HIPAA Compliance Checklist for 2025

Businesses that handle sensitive customer data must adhere to strict security standards. One such framework is SOC 2 Type 2 compliance, which helps ensure companies are effectively protecting this data. This is especially important for industries like SaaS, healthcare, and finance.
Getting SOC 2 Type 2 compliant means meeting requirements for security, privacy, and data protection. The process involves setting up strong security, monitoring it, and demonstrating its effectiveness during an audit. It might seem complex, but it’s necessary to build trust with your customers and protect their data.
Let’s look at the steps to achieve SOC 2 Type 2 compliance and the best practices to maintain it.
TL;DR
- SOC 2 Type 2 ensures your security measures protect customer data effectively over 6-12 months, covering security, privacy, availability, and confidentiality.
- Achieving SOC 2 Type 2 compliance builds customer trust, strengthens security, reduces breach risks, and enhances vendor relationships.
- The five key criteria, security, availability, processing integrity, confidentiality, and privacy, evaluate how well systems protect sensitive data.
- Key requirements include security policies, access management, incident response plans, and employee training to handle sensitive data properly.
- Start with a readiness assessment, automate evidence collection, assign roles, train employees, and continuously monitor systems for year-round compliance.
What Is SOC 2 Type 2 Compliance?
SOC 2 Type 2 compliance is a security standard for companies that handle sensitive data, particularly in technology, healthcare, and finance. According to reports, SOC 2 Type 2 requires a comprehensive operational assessment over 6–12 months.
Cybersecurity Expert Mary K. Pratt says:
"Organizations that want to prove to others – and to themselves – that they have a solid cybersecurity and data privacy program will undergo a SOC 2 audit. As such, a SOC 2 audit is a big deal, and it’s demanding, and it requires some serious preparation."
SOC 2 was developed by the American Institute of Certified Public Accountants (AICPA) and is based on five key Trust Service Criteria:
- Security: Protects systems and data from unauthorized access or attacks.
- Availability: Ensures services are accessible and available as promised, with minimal downtime.
- Processing Integrity: Verifies that systems perform tasks accurately and promptly.
- Confidentiality: Safeguards sensitive data from unauthorized access or disclosure.
- Privacy: Ensures personal information is handled according to privacy regulations and agreements.
SOC 2 Type 2 is different from SOC 2 Type 1 because it doesn’t just check if a company has security measures in place, but also looks at how well they work over time. Achieving it shows that a company consistently protects customer data, building trust with customers.
Why SOC 2 Type 2 Compliance Matters?
SOC 2 Type 2 compliance is crucial for ensuring ongoing data security, building customer trust, and meeting industry standards for companies handling sensitive information.
1. Builds Trust With Customers And Stakeholders
Achieving SOC 2 Type 2 compliance demonstrates to customers, partners, and stakeholders that you take data security seriously. It ensures that their sensitive information is handled with the utmost care, fostering trust and long-term relationships.
2. Strengthens Internal Processes For Data Handling And Security
SOC 2 Type 2 forces companies to implement strong, ongoing security controls and monitor them continuously. This not only protects your data but also improves your internal processes, making your systems and operations more secure and efficient.
3. Reduces Risk Of Breaches, Downtime, And Compliance Penalties
By staying compliant with SOC 2 Type 2, you minimize the risk of data breaches, system downtime, and costly penalties for non-compliance. The ongoing monitoring and risk management help you stay ahead of potential threats and legal issues.
4. Enhances Competitiveness In Vendor Security Assessments
Larger enterprises require vendors to meet specific security standards before forming partnerships. SOC 2 Type 2 compliance gives your company a competitive edge and makes you a more attractive partner when bidding for contracts or collaborations.
5. Increases Operational Efficiency
The process of achieving SOC 2 Type 2 compliance helps organizations improve their internal operations by streamlining security practices. With automation tools, your team can handle compliance tasks more efficiently, freeing up time to focus on other critical business areas.
6. Supports Regulatory and Legal Requirements
SOC 2 Type 2 compliance helps businesses stay aligned with industry regulations and legal requirements, ensuring they meet the necessary standards for handling sensitive data. This reduces the risk of fines and legal challenges while demonstrating your commitment to ethical business practices.
7. Facilitates Easier Audits and Reviews
Once you're SOC 2 Type 2 compliant, the automated tools and reports make it much easier to undergo future audits. The process becomes more efficient, saving you time and reducing the stress of preparing for external audits.
SOC 2 Type 2 Trust Service Criteria
The SOC 2 Type 2 framework is built around five key Trust Service Criteria (TSC), which assess how a company manages and protects sensitive data. Each of these criteria focuses on a specific area of security and operational integrity.
Let's take a closer look at each one:
1. Security
The Security criterion ensures systems are protected from unauthorized access, both physical and digital. It focuses on preventing data breaches and cyberattacks by using firewalls, intrusion detection, access management, and encryption to safeguard data and systems.
2. Availability
The Availability criterion ensures that systems are operational and accessible as agreed upon. It focuses on minimizing downtime, enhancing system resilience, and implementing disaster recovery plans to guarantee reliability and uptime.
3. Processing Integrity
Processing Integrity ensures that systems perform tasks accurately and promptly. It guarantees that data is processed correctly, without errors or delays, and that any issues are swiftly identified and resolved to maintain system accuracy and functionality
4. Confidentiality
The Confidentiality criterion ensures sensitive information, like trade secrets or personal data, is protected from unauthorized access. It uses encryption, access controls, and data classification to safeguard this data at all stages.
5. Privacy
The Privacy criterion ensures that personal information is handled in accordance with privacy laws and agreements, such as GDPR, CCPA, or HIPAA. It focuses on protecting customer data, obtaining proper consent, managing data retention, and granting access rights only for authorized purposes.
SOC 2 Type 2 Compliance Requirements
To achieve SOC 2 Type 2 compliance, businesses must put in place key practices and policies that ensure the security and privacy of sensitive data. Here are the main requirements:
1. Documented Security Policies And Internal Controls.
You need to have clear and written security policies that explain how your company keeps data safe. These policies should cover things like who has access to what data, how data is protected, and how security risks are managed. These documents should be updated regularly to keep up with any changes in your business or the security landscape.
2. Access Management And Monitoring Systems.
SOC 2 Type 2 requires strong controls over who can access your sensitive data. This includes setting up systems to manage who gets access to what information and monitoring those who have access. Multi-factor authentication (MFA) and regular audits are part of this process to ensure only the right people can access critical systems.
3. Incident Response Plans And Regular Audits.
Having an incident response plan is crucial in case of a data breach or security issue. This plan outlines how to identify, respond to, and resolve security incidents quickly. In addition, conducting regular audits ensures that your security practices are always working as they should, helping you spot any potential weaknesses.
4. Vendor Risk Management And Employee Training
If your business works with third-party vendors, it's important to make sure they follow the same security standards as your company. This means checking their security practices and ensuring your agreements cover data protection. Also, employee training is key to keeping your team aware of security risks, like recognizing phishing emails and safely handling data.
The SOC 2 Type 2 Audit Process
This process evaluates the effectiveness of a company’s security controls over time.
Bernard Gallagher, Principal, I.S. Partners, LLC, believes:
"The most important requirement of SOC 2 is that businesses need to develop security policies and procedures that are written out and followed by everyone [within their organization]. These policies and procedures serve as guides for auditors who will review them."
Here’s a simple breakdown of the steps:
Step 1: Readiness Assessment
Before the audit starts, your company should do a readiness assessment. According to reports, organizations that conduct SOC 2 readiness assessments see a 30% improvement in audit success rates. This assessment is a check to make sure you’re ready for the audit. It helps you find any areas where your security controls might need improvement.
Step 2: Control Implementation
Once you’ve completed the readiness assessment, the next step is to put in place the necessary security controls. These could be things like managing access to data, protecting sensitive information, and setting up incident response plans. The goal is to meet the five key areas of SOC 2 Type 2: security, availability, processing integrity, confidentiality, and privacy.
Step 3: Audit Observation Period
The audit observation period usually lasts 6 to 12 months. During this time, auditors monitor how well your security controls are working. This is important because SOC 2 Type 2 checks if your security measures work consistently over time, not just at one point.
Step 4: Independent Audit
At the end of the observation period, an independent auditor will review your company’s security controls. They will check the evidence, test your controls, and see if they meet the SOC 2 Type 2 standards over the entire period.
Step 5: Report Issuance
After the audit, the auditors will issue a SOC 2 Type 2 report. This report shows how your company’s security controls were tested and whether they meet the required standards. It may also include suggestions for improvement. The report is key to proving your company is committed to protecting data and building trust with your customers.
Best Practices for Achieving SOC 2 Type 2 Compliance
Achieving SOC 2 Type 2 compliance is a continuous process that requires strong planning, execution, and monitoring. 72% of companies that achieved SOC 2 Type 2 compliance reported improved data security practices, and 68% noted increased customer trust and satisfaction.
Here are some best practices to help ensure your organization is fully compliant:
1. Start With A SOC 2 Readiness Assessment
Assess your current compliance status to identify gaps in security measures. This helps you address weaknesses before the official audit. A readiness assessment saves time and ensures you’re well-prepared.
2. Automate Evidence Collection And Compliance Tracking
Use automation to streamline evidence collection and track compliance. This ensures real-time data and simplifies generating audit-ready reports. Automation reduces manual work and keeps your organization continuously compliant.
3. Establish Clear Roles For Control Ownership
Assign specific roles for security controls like access management and data protection. Clear ownership ensures responsibilities are met and no critical control is overlooked. This makes compliance management more efficient.
4. Conduct Regular Employee Security Training
Provide regular training on security policies and best practices. Educating employees on recognizing threats and proper data handling reduces human error. This boosts overall security and supports compliance efforts.
5. Maintain Continuous Monitoring and Real-Time Alerts
Implement continuous system monitoring and real-time alerts for suspicious activity. Quick action can prevent security breaches before they escalate. This ongoing vigilance helps maintain SOC 2 Type 2 compliance.
6. Perform Regular Internal Audits
Schedule regular internal audits to verify your security controls are functioning. Audits help catch gaps early and improve security practices. They also prepare your organization for the official SOC 2 Type 2 audit.
7. Document Everything
Keep detailed documentation of security policies, controls, and procedures. Well-documented processes are crucial for audits and future compliance checks. It ensures transparency and makes compliance more manageable.
8. Keep Up with Regulatory Changes
Regulations and security standards evolve, so regularly review and update your security practices. Staying informed ensures that your compliance efforts remain relevant. Adapting to changes keeps your organization secure and compliant.
How CloudEagle.ai Helps Enterprises Stay Compliant?
CloudEagle.ai simplifies and automates compliance management, helping enterprises stay secure, meet regulatory standards, and reduce manual effort across security and audit processes.
Here’s how it helps:
1. Automated Compliance Monitoring
CloudEagle.ai continuously tracks your organization’s security posture and ensures compliance with SOC 2 Type 2, ISO 27001, GDPR, and other industry standards. The platform monitors security measures in real time, making it easier to stay compliant without manual oversight.
How it helps:
- Provides continuous oversight with minimal manual work.
- Flags compliance issues instantly for quick resolution.
- Reduces errors by automating monitoring.
- Saves time by tracking security automatically.
- Keeps data up-to-date for audits.
2. Zero-Touch Onboarding
CloudEagle.ai automates the onboarding process for new employees, ensuring they get access to the right applications and tools from day one. This automatic provisioning of access helps eliminate delays and prevent the risk of improper access levels.

How it helps:
- Provides immediate access to necessary tools.
- Automates user setup, reducing delays.
- Reduces human error in access provisioning.
- Improves onboarding speed and efficiency.
- Enhances security with controlled access.
3. Zero-Touch Offboarding
CloudEagle.ai ensures that user accounts are deactivated automatically when employees leave, closing any potential security gaps and preventing unauthorized access. This fully automated offboarding process ensures that no lingering accounts can be exploited after departure.
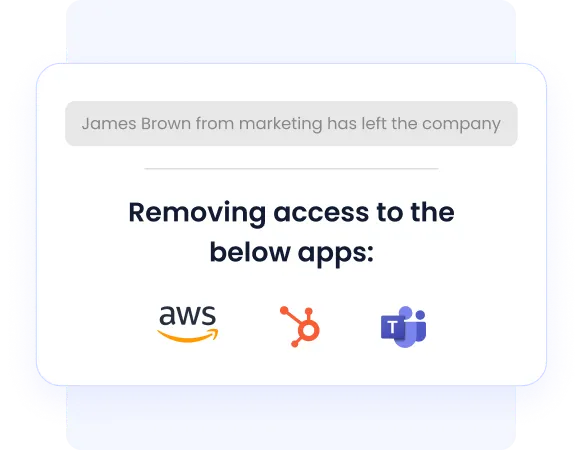
How it helps:
- Eliminates security risks after offboarding.
- Saves time by automating account deactivation.
- Reduces errors with timely access removal.
- Prevents unauthorized access post-departure.
- Streamlines offboarding without manual intervention.
Know how Treasure Data streamlined employee offboarding using CloudEagle.ai.
4. Real-Time Compliance Reporting
CloudEagle.ai generates real-time compliance reports that are automatically updated to reflect your current security posture. This feature simplifies compliance reporting, saving time during audits by ensuring that all data is up to date and readily available.
How it helps:
- Saves time on preparing reports.
- Ensures reports are always up to date.
- Reduces the workload during audits.
- Provides easy access to compliance data.
- Automates report generation for real-time accuracy.
5. Centralized Compliance Dashboard
Reports show that continuous monitoring reduces security incident detection time by 50%.
CloudEagle.ai offers a unified dashboard to manage security measures, applications, and user access all in one place. This centralized view provides full visibility into your compliance status, making it easy to monitor and manage your systems.
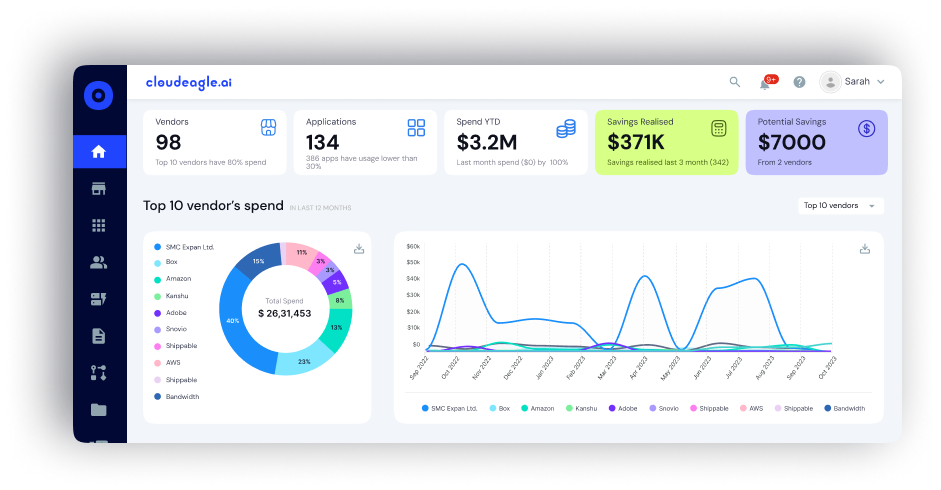
How it helps:
- Centralizes all compliance data.
- Simplifies monitoring across apps.
- Provides a clear overview of access and security.
- Increases efficiency in compliance tracking.
- Helps make quick decisions with real-time updates.
6. Automated Access Reviews
CloudEagle.ai automates access reviews for applications, ensuring that user access rights are regularly checked and updated. The platform simplifies the process of reviewing access permissions, saving time and ensuring compliance with security standards such as SOC 2 Type 2 and ISO 27001.

How it helps:
- Automatically schedules and manages regular access reviews.
- Provides a clear overview of user access permissions.
- Ensures only authorized personnel have access to sensitive data.
- Reduces the risk of over-provisioned or outdated access rights.
- Streamlines compliance with audit-ready reports on user access.
Discover how Dezerv automated its app access review process with CloudEagle.ai.
7. Integrated Risk Management
CloudEagle.ai automatically tracks third-party vendor risks, evaluates their security measures, and ensures they comply with your security standards. The platform provides continuous oversight to reduce risks from third-party services that access your sensitive data.
How it helps:
- Monitors third-party security continuously.
- Ensures vendors meet your security requirements.
- Reduces external security risks.
- Provides real-time vendor security oversight.
- Automates vendor risk assessments.
8. Scalable with Your Business
CloudEagle.ai is designed to scale with your organization’s growth, making it easy to accommodate new applications, additional users, and expanding security controls. Whether you’re adding more teams or integrating new services, the platform adapts to your changing needs without compromising compliance.
How it helps:
- Grows with your business, ensuring ongoing compliance.
- Adapts to new tools and users seamlessly.
- Allows for easy integration as your business scales.
- Provides flexibility for changing compliance needs.
- Keeps compliance processes efficient as your business expands.
Don’t miss this insightful conversation with Karl Haviland, where he dives into SaaS governance, AI, and cloud-first strategies to scale tech innovations effectively.
Conclusion
SOC 2 Type 2 compliance is important for businesses handling sensitive customer data, especially in industries like SaaS, finance, and healthcare. According to LinkedIn Pulse, 66% of B2B customers consider SOC 2 compliance a contract requirement in 2025.
By conducting a readiness assessment, automating tasks, assigning roles, and training employees, your business can easily meet SOC 2 Type 2 requirements. This compliance strengthens security, builds customer trust, reduces breach risks, and gives you a competitive edge, ensuring your business is always audit-ready and secure.
To streamline this process and ensure continuous compliance, consider using platforms like CloudEagle.ai. With features like task automation and real-time monitoring, CloudEagle.ai helps businesses stay audit-ready at all times.
Schedule a demo with CloudEagle.ai to enhance your SOC 2 Type 2 compliance efforts.
FAQs
1. What is the difference between SOC 2 Type 1 and Type 2?
SOC 2 Type 1 evaluates the design of security controls at a specific point in time, while SOC 2 Type 2 assesses the effectiveness of these controls over a period (usually 6-12 months).
2. What is the difference between ISO 27001 and SOC 2 Type 2?
ISO 27001 is a broader, international standard for information security management systems (ISMS), whereas SOC 2 Type 2 focuses specifically on service organizations' security, availability, confidentiality, processing integrity, and privacy.
3. How to get a SOC 2 type 2 report?
To get a SOC 2 Type 2 report, you need to undergo an audit by an independent CPA or audit firm, which will assess your company’s security controls over a defined period and then issue the report if you meet the standards.
4. Who needs SOC 2 type 2 compliance?
SOC 2 Type 2 compliance is typically required for companies that provide services involving sensitive customer data, such as SaaS providers, financial institutions, healthcare organizations, and any company handling or processing personal or confidential information.
5. Who issues SOC 2 type 2?
SOC 2 Type 2 reports are issued by independent Certified Public Accountants (CPAs) or audit firms after they assess your company’s security controls and practices over a specific period.

%201.svg)








.avif)




.avif)
.avif)




.png)









