HIPAA Compliance Checklist for 2025

Managing user accounts and access rights sounds straightforward, until you scale. Most organizations today handle dozens of SaaS apps, hybrid environments, and diverse user groups, from new hires to contractors and vendors. Without the right processes in place, this complexity leads to bottlenecks, manual errors, and even security risks.
This is where user lifecycle management (ULM) steps in. Done right, it not only protects sensitive data but also ensures your IT team doesn’t drown in repetitive, manual tasks. The real game-changer? Automation.
By automating provisioning, deprovisioning, and role modifications, you can streamline the user lifecycle management process, freeing your IT staff to focus on strategic initiatives instead of firefighting.
In this blog, we’ll explore the common bottlenecks in user lifecycle management, the risks of mismanagement, and how automation provides a scalable solution. We’ll also dive into the key benefits enterprises gain from automated workflows, and how platforms like CloudEagle.ai help organizations modernize identity and access management (IAM) at scale.
TL;DR
- User lifecycle management automates onboarding, role changes, and offboarding, reducing manual errors and delays.
- Poorly managed lifecycles create security risks, compliance issues, and operational inefficiencies.
- Automation streamlines provisioning, access approvals, updates, and role-based controls.
- Key benefits include faster onboarding, fewer human errors, simplified compliance, and improved IT/HR productivity.
- CloudEagle.ai empowers enterprises with automated lifecycle management, enhanced security, and operational efficiency.
What Is User Lifecycle Management?
User lifecycle management (ULM) is the strategic approach to controlling a user’s access to an organization’s systems and data throughout their entire tenure. It covers onboarding (creating accounts and granting initial access), modifications (updating roles and permissions), and offboarding (revoking access and deactivating accounts).
Automating the user lifecycle management process boosts security, improves productivity, ensures regulatory compliance, and reduces costs tied to manual identity and access management.
Key aspects of ULM include:
- User onboarding: Creating a new user account and provisioning access.
- Role changes: Adjusting permissions when employees shift positions.
- User offboarding: Ensuring deprovisioning to reduce security risks.
- Auditing and compliance: Maintaining visibility to satisfy regulatory compliance.
Over half of companies (58%) have more than 1,000 inactive user accounts, highlighting the need for effective user lifecycle management.
Modern organizations can’t rely on manual processes alone. With dozens of SaaS apps like Microsoft 365, Slack, or Google Workspace in play, the complexity multiplies. Without a structured user account lifecycle management framework, inactive accounts pile up, creating a risk of errors and opportunities for malicious actors to exploit sensitive data.
What Are the Common Bottlenecks in User Lifecycle Management?
Even with user lifecycle management software, bottlenecks appear when organizations rely too heavily on manual processes. These challenges slow down IT departments, frustrate new employees, and increase exposure to security risks.
Manual Onboarding Delays
When onboarding relies on spreadsheets, emails, and manual setups, new hires often wait days before receiving their IT resources. This poor user experience reduces productivity and can delay integration into the workforce.
Nearly 39% of large businesses face heightened cybersecurity risks because it can take up to a month to close dormant accounts, emphasizing the critical need for streamlined user lifecycle management
Worse, human errors during onboarding, like typos in Active Directory or missed provision user tasks, lead to inconsistent digital identities. These mistakes are costly, both in time and risk exposure.
Typical problems include:
- Delays in creating new user accounts.
- Missed access provisioning across apps like Microsoft 365 and Slack.
- Inconsistent enforcement of best practices.
- IT staff are overwhelmed with repetitive onboarding work.
Inefficient Role and Access Assignments
Assigning the right access is often harder than it seems. Employees with role changes need timely modification of their permissions, but manual processes usually lag behind.
The result is either over-provisioned users with excessive user rights or under-provisioned employees unable to access essential tools. Both scenarios harm the organization’s efficiency while creating risks of unauthorized access.
Key issues include:
- Inconsistent role-based access control (RBAC).
- Excessive or outdated permissions.
- Delays in resource allocation.
- Growing workload on IT departments.
Errors in User Updates and Modifications
Whenever an employee gets promoted, changes departments, or joins a temporary project, their access requires modification. Handling these updates manually creates human errors that leave inactive accounts or excessive access privileges.
Without proper integration across systems like Active Directory, HR databases, and SSO, updates are not synchronized, which weakens auditing efforts.
Problems with manual updates include:
- Forgotten or incomplete modification of user rights.
- Multiple unsynced user identities across apps.
- Risk of leaving sensitive data exposed.
- Time-consuming for IT staff, increasing the risk of errors.
Lack of Visibility in Offboarding Processes
The greatest danger comes from poor user offboarding. Former employees often retain access due to missed deprovisioning steps, creating inactive user accounts that attackers can exploit.
This doesn’t just raise security risks; it also complicates auditing and regulatory compliance requirements. Automated offboarding processes are the only way to ensure effective user lifecycle management at scale.
Risks caused by poor offboarding include:
- Inactive accounts are becoming backdoors for attackers.
- Loss of visibility into user access lifecycle management.
- Compliance violations and audit failures.
- Reputational and financial damage from unauthorized activities.
What Risks Do Poorly Managed User Lifecycles Create?
Poorly managed user lifecycles lead to security breaches from orphaned accounts, compliance violations from unmanaged access, and operational inefficiencies due to manual processes. They also cause financial losses from unused licenses and reputational damage from data exposure.
A study by Beyond Identity found that 83% of former employees still had access to company systems after termination, posing significant security risks.
Security Gaps and Unauthorized Access
When user account lifecycle management fails, employees often retain outdated or excessive permissions. This creates clear paths for unauthorized access and compromises sensitive data. In fact, IBM’s 2024 Data Breach Report shows that stolen or misused credentials remain the #1 attack vector.
Key security risks include:
- Orphaned or inactive accounts with valid credentials.
- Over-permissioned user identities outside of policy.
- Failure to enforce strong password policies and access limits.
Compliance Violations and Audit Failures
Industries bound by GDPR, HIPAA, or SOX can’t afford sloppy access management. Missing logs, incomplete deprovisioning, and inconsistent user rights quickly escalate into audit red flags. Automated auditing is not optional; it’s a best practice.
Compliance issues include:
- Gaps in regulatory compliance documentation.
- Failed audits due to incomplete management process tracking.
- Legal and financial penalties for violations.
Operational Inefficiencies Across Teams
When IT departments spend hours handling manual processes for onboarding, modifications, and user offboarding, they lack time for strategic initiatives. This frustrates both new employees and managers waiting for resource allocation.
Inefficiency risks include:
- Reduced the organization’s efficiency.
- Burnt-out IT staff handling repetitive work.
- Delays in providing access to new users.
How Does Automation Transform User Lifecycle Management?
Automation transforms user lifecycle management by accelerating and streamlining processes like onboarding and offboarding, minimizing manual errors, and enforcing consistent security policies. It frees IT staff for strategic tasks, ensuring compliance, and scales efficiently for large organizations, while improving the user experience with faster access to resources and tools.
"Automating identity lifecycle management is no longer optional; it's a necessity to ensure security, compliance, and operational efficiency."
— Gartner, 2025
Streamlining User Provisioning and Deprovisioning
Automation connects directly with the HR database and Active Directory to automatically provision users and remove inactive accounts at departure. This eliminates delays, cuts down manual errors, and ensures stronger security.
- Instant setup of new user accounts for new employees
- Automatic deprovisioning to prevent risks of unauthorized access
- Policy-based assignment of user rights for consistent access management
Automating Access Requests and Approvals
Instead of waiting for tickets, automation routes access requests through pre-set workflows. Managers approve or deny with one click, ensuring compliance and efficiency.
- Faster turnaround for permissions and resource allocation
- Clear auditing trail for regulatory compliance
- Reduced risk of errors from manual approval chains
Ensuring Real-Time Updates Across Systems
User account lifecycle management often fails when modifications or role changes don’t sync across platforms. Automation keeps everything in sync.
- Real-time updates across HR, IT, and IAM systems
- Reduced manual errors and duplication of digital identities
- Consistency in resource allocation and user rights
Enforcing Role-Based and Policy-Driven Controls
Without automation, IT departments struggle to enforce consistent policies. Automated user lifecycle management software applies strong password policies, access rules, and compliance checks by default.
- Enforces role-based access control (RBAC) automatically
- Minimizes risks of unauthorized access to sensitive data
- Ensures compliance without constant IT staff intervention
What Are the Key Benefits of Automated User Lifecycle Management?
The main benefits of automated user lifecycle management include stronger security, higher operational efficiency, simplified compliance, lower costs, and an improved user experience. Automated provisioning, updates, and deprovisioning ensure consistent policy enforcement, reduce human errors, accelerate access for new hires, and maintain a robust security posture.
Here are the core advantages of automated user account lifecycle management:
Faster and More Secure Onboarding
Manual onboarding slows down new employees and creates delays in productivity. Automation ensures new hires receive the right access immediately.
- Zero-day provisioning of new user accounts across all tools
- Seamless integration with the HR database and Active Directory
- Enforced strong password policies for stronger security
Implementing automated identity lifecycle management can reduce onboarding time by up to 50%, enhancing operational efficiency.
Reduced Human Errors and Misconfigurations
Manual errors in granting permissions or handling role changes can create serious gaps. Automation removes the risk of errors by standardizing every step.
- Consistent user rights assignment across all IT resources
- Automatic updates when employees undergo modifications or transfers
- Lower chance of misconfigured accounts leading to security risks
Simplified Compliance and Reporting
Regulations demand accurate auditing and proper user access lifecycle management. Automation provides built-in compliance checks and reports.
- Automatic auditing of user identities and access changes
- Easy reporting for regulatory compliance needs
- Reduced risk of compliance violations and failed audits
Improved Productivity for IT and HR Teams
Without automation, the IT team spends hours managing manual processes. Automation allows them to focus on strategic initiatives instead of repetitive tasks.
- Fewer low-value tickets for IT departments
- Streamlined workflows between IT and HR systems
- Improved the organization’s efficiency and employee satisfaction
How CloudEagle.ai Helps Enterprises Automate User Lifecycle Management
CloudEagle.ai streamlines user lifecycle management by automating critical processes like onboarding, offboarding, and access reviews. With its powerful user lifecycle management software, IT and security teams can ensure that employees have the right access at the right time, improving both compliance and operational efficiency.
This automation of the user lifecycle management and provisioning process helps enterprises save time and resources while reducing the risks associated with manual management.
Here's how CloudEagle.ai helps enterprises:
Automated Onboarding & Offboarding
CloudEagle.ai streamlines Onboarding & Offboarding by automatically provisioning new employees with the right access based on their role and revoking it immediately when they leave, eliminating security risks from outdated permissions.
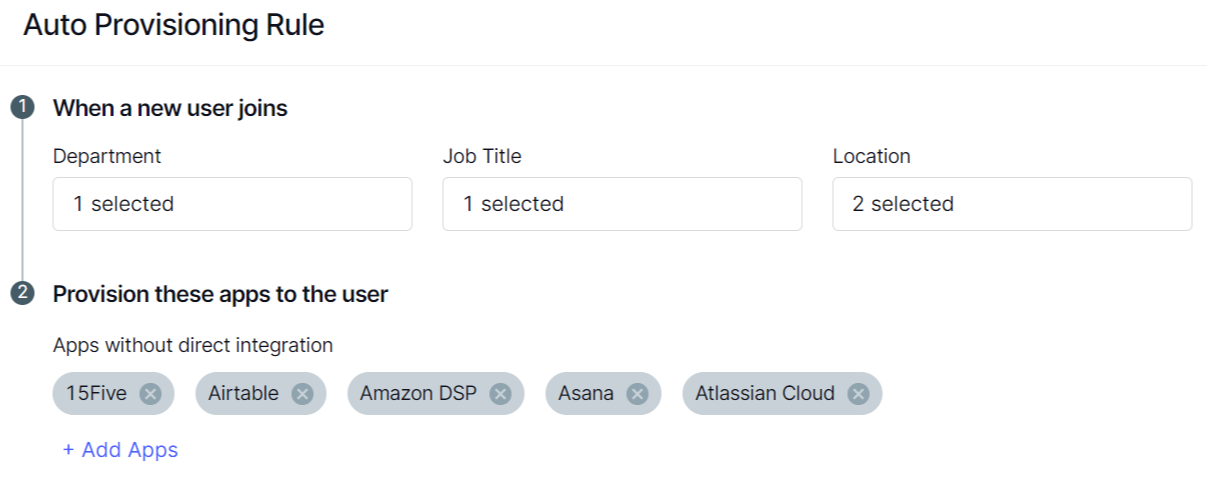
This automation speeds up processes, reducing IT workload and ensuring that all access is up to date.
You can see a real-world example of this in action in our JoVe case study on streamlined employee onboarding and offboarding, where CloudEagle.ai helped the IT team automate provisioning, deprovisioning, and maintain role-based access control efficiently.
Streamlined Access Reviews
The platform automates access reviews, ensuring employees have the right permissions. CloudEagle.ai tracks user access continuously and flags any necessary changes.
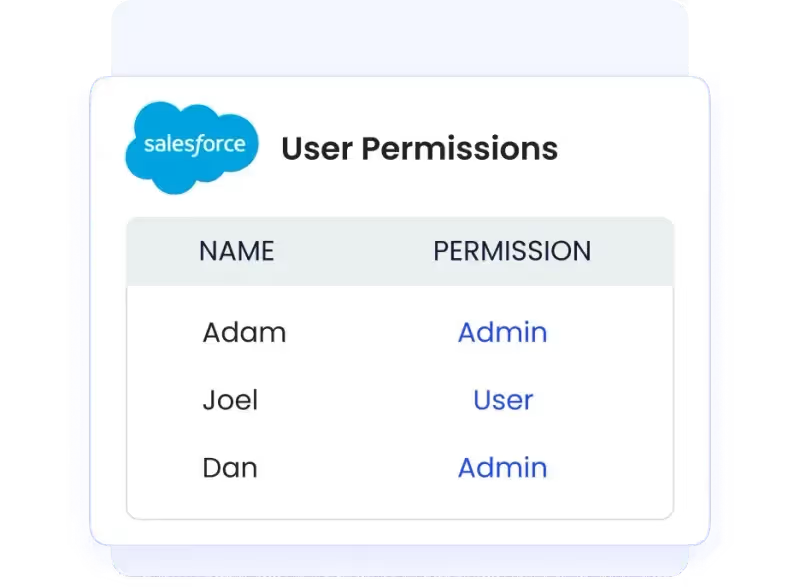
This simplifies compliance and minimizes security risks by ensuring that only authorized users have access to specific tools.
Optimized License Management
CloudEagle.ai tracks license usage and reclaims underutilized licenses. This ensures that organizations are not wasting resources on unused software.
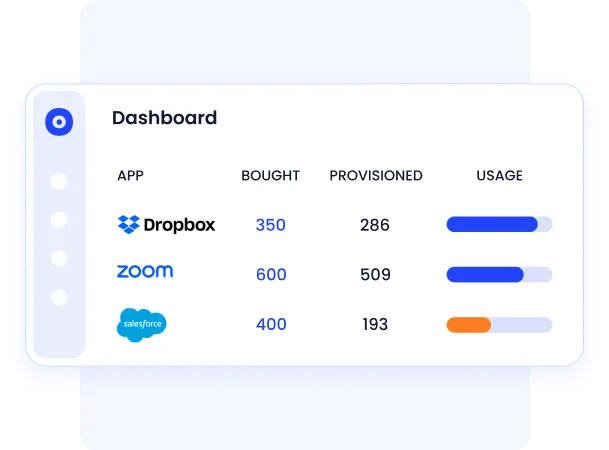
By optimizing license management, businesses can reduce unnecessary software costs and allocate resources more efficiently.
Enhanced Compliance Assurance
With user lifecycle management and provisioning, CloudEagle.ai keeps audit-ready logs of access changes. This makes compliance simpler and reduces the risk of non-compliance.
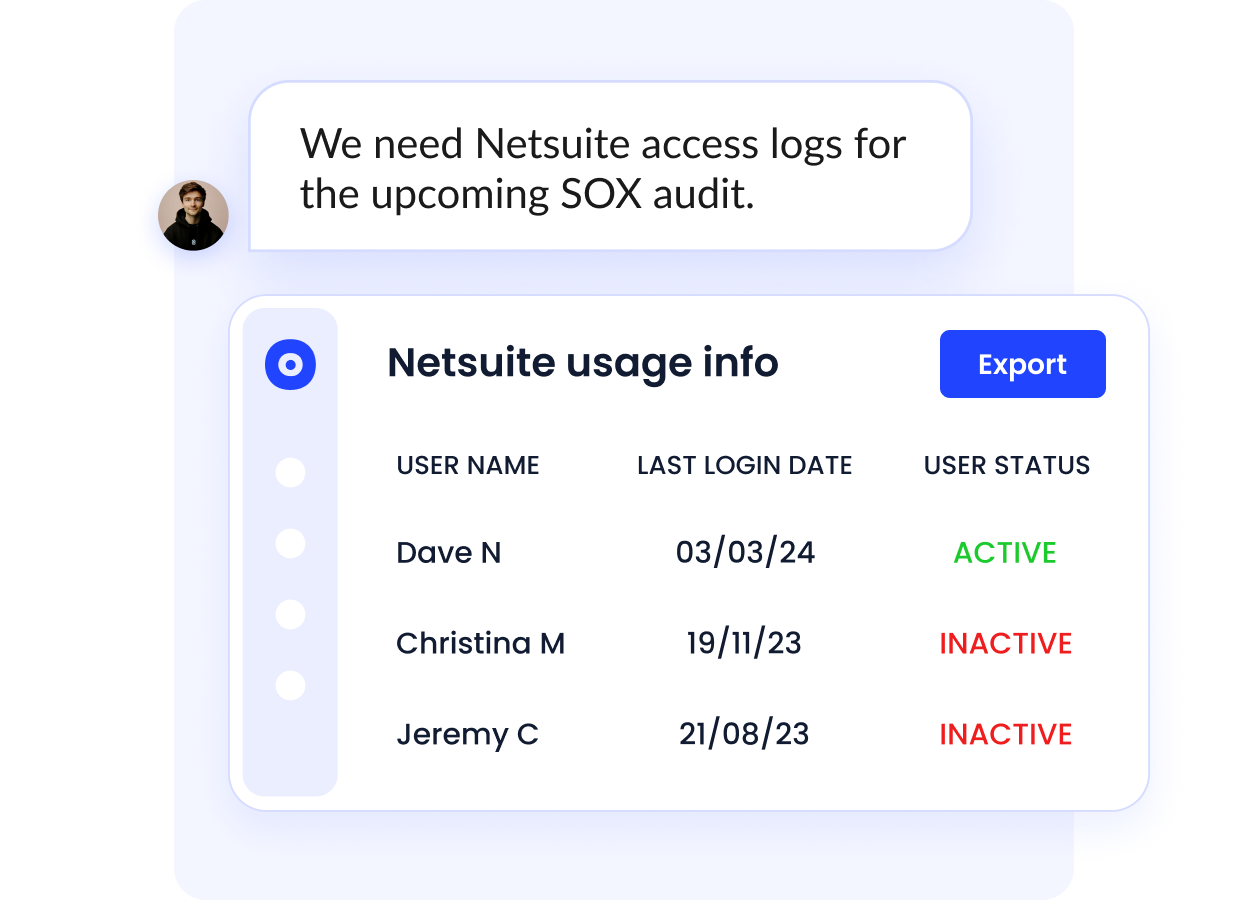
Automating these processes ensures that businesses can easily demonstrate that their access control policies are followed.
Shadow IT Discovery & Management
CloudEagle.ai helps identify and manage unapproved apps used by employees. This reduces the risks of security breaches and ensures that only approved tools are in use.
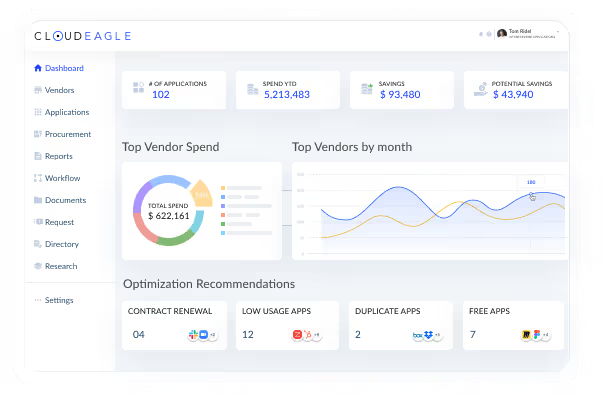
The platform provides visibility into Shadow IT, helping organizations maintain control and reduce unnecessary tech stack costs.
Final Words
Managing the user lifecycle management process manually creates bottlenecks, delays, and unnecessary security risks. From onboarding to offboarding, organizations often face human errors, compliance challenges, and inefficiencies that drain IT resources.
Automation addresses these challenges by transforming user access lifecycle management into a seamless, policy-driven framework. With automated provisioning, real-time updates, and streamlined access management, businesses can improve compliance, protect sensitive data, and boost overall efficiency.
This is where CloudEagle.ai makes a difference. Automating onboarding, deprovisioning, license management, and access reviews, it empowers IT and security teams to focus on strategic work while reducing risks and costs.
Book a free demo with CloudEagle.ai today and see how easy it is to eliminate lifecycle bottlenecks with automation.
Frequently Asked Questions
- What is life cycle management in IAM?
It’s the process of managing user identities from onboarding to offboarding, automating provisioning, access control, and deprovisioning to enhance security and compliance. - What is the user lifecycle model?
The user lifecycle model outlines stages of a user’s journey in an organization: onboarding, role changes, access reviews, and offboarding, ensuring proper access throughout employment. - What is the SDLC life cycle management?
SDLC lifecycle management is the structured process of planning, developing, testing, deploying, and maintaining software to ensure quality, security, and efficiency in delivery. - What are the 5 stages of data lifecycle management?
The five stages are: data creation, storage, usage, sharing, and deletion. Each stage ensures data is managed securely and efficiently while meeting compliance requirements. - What are the 5 phases of the SDLC life cycle?
The five SDLC phases are: planning, analysis, design, implementation, and maintenance. Together, they guide software development from idea to ongoing support.

%201.svg)










.avif)




.avif)
.avif)




.png)









