HIPAA Compliance Checklist for 2025

Every organization today runs on SaaS. But not every app in use is one IT knows about. Shadow IT, those unsanctioned tools employees adopt to move faster, has become the quiet disruptor of enterprise control.
A recent Kaspersky report found that 85% of companies experienced cyber incidents in the past two years, and 11% were directly linked to Shadow IT. It’s a reminder that the biggest security gaps don’t always come from external threats, but from the everyday tools employees bring into the stack.
This article will cover what organizations lose when they can’t fully track Shadow IT, its risks, the blind spots, and how CloudEagle helps teams regain control without slowing innovation.
TL;DR
- Most IT teams still manage SaaS apps through manual spreadsheets, disconnected systems, and slow audits, creating blind spots and security risks.
- Limited visibility leads to shadow IT, duplicate purchases, and overspending on tools that aren’t even in use.
- CloudEagle automatically discovers every SaaS app across your stack, giving you complete visibility into spend, usage, and compliance.
- With one unified dashboard, IT and finance teams can eliminate redundancy, cut costs, and enforce governance effortlessly.
- The result: lower SaaS spend, tighter security, and smarter, data-driven decision-making.
1. How do IT Teams Try to Manage Apps Today?
Most IT teams still manage SaaS applications with methods that weren’t built for today’s scale or complexity. Spreadsheets, email requests, and disconnected tools remain the backbone of app tracking, leaving organizations exposed to inefficiencies and invisible risks.
a. Manual tracking and fragmented visibility.
Spreadsheets remain the default system of record for tracking SaaS usage, licenses, and renewals. IT teams manually reconcile data across SSO logs, finance reports, and HR systems - a process that’s slow, error-prone, and outdated the moment it’s complete. With procurement, contract, identity, and finance tools all operating in silos, there’s no unified view of the truth.
As Robert Findlay, Head of Asia at Smartsheet, notes, “If you do not have tools in place that provide real-time information to help you pivot when you need to, you could very well be setting yourself up for failure.”
b. Decentralized purchasing and reactive discovery.
In many companies, employees buy software independently using corporate or even personal cards. IT only finds out when charges appear on credit statements or during annual audits.
Some teams monitor SSO activity or rely on employees to self-report the tools they use, but those approaches rarely capture the full picture.
c. Manual provisioning and renewals.
Onboarding and offboarding are still handled manually, requiring updates across HR systems, SSO tools, and individual app consoles. It’s common for former employees to retain access for weeks after departure.
Renewals follow the same pattern tracked through shared calendars or spreadsheets, often leading to missed cancellations, duplicate contracts, or rushed negotiations.
d. Limited governance and compliance oversight.
When each department makes independent purchase decisions, IT loses its ability to enforce security and compliance policies. This decentralization not only drives redundant spending but also introduces regulatory risks. Without continuous monitoring of third-party integrations, even “trusted” apps can create vulnerabilities that IT teams have no way to detect or mitigate.
The result is a manual, reactive, and error-prone process. IT teams spend more time reconciling data than optimizing it. And as SaaS adoption accelerates, these outdated management methods are no longer sustainable; they create the very blind spots that Shadow IT thrives in.
2. What IT Teams Miss Without Complete Visibility?
When IT teams can’t see everything, they start managing assumptions, not reality. As a result, unapproved tools lead to slipping through, budgets spiraling, and compliance turning into a guessing game.
a. Security risks go unnoticed.
Shadow IT thrives in the dark. Without full visibility, teams are blind to unauthorized apps that bypass SSO or use unmanaged integrations. These blind spots become attack surfaces waiting to be exploited.
The Cloud Security Alliance found that only 23% of organizations have complete visibility into their SaaS landscape, while 73% struggle to track risks from third-party connected apps - a sign that most security teams are reacting after the damage is done. Unmonitored apps, misconfigurations, and overprivileged access remain the perfect recipe for breaches.
b. Compliance becomes a moving target.
Auditors expect clear access trails, policy adherence, and proof of control. But without a single source of truth, IT teams can’t show who’s using what or whether data handling aligns with standards like GDPR or SOC 2.
Access reviews end up partial, and certifications hang by a thread. What should be a routine audit turns into a time sink filled with spreadsheets and incomplete reports.
c. Budgets quietly leak.
When each department manages its own stack, redundant tools and unused licenses pile up. Procurement can’t negotiate effectively because the full spend picture doesn’t exist.
Over time, hidden renewals and duplicate subscriptions drain budgets without anyone noticing. Manual tracking compounds the issue; by the time the data is ready, it’s already outdated.
d. Operational inefficiency spreads.
Employees wait days for approvals or retain access long after they’ve left. IT teams spend hours reconciling systems instead of improving them.
Fragmented visibility slows onboarding, increases support tickets, and creates dependency loops between IT, finance, and security teams. The cycle feeds itself more complexity, less control.
e. Strategic clarity disappears.
Visibility isn’t just a technical problem; it’s a leadership one. Without a unified, real-time view, decision-makers can’t prioritize, consolidate, or plan ahead. The result is reactive management decisions made too late, with too little data.
When visibility fades, control follows. IT teams don’t just lose sight of their apps; they lose the ability to secure, optimize, and scale with confidence.
3. How Does CloudEagle Help IT Teams Tackle Shadow IT?
CloudEagle replaces scattered guesswork with a complete understanding of your SaaS environment. Instead of discovering shadow IT months later through audits or credit card statements, IT teams see every application, every user, and every device the moment activity begins, even in remote or BYOD setups.
a. Automated discovery across every data source
CloudEagle continuously scans your environment to detect both sanctioned and unsanctioned apps, pulling intelligence from every available signal:
- SSO and IdP logs
- HRIS and org structure changes
- Browser activity and extensions (a growing source of micro–shadow IT)
- Finance and card transactions
- MDM, Netskope, and device-level activity across BYOD and remote environments
With 500+ integrations, including Okta, Google Workspace, HRIS, CASB, MDM, and financial systems, CloudEagle identifies SCIM and non-SCIM apps with equal accuracy. Traditional tooling can't see activity happening outside SSO, but CloudEagle’s behavioral and network-based discovery fills these blind spots instantly.
b. A single dashboard for complete visibility
All your SaaS activity, such as usage trends, vendor contracts, renewal timelines, user access, spend, and app ownership, lives in one unified dashboard.
No more flipping between SSO logs, spreadsheets, and expense tools. CloudEagle correlates every data point into a single, always-live inventory that highlights:
- Shadow IT tools
- Duplicate apps
- Redundant capabilities
- Underutilized licenses
- High-risk or non-compliant applications
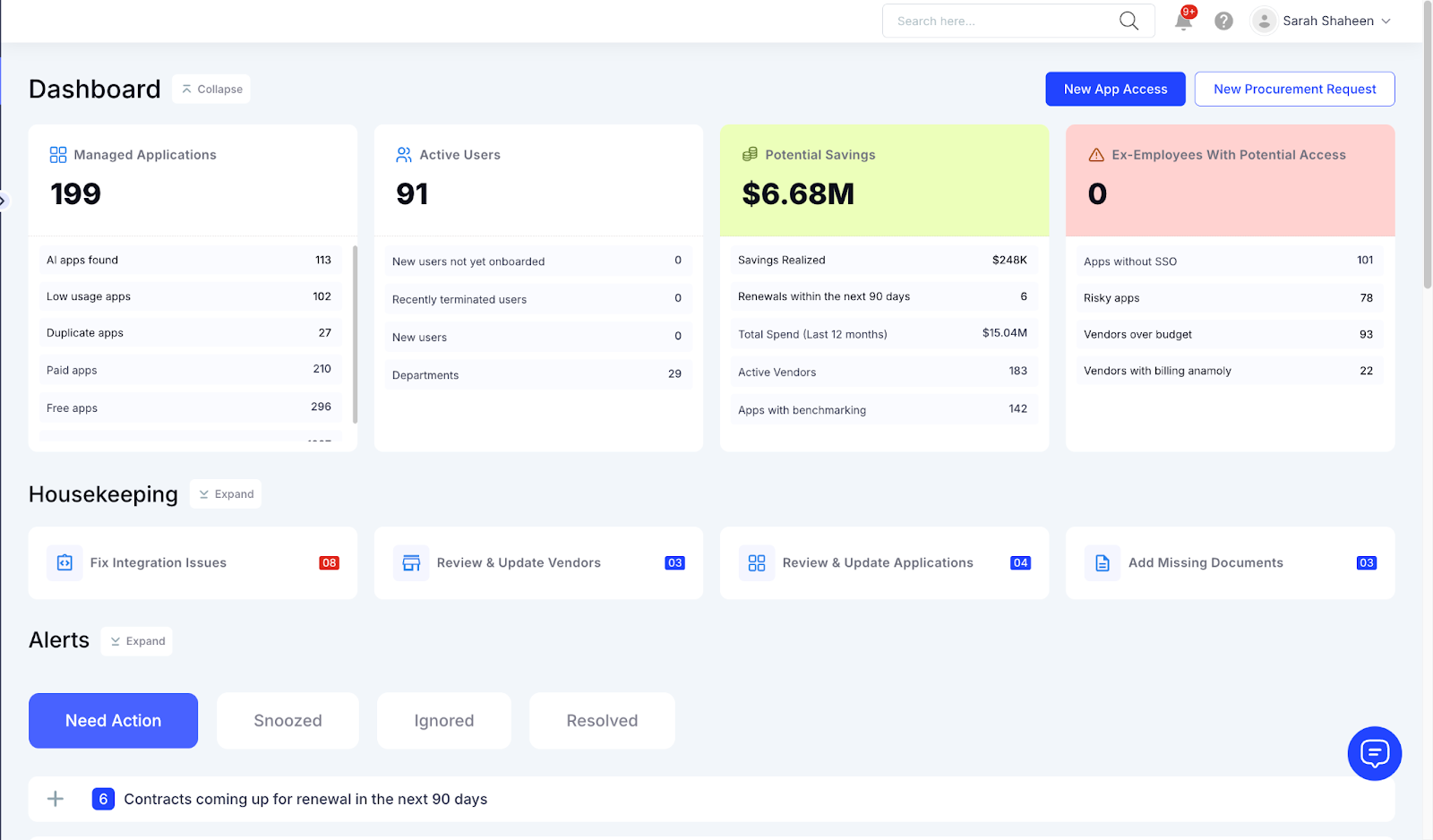
This creates a single source of truth that teams can trust for security, procurement, and renewal decisions.
c. Proactive alerts, automated remediation, and policy enforcement
CloudEagle flags unapproved apps the moment they appear before they spread across teams or put sensitive data at risk.
IT can define automated policies to:
- Block risky or unauthorized tools
- Restrict usage based on department or role
- Trigger provisioning or deprovisioning workflows
- Revoke elevated permissions from shadow IT tools
- Downgrade or terminate unvetted applications
Zero-touch workflows ensure offboarding, role changes, and department transfers never leave security gaps that shadow IT can exploit.
d. Controlled access through an employee app catalog
CloudEagle prevents shadow IT at the source with a company-branded app catalog containing all approved tools. Employees request access from a verified list instead of signing up independently with personal emails or devices.
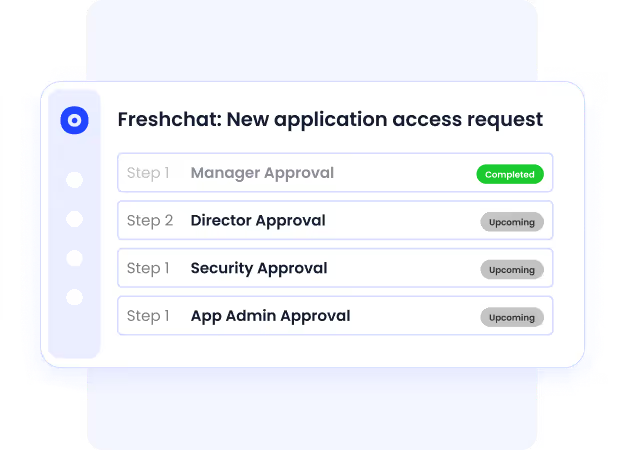
Every request is logged, routed for approval, and tracked to ensure transparent, compliant usage across departments.
e. AI-powered insights to reduce cost and risk
CloudEagle’s AI engine continuously analyzes usage patterns and spending to detect duplicates, redundant tools, and high-risk applications. It flags unapproved apps that may pose compliance or security threats and helps teams reclaim unused licenses, consolidate vendors, and redirect spend where it delivers the most value.
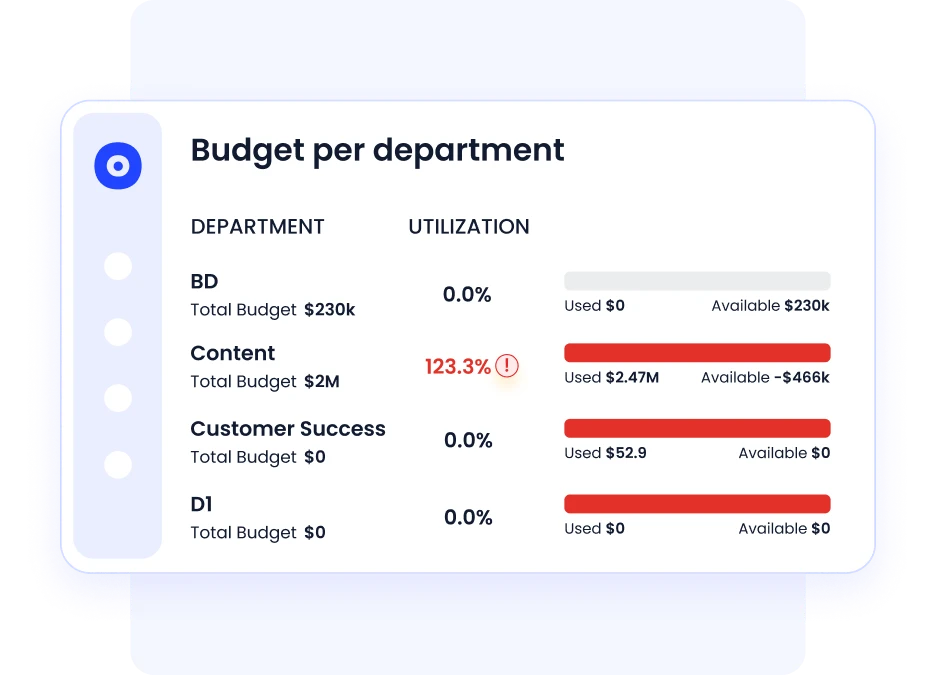
Each app receives a risk score based on security posture, data sensitivity, compliance requirements (GDPR, SOC2, HIPAA), and access behavior. This helps IT prioritize mitigation and eliminate the riskiest shadow IT first.
f. Privilege and identity insights that stop unauthorized access
Shadow IT often bypasses identity governance, giving users more access than intended. CloudEagle prevents this through:
- Privilege escalation detection
- Least-privilege enforcement
- Monitoring permissions across SCIM + non-SCIM tools
- Detecting abnormal access patterns such as:
- Logins from new devices (BYOD)
- Elevated permissions in unsanctioned apps
- Sensitive data uploads to personal SaaS
g. Continuous monitoring across remote work and BYOD environments
With remote and hybrid work, employees often use:
- Personal laptops
- Personal email IDs
- Personal cards
- Non-IT-vetted SaaS tools
- Browser-based “quick sign-up” apps
CloudEagle continuously monitors all devices and user behaviors, ensuring that the shift to remote work doesn’t create unmanaged SaaS sprawl.
4. Why Is CloudEagle the Best Choice for SaaS Visibility?
CloudEagle gives organizations a level of SaaS visibility that spreadsheets, CASBs, and identity tools simply can’t match. With every app, user, device, and vendor contract in one place, teams can make confident, data-backed decisions instead of guessing what’s happening in the shadows.
Complete visibility that teams can trust
CloudEagle consolidates SaaS usage, spend, and access data into a single source of truth. This eliminates blind spots, especially across remote workers, BYOD devices, and non-SCIM tools, and ensures leaders always know exactly what exists in the environment.
Better security and fewer surprises
Shadow IT is no longer invisible. CloudEagle highlights risky apps, flags compliance gaps, and shows how tools connect to sensitive systems. This reduces audit headaches and strengthens security posture without additional overhead.
Immediate ROI through cost optimization
With full visibility, organizations consolidate redundant tools, reclaim unused licenses, and cut wasteful spend. Procurement teams negotiate with leverage because they finally have real usage data instead of assumptions.
For example, ICEYE reduced its SaaS spend by $300,000 in just 120 days using CloudEagle’s insights and benchmarking data. By right-sizing licenses, deprovisioning idle users, and renegotiating contracts, ICEYE transformed unmanaged SaaS growth into an ongoing cost-optimization strategy.

Fast onboarding and scalable results
CloudEagle delivers value within days, not months. Its AI-driven automation and deep integrations scale as your SaaS footprint grows, ensuring visibility never lags behind business expansion.
CloudEagle stands out because it turns SaaS visibility into control, cost savings, and confident decision-making, leading to the foundation every modern IT, security, and finance team needs.
5. Ready to See What You’ve Been Missing?
Shadow IT doesn’t disappear with policies; it fades when you have complete visibility. Now you know what’s at stake when SaaS sprawl goes unchecked.
With CloudEagle.ai, you can finally uncover every app, every cost, and every hidden risk, then turn that clarity into action. Gain control, cut waste, and let your SaaS stack work smarter, not larger. Book a demo or start your free trial to see it in action.
.avif)
%201.svg)







.avif)




.avif)
.avif)




.png)









