HIPAA Compliance Checklist for 2025

Have you ever wondered how enterprises keep their IT systems secure?
With more people working from home and cyberattacks becoming smarter, just using passwords isn’t enough anymore. In fact, weak or stolen passwords cause about 25% of data breaches, showing why advanced security tools like conditional access systems are so important.
Conditional access systems change security based on the situation instead of using the same password rules for everyone. Understanding how these systems work, including newer cardless conditional access systems, helps protect your information better.
These systems stop unauthorized access, help you follow compliance rules, and improve security; all without making it harder for users to get their work done.
Let’s explore what conditional access means, its benefits, and some best practices to build a strong conditional access system that fits your needs.
TL;DR
- Conditional access is a security method that grants or blocks user access based on set criteria in a policy, protecting resources while allowing secure access.
- A conditional access system uses conditional access system software to evaluate factors like user identity, device health, location, and risk before allowing access.
- Implementing effective conditional access policies reduces unauthorized access risk, improves compliance, and strengthens overall security without disrupting user experience.
- Conditional access policies include two main parts: conditions that specify access criteria, and access controls that enforce rules like multi-factor authentication or blocking access.
- Best practices include identifying use cases, defining conditions and controls, testing policies before rollout, and continuously monitoring and updating them.
What Is Conditional Access System?
A conditional access system is a security setup that controls who can access systems and data by checking certain conditions before allowing entry. It uses rules, called policies, to decide who can access what resources, from where, and under which situations.
These policies look at factors like user identity, device health, location, and risk level to make decisions in real time. This system helps enterprises keep sensitive information safe by making sure only authorized users who meet the set criteria can get access.
Unlike simple password checks, conditional access systems provide stronger, more flexible security. The software constantly evaluates these conditions, helping enterprises reduce the chance of breaches while keeping things easy for users.
By using conditional access, enterprises can apply security measures precisely, adjusting access as threats change and needs evolve. This balance of protection and usability makes conditional access a key part of today’s cybersecurity strategies.
What are the two main components of a Conditional Access policy?
A conditional access policy is made up of two key parts: Conditions and Access Controls.
1. Conditions: These are the rules that decide whether someone can access a system. These rules look at things like where the user is located, the health of their device, how risky the sign-in seems, or which user group they belong to.
2. Access Controls: These are the actions the system takes based on those conditions. For example, if the conditions are met, the system might allow access right away, ask for extra verification like multi-factor authentication, block access completely, or apply other security steps.
Together, these two parts work to keep your systems safe by adapting security measures in real time, depending on the situation.
What is an Example of a Conditional Access policy?
A simple example of a conditional access policy is: “Allow access to company email only if the user is signing in from a trusted device and inside the company network; if not, ask for extra verification like multi-factor authentication.”
This means the system checks the device and location before letting someone in, making sure sensitive information stays safe. If conditions aren’t met, it adds extra steps to protect the account.
This type of policy shows how conditional access systems work by adjusting security based on the situation. Instead of treating all access the same, they react to risks or unusual behavior, giving better protection than just using a password.
Is Conditional Access part of IAM?
Yes, conditional access is an important part of Identity and Access Management (IAM). IAM manages the user’s identity and controls who can access what. Conditional access adds more security by checking things like the device’s health, location, and risk level before allowing access.
With conditional access software, IAM can change the access rules depending on the situation. This means security is stronger and more flexible. It also helps companies follow rules and keep their systems safe, while still making it easy for users to sign in securely.
What are the Benefits of Conditional Access?
By implementing a strong conditional access system, enterprises can strike the right balance between security and convenience.
Enhanced Security with Risk-Based Access
A conditional access system evaluates risk factors such as user location, device security status, and authentication methods before granting access. This risk-based approach improves security by allowing access only when specific conditions are met, reducing the chances of unauthorized or risky sign-ins.
Improved Compliance and Governance
Conditional access policies help enterprises meet regulatory requirements by enforcing consistent and auditable access controls. Using conditional access system software, businesses can maintain governance over who accesses sensitive data and under what conditions, supporting compliance with industry standards.
Seamless User Experience
Conditional access is designed to be flexible, allowing legitimate users to access resources easily when they meet security criteria. This approach minimizes disruptions by triggering additional authentication steps only when necessary, providing a smooth experience without sacrificing security.
Reduced Exposure to Threats
By monitoring and enforcing access based on real-time conditions, a conditional access system reduces the risk of cyberattacks such as credential theft or compromised devices accessing critical systems. This dynamic control limits exposure to emerging threats and insider risks.
How Do I Turn On Conditional Access?
Turning on conditional access involves creating and enabling conditional access policies that define access rules based on specified conditions. Here’s a simple process to activate conditional access in your organization:
- Access your Conditional Access system software: Log in to your identity management portal, such as Microsoft Entra (Azure Active Directory). Navigate to the “Security” section, then select “Conditional Access.”
- Create a New Conditional Access Policy: Click on + New policy to start creating a conditional access policy. Give the policy a meaningful name that reflects its purpose.
- Define Assignments (Conditions): Choose Users and groups who will be subject to the policy. Select the cloud applications or resources the policy will apply to. Then specify the conditions necessary for access, such as device compliance, user location, sign-in risk, or client apps (browser, mobile, desktop).
- Set Access Controls: Under Grant controls, decide what requirements need to be met for access. This could require multifactor authentication, blocking access, requiring a compliant device, or other controls.
- Enable and Test the Policy: Before enforcing, consider turning the policy on in Report-only mode to observe its impact without blocking users. After testing, switch the policy status to On to enforce the conditional access rules.
- Monitor and Adjust: Regularly monitor policy reports and user feedback to fine-tune your conditional access policies for effective security without disrupting user experience.
Where are Conditional Access Rules Created?
Conditional access rules are usually created and managed within your identity management system. For example, in Microsoft Entra (formerly called Azure Active Directory), you will find these rules in the Conditional Access area of the security settings.
In Microsoft Entra, conditional access policies are made up of different rules. These rules include assignments, which decide which users, groups, or cloud applications the policy applies to.
They also include access controls, which say what conditions must be met for access to be allowed or blocked. You can create, change, and turn on these policies by going to Entra ID > Security > Conditional Access in the portal.
You can also set extra conditions, like trusted network locations, in a section called Named Locations. Here, you can add things like specific IP addresses or geographic regions. This helps decide if access should be granted or blocked based on where the user is signing in from.
How to Implement Conditional Access Policies?
By crafting strong conditional access policies, enterprises can protect resources while ensuring users have proper access. Here’s how to do it:
Identifying Use Cases for Policies
Start by figuring out the situations where conditional access makes the most sense. Common examples include protecting sensitive company data, requiring multi-factor authentication for users at higher risk, or blocking access from unsecured or unknown locations.
Knowing exactly when and why to apply these rules helps you create policies that focus on real security needs without causing unnecessary hassle for users.
Defining Conditions and Controls
Next, decide what conditions must be true for access to be allowed or denied. This could include which users or groups are involved, whether their device meets security standards, their network location, or if the sign-in looks risky.
After setting these conditions, choose the actions your policy should take—for example, ask for multi-factor authentication, allow access, or block it entirely. Conditional access system software lets you target these rules carefully so they apply only where needed.
Testing Policies Before Deployment
Before turning policies on fully, it’s important to test them. Many systems have a “Report-only” mode that shows how the policies would affect users without actually blocking or limiting access. Testing helps find any mistakes or unnecessary restrictions, so you can fix them early and ensure users won’t face problems once the policy is active.
Monitoring and Adjusting Policies Over Time
Once your policies are active, don’t just forget about them. Keep an eye on how they’re working using the logs and reports built into your conditional access software. Track access attempts, see how policies affect users, and watch for security alerts.
Regularly review and update your policies to keep them effective as your business changes and new threats appear. This ongoing care makes sure your conditional access system stays strong and useful over time.
How to Activate Conditional Access?
Activating conditional access involves setting up and enabling policies that apply security rules based on specific conditions, ensuring the right users access resources securely.
By doing this, you ensure that only the right people can access sensitive information safely, reducing the risk of breaches without making it harder for users to work.
Here’s how you can enable it:
Enabling Policies for Specific Users or Groups
The first step is to decide which users or groups the conditional access policy will apply to. For example, you might focus on high-risk users like administrators or employees handling sensitive data, or specific departments with stricter security needs. Targeting policies to only the necessary groups helps strengthen security where it's needed most, without restricting everyone’s access.
Your conditional access system software allows you to assign these policies precisely. This selective application means regular users who don’t need extra controls won’t face unnecessary hurdles. This approach makes security smarter, efficient, and less disruptive for most employees.
Assigning Conditions like Device, Location, or Risk
Next, you set the conditions that must be met for someone to get access. These often include ensuring the user’s device is compliant, meaning it is managed by the enterprise and meets security standards. You can also require users to connect from trusted networks, like inside the office or over a secure VPN.
Another important condition is assessing the risk level of a sign-in, which looks at factors such as unusual locations or suspicious behavior. By combining these conditions, the system can make smart, real-time decisions about whether to grant access, ask for extra verification, or block the request, greatly improving security.
Rolling Out Policies Gradually for Minimal Disruption
Introducing new conditional access policies right away can sometimes cause problems for users or break workflows. To avoid this, it is best to roll out policies slowly.
Most conditional access platforms include a “Report-only” or “Silent” mode, where the system monitors the effects of the policy without actually enforcing it.
This trial period helps administrators see how the policy affects users and] whether it might cause false alarms or block legitimate access. By testing and refining policies this way, you can ensure a smooth transition before fully activating the rules, which minimizes disruptions and keeps users productive.
How CloudEagle.ai Helps You With Conditional Access?
CloudEagle.ai is an advanced SaaS management and access governance platform that makes securing and managing your cloud environment easy and effective. It works smoothly with your existing IAM, SSO, and security tools, so you don’t need major changes to your current setup.
Here’s how CloudEagle.ai supports and strengthens your conditional access strategy:
Continuous User Behavior Monitoring
CloudEagle.ai monitors user activity in real time, tracking logins, access attempts, and unusual behavior across multiple cloud apps. This continuous monitoring helps detect risk patterns such as access from unfamiliar locations, repeated failed logins, or usage outside standard hours.

Early detection allows you to take timely action before a security issue escalates, adding a vital layer of protection to conditional access policies.
Automated Access Provisioning and Deprovisioning
Managing user access manually can lead to errors and delays. CloudEagle.ai automates this process by aligning access rights with user roles and changes in employment status.

When a user’s role changes or they leave the company, CloudEagle.ai automatically updates or removes their access. This reduces the risk of over-privileged accounts remaining active and eases administrative burdens, ensuring your policies are enforced consistently.

Know how JoVe streamlined employee onboarding and offboarding with CloudEagle.ai.
Role-Based Access Control (RBAC) Enforcement
With CloudEagle.ai, you can define finely tuned roles and assign specific permissions based on job functions. RBAC ensures users have only the access they need to perform their tasks.

CloudEagle.ai automates role assignments and policy enforcement, simplifying management while boosting security by avoiding excessive permissions.
Advanced Privileged Access Management (PAM)
CloudEagle.ai adds strong controls on high-level administrative accounts. It monitors privileged access, enforces the least privilege principle, and can require additional verification steps to access critical systems. This reduces the risk of misuse or compromise of powerful accounts within your environment.
Just-In-Time (JIT) Access Management
CloudEagle.ai enables just-in-time access, granting users temporary permissions only when needed and for a limited time. This minimizes standing privileges, which are often targets for attackers. JIT access limits exposure to sensitive resources, supporting a zero-trust approach where access is granted only as required, reducing the attack surface in your environment.
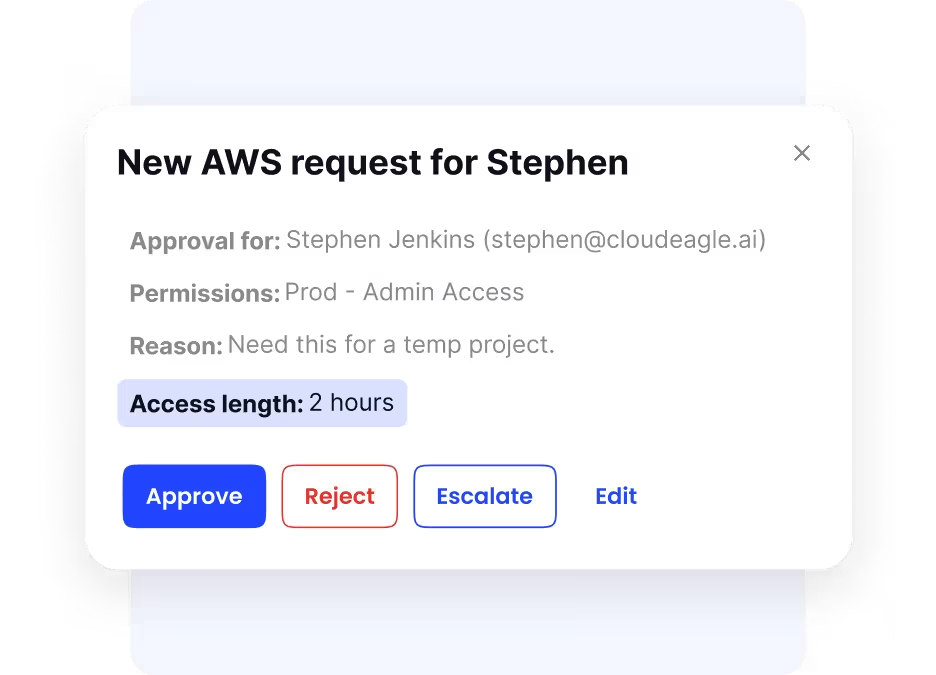
Regular Access Reviews and Certifications
‘To maintain strict control over who can access what, CloudEagle.ai automates scheduled access reviews. Stakeholders receive reminders to review and certify user access rights regularly. This helps detect outdated or unnecessary permissions, keeping your environment compliant with internal policies and external regulations.

Comprehensive Audit Trails and Compliance Reporting
CloudEagle.ai keeps detailed logs of all access activities, policy changes, and enforcement events. These audit trails support transparent reporting and help meet compliance requirements for standards like GDPR, HIPAA, and SOX. Easily generate reports to demonstrate that your conditional access policies are being followed and to support security audits.

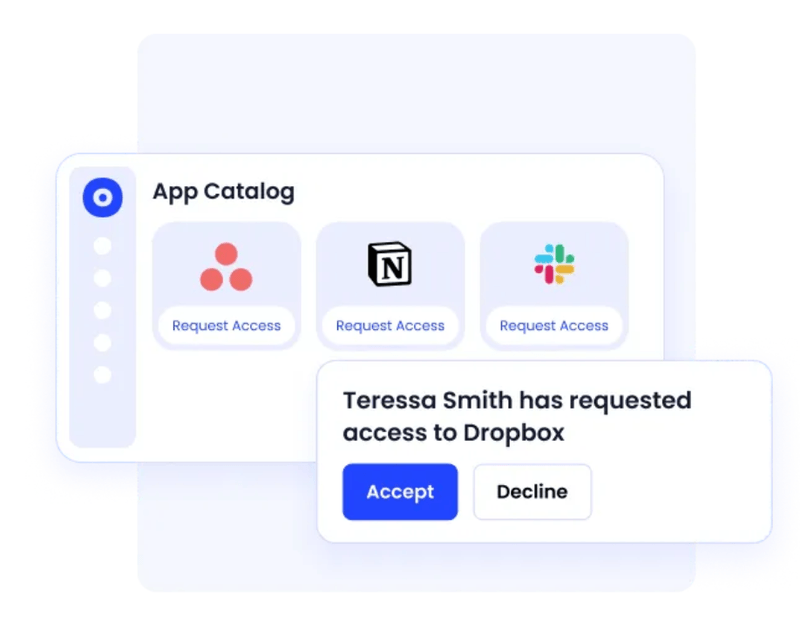
Self-Service Application Access Portal
Users can request access to SaaS applications through a simple, user-friendly self-service app portal powered by CloudEagle.ai. This reduces the workload on IT teams and speeds up access approval processes, all while ensuring access requests go through the proper approval workflows aligned with your conditional access policies.
Adaptive Policy Enforcement with Risk-Based Controls
CloudEagle.ai enhances conditional access with flexible, risk-based controls. It adjusts security requirements based on factors like device health, geographic location, and unusual user behavior. This dynamic approach strengthens security by raising barriers in risky situations while allowing smooth access in low-risk contexts, improving user experience.
Listen to Alice Park from Remediant as she shares her experience using CloudEagle.ai. She explains how the platform helped simplify their access management processes while boosting security.
Conclusion
Conditional access helps organizations control who can use their important systems and data by checking conditions in real time. Setting up clear policies and strong systems improves security, keeps users safe, and makes access easy.
CloudEagle.ai supports this by automating access management, watching user activity, and applying smart rules based on risk. It works smoothly with your existing tools, making it easier to protect your business.
Whether it’s checking devices, locations, or using risk-based controls, conditional access is key to modern security. Using best practices like testing policies and regularly monitoring keeps protection strong as threats change.
Choosing conditional access is a smart way to keep your data safe while staying flexible and running smoothly.
Are you ready to strengthen your enterprise security?
Schedule a demo with CloudEagle.ai to see how conditional access can protect your business.
FAQs
1. What is the difference between MFA and Conditional Access?
Multi-factor authentication (MFA) requires users to verify their identity through multiple methods. Conditional access is a broader framework that uses specific conditions to determine when MFA or other security measures should be enforced.
2. Does Conditional Access require MFA?
Conditional access does not always require MFA. It depends on the conditions set within the policy. MFA is one of several controls that conditional access can enforce based on risk, device status, or user location.
3. Where are Conditional Access rules?
Conditional access rules are created and managed in identity management platforms like Microsoft Entra, typically found under the Security or Conditional Access policies section.
4. What are Conditional Access policies used for?
Conditional access policies enforce security by controlling access based on user identity, device compliance, location, and risk. They help protect sensitive data and ensure compliance with organizational security requirements.
5. What is the limit of Conditional Access rules?
The number of conditional access rules depends on the platform. For example, Microsoft Entra supports many policies, but it’s important to manage them carefully to avoid complexity and conflicts.

%201.svg)








.avif)




.avif)
.avif)




.png)









