HIPAA Compliance Checklist for 2025

Enterprises today rely heavily on a growing number of SaaS apps to run their business efficiently. Managing identities and access across these platforms is a complex challenge that, if left unmanaged, exposes enterprises to security risks and compliance issues.
Without a clear identity and access management strategy, IT teams face overwhelming manual processes, and users experience access delays and frustration. A well-planned IAM implementation not only secures user access but also streamlines workflows, reduces risk, and ensures compliance with industry regulations.
To build a strong IAM system, enterprises need a clear plan that includes assessing current systems, designing solutions, automating tasks, and ongoing management. This step-by-step plan helps improve security, user experience, and operational efficiency.
Let’s explore the 8-step plan every enterprise should follow to implement IAM effectively.
TL;DR
- Enterprises rely on many digital systems and cloud apps, making identity and access management (IAM) critical to reduce security risks and improve compliance.
- IAM implementation involves creating a clear plan to manage digital identities, enforce strong access controls, and automate provisioning across systems.
- The 8-step implementation plan starts with defining goals, assessing current systems, selecting tools, establishing authentication policies, and role-based access controls.
- Effective IAM improves security with centralized access control, reduces costs by automating manual tasks, and enhances user experience with single sign-on (SSO).
- Continuous monitoring, audits, and user training ensure that the IAM system stays secure, compliant, and adapts to the enterprise’s evolving needs.
What is IAM Implementation?
Identity and Access Management (IAM) implementation is the process of setting up systems and policies that control who can access what in an organization’s digital environment. It helps ensure that the right people have the right access to the right resources.
IAM implementation involves creating digital identities for users and managing their permissions across applications and systems. It includes verifying users’ identities when they log in, deciding what they are allowed to do, and regularly reviewing access to keep everything secure.
A good IAM implementation makes it easier for employees to get the access they need while reducing the risk of unauthorized users gaining entry. It also helps enterprises meet compliance rules and monitor access activities.
A typical IAM implementation includes key elements such as:
- Identity Management: Creating, storing, and maintaining digital identities along with their associated attributes and roles.
- Access Management: Controlling user authentication and authorization to ensure users have appropriate access levels to systems and data.
- Authentication: Verifying the identity of users or devices trying to access resources, often using passwords, biometrics, or multi-factor authentication (MFA).
- Authorization: Defining and enforcing what resources an authenticated user can access and what actions they can perform.
- Identity Governance: Monitoring and auditing access to prevent misuse, ensure compliance with regulatory frameworks, and maintain security.
According to CloudEagle.ai’s IGA report, Chetna Mahajan, Global CDO & CIO at Webflow, says: “IAM is often the most underfunded yet mission-critical part of security. Those taking a proactive approach with automation and AI-driven governance not only reduce risk but also unlock efficiency and deliver long-term cost savings.”
What are the Benefits of Implementing Identity and Access Management?
Implementing IAM lets enterprises control who accesses their systems and data from one central platform. The global IAM market is projected to reach $24.1 billion by 2025, growing at an annual rate of around 12.5%, driven by rising cloud adoption and stricter regulations.
Let’s take a closer look at the key benefits in detail:
Strengthening Security With Centralized Access Control
Implementing IAM gives enterprises a central way to control who can access what systems and data. By managing user access from one platform, companies reduce the chance of unauthorized users getting in.
IAM also enforces strong authentication methods like multi-factor authentication, making it harder for attackers to breach systems. Centralized control improves visibility, so suspicious activities are detected and stopped faster, strengthening overall security.
Identity-related attacks account for more than 80% of data breaches, highlighting IAM as a critical security priority.
Reducing Operational Costs Through Automation
IAM automates many manual tasks like creating user accounts, password resets, and managing access changes. This reduces the workload on IT teams, lowering administrative costs and saving time.
Automation helps speed up onboarding and offboarding of employees, ensuring access is granted or removed promptly. By reducing errors and manual work, IAM also cuts costs linked to security incidents and inefficient processes.
Improving User Experience With Seamless Access
Enjoy a smoother access experience through Single Sign-On (SSO), using one set of credentials to access multiple apps. This reduces password fatigue and makes login easier and faster. Self-service options let users manage passwords or access requests without waiting on IT. Overall, IAM improves productivity and employee satisfaction by simplifying secure access.
Ensuring Compliance With Industry Regulations
IAM helps enterprises meet regulatory requirements by enforcing consistent access policies and maintaining detailed audit trails. Companies can quickly generate reports to prove compliance during audits, reducing stress and manual effort.
Automated policy enforcement lowers risks of violations, helping avoid fines and reputational damage. IAM is essential for industries with strict data privacy and security standards.
8 IAM Implementation Steps to Follow
Implementing IAM successfully requires a clear, step-by-step plan. Here’s how you can build one:
Step 1: Define IAM Objectives and Business Goals
The first step in IAM implementation is understanding why your organization needs it and what you want to achieve. Define clear objectives aligned with your business goals—whether it’s improving cybersecurity, streamlining access management, reducing IT costs, or ensuring regulatory compliance.
Engage stakeholders across IT, security, legal, and business units early on to gather requirements and build consensus. This foundation will guide all subsequent steps and help measure success.
Step 2: Assess Current Systems and Access Gaps
Next, conduct a thorough assessment of your existing IT environment. Catalog all applications, systems, and data repositories to understand where and how digital identities are created, stored, and managed. This helps reveal the full scope of your identity landscape and ensures no critical asset is overlooked.
During this assessment, identify security gaps such as orphaned accounts, excessive access privileges, or outdated authentication methods. Consider all user groups—including employees, contractors, partners, and customers—and analyze how they currently gain access to systems.
Step 3: Choose the Right IAM Tools and Platforms
Based on your assessment and goals, select IAM technologies that fit your organization’s needs. Decide between cloud, on-premises, or hybrid IAM platforms by weighing factors like cost, scalability, security, and integration capabilities.
Look for solutions offering key features such as multi-factor authentication, Single Sign-On (SSO), automated provisioning, and detailed auditing. Vendor reputation, support, and future roadmap should also factor into your decision to ensure long-term viability.
Step 4: Establish Strong Authentication Policies
Authentication is a critical security layer. Implement policies that require robust verification of user identities before granting access. This typically includes multi-factor authentication (MFA), combining passwords with something users have (tokens, smartphones) or biometrics.
Define when and how authentication challenges occur—especially for sensitive systems or risky behaviors—to balance security with user convenience. Strong authentication significantly reduces the risk of unauthorized access.
Step 5: Implement Role-Based Access Controls (RBAC)
To simplify access management, categorize users into roles based on their job functions and assign permissions accordingly. Role-Based Access Control (RBAC) ensures users only get access necessary for their roles, minimizing excessive privileges that cause security risks.
Define clear roles and permissions, and periodically review them to adapt to changes in job responsibilities or organizational structure. RBAC helps maintain security while easing administration.
Step 6: Integrate IAM With Existing Applications
For IAM to be effective, it must work seamlessly across all your critical systems and applications. Integrate your IAM platform with on-premises software, SaaS apps, cloud services, and network devices.
Automated IAM solutions reduce user access provisioning time by over 50%, boosting both security and operational efficiency.
Use open standards like SAML, OAuth, or OpenID Connect to enable smooth authentication and authorization flows across diverse environments. This integration ensures consistent policy enforcement and improves user experience by enabling Single Sign-On (SSO).
Step 7: Conduct User Training and Awareness Programs
Even the best IAM system is only as strong as its users’ behavior. Educate employees, contractors, and partners about IAM policies, security best practices, and how to use new tools like SSO or MFA.
MFA can block up to 99.9% of automated cyberattacks targeting compromised credentials.
Promote awareness about phishing, credential security, and reporting suspicious activities. Regular training helps create a security-conscious culture and reduces risks caused by human error or negligence.
Step 8: Monitor, Audit, and Continuously Improve IAM
IAM implementation is an ongoing process. Set up continuous monitoring to track access patterns, detect anomalies, and identify potential security incidents early. Conduct regular audits and reviews to ensure users’ access rights align with policies and compliance requirements.
Collect feedback from users and admins to identify pain points. Stay updated on emerging threats and industry best practices, and regularly update IAM configurations to keep the system effective and resilient.
How CloudEagle.ai Can Streamline Identity and Access Management?
CloudEagle.ai is a powerful SaaS management and access governance platform. It gives IT and security teams complete visibility, automated workflows, and compliance-ready controls, all while reducing costs and saving valuable time.
The platform integrates with 500+ SaaS applications and works seamlessly with existing IAM, SSO, and security tools. This means enterprises can secure their SaaS environments without overhauling their current IT infrastructure.
Here’s how CloudEagle.ai simplifies identity and access management (IAM):
Complete Visibility Across SaaS and AI Applications
Most enterprises underestimate how many tools their employees use. Beyond approved apps, staff often adopt new SaaS or AI tools without IT’s knowledge; what’s known as Shadow IT. This not only drives up costs but also introduces security and compliance risks.
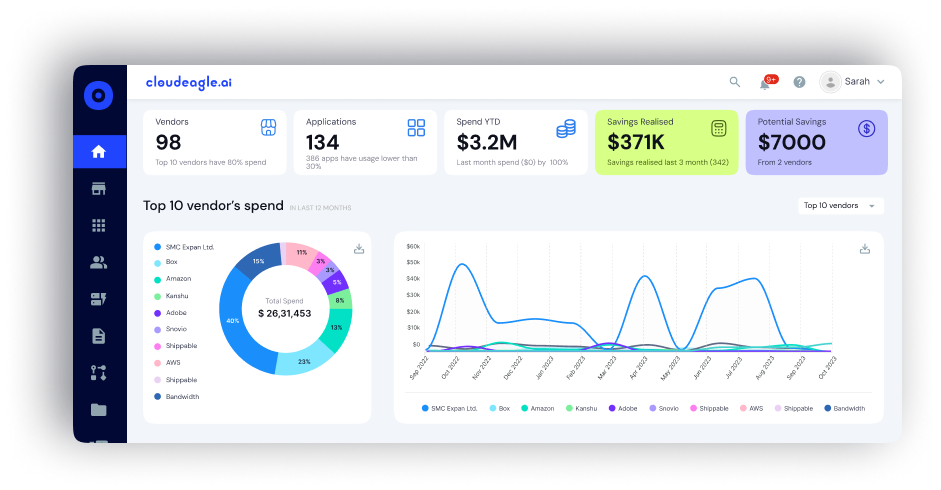
CloudEagle.ai automatically uncovers every SaaS app in use and consolidates usage, spending, and access data into one dashboard. With this insight, IT teams can eliminate blind spots, reduce redundancies, and improve governance across all applications.
Enforcing the Principle of Least Privilege
Over time, employees often collect more access than they need, sometimes even admin rights, creating dangerous security risks. CloudEagle.ai enforces least privilege access by continuously auditing permissions and adjusting them as roles change. This prevents privilege creep, reduces insider threats, and ensures regulatory compliance.
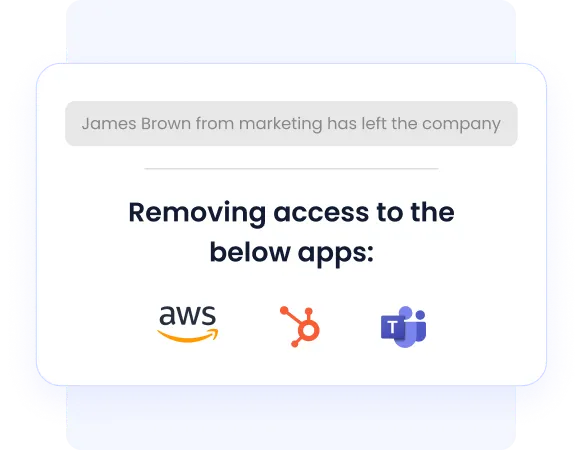
Automated Onboarding and Offboarding
Onboarding and offboarding are two of the most critical identity touchpoints, but manual processes often cause delays, mistakes, and security gaps. With CloudEagle.ai, new employees get instant access to the right apps on day one.

Likewise, by using automated deprovisioning workflows, departing employees immediately lose access to all connected applications. This automation secures the entire employee lifecycle and simplifies audit processes, making compliance hassle-free.
Know this inspiring story of how JoVe streamlined employee onboarding and offboarding with CloudEagle.ai.
Simplified Access Reviews and Compliance
Manual access reviews are slow, error-prone, and often fail compliance checks. According to reports, only 95% of organizations still conduct manual access reviews.
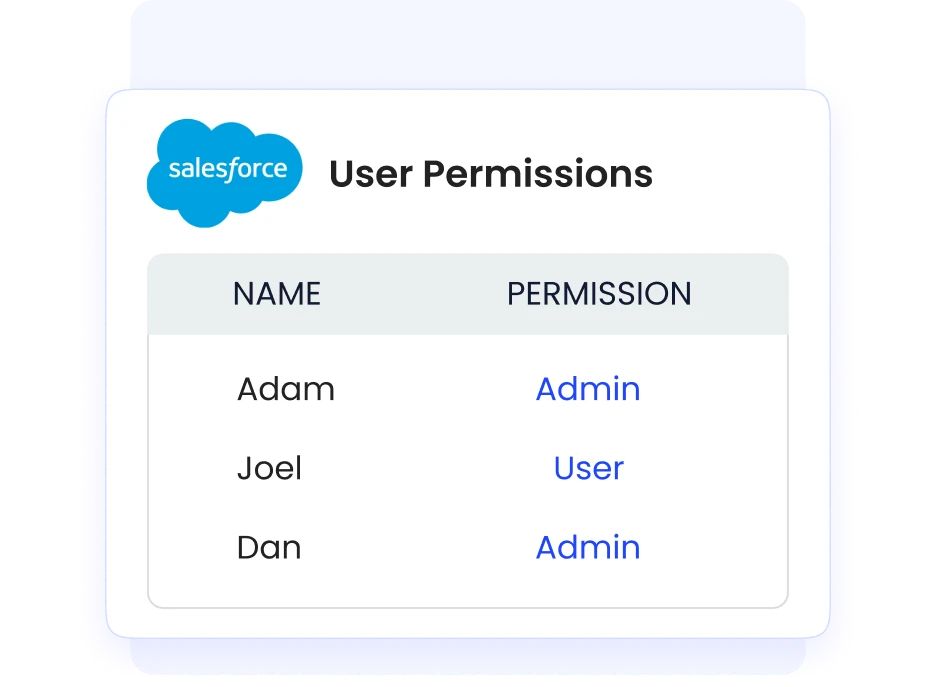
CloudEagle.ai automates access reviews using AI-driven monitoring, producing audit-ready reports instantly. This reduces preparation time and ensures outdated or excessive permissions are quickly removed.
Centralized Compliance and Governance
Managing compliance across dozens of SaaS apps is difficult when approvals are scattered in spreadsheets, emails, or ticketing systems. CloudEagle.ai centralizes policies and workflows on a single platform.

Automated governance enforces access controls consistently, while detailed logs create clear audit trails. This makes compliance easier and keeps enterprises always audit-ready.
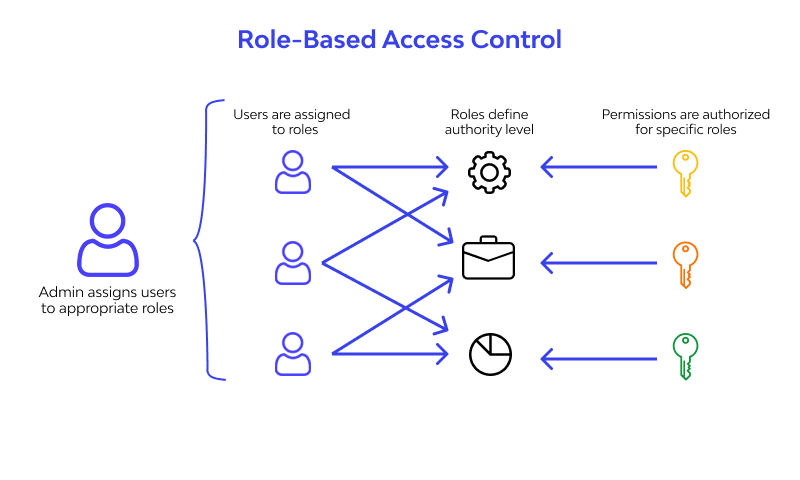
Role-Based Access Control (RBAC)
Instead of granting app access one by one, CloudEagle.ai lets enterprises assign access by role, department, or seniority. For example, sales managers automatically get Salesforce, Gong, and Zoom, while developers receive their engineering tools. RBAC reduces IT effort, eliminates errors, and speeds up provisioning.
Just-in-Time (JIT) Access
Temporary workers, contractors, and project staff shouldn’t keep long-term access. CloudEagle.ai offers JIT access, granting permissions only for the required time and automatically revoking them when no longer needed. This closes security gaps without slowing down work.
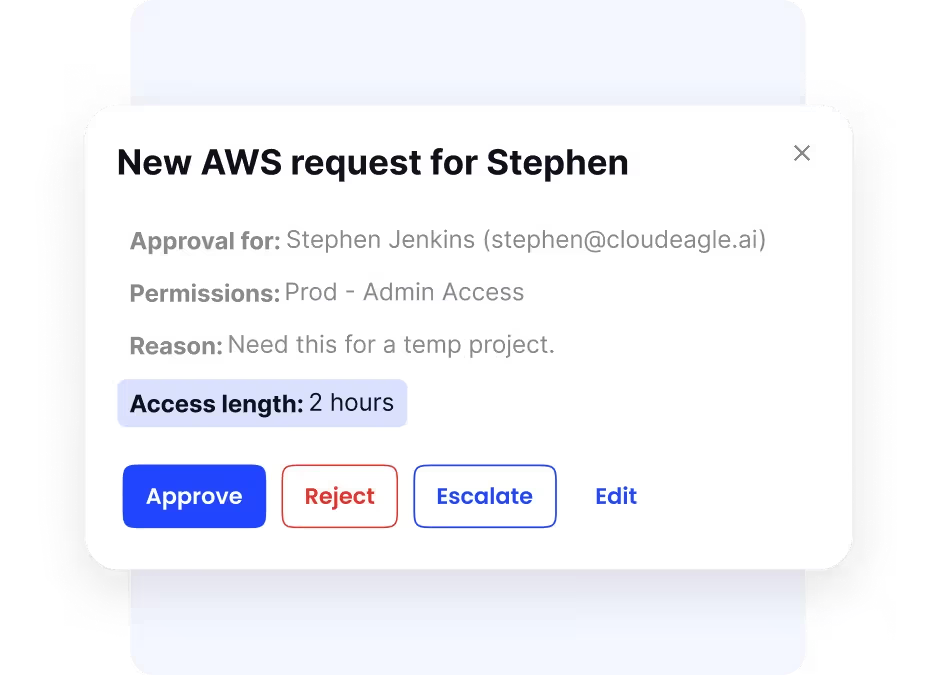
Employee Self-Service App Catalog
Employees often struggle to know what apps are available or how to request them. CloudEagle.ai solves this with a centralized self-service catalog, where users can easily request access. Approvals flow through automated workflows, giving IT full visibility while delivering faster access for employees.

Take a moment to hear from Alice Park at Remediant, who shares her experience with CloudEagle.ai. She explains how the platform made access management simpler and significantly improved their security posture.
Conclusion
Implementing Identity and Access Management (IAM) helps enterprises protect their complex digital environments. Successful IAM is an ongoing effort that requires teamwork across IT, security, and business teams using modern technology and best practices.
Enterprises focusing on identity-first security with robust IAM tools can better prevent breaches, reduce operational overhead, and foster safer, more productive work environments.
Carefully taking these steps builds a flexible, scalable, and future-ready IAM system that adapts to your enterprise’s evolving needs and helps you stay ahead of threats.
Nidhi Jain, CEO and Founder of CloudEagle.ai, says: “When security, IT, HR, and finance operate in silos, access gaps go unnoticed, privilege creep accumulates, and compliance risks grow. Without a unified strategy, IAM becomes fragmented rather than a business enabler. The future of identity management depends on breaking down these silos and making IAM a shared responsibility across the entire enterprise.”
Are you ready to strengthen your identity security?
Schedule a demo with CloudEagle.ai and explore how its AI-driven IAM platform can transform your access management and reduce risk.
FAQs
1. What is the IAM life cycle?
The identity and access management life cycle manages digital identities and access from onboarding through authentication, authorization, and offboarding. A smooth identity and access management workflow ensures secure access throughout a user's journey.
2. What are the 4 pillars of IAM?
The four pillars of identity and access management are Identification, Authentication, Authorization, and Accountability. These pillars support strong security within any IAM implementation.
3. What is the identity and access management implementation plan?
An identity and access management implementation plan is a strategic roadmap that outlines how an organization will manage identities, set access policies, and secure resources. It guides IAM implementation from start to finish and includes workflows and governance.
4. How is IAM implemented?
How to implement IAM involves assessing current systems, defining access controls, choosing the right tools, integrating with applications, applying role-based access, training users, and ongoing monitoring. This approach ensures effective IAM implementation.
5. Does IAM require coding?
Most IAM implementation solutions offer configurable tools that don’t require coding. However, custom integrations or workflows might need some scripting, depending on your identity and access management strategies and technical requirements.

%201.svg)








.avif)




.avif)
.avif)




.png)









