HIPAA Compliance Checklist for 2025

Did you know that 70% of IAM implementations fall short of expectations or fail outright? This highlights the critical need for organizations to assess and advance their Identity and Access Management (IAM) maturity.
The IAM Maturity Model provides a structured framework to evaluate and improve IAM capabilities. By understanding and progressing through its stages, businesses can strengthen security, ensure compliance, and optimize operational efficiency.
Also, according to Forrester, organizations with mature IAM experience 46% fewer server or app breaches, 51% fewer database breaches, and 63% fewer cloud breaches.
In this guide, we'll explore the five key stages of the IAM Maturity Model, discuss essential components like Privileged Access Management (PAM), share best practices, and explain how CloudEagle.ai helps enterprises automate and enhance their IAM processes.
What is Identity and Access Management Maturity Model?
An Identity and Access Management (IAM) Maturity Model is a framework that evaluates how effective an organization’s IAM program is. It guides progression from an ad-hoc, immature state to an optimized, automated, and strategically aligned system.
Defining distinct maturity levels helps organizations assess their current capabilities in managing user identities and access, identify gaps, and develop a roadmap to enhance processes, technology, and governance for stronger security, improved efficiency, and regulatory compliance.
Key aspects include:
- Assessing identity management lifecycle phases to understand how new employees are onboarded and offboarded efficiently.
- Evaluating integration capabilities with cloud, hybrid, and SaaS environments to streamline single sign-on (SSO) and multi-factor authentication (MFA).
- Leveraging automation and real-time insights to maintain access governance, reduce security risks, and optimize user experience.
According to Gartner, 60% of organizations experience at least one identity-related security breach per year due to poorly managed access.
“Identity and access management is the backbone of enterprise security. Organizations that invest in a mature IAM program not only reduce risk but also enable scalable, efficient operations across all digital resources.”
— John Kindervag, Cybersecurity Strategist and Creator of Zero Trust
By establishing a clear view of IAM practices and maturity levels, organizations can create a structured roadmap to advance from ad-hoc processes to automated, adaptive IAM solutions, ensuring both cybersecurity and operational efficiency.
What are the Essential Levels of the IAM Maturity Model?
The key levels of an Identity and Access Management Maturity Model start with Initial/Ad Hoc, where processes are chaotic, move to Defined/Managed, with standardized and documented procedures, and end at optimized, featuring automated, integrated IAM aligned with business goals. Some models add a Transformational level for maximum value.
Level 1 – Initial (Ad-hoc Identity Practices)
At this stage, organizations operate with ad-hoc and informal IAM practices. Processes are largely reactive, and manual processes dominate:
- User identities are managed inconsistently, often on spreadsheets or standalone systems.
- Limited Privileged Access Management (PAM); role-based controls are either missing or poorly defined.
- Minimal visibility into devices, logins, and access rights leaves gaps that expose the organization to security threats.
- Onboarding and offboarding rely on manual steps, increasing the risk of unauthorized access and human errors.
Research by Forrester shows that organizations at the Managed or Optimized IAM maturity level reduce identity-related incidents by over 70% compared to organizations at the Ad-Hoc level.
Challenges/Risks: High likelihood of compliance gaps, inefficient business processes, and security vulnerabilities.
Level 2 – Repeatable (Basic IAM Processes in Place)
Organizations begin creating repeatable IAM processes, though they remain basic:
- Initial identity governance ensures that users have appropriate access to critical systems.
- Self-service portals allow employees to reset passwords and manage some access independently, improving user experience.
- Multi-factor authentication (MFA) is introduced for higher-risk accounts, boosting cybersecurity.
- Partial integration with SaaS applications, core IT systems, and directories begins, creating the first steps toward a structured IAM lifecycle.
Challenges/Risks: Manual approvals and partial integration can cause delays, errors, and gaps in access management maturity.
Level 3 – Defined (Formal IAM Framework and Policies)
Organizations implement formal IAM frameworks with documented policies and procedures:
- Identity management lifecycle phases are standardized for user onboarding, role changes, and deprovisioning.
- Privileged Access Management (PAM) practices are applied consistently, reducing security risks from excessive permissions.
- Compliance requirements are incorporated into IAM processes, with regular reporting and auditing.
- Single sign-on (SSO) and enhanced self-service improve user experience and reduce the burden on IT teams.
Challenges/Risks: Ensuring consistent application of policies and monitoring sensitive data across hybrid systems.
Level 4 – Managed (Proactive Monitoring and Governance)
Managed organizations leverage real-time monitoring and governance to reduce security threats:
- Continuous auditing of access rights, user identities, and devices helps detect anomalies in real-time.
- Automated alerts notify IT staff of potential unauthorized access or policy violations.
- Strong integration with cloud, hybrid, and SaaS systems ensures consistent identity governance across all resources.
- Insights from monitoring optimize business processes, risk management, and access management maturity.
Example/Practice: CloudEagle.ai automates access reviews, tracks user access continuously, and alerts IT staff to suspicious activity, reducing manual processes while ensuring regulatory compliance.
Level 5 – Optimized (Automated, Adaptive IAM Practices)
The highest level represents full automation, AI-driven decision-making, and adaptive IAM policies:
- End-to-end automation of user provisioning, deprovisioning, and role changes reduces manual errors and accelerates user onboarding.
- API-driven identity lifecycle management (ILM) allows seamless integration across enterprise systems.
- Predictive security threat detection leverages artificial intelligence (AI) and insight from activity analytics.
- Continuous optimization improves compliance, user experience, resource allocation, and overall IAM practices, helping organizations maintain a successful IAM program.
Example/Practice: Enterprises use CloudEagle.ai to fully automate identity governance, privileged access management (PAM), and access management, ensuring stronger cybersecurity, consistent user experience, and efficient resource allocation.
Identity and Access Management Maturity Model Key Components
A robust Identity and Access Management Maturity Model outlines key components and progressive levels to assess and enhance an organization’s IAM program. Core elements include Authentication, Authorization, Administration, and Auditing.
Advanced models also incorporate Identity Governance & Administration (IGA), Privileged Access Management (PAM), and Identity Lifecycle Management, promoting a more mature, automated, and business-aligned security framework.
According to Cybersecurity Insiders, 85% of enterprises report that implementing Privileged Access Management (PAM) and Identity Governance & Administration (IGA) is critical for reducing risks of unauthorized access.
Access Governance and Policy Enforcement
Effective access governance is the foundation of a mature IAM program. It ensures that users have the right level of access and that policies are consistently enforced across all systems:
- Establishes clear access controls and policies for all users.
- Tracks and audits user identities to ensure only authorized personnel can access sensitive data.
- Helps enforce regulatory compliance by monitoring adherence to internal and external policies.
- Best practices: Implement periodic access reviews, use role-based access control, and enforce strong authentication measures.
Authentication and Authorization Controls
Strong authentication and authorization controls protect organizational resources from unauthorized access while improving usability for employees:
- Ensures secure login processes for employees, contractors, and third-party vendors.
- Supports multi-factor authentication (MFA) and single sign-on (SSO) for simplified and secure access.
- Reduces risks of unauthorized access to corporate resources and sensitive data.
- Best practices: Apply strong password policies, integrate federation for external identities, and enforce real-time authentication checks.
Privileged Access Management (PAM)
Managing privileged users is critical, as they have elevated rights that could expose the organization to major security risks:
- Monitors and controls access to critical systems for privileged users.
- Mitigates the risk of excessive permissions or misuse by administrators.
- Tracks user access and maintains an entitlement repository for audits.
- Best practices: Implement session monitoring, approval workflows for privilege escalation, and automated deprovisioning when roles change.
User Lifecycle and Provisioning Automation
Automating the identity management lifecycle ensures timely onboarding, modification, and offboarding of users while reducing human errors:
- Automates user provisioning and deprovisioning based on roles and policies.
- Ensures new hires get appropriate access quickly and former employees are properly deactivated.
- Enhances user experience and reduces the risk of errors from manual processes.
- Best practices: Integrate CloudEagle.ai or similar platforms for automated workflows and consistent identity governance.
Continuous Monitoring and Reporting
Continuous monitoring provides real-time insight into access patterns, helping IT teams detect anomalies early:
- Tracks user activities, login attempts, and privileged access across systems.
- Generates audit-ready reports for regulatory compliance and internal governance.
- Helps organizations identify security risks and inefficiencies in IAM practices.
- Best practices: Implement dashboards, automated alerts, and periodic compliance reporting.
Integration With Cloud and Hybrid Environments
A modern IAM solution must work seamlessly across on-premises, cloud, and hybrid infrastructures:
- Ensures consistent identity governance across SaaS applications, cloud platforms, and legacy systems.
- Supports federation, SSO, and API-driven ILM for streamlined access management.
- Improves resource allocation, user experience, and reduces manual administration.
- Best practices: Adopt integrated IAM platforms that unify identity lifecycle management across all environments.
How CloudEagle.ai Helps Maintain Identity and Access Management
Managing identity and access management (IAM) effectively requires automation, governance, and visibility. CloudEagle.ai provides an all-in-one solution that streamlines user provisioning, access management, and identity governance, ensuring organizations maintain compliance, improve security, and optimize SaaS operations.
Employee App Access & Usage
CloudEagle.ai offers detailed insights into user identities and app access, giving enterprises complete visibility into employee activity across all SaaS applications.
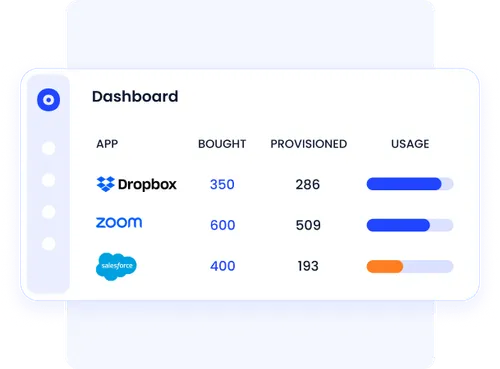
- Monitors app logins and feature-level usage for each employee.
- Maintains an extensive audit log to ensure regulatory compliance and strong identity governance.
- Helps organizations identify underutilized resources and manage shadow IT effectively.
Easy Provisioning & Deprovisioning
With CloudEagle.ai’s automated user lifecycle management, IT teams can eliminate repetitive manual tasks and reduce the risk of human error, ensuring users always have the right access at every stage of their journey.
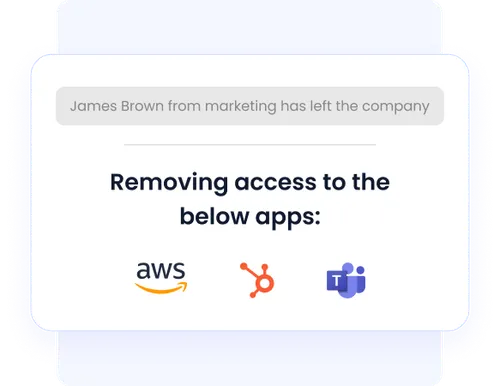
- Streamlines user provisioning and deprovisioning, granting or revoking access with a few clicks.
- Prevents unauthorized access to sensitive data by promptly removing departed employees’ access.
- Enhances IT productivity, allowing teams to focus on strategic tasks instead of manual processes.
Self-Service Platform for App Access Requests
CloudEagle.ai empowers both employees and admins with a self-service portal for access requests, streamlining approvals and reducing IT bottlenecks.
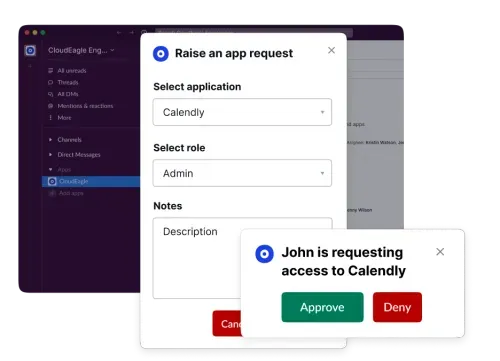
- Users can request access to applications, while admins receive instant alerts via email or Slack.
- Simplifies access management and improves the overall user experience.
- Reduces delays and errors associated with manual approval workflows.
Relevant App Suggestions
CloudEagle.ai automatically recommends the right applications to new employees based on their roles, ensuring faster onboarding and immediate productivity.
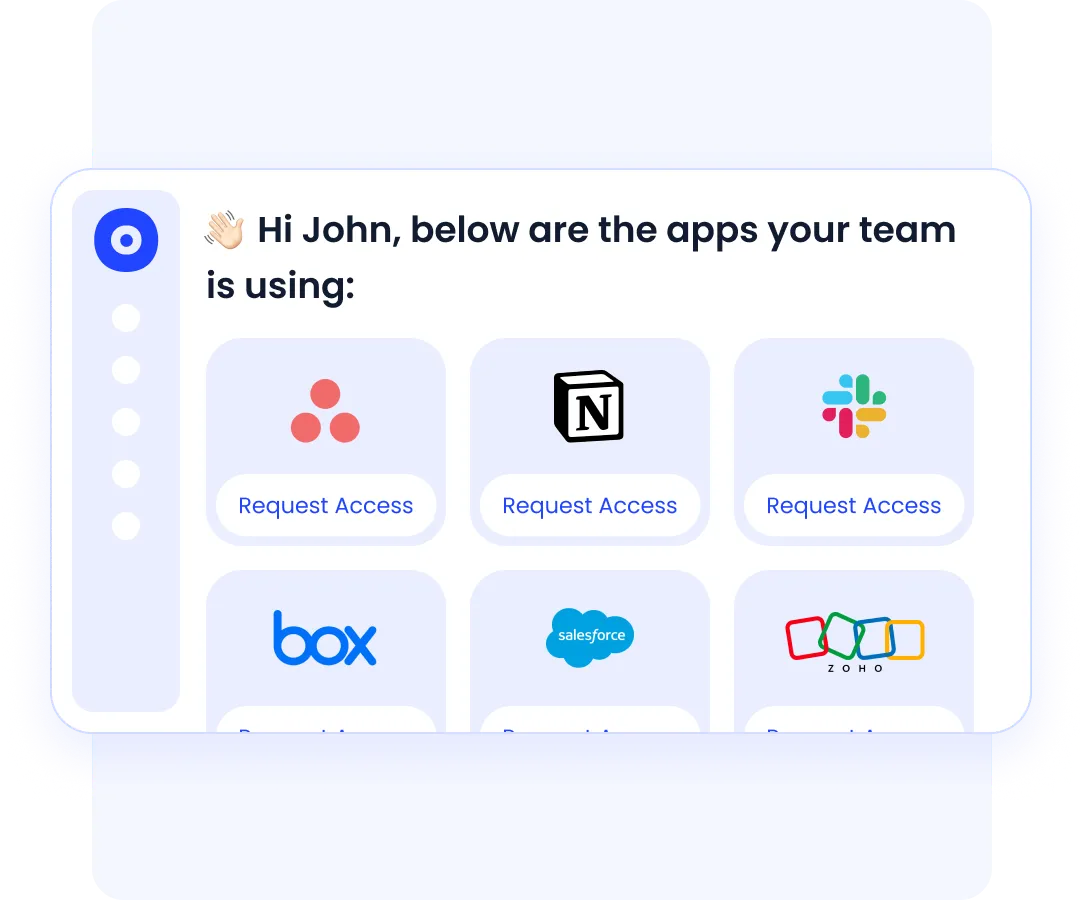
- Ensures new hires get appropriate access efficiently.
- Automatically revokes access during employee separation, maintaining a secure software stack.
- Optimizes resource allocation and reduces administrative overhead.
Role-Based Access Control (RBAC)
Role-based access Control (RBAC) ensures employees only have the permissions they need to perform their jobs, reducing the risks of excessive or unnecessary access.
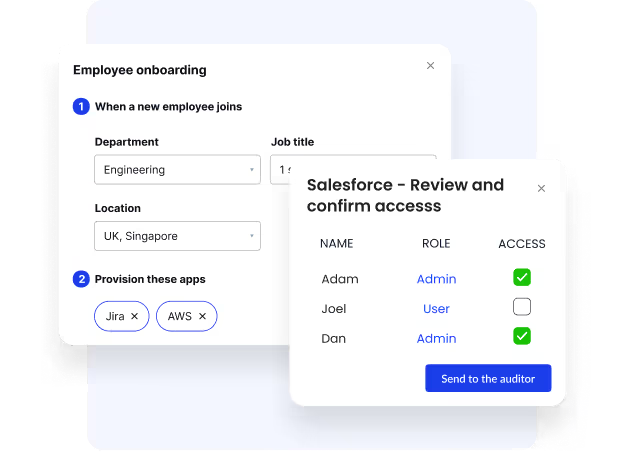
- Assigns access based on roles and responsibilities.
- Minimizes risks from excessive permissions or privilege creep.
- Helps maintain compliance and strengthens identity governance across all systems.
Just-in-Time (JIT) Access
CloudEagle.ai supports Just-in-Time access to critical applications, allowing employees to request temporary permissions only when needed, minimizing security risks from standing privileges.
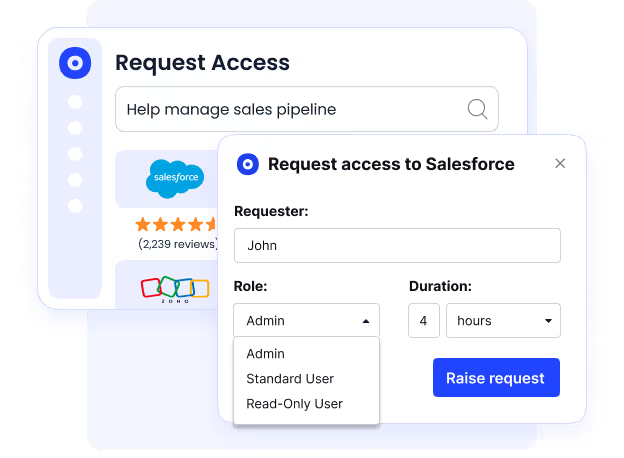
- Employees request access for a defined period, automatically expiring afterward.
- Reduces potential security vulnerabilities from standing access.
- Ensures compliance with internal policies and external regulatory requirements.
Automated App Access Reviews
CloudEagle.ai automates regular app access reviews to maintain security and compliance, ensuring users only have the permissions they truly need.
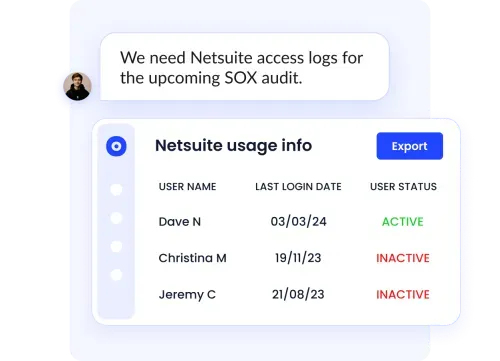
- Prompts admins to certify user access and revoke unnecessary permissions.
- Helps organizations detect inactive accounts and prevent unauthorized access.
- Improves audit readiness while reducing manual processes and human error.
In A Nutshell
Implementing an Identity and Access Management (IAM) Maturity Model is vital to strengthening security, streamlining workflows, and ensuring regulatory compliance. By evaluating your IAM maturity level, you can pinpoint gaps and prioritize improvements. A structured approach builds a scalable and robust identity governance framework.
Automating identity management lifecycle phases minimizes manual errors and security risks while improving the user experience for employees and IT teams. Features like role-based access control (RBAC) and just-in-time access help protect sensitive data. Efficient processes also optimize resource allocation across the organization.
CloudEagle.ai empowers enterprises to reach higher IAM maturity with centralized user lifecycle management, access governance, and real-time monitoring. Its automated provisioning, AI-driven insights, and compliance reporting ensure secure, consistent access.
Book a free demo today to see how CloudEagle.ai can elevate your IAM practices.
Frequently Asked Questions
- What are the 5 levels of maturity modeling?
The 5 levels include: Initial (ad-hoc), Repeatable, Defined, Managed, and Optimized, showing an organization’s progression from basic processes to automated, proactive, and adaptive identity and access management practices. - What is the AML maturity model?
The AML maturity model assesses how well an organization’s anti-money laundering controls, processes, and monitoring are implemented, ranging from ad-hoc practices to fully automated, compliant, and optimized AML systems. - What is the IAM maturity scale?
The IAM maturity scale measures an organization’s identity and access management capabilities, from basic, manual controls to advanced automated processes, robust governance, and continuous monitoring of user identities and access rights. - What are the 4 A's of IAM?
The 4 A's stand for Authentication, Authorization, Accounting, and Auditing, which collectively manage user identities, control access, track actions, and ensure compliance across systems. - What are the key phases of the identity management lifecycle?
Key phases include onboarding, provisioning, modification, role changes, access reviews, and offboarding, ensuring users have the right access throughout their lifecycle while minimizing security risks and manual errors.

%201.svg)










.avif)




.avif)
.avif)




.png)









