HIPAA Compliance Checklist for 2025

The CloudEagle IGA Report reveals a concerning gap: only 15% of organizations have adopted Just-In-Time (JIT) access, despite standing privileges being one of the most significant security risks today. Employees, contractors, and even ex-staff often hold onto access far longer than necessary, leaving sensitive systems exposed.
Ephemeral access closes this gap. By issuing short-lived, task-specific permissions that automatically expire, it eliminates lingering credentials, reduces the attack surface, and makes compliance easier to achieve.
In this article, we’ll cover what ephemeral access is, why it matters, practical use cases, and how it connects to ephemeral credentials and the ephemeral browser as part of a stronger identity and access governance strategy.
TL;DR
- Ephemeral access provides temporary, task-specific permissions that automatically expire, reducing the risks of overprivileged accounts, insider threats, and credential misuse.
- It works through just-in-time access, short-lived ephemeral credentials, and automatic revocation, aligning with Zero Trust and least-privilege principles.
- Common use cases include contractors and vendors, sensitive system access, cloud resource provisioning, and emergency response scenarios.
- Key benefits include stronger security posture, less operational overhead, and clearer governance with auditable logs.
- CloudEagle automates ephemeral access with provisioning, JIT workflows, and monitoring, turning manual, error-prone processes into secure, policy-driven, and audit-ready workflows.
What Is Ephemeral Access?
Ephemeral access is a modern security approach that gives users temporary permissions only for the time and task they need them and then revokes those permissions automatically. Unlike static access, which often lingers long after the job is done, ephemeral access ensures that every account or identity operates under the principle of least privilege.
Think of it as access on demand: permissions are spun up when required, tightly scoped to the task, and shut down once completed. This prevents overprivileged accounts from piling up, reduces insider threat risks, and makes it harder for attackers to exploit stolen logins.
In practice, ephemeral access works hand-in-hand with ephemeral credentials (short-lived tokens or certificates) and tools like the ephemeral browser to secure access to apps, systems, and cloud resources without leaving behind permanent doors for attackers.
How Ephemeral Access Works in Modern IT Environments
Ephemeral access is simple at its core: instead of leaving permissions open-ended, it grants them only when needed and takes them away the moment they’re no longer useful. Here’s how it plays out in modern IT setups:
Request and approval in real time
When a user needs to log into a system or pull sensitive data, they raise a request. Policies decide whether that request is valid, and access is approved instantly.
Short-lived credentials
The system issues ephemeral credentials such as tokens or certificates that live for a short period. They might last a few minutes, maybe a few hours, but never longer than the task itself.
Automatic expiration
As soon as the work is complete or the timer runs out, access is revoked automatically. Nothing lingers in the background, and there are no forgotten accounts to worry about.
Alignment with zero trust
Every new session requires verification. No assumptions or permanent trust. Even if someone manages to steal credentials, they expire before they can be misused.
Built for modern workflows
Cloud environments, DevOps pipelines, and third-party contractors all thrive on speed. Ephemeral access keeps up: permissions spin up quickly, scale with the workload, and vanish once they’re no longer required.
The end result: smoother workflows, fewer risks, and audit logs that are clean enough to satisfy even the toughest compliance checks.
Difference Between Ephemeral Access and Regular Access
The easiest way to understand ephemeral access is to contrast it with the “regular” access most companies still use. Regular access is static; once a user is added to a system or given credentials, they often keep them until someone remembers to revoke them. That might mean months of unnecessary privileges, long-forgotten logins, or even ex-employees still holding the keys.
Ephemeral access is dynamic. Instead of granting standing privileges, it issues time-bound permissions that expire automatically. Users only have what they need, when they need it, and nothing lingers once the task is complete. This makes access lightweight, auditable, and less tempting for attackers.
Here’s how the two approaches stack up:
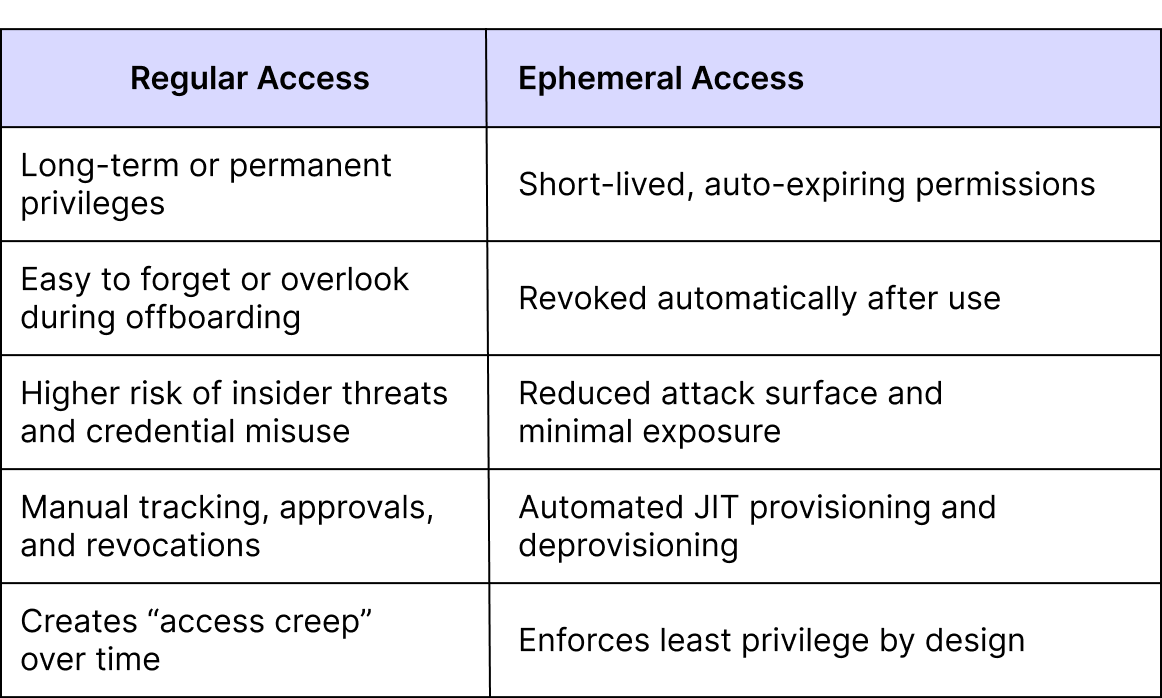
Put simply, regular access assumes trust until revoked; ephemeral access assumes no trust until proven necessary, and only for as long as required.
Why Ephemeral Access Is Critical for Security?
Ephemeral access is critical because it takes away one of the biggest weapons attackers rely on: time. It grants permissions only when needed and revokes them automatically once the task is done; this drastically reduces the window for misuse.
This time-bound approach limits damage from compromised credentials and enforces least privilege, supports Zero Trust practices, and relieves teams from the burden of manually tracking and revoking access.
Reducing Unauthorized Access Risks
Static credentials are an open door: if they’re stolen, attackers can use them for as long as they remain valid. With ephemeral credentials, that opportunity disappears.
Sessions are short-lived, permissions expire quickly, and access has to be re-requested each time, leaving little chance for exploitation.
Preventing Privilege Creep and Insider Threats
Over time, people collect permissions they no longer need: old project access, unused admin rights, forgotten logins.
This “access creep” creates risk, especially if insider misuse or account compromise occurs. Ephemeral access prevents this by wiping out privileges automatically, so users never keep access longer than necessary.
Meeting Compliance and Audit Requirements
Auditors care about accountability.
They want to know who had access, when, and why. Ephemeral access generates precise logs for every session, mapping permissions to specific requests and timeframes.
This makes compliance checks smoother and builds confidence that access governance is more than just a checkbox exercise.
Common Use Cases of Ephemeral Access
Ephemeral access is designed for situations where users need quick, limited access without leaving behind standing privileges.
Whether it’s an external vendor, a developer troubleshooting production, or a response team containing an incident, the model ensures permissions exist only as long as they’re needed. This makes it especially valuable in environments where agility and security must work hand in hand.
Temporary Permissions for Contractors and Vendors
Contractors and third-party vendors often need system access to complete projects, but keeping those accounts active after the work is done creates unnecessary exposure.
With ephemeral access, permissions are spun up at the start of the project and automatically revoked once it’s completed, ensuring outsiders don’t retain a permanent foothold in sensitive environments.
Just-in-Time Access for Sensitive Systems
Systems like production databases, financial platforms, or privileged admin consoles should never have standing access accounts lying around.
Ephemeral access provides just-in-time, tightly scoped permissions that vanish after use, so even high-value systems can be accessed securely without the risk of persistent credentials hanging in the background.
Temporary Cloud Resource Provisioning
Cloud environments are dynamic: resources are created and destroyed constantly.
Ephemeral access fits naturally here, allowing developers or engineers to provision temporary access to compute, storage, or test environments, and then automatically revoke it once tasks like deployment or staging are complete.
This not only secures resources but also improves operational efficiency.
Emergency and Incident Response Scenarios
When something breaks, security teams and engineers often need rapid access to systems they wouldn’t normally use. Granting permanent permissions for “just in case” moments is risky.
Ephemeral access solves this by enabling emergency, time-bound permissions that are revoked as soon as the issue is resolved, reducing the chance of lingering rights while keeping response times fast.
Benefits of Using Ephemeral Access Controls
The biggest benefit of ephemeral access is that it shuts down one of the most common risks in IT: credentials that live longer than they should.
It makes permissions temporary and task-specific, which enforces least privilege, blocks attackers from exploiting stolen logins, and prevents stale accounts from piling up.
Beyond security, ephemeral access also lightens the load for IT teams and creates cleaner audit trails for compliance.
Improved Security Posture
Every extra minute of unnecessary access is a potential opening for attackers. Ephemeral access minimizes that risk by issuing short-lived credentials that disappear automatically.
Even if compromised, those credentials expire quickly, limiting damage and aligning perfectly with Zero Trust practices.
Reduced Operational Overhead
Without automation, managing access means endless approvals, revocations, and manual cleanups.
Ephemeral access reduces this friction by provisioning accounts or certificates only when needed and retiring them instantly after use. IT teams spend less time chasing permissions and more time focusing on strategic security tasks.
Better Access Governance and Auditability
Traditional access logs are cluttered with accounts that remain active long after they’re useful. Ephemeral access provides clarity where each session has a defined start and end, tied to a specific user and task.
This creates reliable, audit-ready records that make compliance reporting easier and give leadership confidence that access is under control.
How to Implement Ephemeral Access Effectively
To make ephemeral access work in practice, organizations need more than a theoretical model. Success comes from clear policies, the right technology, and real-time monitoring.
The aim is simple: temporary access that’s easy to request, tightly controlled, and automatically revoked without adding friction for users or administrators.
Automating Temporary Access Requests and Approvals
Automation ensures temporary access can be granted quickly and consistently. Policies define who can request access, for which systems, and for how long.
Once a request is made, the system validates it and provisions permissions without waiting for manual intervention. For critical systems, approval steps can still be enforced, but automation keeps processes fast, reliable, and free from human error.
Integrating with Identity and Access Management (IAM) Tools
Integrating ephemeral access with IAM tools brings consistency across applications, cloud services, and on-premise systems.
Short-lived tokens, certificates, or accounts can be tied directly to user identities and roles already managed by IAM. This alignment ensures every access session follows existing governance frameworks while reducing the need for separate processes or shadow systems.
Monitoring and Revoking Access in Real Time
Access must be tracked as carefully as it’s granted. Real-time monitoring makes it possible to see who is connected, what resources they’re using, and how long they’ve had access.
When the task is complete or the time limit expires, permissions are revoked automatically. These session records provide a reliable audit trail that supports compliance reviews and strengthens accountability.
Ephemeral Access Best Practices for Organizations
Implementing ephemeral access effectively requires discipline. Temporary access alone won’t solve security challenges unless it’s paired with clear policies and consistent governance.
These best practices help organizations strengthen their approach and make ephemeral access sustainable.
Adopt the Principle of Least Privilege
Every access request should be evaluated against the minimum rights needed to complete the task.
Restricting permissions in this way keeps temporary accounts from becoming a hidden source of risk and limits the damage if credentials are ever compromised.
Use Role-Based and Attribute-Based Access Controls
Standardizing access with role-based access control (RBAC) and ABAC ensures permissions are granted logically and consistently. Roles determine what access a job function requires, while attributes such as department or location help fine-tune permissions.
This approach removes the guesswork from manual assignments and helps ephemeral access scale across large, complex environments.
Regularly Review and Optimize Access Policies
Policies must evolve as the business changes. Regular reviews highlight redundant rules, detect overly broad permissions, and confirm that ephemeral credentials are being used as intended.
Policy optimization also improves the user experience, ensuring employees can request and receive temporary access quickly without creating unnecessary security gaps.
Automating Ephemeral Access with CloudEagle
Manual processes make ephemeral access messy. Spreadsheets, delayed approvals, and forgotten revocations leave too much room for error and slow teams down.
Automation changes the game, like access requests move faster, permissions stay precise, and nothing lingers beyond its purpose.
Automated Provisioning and Deprovisioning: Creating and removing temporary accounts by hand often leads to delays or oversights. CloudEagle.ai automates the full lifecycle, spinning up access only when it’s needed and removing it the moment the task ends. Teams save time, reduce mistakes, and eliminate the risk of stale accounts.

Take RecRoom as an example. Their IT team struggled with offboarding employees across 100+ SaaS apps, leaving ex-staff with lingering access and wasting $200K annually on unused licenses. With CloudEagle’s Zero-Touch Offboarding, they cut lingering access by 75%, reduced offboarding time from 24 hours to under one, and unlocked $200K+ in yearly savings, while tightening compliance.
Just-in-Time Access: Many organizations still grant broad, standing access for convenience, which leaves systems exposed. With CloudEagle, access is approved only at the moment it’s required and scoped to the task at hand.
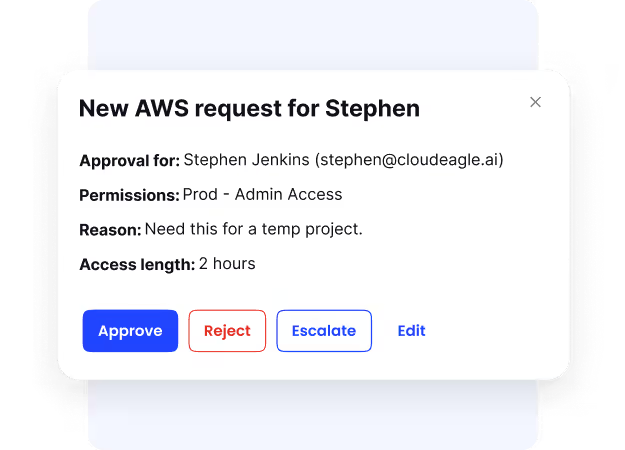
Once the work is complete, permissions expire automatically. This approach enforces least privilege, cuts down insider threats, and keeps sensitive data better protected.
Policy-Driven Workflows: Approvals can be inconsistent when handled manually. CloudEagle applies pre-set policies to each request, making sure access always aligns with identity, role, and business context.
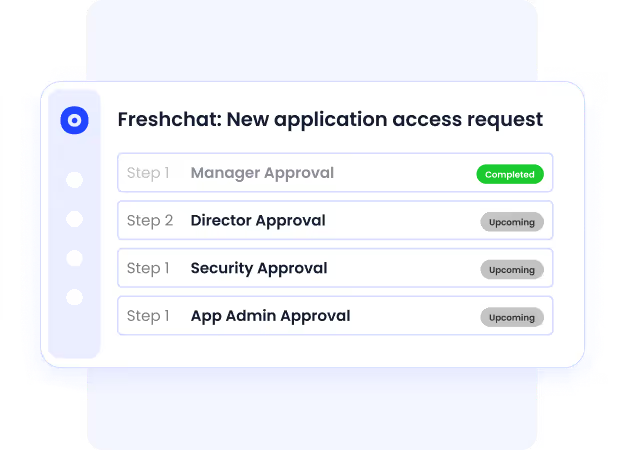
Security teams don’t need to micromanage, and employees don’t waste time waiting for approvals.
Integrated Monitoring: Logs scattered across multiple systems make audits painful. CloudEagle consolidates every access event into one clear trail, giving security leaders real-time visibility and auditors reliable records without the scramble.
No More Lingering Privileges; Automate Them Away
Ephemeral access shows that the strongest defense isn’t permanent barriers but temporary, well-scoped permissions. Done right, it reduces risks, blocks misuse, and makes compliance less of a burden.
CloudEagle automates this process end-to-end, such as provisioning, approvals, and revocations, so your team gets secure, just-in-time access without slowing down work. If standing privileges are keeping you up at night, CloudEagle turns them into short-lived, auditable sessions you can trust.
Ready to see it in action? Start your free trial or book a demo at CloudEagle.ai.
FAQs
1. What is ephemeral authentication?
Ephemeral authentication uses short-lived credentials, like tokens or certificates, that expire quickly after use. It enables secure, just-in-time verification without leaving long-term secrets behind for attackers to exploit.
2. What is ephemeral access?
Ephemeral access grants temporary, task-specific permissions that automatically expire after a set time or once work is done. It reduces overprivileged accounts, limits misuse, and aligns with Zero Trust and least-privilege principles.
3. What is an ephemeral user?
An ephemeral user is a temporary identity created for a specific purpose, such as a contractor or auditor. The user profile exists only for the required session or project, is then removed to prevent long-term security risks.
4. What is an ephemeral account?
An ephemeral account is a short-lived account provisioned for a task or session. It provides just-enough, time-bound access and is automatically deprovisioned once the work ends, eliminating lingering credentials or unused accounts.
5. What does ephemeral mean in cybersecurity?
In cybersecurity, ephemeral refers to something temporary and short-lived, like access rights, accounts, or credentials. Ephemeral methods reduce attack surfaces by ensuring permissions vanish when no longer needed.
.avif)
%201.svg)







.avif)




.avif)
.avif)




.png)









