HIPAA Compliance Checklist for 2025

Think about your last day at work. You probably returned your laptop, handed in your badge, and maybe grabbed that coffee mug. But if your exit isn’t managed properly, you could still have access to sensitive systems weeks later.
That’s why the Joiner-Mover-Leaver framework matters. Every onboarding, role change, or offboarding carries risk.
And today? Those risks are more expensive than ever.
IBM Security’s 2024 report found that over 80% of data breaches involve compromised employee credentials.
In this guide, you’ll learn the best practices for managing the JML lifecycle so your organization stays efficient, compliant, and secure, without adding extra work for IT.
TL;DR
- The Joiner-Mover-Leaver (JML) framework manages employee access from onboarding to role changes and offboarding, ensuring users only have the permissions they need.
- Manual JML workflows create risk, orphaned accounts, privilege creep, and delayed revocation are leading causes of credential-based breaches.
- Automating provisioning, deprovisioning, and role updates reduces identity-related security incidents by over 67% and accelerates productivity for new hires and movers.
- Best practices include RBAC, Zero Trust, real-time access auditing, HR-IT-System integration, and centralized identity governance through an IGA/IAM platform.
- CloudEagle.ai simplifies JML by automating onboarding and offboarding, enforcing least-privilege permissions, reclaiming unused licenses, and keeping organizations audit-ready.
Understanding the Joiner-Mover-Leaver (JML) Framework
The Joiner-Mover-Leaver (JML) framework is how organizations manage employee access throughout their lifecycle.
It ensures identities are created when someone joins, permissions are updated when their role changes, and all access is removed when they leave.
The "Joiner" Stage
Picture this: it’s someone’s first day, and they’re excited to dive in. But they’re stuck waiting for system access while IT scrambles across multiple platforms.
Not exactly the warm welcome you’d hope for.
The joiner stage focuses on provisioning access efficiently without compromising security. New employees need the right tools from day one: email accounts, collaboration platforms, department-specific apps, and role-based permissions.
Key points:
- Grant enough access to be productive without handing over the keys to the kingdom.
- Automated provisioning reduces onboarding time by 73% (CloudEagle 2025 IGA Report).
- Use predefined role templates to eliminate guesswork and speed up time-to-productivity.
- Stanford-Tessian research reveals that 88% of breaches involve employee mistakes. That underscores why security education can't be an afterthought.
The "Mover" Stage
Internal role changes can create major security gaps. An employee moves from marketing to product management, which now creates a risk for IT.
The employee may retain access to old systems plus new tools, causing privilege creep.
Key points:
- Reassess access completely whenever roles change; remove old permissions and grant new ones.
- Document all changes to maintain compliance.
- Automated JML workflows in IAM systems can trigger updates as soon as HR reflects a role change.
- CloudEagle's 2025 IGA Report uncovered something shocking: 68% of organizations struggle with access reviews during role changes.
The "Leaver" Stage
Offboarding seems simple: someone leaves, revoke their access. Reality is different; many organizations take too long.
Key points:
- The CloudEagle 2025 IGA Report found that 42% of organizations take more than a week to fully revoke access after an employee departs; some take more than a month.
- Immediate revocation is critical: email, VPN, API keys, SSH certificates, mobile device management, and third-party apps.
- Automated deprovisioning completes offboarding 85% faster than manual processes.
- Lingering access is a huge risk, whether from disgruntled ex-employees or external attackers targeting old accounts.
Common Challenges in Managing the JML Lifecycle
Even organizations that care about security often struggle with Joiner-Mover-Leaver (JML) implementation due to legacy systems and departmental silos.
1. Manual Processes and Delays
Many IT teams still juggle spreadsheets, emails, and manual account creation across multiple platforms, making onboarding and offboarding slow and error-prone.
Productivity suffers during delays, while security gaps grow when offboarding takes weeks.
According to the 2025 CloudEagle IGA Report, manual processes increase the risk of orphaned accounts by 300%, leaving ghost accounts that attackers could exploit.
2. Lack of Centralized Visibility
Most organizations do not have a unified view of who has access to what across their IT ecosystem.
Siloed systems like HR databases, Active Directory, IAM platforms, and SaaS apps make accurate visibility nearly impossible.
Organizations without centralized identity governance experience 58% more compliance violations, showing that incomplete visibility is both a security and a business risk.
3. Inconsistent Policy Enforcement
Policies may exist, but inconsistent interpretation across departments creates gaps.
Some teams grant broad permissions “just in case,” while others strictly follow least-privilege principles, leaving uneven security coverage.
When policy enforcement depends on manual judgment, variance is inevitable, resulting in potential compliance issues and security exposures.
Best Practices for a Seamless JML Process
Streamline the JML process by automating account workflows and fostering HR-IT collaboration for timely, accurate access management. Regular audits, clear policies, and a centralized system ensure security and compliance throughout the user lifecycle.
1. Automate Provisioning and Deprovisioning
Automation is the backbone of any efficient JML process. It speeds up access provisioning, removes human error, and ensures departing employees lose access immediately.

According to the CloudEagle 2025 IGA Report, organizations with 80%+ automation in JML reduce identity-related security incidents by 67%.
Key benefits:
- Instant provisioning: New hires get access to all tools within hours, not days, boosting productivity.
- Zero human error: Workflows follow the same steps every time, preventing orphaned accounts.
- Immediate deprovisioning: Former employees lose access across all systems instantly, reducing breach risk.
- Audit trails: Every action is logged automatically, making compliance reporting effortless.
- License optimization: Departed employees’ licenses and software are reassigned automatically, saving costs.
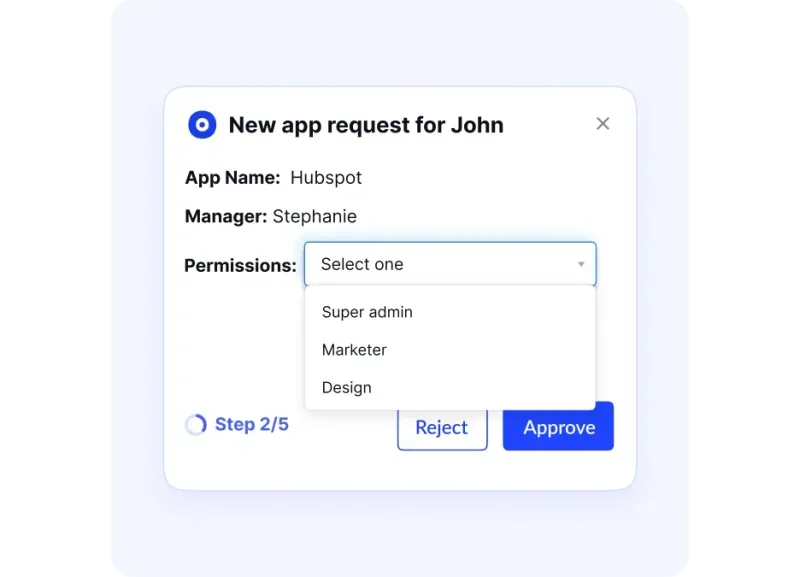
2. Implement Role-Based Access Control (RBAC)
RBAC groups permissions by role instead of individuals, ensuring everyone has just the access they need.
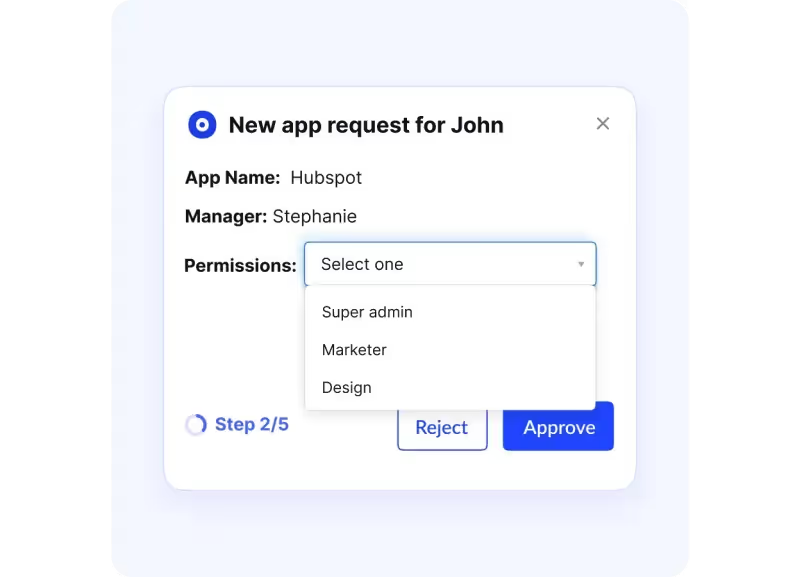
It also makes internal role changes seamless without adding risk.
A Gartner study found that organizations using RBAC reduced privilege creep by 50%, while Forrester reports that role-based onboarding accelerates productivity by up to 60%.
Key benefits:
- Faster onboarding: Employees inherit predefined permissions automatically.
- Reduced privilege creep: Role changes trigger automatic permission updates.
- Easier auditing: Review role-level permissions instead of each account individually.
- Scalability: Supports hundreds or thousands of employees without extra manual work.
- Clear accountability: Permissions tied to business functions, not individuals.
3. Maintain Real-Time Access Auditing
You can’t secure what you can’t see.
Real-time auditing gives visibility into who has access, how it’s used, and whether it aligns with current roles.

Even according to Verizon’s 2024 Data Breach Investigations Report shows that detecting breaches in minutes instead of days saves $1.2 million per incident.
Key practices:
- Continuous monitoring: Tracks access patterns in real time.
- Automated anomaly detection: Flags unusual behavior immediately.
- Regular access reviews: Quarterly or monthly recertifications ensure permissions remain appropriate.
- Compliance reporting: Generate instant audit-ready reports.
- Historical analysis: Review changes over time to catch recurring issues.
4. Integrate HR, IT, and Security Systems
Silos are the enemy.
Integration ensures HR updates trigger automatic workflows across IT and security platforms, preventing delays and errors.
Key benefits:
- Single source of truth: HR drives all identity changes.
- Automatic synchronization: Updates flow to all connected systems.
- Reduced manual communication: No more chasing emails between departments.
- Faster response: Access changes are applied in minutes, not days.
- Data consistency: Employee information stays accurate across platforms.
5. Document Clear JML Policies
Technology helps, but policies guide it. Clear, written rules ensure everyone knows their responsibilities, timelines, and approval chains, reducing mistakes and compliance risks.
CloudEagle 2025 reports organizations with documented JML policies have 45% fewer audit findings.
In addition, ISACA research finds that clear access policies reduce misconfigurations by 52%.
Key policies:
- Standard provisioning timelines for different roles.
- Approval chains for regular and exceptional access.
- Mandatory access review schedules.
- Immediate steps for offboarding.
- Procedures for role changes and transfers.
- Escalation paths for conflicts.
- Documentation for audits and compliance.
- Exception handling processes.
6. Implement Zero Trust + Least Privilege
A seamless JML process needs more than just correct access; it needs minimal access.
Zero Trust ensures employees only access what they need when they need it, while Least Privilege prevents lingering access during role changes.
According to Microsoft’s 2024 Security Benchmark Report, Zero Trust adoption reduces lateral movement risk by 92% during internal access breaches.
Key benefits:
- Limits the blast radius if credentials are compromised
- Ensures movers don’t accumulate access over time
- Easier to identify + revoke unnecessary permissions
7. Standardize Offboarding With Immediate Access Revocation
The “Leaver” stage is where most breaches happen.
A standardized, time-bound offboarding playbook ensures access is revoked instantly across all clouds, SaaS apps, and shadow tools.
IBM’s 2025 Cost of Insider Threat Report shows 46% of data breaches involve dormant or orphaned accounts.
Key practices:
- Use HR exit triggers to initiate instant deprovisioning
- Reclaim SaaS licenses & reassign automatically
- Revoke access from personal devices and former SSO sessions
8. Centralize Identity Lifecycle in an IGA / IAM Platform
Spreadsheets, email approvals, and individual admin actions don’t scale.
A centralized Identity Governance & Administration (IGA) platform acts as the control plane for lifecycle management.
CloudEagle data shows organizations using a centralized IGA reduce manual IT workload by 53%.
Key benefits:
- One dashboard for joiners, movers, and leavers
- Standardized workflows instead of tool-by-tool provisioning
- Better compliance posture with audit-ready logs
Benefits of Streamlined JML Management
Getting your Joiner-Mover-Leaver process right isn’t just about closing security gaps; it directly impacts efficiency, cost savings, and compliance readiness.
1. Strengthened Security Posture
A smooth JML workflow reduces risk from lingering access, privilege creep, and insider threats.
- Companies that detect insider threats quickly save up to $2.7 million per incident.
- Real-time access monitoring helps flag unusual behavior, reducing the chance of breaches.
- Organizations with strong onboarding and access policies see 52% better employee retention and productivity.
2. Operational Efficiency and Cost Savings
Automating JML processes frees IT from repetitive tasks, letting teams focus on strategic work.
- Privilege management and automation can reduce manual errors by 50%, cutting wasted time.
- Faster onboarding and offboarding accelerate productivity and reclaim unused licenses.
- Less reliance on helpdesk support means fewer tickets and smoother workflows.
3. Enhanced Compliance and Audit Readiness
A clear, automated JML framework keeps your organization audit-ready without extra effort.
- Historical logs and access reviews provide ready evidence for SOC 2, ISO 27001, or GDPR audits.
- Automated recertifications flag unnecessary permissions before they create compliance risks.
- Policy-driven workflows ensure consistent enforcement across teams, reducing misconfigurations.
How CloudEagle.ai Automates Employee Onboarding and Offboarding
Manual onboarding and offboarding are slow, error-prone, and risky. CloudEagle.ai streamlines these processes to improve efficiency, security, and compliance.
Zero-Touch Onboarding
Pain Point: Manual onboarding often delays system access, frustrates new hires, and increases IT workload. When employees can’t get started immediately, productivity suffers.

CloudEagle Solution: CloudEagle automatically provisions access based on role, department, and location, ensuring new hires are productive from day one.
- New hires get access to all tools within hours, not days.
- Role changes trigger instant updates to permissions.
- Eliminates manual errors and reduces IT workload.
Automated Offboarding
Pain Point: When employees leave, lingering access can create serious security risks and compliance issues. Orphaned accounts are an easy target for attackers.
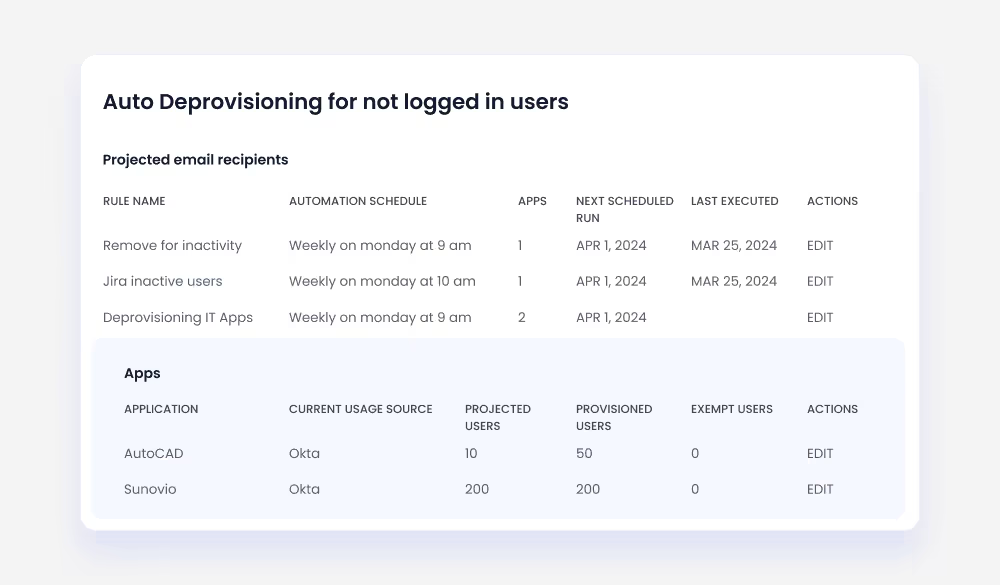
CloudEagle Solution: CloudEagle automatically revokes access across all systems and apps, including those outside traditional IAM platforms.
- Prevents orphaned accounts and unauthorized access.
- Frees up unused licenses for reassignment.
- Ensures audit-ready offboarding records.
Role-Based Access Management
Pain Point: Employees often retain access they no longer need, causing privilege creep and regulatory risks. Unchecked permissions make audits painful and risky.
CloudEagle Solution: CloudEagle assigns access strictly based on role, keeping employees productive while minimizing security and compliance risks.
- Employees only have access to the apps they need.
- Detailed logs simplify audits and provide transparency.
- Reduces compliance risks and improves overall security posture.
Integration with Your Tech Stack
Pain Point: Fragmented systems make onboarding and offboarding cumbersome, causing errors and inefficiencies. IT teams struggle to coordinate across multiple platforms.
CloudEagle Solution: CloudEagle integrates with Okta, Microsoft AD, and other systems, centralizing management for seamless workflows.
- Streamlines workflows across multiple platforms.
- Reduces manual IT effort and bottlenecks.
- Supports scalable operations for growing teams.
Final Words
Managing the Joiner-Mover-Leaver lifecycle is essential for keeping your organization secure and compliant. Every employee transition, onboarding, role change, or offboarding, introduces potential risks if access isn’t handled properly.
Following best practices like automated provisioning, role-based access control, real-time auditing, and system integration ensures faster onboarding, reduces privilege creep, and closes security gaps. Organizations that implement these practices also see improved productivity and smoother compliance.
CloudEagle.ai makes it simple by automating onboarding and offboarding, enforcing role-based access, and providing detailed audit logs. This allows your IT teams to focus on strategic initiatives while maintaining security and compliance effortlessly.
Book a free demo today to see how CloudEagle.ai can secure your employee lifecycle and streamline access management.
Frequently Asked Questions
- What is the Joiners, Movers, and Leavers policy?
A policy that manages employee access throughout their lifecycle, ensuring secure onboarding, role changes, and offboarding. - What is JML used for?
JML ensures employees get appropriate access when joining, updating, or leaving, reducing security risks and maintaining compliance. - What is JML in identity?
In identity management, JML tracks and controls user access rights across systems, aligning permissions with roles and employment status. - What is the JML process in IAM?
The JML process in IAM automates provisioning, updates, and deprovisioning of accounts to enforce security, least privilege, and compliance.

%201.svg)









.avif)




.avif)
.avif)




.png)









