HIPAA Compliance Checklist for 2025

Imagine logging into five different apps every morning, each demanding a unique password. For many employees, this is daily reality, creating frustration and slowing productivity.
Active Directory Federation Services (ADFS) solves this by enabling single sign-on (SSO) across both cloud and on-premises systems. Instead of juggling logins, users authenticate once and gain secure access everywhere.
The impact is significant. Forrester reports the average cost of a single password reset is $70. By reducing resets, enterprises save IT resources and deliver a smoother user experience. This article explores what ADFS is, why it matters, and its implementation process.
TL;DR
- ADFS lets users log in once and securely access multiple apps without repeated passwords.
- ADFS enables trusted authentication across organizational boundaries, supporting partners, cloud, and on-prem systems.
- Instead of sending passwords, ADFS issues encrypted tokens with identity claims for safer access.
- IT admins control authentication policies, enforce MFA, and streamline user access from one directory.
- ADFS reduces password fatigue, lowers helpdesk costs, supports hybrid environments, and boosts security compliance.
What is ADFS?
Active Directory Federation Services (ADFS) is Microsoft’s solution for single sign-on (SSO) and secure identity federation. ADFS active directory lets users access applications and services across different enterprises using their existing Active Directory credentials.
ADFC means acting as a secure bridge using claims-based identity to share user information safely. With ADFS authentication, users authenticate once on their internal network and access web apps without re-entering passwords. Key aspects of ADFS include:
- Single Sign-On (SSO): Users log in once and gain access to multiple applications without re-entering credentials.
- Federated Identity Management: ADFS SAML enables latest authentication methods across organizational boundaries, supporting partner or third-party applications.
- Token-Based Authentication: It issues security tokens containing user identity information instead of transmitting passwords.
- Interoperability: Active Directory FS works with various standards like ADFS SAML and OAuth, allowing integration with diverse platforms.
- Centralized Identity Control: Administrators manage policies, authentication, and access rights through a single, centralized directory.
How Does ADFS Work?
ADFS creates a trusted link between organizations for single sign-on (SSO) access to multiple applications. When users request access, ADFS authenticates them using their organization’s Active Directory credentials.
Active Directory Federation Services then generates a security token containing claims about the user's identity. This token is sent to the partner application, which trusts the information and grants access instantly. Core steps in the ADFS process include:
- User Authentication: A user signs in with their Active Directory credentials on a corporate device or portal.
- Token Issuance: ADFS server validates the credentials and generates a security token containing identity claims.
- Federation Trust: Partner or third-party applications trust ADFS active directory as the identity provider, accepting its tokens.
- Access Granted: The application reads the token, verifies claims, and grants access without requesting another login.
- Policy Enforcement: Administrators define rules for access, such as requiring multi-factor authentication for sensitive apps.
As Microsoft’s former identity program manager Kim Cameron once said,
“The internet needs identity systems that are simple, secure, and built for federation.”
ADFS authentication follows this principle by delivering seamless, standards-based authentication across applications and environments.
Why Enterprises Use Active Directory Federation Services?
Enterprises adopt ADFS for secure Single Sign-On (SSO) and simplified user access across many applications. ADFS centralizes identity management, strengthening security while reducing the causes of data breaches.
1. Enabling Single Sign-On Across Multiple Platforms
ADFS enables enterprises to implement single sign-on (SSO) across multiple platforms, including on-premises applications, cloud services, and partner portals. By allowing users to authenticate just once, it eliminates the hassle of remembering multiple passwords and reduces login friction.
Centralized authentication also enhances security. IT teams can enforce consistent policies across all systems, monitor and manage privileged access, and detect suspicious behavior more efficiently. This reduces the risk of unauthorized access while ensuring compliance with internal and external security standards.
2. Simplifying IT Administration
ADFS simplifies IT administration by centralizing identity and access management. Instead of managing multiple credentials for every application, IT teams can control access from a single point, reducing errors and improving operational efficiency.
Key ways Active Directory Federation Services eases IT workloads include:
Centralized User Management
Administrators can add, remove, or modify user access in one place, instantly updating permissions across all connected applications.
Reduced Helpdesk Requests
With fewer login issues and password resets from ADFS authentication, IT support teams spend less time on routine troubleshooting.
Policy Consistency
Security policies such as multi-factor authentication and conditional access can be uniformly enforced across platforms.
Seamless Integration
ADFS works with both legacy on-premises applications and modern cloud services, minimizing configuration complexity.
For instance, Microsoft itself uses Active Directory FS internally to manage employee access across its global workforce. Centralizing authentication helped reduce password-related support tickets significantly, while ensuring consistent access controls across thousands of applications and offices worldwide.
3. Supporting Hybrid and Cloud Environments
ADFS plays a critical role in hybrid IT environments, where enterprises use a combination of on-premises systems and cloud services. Key benefits of ADFS authentication for hybrid and cloud environments include:
- Unified Authentication Across Platforms: Users can log in once to access both cloud applications and on-premises systems without repeated credentials.
- Secure Access for Remote Work: Conditional access and multi-factor authentication ensure that employees working from anywhere remain secure.
- Smooth Cloud Migration: Enterprises moving services to platforms like Microsoft 365 or Azure can integrate ADFS without disrupting user access.
- Reduced Administrative Complexity: IT teams focus on cloud identity management, simplifying maintenance and policy enforcement.
4. Reducing Password Fatigue for Users
Password fatigue is a common issue in enterprises where employees must remember multiple complex credentials. This often leads to weak password practices, such as reuse across platforms or storing passwords insecurely, which increases SaaS security risks.
ADFS with Single Sign-On (SSO) addresses this by allowing users to log in once and access multiple applications seamlessly, reducing the number of passwords employees need to manage.
A Deloitte report revealed that the average cybersecurity spend, including password reset costs, was $2,700 per employee in 2020. Implementing SSO through ADFS active directory can mitigate this, improving security and user convenience simultaneously.
How ADFS Benefits the End Users?
ADFS provides end users with a simpler, more secure experience through single sign-on (SSO). Active Directory FS eliminates the need to remember multiple passwords for internal, cloud, or partner applications.
By streamlining access, ADFS reduces login interruptions and saves users valuable time daily. This improves employee productivity and decreases frustration caused by repeated password entries.
1. Seamless Access to Applications
Seamless access to applications is a key benefit of ADFS for end users. With Single Sign-On (SSO), employees log in once and immediately access multiple cloud and on-premise apps without repeatedly entering credentials. This reduces delays and frustration, letting users focus on their work.
For instance, Microsoft leveraged ADFS server for its internal Office 365 and Azure applications, enabling employees to authenticate once while accessing multiple services securely. The implementation decreased login-related IT tickets by over 40%, demonstrating tangible productivity improvements and a smoother user experience.
2. Reduced Login Friction
ADFS significantly reduces login friction by simplifying the authentication process for end users. Instead of remembering multiple passwords for different applications, employees can access all authorized systems with a single set of credentials.
Key ways ADFS SAML reduces login friction include:
- Single Sign-On (SSO) Integration: Users authenticate once and access multiple apps, eliminating repeated logins.
- Password Policy Enforcement: Centralized control ensures strong, consistent access management practices across all platforms.
- Reduced Help Desk Load: Fewer password-related issues mean IT teams spend less time resolving login problems.
- Faster Onboarding: New employees gain immediate access to necessary tools without multiple account setups.
- Cross-Platform Accessibility: Users experience smooth authentication across desktops, mobile devices, and cloud applications.
3. Consistent Experience Across Devices
ADFS ensures that users enjoy a consistent authentication experience across desktops, laptops, tablets, and smartphones. By centralizing access management, employees can switch between devices without re-authenticating multiple times. Thus, Active Directory FS streamlines workflows and reduces frustration.
Key aspects of a consistent multi-device experience include:
- Unified Login Interface: The same sign-on process applies across all devices, reducing confusion and training requirements.
- Device-Aware Security: ADFS authentication adapts authentication based on device type, location, and security posture.
- Improved Productivity: Employees spend less time managing logins, allowing more focus on core responsibilities.
- Reduced Errors: Centralized authentication minimizes failed login attempts across devices.
A 2024 report by Ping Identity found that businesses implementing Single Sign-On (SSO) solutions, such as ADFS, experienced a 50% reduction in password-related help desk costs, highlighting the efficiency gains and user satisfaction improvements achieved through consistent authentication experiences across devices.
What is the ADFS Authentication Process?
The ADFS authentication process enables secure, seamless access by letting users log in once for many applications. Active Directory Federation Services verifies user credentials against the organization’s Active Directory using role-based access control flow.
It issues a secure token containing user identity and permissions as claims. This token is sent to target applications or partners, which trust the claims and grant access.
This process supports Single Sign-On (SSO), allowing users to avoid repeated logins across systems. Understanding ADFS SAML helps IT teams optimize security while enhancing user experience.
Key steps in the ADFS authentication process include:
- User Requests Access: The user tries to access an application, prompting a login request.
- Credentials Verification: ADFS validates the user access management against Active Directory.
- Claims Generation: ADFS generates security tokens containing claims about the user’s identity and access rights.
- Token Issuance: The application receives the token to grant secure access.
- Continuous Security Checks: Policies like multifactor authentication or device checks are applied to ensure secure sessions.
As Bruce Schneier, security expert said,
“Security is not a product, but a process.”
This says a lot about ADFS authentication is about continuous authentication and SaaS risk management, not just a single login step.
What are the Different ADFS Versions?
ADFS server has evolved with new versions adding features, enhanced security, and better integration options. Each version corresponds to specific Windows Server operating systems and their improvements.
- ADFS 1.0: The initial release focused on basic federated identity for Windows Server 2003. It supported simple single sign-on but had limited claims-based authentication features.
- ADFS 2.0: Introduced with Windows Server 2008 R2, it added claims-based authentication, support for multiple identity providers, and SSO across applications.
- ADFS 3.0: Released with Windows Server 2012 R2, it eliminated the need for IIS, streamlined management, and enhanced security with integrated certificate management.
- ADFS 4.0: Comes with Windows Server 2016/2019, providing modern authentication protocols, better cloud integration, and support for Azure Active Directory scenarios.
- ADFS 5.0 (Windows Server 2022): Latest version with advanced MFA options, improved performance, and extended support for hybrid and cloud-native applications.
What are the Risks of ADFS?
ADFS simplifies identity management but carries risks if not properly configured or maintained. Compromised ADFS active directory servers can allow attackers to forge tokens and impersonate users.
Using outdated versions or weak authentication policies increases vulnerability to common causes of data breaches. Understanding these risks helps IT teams implement safeguards to protect user trust and system security.
1. Vulnerabilities in Legacy Versions
Older versions of ADFS, such as 1.0 and 2.0, often lack modern security features like advanced multi-factor authentication, conditional access policies, and streamlined patching mechanisms. Enterprises running legacy deployments risk exposure to known vulnerabilities that have already been exploited in other organizations.
Additionally, legacy versions may not fully support modern authentication protocols like OAuth 2.0 or OpenID Connect, limiting their ability to integrate securely with cloud applications. Regularly updating to supported Active Directory Federation Services versions ensures that security patches are applied, reducing the potential attack surface.
2. Risk of Token Theft and Replay Attacks
ADFS relies on security tokens for authenticating users across applications. If these tokens are intercepted or stolen, attackers can potentially gain unauthorized access to multiple systems, leading to serious security breaches.
For instance, in 2021, a security incident at a school involved attackers exploiting weak token handling in an ADFS deployment, allowing them to access internal financial applications without detection.
This case highlights the importance of encrypting tokens, implementing short-lived lifetimes, and monitoring for unusual authentication patterns to prevent replay attacks.
3. High Maintenance and Operational Costs
While ADFS server provides robust identity federation capabilities, managing the infrastructure can be resource-intensive. Enterprises must regularly patch servers, monitor certificate expirations, handle configuration changes, and ensure uptime across multiple environments.
Enterprises with complex hybrid or multi-cloud setups often face increased administrative overhead, requiring dedicated IT staff to maintain operational efficiency. Failure to properly maintain the system can lead to downtime, degraded user experience, and elevated security risks.
How CloudEagle.ai Can Improve Identity and Access Management?
CloudEagle.ai is a SaaS management and procurement platform designed to help you discover, govern, renew, and optimize SaaS licenses. With robust identity and access management features, it offers a centralized dashboard to manage user permissions, roles, and access effortlessly.
With over 500 integrations, including finance, SSO, and HRIS systems, CloudEagle.ai simplifies managing your tech stack by enabling granular access control and providing deep insights into user activity, all from one platform.
Just-in-Time Access
CloudEagle.ai grants time-based access to essential systems and automatically revokes permissions once the task is finished. This reduces the risk of unauthorized access by ensuring access is only available for the necessary duration.
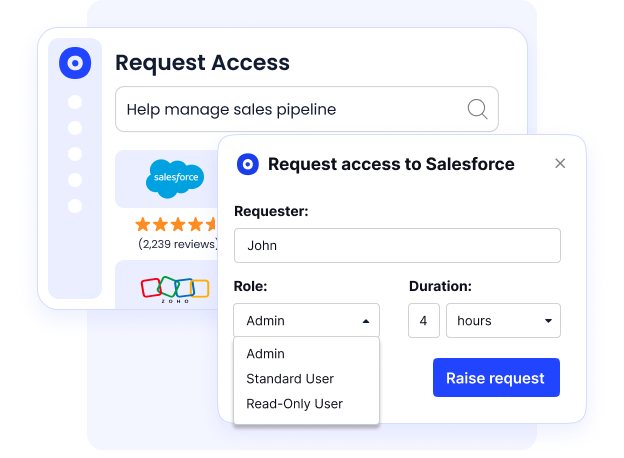
This functionality is ideal for managing contractors, freelancers, and temporary workers, offering customized permissions while upholding strong security, without requiring manual oversight.
Automated App Access Reviews
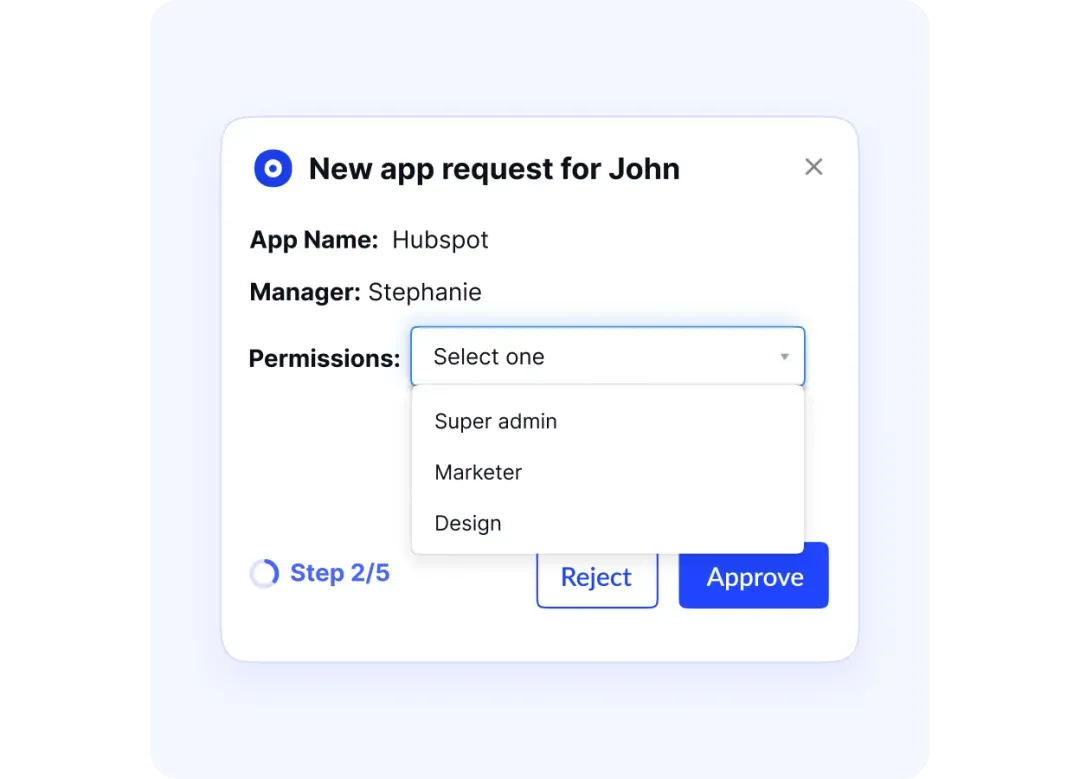
CloudEagle.ai streamlines SOC 2 and ISO 27001 access reviews by automating the process, removing the need for manual app checks or last-minute proof of deprovisioning. With all essential tools integrated into one intuitive dashboard, it simplifies compliance, ensuring efficiency and peace of mind.
Access Control
CloudEagle.ai provides full transparency into application access control, including who has access, the reasons behind it, and how they utilize it. With centralized access control, it oversees the entire access lifecycle, from request to provisioning and deprovisioning, all within a single platform.
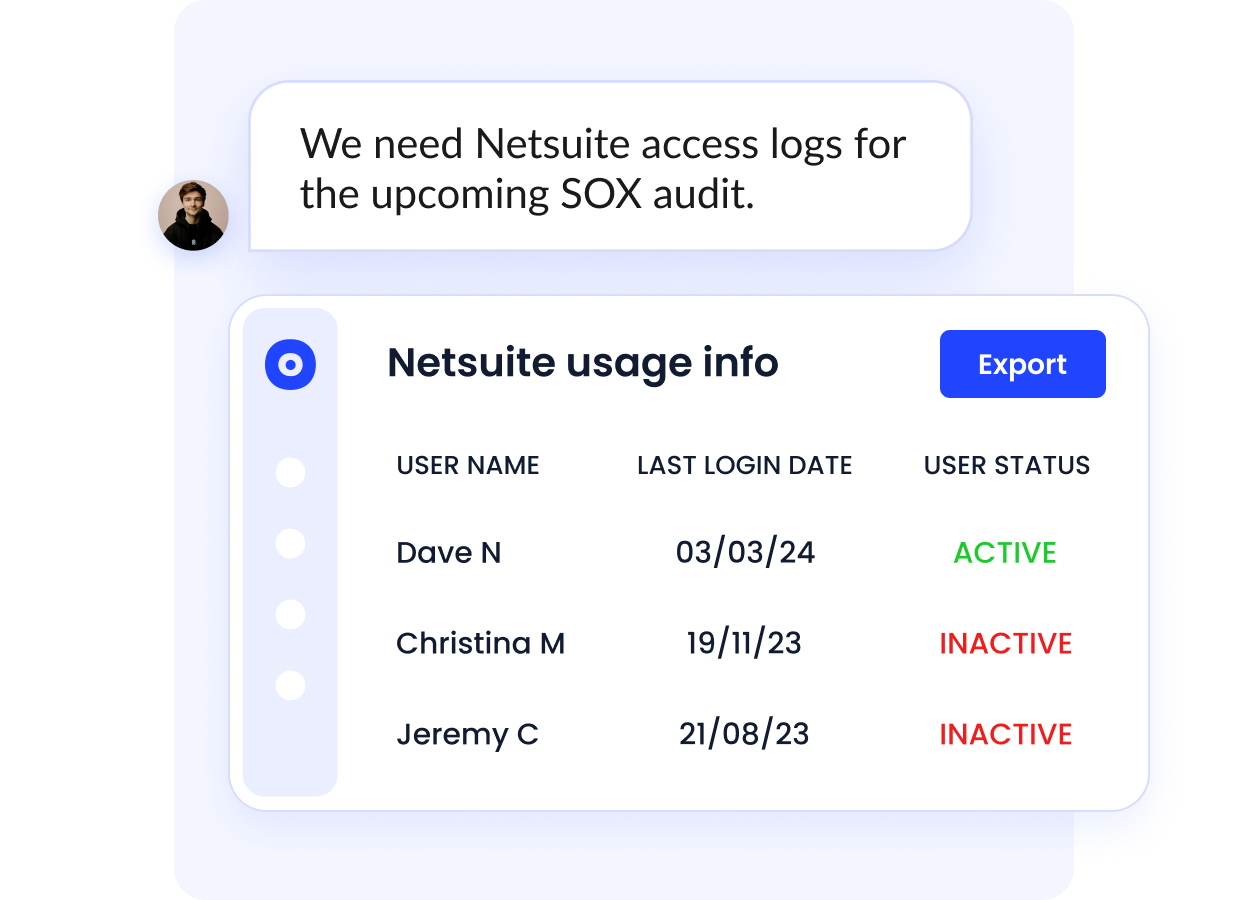
Additionally, the platform simplifies compliance and security audits by offering instant access to application logs. Detailed access records can be exported directly, making audit preparation seamless and hassle-free.
Privileged Access Management
CloudEagle.ai streamlines privileged access management by automating the assignment of elevated access, ensuring that only authorized users can access critical systems like AWS and NetSuite, thereby reducing the risk of unauthorized activity.
With continuous monitoring and automated controls, the platform strengthens security and compliance while easing administrative workloads and minimizing human error.
Employee Onboarding and Offboarding
CloudEagle.ai streamlines access management with auto-provisioning workflows, automatically granting application access to new users based on their roles and departments. This ensures employees have the necessary tools from day one, enhancing productivity.

To bolster security, the platform automates user offboarding by revoking access for inactive accounts after a set period, reducing risks associated with manual processes.
For instance, Remediant leveraged CloudEagle.ai to automate provisioning and deprovisioning, significantly boosting operational efficiency.
Compliance Management
CloudEagle.ai centralizes SaaS compliance verification across all your SaaS applications, offering full visibility and access to critical data. It continuously scans for vulnerabilities, facilitates external audits, manages certifications, and monitors account logs to ensure comprehensive compliance oversight.
Now that you know how CloudEagle.ai can protect your company’s data, let’s see the top 10 data recovery software for enterprises.
Conclusion
ADFS simplifies access management, reduces login friction, and provides a consistent user experience across platforms. However, security risks like legacy vulnerabilities, token theft, and high maintenance costs mean proactive management is essential.
With CloudEagle.ai, you can centralize identity and access management, monitor authentication events, and ensure compliance across all ADFS deployments. The platform helps you automate monitoring, detect anomalies, and maintain robust security controls, keeping your enterprise systems safe and efficient.
FAQs
1. What is ADFS used for?
ADFS enables secure single sign-on (SSO) across on-premises and cloud applications. It allows users to access multiple services with one set of credentials, improving productivity and reducing login friction while ensuring identity security.
2. Does ADFS use SQL?
Yes, ADFS relies on a SQL Server database to store configuration and token information. This database maintains trust relationships, claim rules, and other critical identity data necessary for authentication.
3. What is the difference between AD and ADFS?
Active Directory (AD) stores and manages user credentials on-premises. ADFS extends AD by providing secure SSO across different applications and domains, including cloud services.
4. Are LDAP and Active Directory the same?
No. LDAP is a protocol used to query and modify directory services. Active Directory is a directory service that supports LDAP for authentication and data access.
5. Is ADFS SAML or OAuth?
ADFS primarily supports SAML for authentication, but it also integrates with OAuth and OpenID Connect for modern applications. This enables flexible, standards-based identity management.

%201.svg)









.avif)




.avif)
.avif)




.png)









