HIPAA Compliance Checklist for 2025

Every enterprise needs to manage who can access its systems and data, especially in today’s cloud-first world. When choosing the right tools, many wonder about the difference between IAM and IGA. What do these terms mean, and how are IAM and IGA different?
IAM IGA solutions work together to keep your enterprise safe and running smoothly, but each has its job. You might hear people ask, “What is IAM/IGA?” or want to understand the IGA security meaning for their company. Simply put, IAM/IGA helps you control access and follow security rules, but in slightly different ways.
Let’s break down IAM vs. IGA, and explain the benefits these tools can bring to your enterprise.
TL;DR
- IAM controls access instantly by verifying identities and granting permission, while IGA manages and reviews user access over time to keep it safe and compliant.
- IAM performs immediate access decisions; IGA schedules periodic access reviews and certifications to manage risks like privilege creep.
- IAM uses role- or attribute-based access control to grant or deny access instantly; IGA focuses on role mining, attestation, and audit reporting to provide compliance evidence.
- IAM manages authentication and sessions, whereas IGA automates access requests, reviews, and governance workflows, often integrating with PAM, SIEM, and ITSM tools.
- Together, IAM and IGA reduce security risks, help meet regulations (SOX, HIPAA, GDPR), improve audit readiness, boost user productivity, and optimize operational costs.
What is Identity and Access Management (IAM)?
Identity and Access Management (IAM) is a system that helps enterprises control who can access their digital resources, like apps, data, and devices. It creates and manages user identities, verifies who they are through logins or multi-factor authentication, and decides what they are allowed to do.
IAM keeps your systems safe by making sure only the right people can access the right information at the right time. It also helps with tasks like adding new users, updating permissions, and removing access when needed.
Key Features of IAM:
- User Identity Management: Creates and manages digital identities for employees, partners, and customers.
- Authentication: Verifies users through passwords, multi-factor authentication (MFA), or other methods.
- Access Control: Grants or restricts access to applications and data based on user roles or permissions.
- Single Sign-On (SSO): Lets users sign in once and access multiple resources without logging in again.
- Password Management: Helps users reset and manage passwords securely.
Why IAM is Important for Enterprises:
CloudEagle.ai’s IGA report suggests that 28% of enterprises experienced major security incidents due to overprivileged access.
Thus, IAM is vital to stop unauthorized users from accessing sensitive information, protecting enterprises from cyber threats. It ensures the right people have access to the right resources, making operations safer and smoother.
This is why IAM and IGA often work together: IAM provides access control, while IGA governs and monitors those permissions over time. Understanding IAM security helps companies stay compliant with regulations and build stronger defenses.
What is Identity Governance and Administration (IGA)?
Identity Governance and Administration (IGA) is a system that helps enterprises manage and control user access over time to keep things secure and compliant. When comparing IGA vs IAM or asking “what is IAM/IGA,” remember that IGA focuses on overseeing and governing user permissions, making sure access stays appropriate as roles and needs change.
Key Features of IGA:
- Access Reviews: Regularly checks who has access to what and verifies if it’s still needed.
- Access Certifications: Let managers approve or revoke permissions to keep access up to date.
- Policy Enforcement: Ensures company policies for access are followed automatically.
- Role Management: Defines and maintains clear roles and associated permissions.
- Audit and Reporting: Tracks access changes and produces reports for compliance audits.
Why IGA is Important for Enterprises:
IGA adds an important layer of control beyond IAM by continuously monitoring and reviewing access permissions. This helps organizations reduce risks from over-privileged accounts and ensures compliance with regulations.
The IGA security meaning highlights that it’s not just about granting access but making sure that access is appropriate, tracked, and regularly updated. Together, IAM and IGA provide a complete solution for secure identity and access management.
According to CloudEagle.ai’s IGA report, Chetna Mahajan, Global CDO & CIO of Webflow, said: “IAM is often the most underfunded yet mission-critical part of security. But those taking a proactive approach, starting with automation and AI-driven governance, are not just reducing risk, they’re unlocking efficiency and long-term cost savings.” — Chetna Mahajan, Global CDO & CIO, Webflow.”
Key Differences Between IAM and IGA
When enterprises compare IAM and IGA, it’s important to know the main differences. Both work together to keep access secure, but they have different goals and ways of doing it.
Primary Objectives: Enforcement Vs. Governance
The main goal of IAM is enforcement. IAM systems focus on verifying user identities and controlling access in real time, deciding who gets in and what they can use.
In contrast, IGA is about governance, meaning it oversees and manages access over time, ensuring that permissions are appropriate, compliant, and regularly reviewed.
So, while IAM enforces access policies at the moment of login or request, IGA governs how access should be granted and maintained throughout a user’s lifecycle.
Timeframe: Real-time Controls Vs. Periodic Reviews
IAM works with real-time controls. It enables or blocks access instantly based on current authentication and authorization checks. On the contrary, IGA uses periodic reviews through scheduled access certifications and attestation processes.
IGA helps enterprises review, update, or revoke user permissions regularly to prevent over-privileged access, something IAM alone does not typically handle.
Policy Models: Rbac/abac Vs. Role Mining And Attestation
IAM mainly relies on policy models like Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) to assign and enforce access rights. These policies define who can do what based on roles or attributes.
Meanwhile, IGA focuses on role mining and attestation, which analyzes existing permissions to create or refine roles and requires managers to certify access validity. This helps maintain accurate access controls aligned with business needs.
Outcomes: Access Decisions Vs. Audit Evidence
The direct outcome of IAM is access decisions, granting or denying users access to systems and data in real time. IGA’s outcome, however, is audit evidence and compliance assurance.
IGA tracks and reports on access permissions, policy enforcement, and review results, helping organizations meet regulatory standards and prove good governance during audits.
Architecture And Tooling Distinctions
From a technical perspective, IAM solutions are designed to manage authentication, authorization, and user sessions. They integrate with apps and systems to control access immediately.
IGA solutions are built for comprehensive access governance, offering features like workflow automation for access requests, periodic access reviews, and detailed reporting. While there is overlap, IAM/IGA systems often come as complementary tools, IAM for enforcement and IGA for governance.
Let’s check out this table summarizing the differences between IAM and IGA.

How IAM and IGA Work Together?
IAM and IGA may focus on different parts of access management, but they complement each other to provide a complete security solution. By understanding how IAM and IGA work together, you can manage identities and access efficiently throughout the user lifecycle.
Here’s how IAM and IGA work together:
Shared Sources Of Truth And Hr System Of Record
Both IAM and IGA use the same trusted data, usually from the company’s HR system. The HR system keeps records of employee status, roles, and departments. This shared data helps IAM and IGA stay accurate and consistent, reducing mistakes and old access rights.
Joiner-mover-leaver Lifecycle Orchestration
IAM and IGA work together to manage the entire Joiner-Mover-Leaver lifecycle:
- Joiner: When new employees or contractors join, IAM creates their accounts and assigns initial access based on role, while IGA ensures these permissions follow policies and get reviewed.
- Mover: When employees change roles, IAM updates access in real time, and IGA governs the new permissions through reviews and certifications.
- Leaver: When employees leave, IAM automatically deactivates accounts, and IGA ensures all access rights are revoked to prevent lingering permissions.
Closed-loop Remediation And Revocation
IGA finds risky or wrong access during reviews and asks IAM to fix it right away. This creates a complete process: IGA manages and spots problems, while IAM quickly makes changes like removing or changing access. This teamwork lowers security risks and helps with compliance.
Integrations with PAM, SIEM, EDR, ITSM
IAM and IGA integrate with other key security and IT tools to strengthen protection:
- PAM (Privileged Access Management) controls and monitors high-risk accounts.
- SIEM (Security Information and Event Management) collects and analyzes security alerts.
- EDR (Endpoint Detection and Response) monitors device-level threats.
- ITSM (IT Service Management) handles service requests and workflows.
Example End-to-end Workflow
Imagine a new employee joining the company:
- The HR system updates its status.
- IAM automatically creates a user account and grants access based on the employee’s role.
- IGA schedules access reviews and certificates, ensuring the permissions remain appropriate over time.
- If a manager spots unnecessary access during a review, IGA triggers IAM to revoke it immediately.
This seamless collaboration between IAM and IGA helps enterprises maintain security and compliance while keeping access management efficient and user-friendly.
Why Must You Know the Differences between IAM and IGA?
Understanding the differences between IAM and IGA helps you implement the best possible systems that bring the most benefits to your enterprise. It ensures:
Risk Reduction From Excessive Privileges
IAM decides who can access systems, while IGA makes sure those permissions don’t get too broad over time. Without IGA checking regularly, users might keep access they don’t need, which can lead to security risks. Understanding the difference between IGA and IAM helps companies reduce these risks and protect important data.
Regulatory Alignment (SOX, HIPAA, GDPR)
Many laws like SOX, HIPAA, and GDPR require companies to prove they manage user access properly. IGA supports compliance by providing audit-ready reports and ensuring access policies are enforced and reviewed continuously. IAM provides the technical enforcement, while IGA offers the governance needed to meet regulatory standards.
Audit Readiness And Evidence Collection
IGA plays a key role in collecting detailed access records and certifications that auditors need to see. While IAM focuses on granting access, IGA tracks the why, when, and who behind those decisions. This helps enterprises pass audits easily and avoid penalties.
User Productivity And Self-Service Impact
IAM systems often include self-service features like password resets and access requests, which improve user productivity and reduce IT workload. IGA complements this by ensuring access requests follow proper approval workflows, balancing convenience with control.
Cost And Operational Efficiency
By clearly defining roles and automating access reviews, IGA cuts down on manual work and mistakes. Together with IAM’s automation of giving and removing access, businesses save time and money while staying safe. Knowing how IAM and IGA work helps organizations use their resources better.
Best Practices for IAM and IGA Implementation
Implementing IAM and IGA effectively helps enterprises secure systems, protect data, and stay compliant. Here are six simple best practices to guide a successful IAM/IGA rollout:
1. Start With Least Privilege And Role Engineering
The principle of least privilege means giving users only the access they need to perform their jobs. This reduces the risk of accidental or intentional misuse of access rights. Begin by carefully analyzing job functions and responsibilities to design clear roles with specific permissions.
Role engineering involves grouping users into roles based on their duties, helping enforce consistent and manageable access controls. This approach prevents over-provisioning and forms a solid foundation for IAM and IGA collaboration.
2. Define Guardrails And Exception Handling
A well-defined governance framework is essential for keeping access policies consistent and effective. Guardrails are the policies and rules that guide who can access what resources and under what conditions.
Alongside guardrails, define clear procedures for exception handling—how unique or temporary access requests are approved, monitored, and revoked. Having these policies documented and automated ensures IAM enforces access controls correctly, while IGA oversees ongoing compliance and governance.
3. Automate Provisioning With Approvals
Automating the provisioning process, including creating, modifying, and removing user access, makes it faster and less error-prone. However, automation must include approval workflows to maintain control and accountability.
For example, when a new employee joins, their manager or security team should approve their access requests before IAM grants permissions. This mix of automation and human oversight matches IAM’s role in enforcing access and IGA’s role in managing it, helping businesses stay secure without slowing down.
4. Schedule Risk-based Access Reviews
Access reviews are crucial to ensure users still need the permissions they have. Use IGA tools to schedule these reviews regularly, prioritizing high-risk accounts or access to sensitive resources first.
Risk-based reviews focus efforts where they matter most, reducing the chance of lingering overly broad access. Regular, automated certifications help organizations demonstrate compliance and minimize security gaps over time.
5. Track KPIs: TTP, Orphaned Accounts, SoD Violations
Monitoring key performance indicators (KPIs) is vital for measuring the effectiveness of your IAM and IGA programs.
- Time to Provision (TTP): Measures how quickly access is granted after a request, reflecting operational efficiency.
- Orphaned Accounts: Accounts belonging to users who no longer work for the enterprise; these represent security risks and require timely cleanup.
- Segregation of Duties (SoD) Violations: Conflicting permissions that could allow fraud or errors.
Tracking these KPIs helps security teams identify weaknesses, improve processes, and justify investments in IAM and IGA technologies.
6. Phased Rollout And Change Management
Rolling out IAM and IGA in phases helps manage complexity, reduce risk, and improve user adoption. Start with smaller departments or specific applications, learn from the rollout, and gradually expand.
Equally important is change management: communicating clearly about the benefits, providing training, and addressing user concerns. This ensures smoother transitions, helps build user trust, and maximizes the chance that staff will adopt and support the new IAM/IGA processes.
How CloudEagle.ai Simplifies Identity Access and Governance?
CloudEagle.ai is an advanced SaaS Management and Access Governance platform that helps IT and Security teams gain visibility, automate access, and maintain compliance; all while saving time and reducing software costs.
It connects with over 500 SaaS applications and integrates seamlessly with your existing IAM, SSO, and security tools, making it easy to secure and manage your cloud environment without major changes to your current setup.
Here’s how the platform simplifies IAM:
Complete Visibility into SaaS & AI Tools
Most enterprises don’t realize how many applications employees are using. Many of these apps are approved, but a large portion are adopted independently by teams or individuals without IT oversight.

This “Shadow IT” creates serious security and compliance risks while driving up costs. CloudEagle.ai automatically discovers every SaaS and AI application in use across the business, combining login, spend, and usage data into one dashboard.
With this complete visibility, IT teams can finally eliminate blind spots, consolidate redundant tools, and ensure tighter governance over the entire software stack.
Principle of Least Privilege
CloudEagle.ai helps enterprises enforce the principle of least privilege, making sure employees only have the access they truly need. Over time, many employees accumulate excessive rights, such as admin or super-admin access, which creates unnecessary risks. CloudEagle.ai continuously monitors and adjusts access to prevent this “privilege creep.”
By ensuring access stays minimal and role-appropriate, companies can protect sensitive data, reduce insider threats, and stay compliant with security regulations.
Zero-Touch Onboarding & Offboarding
Onboarding and offboarding are critical identity touchpoints, but when handled manually, they are slow, error-prone, and risky. CloudEagle.ai automates the process, ensuring every new hire gets access to all the right apps and tools from day one. This improves productivity, reduces ticket volume, and delivers a smooth digital employee experience.

Offboarding is just as critical. If handled manually, departing employees often retain access to sensitive applications, creating major security and compliance risks. CloudEagle.ai automatically revokes access to every tool the moment an employee leaves. This closes security gaps, prevents data leaks, and keeps your enterprise audit-ready.

Read this inspiring success story of how JoVe streamlined employee onboarding and offboarding with CloudEagle.ai.
Automated Access Reviews & Audit Readiness
Compliance requirements such as SOC2, GDPR, and ISO demand that enterprises regularly review access permissions. Unfortunately, manual access reviews are time-consuming, often inaccurate, and usually done only quarterly or annually.

CloudEagle.ai automates the entire access review process with AI-powered, continuous monitoring. It generates audit-ready reports at any time, reducing compliance preparation effort and ensuring no outdated permissions slip through the cracks.
Streamline Compliance Management
Managing compliance across hundreds of SaaS applications is challenging, especially when access controls and approvals are scattered across emails, spreadsheets, and tickets. CloudEagle.ai simplifies compliance management by centralizing policies and workflows into one platform.

Automated governance ensures access rules are consistently enforced, while detailed logs provide clear evidence during audits. This not only reduces the workload on IT and compliance teams but also ensures the business is always prepared for regulatory checks without scrambling at the last minute.
Privileged Access Management
Excessive privileged access is one of the biggest security risks companies face today. CloudEagle.ai gives IT teams complete visibility into who holds administrative or high-level access across all SaaS applications.
It automatically flags unusual or excessive privileges and revokes unnecessary rights. By tightening control over privileged accounts, organizations significantly reduce the chances of insider threats, accidental data exposure, or failed compliance audits.
Role-Based Access Management
Instead of giving access to apps one by one, CloudEagle.ai lets companies set access based on role, department, or seniority. For example, a sales manager gets Salesforce, Gong, and Zoom automatically, while a new engineer gets development tools on their first day.

Once these role-based policies are defined, CloudEagle.ai enforces them consistently across the organization, eliminating errors, reducing IT workload, and improving the employee experience with faster access to the tools they need.
Just-in-Time (JIT) Access
In many enterprises, temporary staff, contractors, or project-based workers are granted access that lasts far longer than needed. This creates unnecessary risks when accounts remain active after the work is complete. CloudEagle.ai introduces just-in-time access, allowing teams to grant temporary, self-expiring permissions.
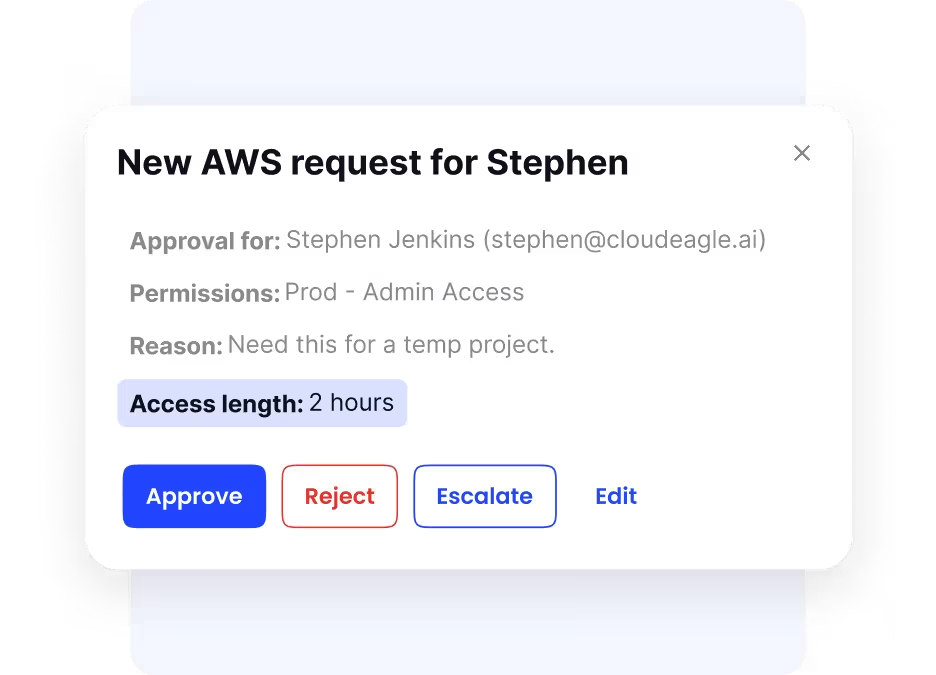
Once the task or contract ends, access is automatically revoked. This minimizes long-term exposure, prevents privilege creep, and ensures tighter security without slowing down productivity.
Centralized Employee App Catalog
Employees often struggle to know which apps are available or how to request them. Requests end up scattered across emails, chats, and ticketing systems, making it hard for IT to manage approvals or track compliance.
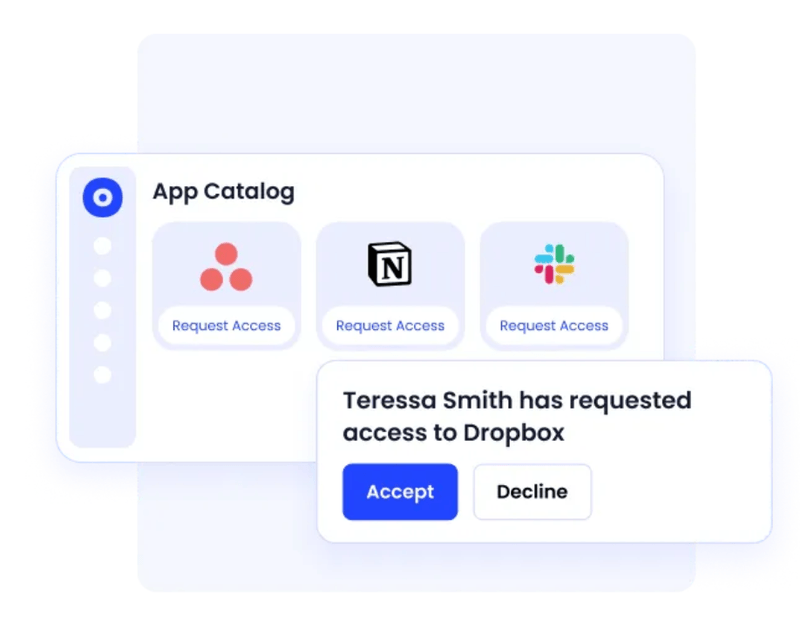
CloudEagle.ai solves this with a centralized self-service app catalog where employees can easily browse and request the tools they need. Automated approval workflows ensure requests are routed correctly, while IT gains complete visibility into access decisions. The result is faster fulfillment, happier employees, and a standardized process that supports compliance.
Take a look at this testimonial from Alice Park at Remediant, where she shares her experience with CloudEagle.ai. She describes how the platform simplified their access management and enhanced security.
Conclusion
To keep your enterprise safe, it’s essential to know exactly who can access your systems and data, and to ensure that access is always appropriate. Understanding the key differences between IAM and IGA is critical for this.
IAM controls access in real time, making sure only the right people can get in when they need to. Meanwhile, IGA provides ongoing governance by regularly reviewing and managing user permissions to prevent any outdated or excessive access.
Together, IAM and IGA form a complete security solution. This teamwork not only protects your company from security risks but also helps you stay compliant with important regulations like SOX, HIPAA, and GDPR.
If you want to strengthen your security, simplify access management, and keep your enterprise running smoothly, now is the perfect time to explore how IAM and IGA can help, especially with advanced access governance tools like CloudEagle.ai.
Are you ready to take the next step?
Schedule a demo with CloudEagle.ai and discover how you can protect your enterprise, boost compliance, and make managing user access easy and secure.
FAQs
1. What is IAM and IGA?
IAM controls who can access your systems and data in real time, while IGA manages and reviews user access over time to ensure it stays appropriate and compliant. Together, IAM and IGA help secure and govern enterprise access efficiently.
2. What does IGA stand for in IAM?
IGA stands for Identity Governance and Administration. It is a critical component within the broader IAM framework that focuses on governance, including regular reviews, access certifications, and policy enforcement to keep access permissions secure and compliant.
3. What is the difference between IGA, IAM, and PAM?
IAM manages user access and authentication, IGA governs and reviews access over time, and PAM (Privileged Access Management) specifically controls and monitors access for high-level or privileged accounts to prevent misuse of critical system controls.
%201.svg)








.avif)




.avif)
.avif)




.png)









