HIPAA Compliance Checklist for 2025

Did you know that 81% of data breaches are caused by weak or stolen passwords (Verizon DBIR)? That alarming figure highlights why enterprises are turning to Identity and Access Management Benefits to secure their digital ecosystems.
Every employee, contractor, and partner adds new user identities that must be secured, monitored, and controlled. Without the right framework, unmanaged access privileges, unsecured devices, and weak passwords can create major security risks.
This is why enterprises are investing in identity and access management solutions. Beyond just protecting sensitive data, the top Identity and Access Management Benefits include stronger compliance, reduced IT costs, and improved user experience across all platforms.
In this blog, we’ll explore the 10 Identity and Access Management Benefits that matter most, why IAM is critical for your enterprise, and how to maximize these gains with the right IAM tools.
TL;DR
- Identity and Access Management (IAM) secures data, prevents unauthorized access, and ensures compliance across enterprises.
- Key Identity and Access Management Benefits include automation, visibility, and reduced human error.
- Features like RBAC, JIT access, and automated reviews prevent privilege creep and streamline governance.
- IAM training boosts security awareness and helps employees manage access responsibly.
- CloudEagle.ai simplifies IAM with automated provisioning, detailed usage insights, and compliance-ready audits.
What is Identity and Access Management
Identity and Access Management (IAM) is a framework of policies, processes, and technologies that allows enterprises to securely manage user identities, control access privileges, and protect sensitive data across all platforms.
IAM ensures that the right employees, contractors, and partners have access to the right resources at the right time, while preventing unauthorized access and reducing security risks.
Key features include:
- Authentication and Authorization: Verifying users and granting access based on roles.
- User Lifecycle Management: Automating onboarding, offboarding, and access adjustments.
- Single Sign-On (SSO) and Multi-Factor Authentication (MFA): Enhancing security and simplifying login experiences.
- Audit and Compliance: Maintaining logs to meet regulatory requirements like HIPAA, GDPR, and SOX.
By implementing IAM, enterprises not only strengthen security but also streamline operations, reduce IT costs, and enhance the overall user experience.
Why IAM is Important for Enterprises?
IAM is essential for enterprises as it strengthens security by blocking unauthorized access, ensures compliance with data protection regulations, boosts efficiency through streamlined access controls, and enables secure collaboration to drive digital transformation across platforms.
Before exploring the top Identity and Access Management Benefits, it’s crucial to understand why IAM has become indispensable for enterprises.
Rising Cybersecurity Threats in Cloud Environments
As enterprises migrate workloads to cloud platforms, cybercriminals are targeting weak passwords, compromised devices, and stolen sets of credentials. This increases the risk of data breaches and exposes organizations to insider abuse.
IAM systems mitigate these risks by:
- Enforce multi-factor authentication (MFA) for stronger login security.
- Monitoring user behavior for unusual activity.
- Applying the principle of least privilege to limit unnecessary access permissions.
70% of organizations report at least one instance of insider misuse in the last year. Moreover, 81% of breaches involve weak or stolen passwords, highlighting the importance of IAM in securing employee access and credentials
Complex User Identities Across Hybrid Workforces
Managing user identities across a distributed workforce is no easy task. Enterprises must control access for full-time employees, contractors, and vendors, each requiring different access privileges.
Without the right IAM tools, this can lead to:
- Forgotten or orphaned accounts after offboarding.
- Mismanaged user roles and excessive privileges.
- Shadow IT and unmanaged assets across multiple platforms.
Studies show that enterprises with poor IAM governance experience up to 60% more unauthorized access incidents compared to organizations with automated IAM controls
An effective IAM solution simplifies user management, enforces role-based access control, and ensures only authorized users have secure access.
Growing Regulatory and Compliance Demands
Data protection regulations such as GDPR, HIPAA, and SOX demand strict identity management controls. Non-compliance can result in hefty fines and loss of customer trust.
IAM helps enterprises stay compliant by:
- Maintaining detailed audit logs of all user access activities.
- Enforcing identity governance and clear directory service policies.
- Aligning access control with regulatory requirements.
Business Need for Streamlined Access Control
Manually managing access rights is time-consuming for IT teams and prone to errors. Missed de-provisioning or excessive privileges can open the door to insider threats.
With IAM, enterprises can:
- Automate user lifecycle management from onboarding to offboarding.
- Improve operational efficiency with reduced IT overhead.
- Guarantee secure access for all employees across multiple platforms.
The Shift to Zero Trust Security Models
Traditional perimeter-based security is no longer sufficient. Enterprises are embracing Zero Trust, where no user identities or devices are trusted by default.
“Zero Trust without effective IAM is just theory. Identity is the new perimeter, and access management is the first line of defense.” – Michael Hill, Security Strategist
IAM supports this shift by:
- Enforcing single sign-on (SSO) and multifactor authentication.
- Continuously monitoring user behavior to detect anomalies.
- Applying the principle of least privilege for all access privileges.
10 Identity and Access Management Benefits Enterprises Should Know
Identity and Access Management (IAM) enables enterprises to securely control user access, prevent data breaches, boost productivity with SSO and automation, streamline compliance, reduce IT costs, and enhance the overall user experience.
Now that you see why IAM is essential, let’s dive into the 10 key Identity and Access Management Benefits enterprises can’t afford to overlook. These benefits extend beyond password protection, helping organizations strengthen security, lower costs, and deliver a seamless experience for employees across all platforms.
1. Enhanced Security Against Unauthorized Access
One of the biggest Identity and Access Management Benefits is protection against the risk of unauthorized access. IAM enforces robust security measures like multi-factor authentication (MFA), privileged access management (PAM), and the principle of least privilege.
Organizations implementing MFA and privileged access management report 50–70% fewer security incidents
Key advantages include:
- Verifying each login attempt with multi-factor authentication.
- Restricting access rights to only what user roles require.
- Preventing insider threats by monitoring user behavior in real time.
2. Simplified User Authentication Across Applications
Enterprises often rely on dozens of platforms and SaaS apps. Managing multiple sets of credentials leads to weak passwords and frustrated employees. A major Identity and Access Management Benefit is the ability to unify authentication.
With single sign-on (SSO) and multifactor authentication, enterprises can:
- Allow seamless user access across all business apps.
- Reduce password fatigue while improving user experience.
- Guarantee secure access without sacrificing convenience.
3. Improved Compliance With Regulations (HIPAA, GDPR, SOX)
Meeting global regulatory requirements is a top challenge for IT administrators. Another critical Identity and Access Management Benefit is helping enterprises stay audit-ready.
IAM makes compliance easier by:
- Enforcing identity governance and role-based access control.
- Maintaining detailed audit logs of all user access activities.
- Ensuring only authorized user roles can reach sensitive data.
4. Reduced IT Costs Through Automated Processes
Manually managing user management, credential management, and access rights consumes valuable time. One of the most practical Identity and Access Management Benefits is reducing costs through automation.
With IAM automation, enterprises can:
- Automatically provision and revoke access privileges.
- Streamline onboarding/offboarding for employees.
- Free up IT teams to focus on higher-value projects.
It is also stated that enterprises using automated IAM reduce manual provisioning costs by up to 40%, saving millions annually on IT overhead.
5. Stronger Control Over Privileged Accounts
Privileged accounts often carry the highest security risks. An essential Identity and Access Management Benefit is the ability to secure these accounts with privileged access management.
IAM ensures:
- Access permissions are tightly controlled for admins.
- Session monitoring detects abnormal user behavior.
- Critical assets and sensitive data are shielded from misuse.
6. Faster Onboarding and Offboarding of Employees
Delays in granting or removing user access can create both inefficiencies and vulnerabilities. Another key Identity and Access Management Benefit is streamlining employee lifecycle management.
With IAM systems, you can:
- Provision access rights instantly for new hires.
- Remove access for departing employees immediately.
- Reduce insider threats and improve operational efficiency.
7. Greater Visibility Into User Activity and Access Logs
Without visibility, you can’t detect threats. Another important Identity and Access Management Benefit is centralized monitoring.
IAM solutions give IT administrators:
- Real-time insights into user behavior across platforms.
- Detailed audit trails for compliance and investigations.
- Early warnings of insider threats or unusual login activity.
8. Seamless Integration With Cloud and On-Prem Systems
Hybrid enterprises run workloads on both Active Directory and cloud directory services. A major Identity and Access Management Benefit is smooth integration across environments.
IAM technologies deliver:
- Consistent user management across cloud and on-prem.
- Support for legacy IAM tools alongside modern SaaS apps.
- Unified identity management that strengthens overall security posture.
9. Support for Remote and Hybrid Workforce Models
With remote work now standard, securing devices and user identities outside the office is crucial. Another valuable Identity and Access Management Benefit is enabling secure remote access.
IAM platforms provide:
- Secure access for employees working from any location.
- Stronger protections with multi-factor authentication.
- Flexible capabilities that adapt to hybrid workforce scenarios.
10. Foundation for Zero Trust and Future-Ready Security
Perhaps the most strategic Identity and Access Management Benefit is laying the foundation for Zero Trust. As enterprises evolve, IAM ensures long-term security resilience.
IAM enables:
- Continuous verification of all user identities and devices.
- Enforce the principle of least privilege for every user role.
- Adapting to new threats with artificial intelligence and advanced IAM technologies.
How to Maximize Identity and Access Management Benefits in Your Enterprise?
To maximize IAM benefits, centralize identity management, use MFA and SSO, enforce least privilege, automate user lifecycles, adopt zero trust, and ensure continuous monitoring with regular access reviews.
To fully realize the Identity and Access Management Benefits, enterprises need the right strategies in place. Here’s how you can get the most value:
- Adopt a Zero Trust model
Require verification for every login and device to extend IAM’s protection beyond basic access control. - Implement Multi-Factor Authentication (MFA)
Adding MFA ensures sensitive data stays protected even if passwords are compromised. - Leverage Single Sign-On (SSO)
With single sign-on, employees use one set of credentials across platforms, improving both security and user experience. - Automate provisioning and de-provisioning
Automation gives employees the right access privileges instantly and removes them at offboarding, reducing risks and costs. - Regularly review access rights
Routine audit checks prevent privilege creep, keeping user roles aligned with actual responsibilities. Companies performing automated access reviews detect anomalies faster and save an average of $900,000 per breach. - Secure privileged accounts with PAM
Use Privileged Access Management to enforce least privilege and monitor high-risk user identities. - Integrate IAM with IT infrastructure
Connect your IAM solution to Active Directory, cloud apps, and other components for full coverage. - Use IAM analytics
Analyze user behavior and access logs to detect anomalies and enhance your overall security posture.
How CloudEagle.ai Helps Enterprises Leverage IAM Benefits
Managing IAM effectively requires automation, governance, and visibility. CloudEagle.ai delivers an all-in-one IAM solution that streamlines provisioning, enforces access controls, and strengthens identity governance. The result? Stronger Identity and Access Management Benefits, improved compliance, and optimized SaaS operations.
Employee App Access & Usage
CloudEagle.ai gives IT teams deep visibility into user identities and employee activity across SaaS apps, ensuring secure app access. It tracks logins, monitors feature-level usage, and maintains detailed audit logs to support regulatory compliance.
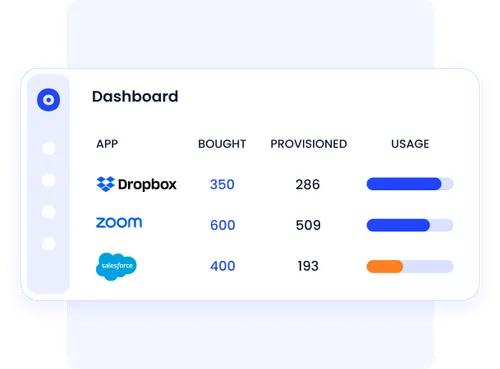
These insights also help identify underutilized resources and manage shadow IT more effectively.
Easy Provisioning & Deprovisioning
Automated Provisioning & Deprovisioning ensures new hires get the right access instantly, while departing employees lose access to sensitive data immediately.
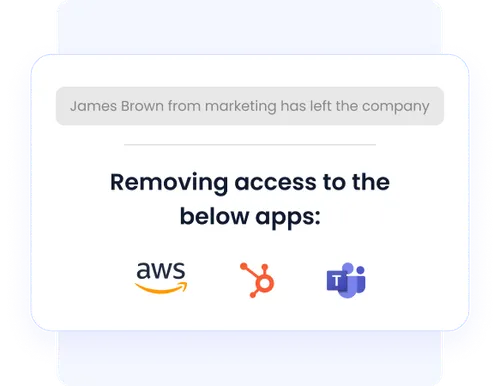
This prevents stale accounts, reduces human error, and allows IT to focus on strategic priorities instead of manual tasks.
Self-Service Platform for Access Requests
With CloudEagle.ai’s self-service portal, employees can request access to apps directly. Admins receive instant alerts through Slack integrations or email, simplifying approvals.
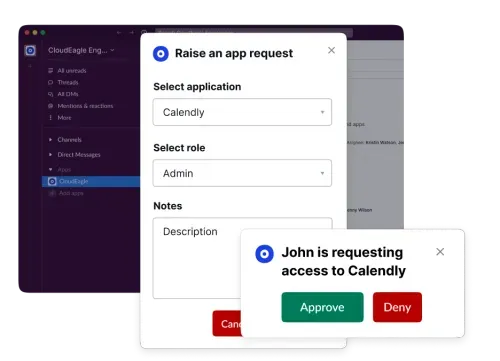
This improves secure access workflows, reduces delays, and enhances overall user experience.
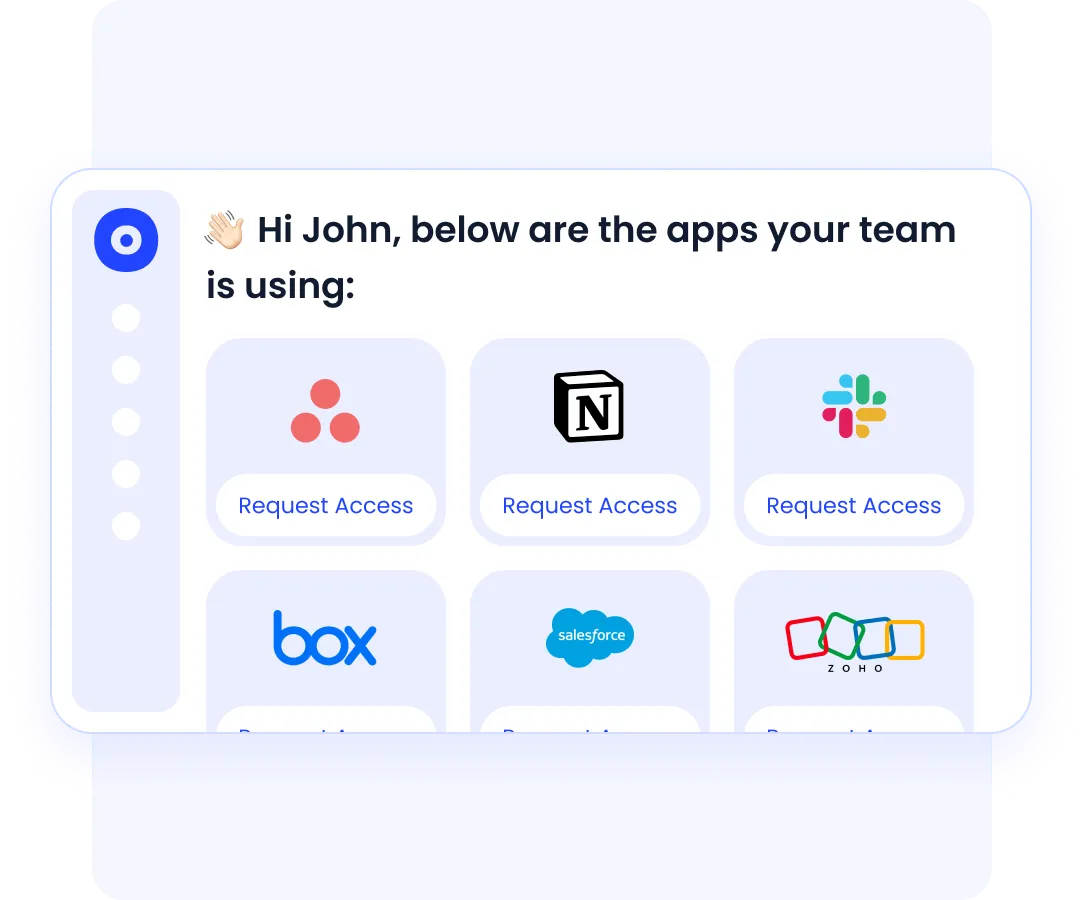
Relevant App Suggestions
CloudEagle.ai recommends the right applications for new hires based on their user roles. It automatically provisions necessary tools and revokes them during offboarding, preventing unnecessary access privileges and keeping your SaaS stack secure and optimized.
Role-Based Access Control (RBAC)
By applying role-based access control, CloudEagle.ai ensures each user only has the access permissions required for their responsibilities.
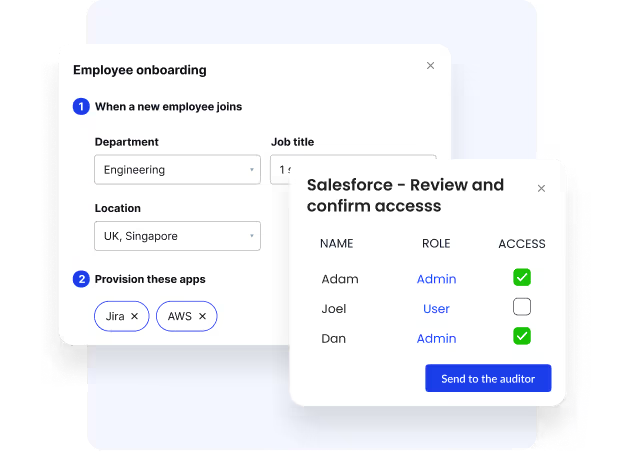
This reduces privilege creep, protects critical assets, and strengthens enterprise-wide identity governance.
Just-in-Time (JIT) Access
Instead of permanent permissions, employees can request Just-in-Time access rights for critical apps.
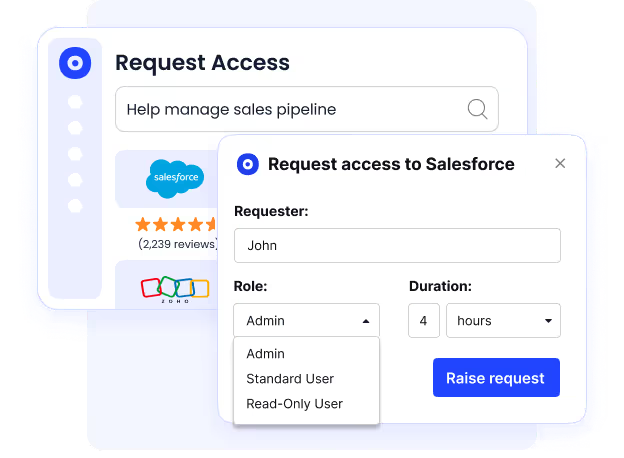
These expire automatically, aligning with the principle of least privilege and reducing the risk of unauthorized access.
Automated App Access Reviews
CloudEagle.ai automates periodic reviews of user access to confirm accuracy and compliance. Admins are prompted to certify or revoke unnecessary rights, which improves audit readiness, enhances your overall security posture, and lowers the risk of data breaches.
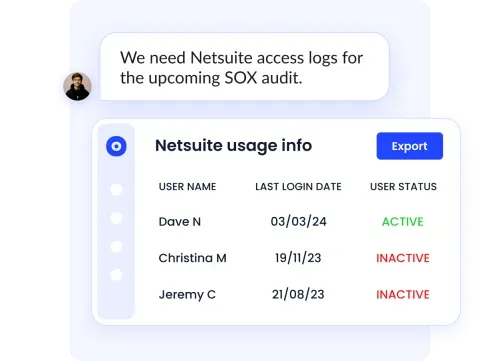
In A Nutshell
Identity and Access Management is no longer optional; it’s the backbone of enterprise security and compliance. From securing sensitive data to simplifying user provisioning, the Identity and Access Management Benefits extend across every layer of your IT ecosystem.
By adopting IAM, enterprises not only minimize risks but also improve operational efficiency. Features like role-based access, just-in-time provisioning, and automated reviews ensure that the right people always have the right access, nothing more, nothing less.
CloudEagle.ai takes IAM to the next level by automating app provisioning, simplifying access requests, and enabling real-time visibility across your SaaS stack. With these capabilities, your business can fully unlock the Identity and Access Management Benefits while saving time and reducing costs.
Book a free demo with CloudEagle.ai today, because secure access shouldn’t slow your business down.
Frequently Asked Questions
- What are the four pillars of IAM?
The four pillars of IAM are Authentication, Authorization, User Management, and Central User Repository, together ensuring secure and efficient identity and access control. - What are the 4 components of IAM?
The core components are Identification, Authentication, Authorization, and Accountability, covering the full cycle of verifying, granting, and tracking access. - What are the organizational benefits of IAM training?
IAM training improves security awareness, reduces insider risks, ensures compliance, and empowers employees to manage access responsibly and effectively. - Which IAM tool is best?
The best IAM tool depends on your needs, but CloudEagle.ai, Okta, and Microsoft Entra ID are leaders, offering strong automation, governance, and compliance features. - How many IAM tools are there?
There are dozens of IAM tools in the market, ranging from cloud-based leaders like Okta and CloudEagle.ai to enterprise solutions from Microsoft and IBM.

%201.svg)










.avif)




.avif)
.avif)




.png)









