec, Endpoint Protector, McAfee, Forcepoint, Digital Guardian, and CloudEagle.ai each have strengths that suit different business needs. Enterprises should choose based on features, ease of use, scalability, and support to find the right balance of security and cost.
Having a strong DLP strategy with the right tools helps enterprises lower risks, keep valuable data safe, follow regulations, and build trust with customers and partners in today’s digital world.
Are you ready to protect your sensitive data with confidence?
Schedule a demo with CloudEagle.ai to learn how you can strengthen your enterprise's security.
FAQs
1. What are DLP and SIEM?
Data Loss Prevention (DLP) protects sensitive data by monitoring and controlling how it is used. Security Information and Event Management (SIEM) collects and analyzes security data to detect and respond to threats. DLP stops data loss, while SIEM helps find and manage attacks.
2. How to keep customer data secure?
A firewall blocks unauthorized traffic at the network edge to protect the system. DLP monitors and controls sensitive data inside the enterprise to prevent leaks and misuse.
3. What is the difference between DLP and a firewall?
A Web Application Firewall (WAF) protects websites by blocking attacks on web apps. DLP prevents sensitive data from leaving the company accidentally or intentionally.
4. What are the three steps of DLP?
Data Loss Prevention involves three steps: first, discover and identify sensitive data; second, monitor its use and movement; third, protect it by blocking, encrypting, or alerting on unauthorized actions.
5. What types of data does DLP protect?
Data loss prevention software protects sensitive business information including personally identifiable information (PII), financial records, intellectual property, healthcare data (PHI), payment card information (PCI), and confidential documents across endpoints, networks, email, and cloud applications.
6. What are the main deployment models?
DLP tools typically deploy across three areas: endpoint DLP (protects devices), network DLP (monitors data in transit), and cloud/SaaS DLP (secures cloud applications and storage). Comprehensive protection requires coverage across all three environments.

%201.svg)








.avif)




.avif)
.avif)




.png)









