HIPAA Compliance Checklist for 2025

As companies expand their cloud footprint, controlling who accesses critical data and applications has become a top priority. Without effective cloud identity management, organizations risk unauthorized access, operational disruption, and regulatory penalties.
A robust cloud-based identity management framework ensures employees, contractors, and partners can access exactly what they need, no more, no less. By leveraging identity and access management in cloud computing, leaders can simplify access controls while maintaining security across multiple platforms.
In this blog, you will read how features like Single Sign-On and Multi-Factor Authentication streamline workflows, while advanced cloud identity management solutions help enterprises stay compliant and reduce the risk of breaches.
TL;DR
- Cloud identity management secures digital identities and controls user access across SaaS, IaaS, and hybrid environments.
- Central features include Single Sign-On (SSO), Multi-Factor Authentication (MFA), and role-based access for streamlined, safe workflows.
- Automated provisioning and deprovisioning help prevent orphaned accounts and minimize security gaps.
- Enterprises benefit from centralized control, reduced risk, and improved compliance with evolving regulations.
- Solutions like CloudEagle.ai simplify access management, automate critical workflows, and deliver real-time monitoring for stronger cloud security.
What is Cloud Identity Management?
Cloud identity management is a system that securely controls access to cloud-based applications and data by managing user identities, authentication, and authorization across devices and platforms.
It provides centralized administration for users, apps, and devices, offering benefits such as single sign-on (SSO) for a seamless user experience, multifactor authentication (MFA) for enhanced security, and simplified compliance management.
Unlike traditional on-premises systems, cloud identity management tools can automatically manage permissions across multiple environments, giving organizations the flexibility and scalability required for modern, distributed IT infrastructures.
- Single Sign-On (SSO): Streamlines access across multiple cloud applications with a single set of credentials.
- Multi-Factor Authentication (MFA): Adds an extra layer of security to prevent unauthorized access.
- Role-Based Access Control (RBAC): Ensures users can access only the resources they need.
- Attribute-Based Access Control (ABAC): Provides granular access based on user attributes like department or location.
- Automated Provisioning & Deprovisioning: Quickly adds or removes user access to maintain security.
- Audit Trails & Monitoring: Tracks user activity to detect anomalies and maintain compliance.
For enterprises, identity and access management in cloud computing is critical. It bridges the gap between operational efficiency and security, enabling seamless collaboration while maintaining full control over sensitive data.
Why Cloud Identity Management is Essential for Enterprises
Cloud Identity Management is critical for enterprises because it strengthens security with multi-factor authentication and granular access controls, boosts operational efficiency by automating user onboarding and enabling single sign-on, and scales seamlessly as businesses grow.
It also ensures regulatory compliance with detailed audit trails and supports a distributed workforce by allowing secure access from any location. Strong cloud identity and access management is no longer just a technical requirement; it’s a strategic advantage.
Managing User Access Across Multi-Cloud Environments
Enterprises today often operate across several cloud platforms, including AWS, Microsoft Azure, and Google Cloud. Managing access manually across these environments is complex and prone to errors. A centralized cloud identity manager provides:
- Unified access control for cloud security.
- Consistent enforcement of security policies for all users.
- Simplified onboarding and offboarding of employees and contractors.
- Reduced administrative overhead and fewer security gaps.
Ensuring Compliance with Data Privacy Regulations
Regulatory compliance is a top concern for enterprises using cloud technologies. Laws like GDPR, HIPAA, and CCPA require strict controls on who can access sensitive data. Identity and access management in cloud computing helps organizations:
- Track and log all user access for audits.
- Enforce access policies consistently across platforms.
- Reduce the risk of non-compliance penalties.
- Demonstrate accountability to stakeholders and regulators.
Reducing the Risk of Credential Theft and Misuse
Credential theft and misuse are among the most common causes of cloud security breaches. Cloud identity management reduces these risks by enforcing:
- Strong password policies and Multi-Factor Authentication (MFA).
- Monitoring and alerting for unusual login patterns.
- Role-Based and Attribute-Based Access Controls to limit unnecessary privileges.
- Automated provisioning and deprovisioning to prevent orphaned accounts.
Enhancing User Experience with Seamless Access
Security should not come at the cost of productivity. Cloud-based identity management enhances the user experience by simplifying access without compromising security. Key benefits include:
- Single Sign-On (SSO): Employees log in once to access multiple applications.
- Reduced password fatigue and fewer login errors.
- Faster onboarding and access to required resources.
- Support for federated identities to enable partners and contractors to collaborate securely.
Key Components of Cloud Identity Management
Key components of cloud identity management include Authentication (confirming a user’s identity), Authorization (defining user permissions), User Management (overseeing user roles and lifecycle), Role-Based Access Control (RBAC), Auditing (monitoring user activity), and integration with directory services like Active Directory.
Advanced features such as Single Sign-On (SSO) and Multi-Factor Authentication (MFA) are also vital for strengthening security and improving the user experience.
Implementing these elements ensures effective cloud-based identity management across all cloud platforms.
Identity Lifecycle Management
Proper management of user accounts from creation to deactivation is critical for security and efficiency. Identity lifecycle management in a cloud identity manager ensures that the right employees have timely access while minimizing risks:
- Quick onboarding and offboarding of employees and contractors.
- Timely updates to access rights based on role changes.
- Reduction of orphaned accounts and potential security gaps.
Single Sign-On (SSO) for Cloud Applications
Enabling seamless access to multiple applications is a key benefit of cloud identity and access management. Single Sign-On (SSO) allows employees to work efficiently without compromising security:
- One login to access multiple cloud applications.
- Reduced password fatigue and fewer login errors.
- Streamlined workflows across SaaS platforms.
Multi-Factor Authentication (MFA) for Stronger Security
Adding layers of verification strengthens identity management in cloud computing. Multi-Factor Authentication (MFA) ensures that even if credentials are compromised, access remains secure:
- Protection against stolen passwords.
- Enforcement of stronger security policies.
- Supports compliance with regulatory standards.
Role-Based and Attribute-Based Access Controls
Controlling access based on roles or user attributes ensures users see only what they need. Identity management on the cloud uses RBAC and ABAC to:
- Limit unnecessary access privileges.
- Enforce consistent security policies.
- Reduce risks of internal misuse of sensitive data.
Privileged Access Management (PAM)
Privileged accounts carry higher risks and require specialized oversight. Cloud identity management solutions like PAM help organizations:
- Monitor and manage administrative access.
- Prevent misuse or insider threats.
- Secure critical cloud resources efficiently.
Continuous Monitoring and Audit Trails
Continuous oversight is vital to detect and respond to threats quickly. Identity and access management in cloud computing provides monitoring and audit trails that:
- Identify unusual or suspicious behavior in real-time.
- Maintain compliance with evolving regulations.
- Enable proactive threat mitigation and reporting.
How Cloud Identity Management Works
Cloud identity management operates by centrally verifying user identities (authentication) and controlling their access (authorization) across both cloud-based and on-premises systems.
It leverages protocols such as SAML and OAuth to enable Single Sign-On (SSO) and manages permissions through a role-based framework, ensuring robust security, regulatory compliance, and a seamless user experience in cloud environments.
Implementing cloud identity management effectively requires a step-by-step approach that ensures secure and seamless access across cloud environments. Understanding these steps helps enterprises protect sensitive data, streamline workflows, and maintain compliance.
Step 1: Authentication and Authorization in Cloud Environments
Authentication and authorization form the foundation of cloud identity and access management. Key steps include:
- Verifying user identities before granting access.
- Assigning role-based permissions to control resource access.
- Using Multi-Factor Authentication (MFA) for stronger security.
- Monitoring login patterns to detect suspicious activity.
Business Value: Ensures only authorized users access to sensitive resources, reducing the risk of breaches and strengthening regulatory compliance.
Step 2: Integration with SaaS, IaaS, and Hybrid Infrastructure
A robust cloud-based identity management system must integrate across all cloud platforms. Key actions include:
- Centralizing user management for SaaS, IaaS, and hybrid cloud environments.
- Applying consistent access policies across all platforms.
- Reducing administrative overhead and human errors.
- Enabling seamless collaboration between teams and external partners.
Business Value: Streamlines operations and enforces uniform security policies across all cloud platforms, reducing operational complexity.
Step 3: Automated Provisioning and Deprovisioning of Users
Automation ensures the timely and secure management of user accounts in identity management in cloud computing. Core steps include:
- Automatically granting new employees access to required applications.
- Instantly revoke access for departing employees to prevent security risks.
- Managing temporary or contractor accounts efficiently.
- Minimizing errors in user access assignments.
Business Value: Protects against orphaned accounts and insider threats while improving efficiency in user management processes.
Best Practices to Secure Your Cloud Environment with Identity Management
To secure your cloud environment, adopt a Zero Trust approach and enforce the Principle of Least Privilege. Implement robust Multi-Factor Authentication (MFA) and Single Sign-On (SSO), and use Role-Based Access Control (RBAC) to manage permissions effectively.
Conduct regular audits and monitoring, and apply adaptive authentication based on user risk. Centralize your identity management, automate workflows, encrypt sensitive data, and enforce strong password policies to substantially reduce cloud security risks.
Enforce Strong Authentication and MFA
Securing access starts with robust authentication. Implementing Multi-Factor Authentication (MFA) alongside strong password policies enhances cloud identity and access management. MFA ensures that even if credentials are compromised, unauthorized access is prevented, protecting sensitive cloud resources.
Adopt the Principle of Least Privilege
Grant users only the access necessary for their role. Using identity management in cloud computing, organizations can apply role-based (RBAC) or attribute-based (ABAC) controls to minimize unnecessary privileges. This reduces the potential attack surface and enforces consistent access policies.
Regularly Audit and Review Access Controls
Continuous review of permissions is essential in identity management on the cloud. Periodic audits help identify inactive accounts, orphaned privileges, or excessive access rights, ensuring that access remains appropriate across cloud applications and services.
Implement Automated Provisioning and Deprovisioning
Automation in cloud identity management solutions simplifies account lifecycle management. Employees, contractors, and temporary users can be added or removed efficiently, reducing administrative errors and ensuring timely updates to access privileges.
Use Identity Federation for Simplified Access Management
Identity federation allows secure access across multiple systems and platforms in cloud-based identity management. By supporting Single Sign-On (SSO) and integrating external identities, organizations can streamline workflows while maintaining centralized control of access policies.
Continuously Monitor User Activity for Anomalies
Monitoring user activity in real-time is a core part of cloud identity and access management. Detecting unusual login patterns or access behavior helps prevent potential security incidents and ensures that cloud resources are used appropriately.
Challenges in Cloud Identity Management
Cloud identity management faces challenges such as multi-cloud complexity, misconfigured roles and overprivileged accounts, and managing the full user lifecycle. Ensuring compliance, integrating with on-premises and cloud systems, and maintaining centralized visibility are also difficult, along with limited resources and the constant need for security updates and monitoring.
Managing Access Across Hybrid and Multi-Cloud Platforms
Enterprises often operate across multiple cloud platforms, making identity and access management in cloud computing complex. Key challenges include:
- Ensuring consistent access policies across SaaS, IaaS, and hybrid infrastructures.
- Managing user accounts and permissions centrally without creating administrative bottlenecks.
- Preventing gaps that could be exploited by unauthorized users.
Balancing Security with User Convenience
Maintaining strong security through cloud identity and access management can sometimes affect user experience. Challenges include:
- Implementing Multi-Factor Authentication (MFA) without slowing workflows.
- Providing seamless access via Single Sign-On (SSO) while maintaining control.
- Ensuring security measures do not disrupt productivity.
Preventing Identity Sprawl and Shadow IT
Uncontrolled identity creation and unmanaged apps create risks in identity management on the cloud. Challenges include:
- Detecting and managing orphaned or unused accounts.
- Preventing employees from using unauthorized applications (Shadow IT).
- Keeping a centralized record of all users and access rights.
Staying Compliant with Evolving Regulations
Regulatory requirements in cloud computing are constantly evolving, posing challenges for identity management in cloud computing:
- Keeping access controls and audit trails compliant with GDPR, HIPAA, CCPA, and other standards.
- Adapting policies quickly to meet new or updated regulations.
- Ensuring all cloud platforms adhere to enterprise compliance standards.
Using CloudEagle.ai to Manage Access and Balance Security
Managing access and securing cloud environments is a complex challenge for modern enterprises. Cloud identity management solutions like CloudEagle.ai simplify access management by centralizing control over identities and permissions across your cloud infrastructure.
With CloudEagle, you can automate critical access management workflows, monitor user access in real time, and gain complete visibility across all your SaaS applications, reducing security risks and improving operational efficiency.
Transparent Access Control
CloudEagle provides a centralized platform for controlling who has access to which applications, making identity management on the cloud more secure and efficient.
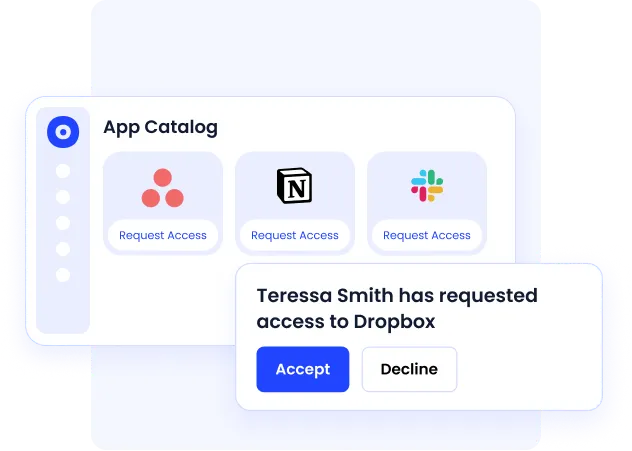
Key features include:
- An intuitive application catalog where users can request access to apps.
- Admins can review and approve requests efficiently, ensuring proper authorization.
- Instant notifications via email or Slack alert admins about access requests.
- The self-service app catalog empowers employees to request and track their access without relying on IT teams.
- Enables consistent policy enforcement across all cloud applications, reducing the risk of unauthorized access.
Easy App Access Tracking
Tracking access across multiple applications is a core feature of cloud identity and access management.
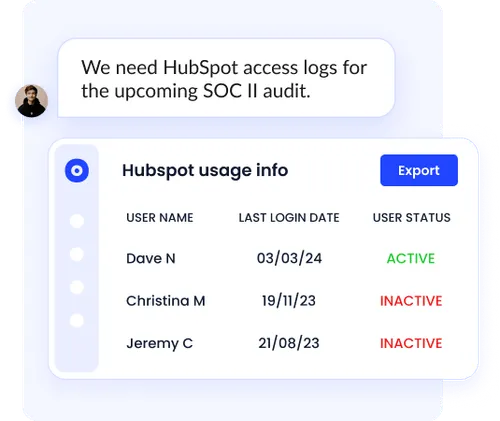
CloudEagle makes it easy to:
- Export detailed access logs directly from the portal for compliance and audits.
- Monitor which users have access to each application at any given time.
- Identify unused accounts or excessive privileges quickly.
- Maintain complete visibility of all SaaS applications in a single dashboard.
Automated User Provisioning
Automation reduces the workload on IT teams while ensuring secure access in cloud-based identity management. CloudEagle enables:
- Automatic assignment of access to new employees based on their role and department.
- Elimination of spreadsheets and manual tracking for onboarding processes.
- Faster productivity for employees by granting immediate access to required applications.
- Efficient handling of temporary or contractor accounts, ensuring proper role-based permissions.
Automated User Deprovisioning
Removing access when an employee leaves or becomes inactive is critical in identity management in cloud computing.
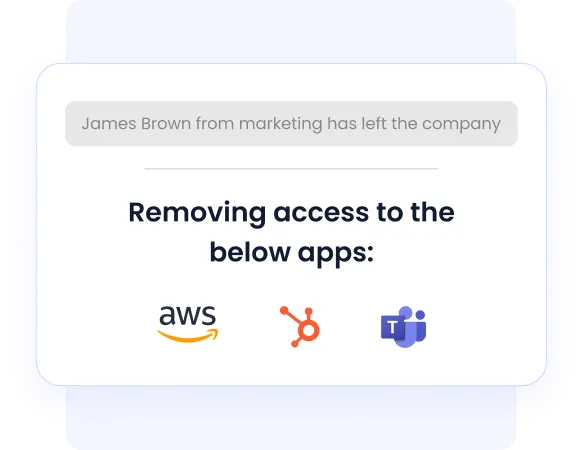
CloudEagle’s automated deprovisioning features include:
- Instant revocation of user access upon employee exit.
- Workflows that automatically deprovision accounts inactive for a set period.
- Reduced risks associated with orphaned accounts or insider threats.
- Enhanced security by maintaining a real-time, accurate view of active users.
App Discovery
CloudEagle goes beyond basic access management by helping users discover applications relevant to their role and department, improving overall cloud identity management efficiency:
- Employees receive recommended apps without waiting for manual approvals.
- Pre-configured access ensures immediate productivity from day one.
- Reduces unnecessary access requests to IT teams.
- Helps maintain standardized access across teams while boosting operational efficiency.
Integration Capabilities
Integration is a key aspect of effective cloud identity and access management. CloudEagle supports over 500 + direct integrations, allowing enterprises to:
- Connect with HRIS, Single Sign-On, finance, and other internal systems.
- Gain accurate insights into user access, contracts, licenses, and SaaS spend.
- Ensure data protection and consistency across multiple cloud platforms.
- Streamline workflows while maintaining comprehensive visibility for administrators.
Comprehensive Reporting and Monitoring
CloudEagle’s reporting and monitoring features strengthen identity management on the cloud:
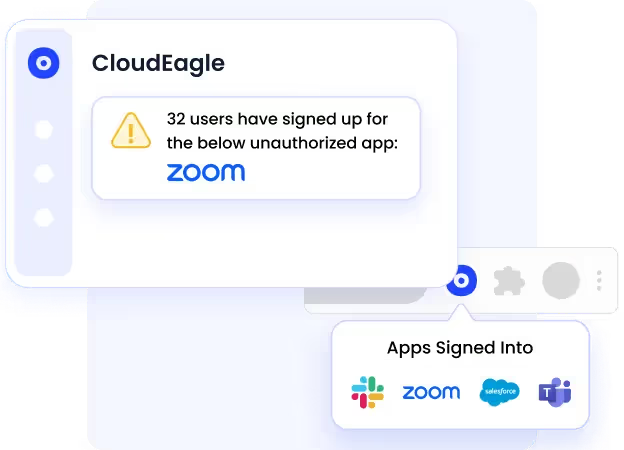
- Generate real-time reports on user access, application usage, and policy compliance.
- Identify potential risks such as excessive permissions or unusual activity.
- Support audits with detailed logs and actionable insights.
- Help IT teams proactively manage identity and access across the organization.
Final Thoughts
Cloud identity management provides centralized control, securing user access and streamlining workflows across cloud platforms. Key features like Single Sign-On and Multi-Factor Authentication help protect data while enhancing user experience. Automated provisioning and activity monitoring further reduce risks and ensure compliance.
Enterprises face challenges managing identities in multi-cloud environments, balancing security with convenience. Solutions automate access controls and enable real-time monitoring for better oversight. Consistent policy enforcement simplifies management and supports regulatory compliance.
CloudEagle.ai streamlines access requests, automates user provisioning, and delivers complete visibility for IT teams. Efficient management reduces risks, improves productivity, and adapts to business growth.
Book a free demo with cloudeagle.ai because seamless cloud security drives smarter enterprise success.
Frequently Asked Questions
- What are cloud identity services?
Cloud identity services are cloud-based solutions that manage user identities, authentication, and access to applications and resources securely, often offering features like single sign-on (SSO), multi-factor authentication, and centralized user management. - What are the different types of IAM?
IAM types include Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), Identity Federation, and Privileged Access Management (PAM). These help control who can access what across cloud and on-premise systems with varying levels of granularity. - What is a cloud-based identity provider?
A cloud-based identity provider (IdP) is a service that manages user authentication and identity verification in the cloud, enabling secure access to applications via protocols like SAML or OAuth without on-premises infrastructure. - What is CIdP authentication?
CIdP authentication refers to Cloud Identity Provider authentication, which validates user identities through cloud-based IdPs, enabling secure access management across various cloud services and applications. - What is identity and access management in cloud?
IAM in cloud manages and controls user identities and access permissions for cloud resources, ensuring only authorized users gain access to data and applications, often via centralized policies and authentication mechanisms. - Which IAM tool is best?
The best IAM tool depends on business needs. Top tools like CloudEagle.ai, Microsoft Azure AD, Okta, and Google Cloud Identity offer scalable, secure cloud identity management with features like automation, SSO, and MFA.

%201.svg)







.avif)




.avif)
.avif)




.png)









