HIPAA Compliance Checklist for 2025

Employee offboarding should be straightforward: someone leaves, their access gets revoked, case is closed.
But in reality, it's one of the messiest, riskiest processes most organizations deal with.
When an employee exits, their access should disappear across every system they touched, SaaS apps, admin panels, databases, collaboration tools, everything. Yet most companies are managing this through a patchwork of manual emails, spreadsheets, and crossed fingers.
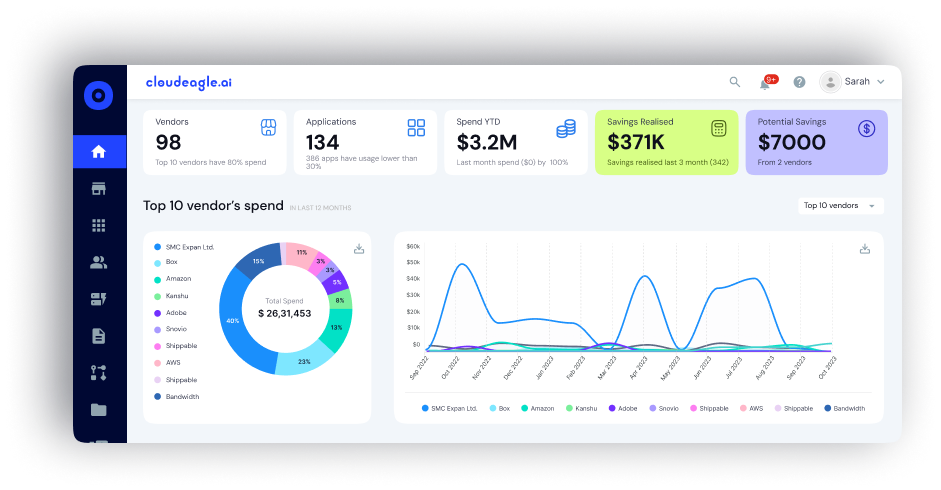
CloudEagle's 2025 IGA Report revealed something startling: 48% of ex-employees still have access to business applications 6+ months after they leave.
Even worse, 70% of breaches now stem from employees who had authorized access, and that includes former employees whose access was never properly revoked.
Let's break down how most organizations handle this "leaver" process today, why it's creating massive security gaps, and how CloudEagle.ai secures it through AI-powered automation.
TL;DR
- Instantly revokes employee access across all apps to eliminate lingering accounts and security gaps.
- Provides visibility into all SaaS and shadow IT tools, so no access goes unnoticed.
- Generates audit-ready SOC2-compliant logs automatically, making compliance effortless and reliable.
- Continuously monitors access and flags risky behavior to prevent insider threats before they happen.
- Reclaims unused licenses, reducing wasted SaaS spend while keeping your environment secure.
What is the Leaver Process in Employee Offboarding?
The leaver process refers to the systematic set of procedures an organization executes to terminate an employee's access rights and system privileges upon departure.
This encompasses deprovisioning user accounts from SaaS applications, revoking system-level permissions, updating internal access records, and ensuring complete access termination across the technology infrastructure.
What it includes:
- Deprovisioning from SaaS applications
- Removing system privileges and admin rights
- Updating internal access records and directories
- Ensuring complete access termination across all platforms
Sounds simple in theory, but here's the catch: the average enterprise runs 300–800 SaaS apps, and many operate completely outside IT's oversight.
You can't revoke access to apps you don't even know exist.
This makes offboarding one of the absolute riskiest steps in the employee lifecycle.
Understanding the Current Offboarding Process in Organizations
Most companies manage offboarding with a total patchwork system, IAM tools, email requests, spreadsheets, and manual updates. Basically, duct tape and hope.
What the Offboarding Process Looks Like Today
- HR initiates the exit: Departures are recorded in HRIS systems like Workday, but IT often learns about them through delayed email notifications or manual handoffs.
- IT manually revokes access: Teams go through each SaaS app, Slack, Google Workspace, Salesforce, project management tools, and deprovision users one by one across potentially hundreds of applications.
- Managers handle app-specific access: Department heads are expected to identify and request the removal of specialized tools or shadow IT apps the employee used, but this rarely happens comprehensively.
The current state, according to CloudEagle's 2025 IGA Report:
- 48% of ex-employees retain access to business applications 6+ months post-exit.
- 75% of IT employees retain elevated privileges after leaving due to complex system dependencies.
- 67% of temporary workers still have access after contracts end.
The Pain Points of Managing the Leaver Process Manually
Managing employee offboarding might sound straightforward, but without automation, it quickly turns into a security and operational nightmare for HR, IT, and security teams. Here's why:
Delayed Access Revocation
When employees leave, IT teams rely on emails or tickets to manually revoke permissions across hundreds of apps. This creates critical security windows:
What happens:
- Former employees retain active access for days, weeks, or even months after departure
- Manual deprovisioning workflows create delays across disconnected systems
- Critical security gaps remain open during the transition period
- Each delay extends the window for potential unauthorized access or data exfiltration
According to CloudEagle's 2025 IGA Report, 48% of ex-employees retain access to business applications 6+ months post-exit, and 75% of IT employees retain elevated privileges after leaving due to complex system dependencies.
Zero Visibility into Complete Access Footprint
Without a unified dashboard, teams have no clear view of which apps former employees actually used or still have access to:
The visibility problem:
- HR, IT, and managers track offboarding separately in spreadsheets or ticketing systems
- Shadow IT apps remain completely invisible to security teams
- No way to know which apps need to be deprovisioned beyond the obvious ones
- Fragmented tracking leads to incomplete offboarding and missed access points
The average enterprise runs 300–800 SaaS apps, with many operating outside IT oversight entirely.
You can't revoke access to apps you don't know exist.
Incomplete Deprovisioning and Access Errors
Manual offboarding processes are inherently inconsistent and error-prone:
Where it breaks down:
- Former employees retain access to sensitive systems they no longer need
- Deprovisioning happens inconsistently across different applications
- Admin privileges often get overlooked in complex system dependencies
- Audit trails are incomplete, making it impossible to prove compliance during reviews
67% of temporary workers still have access after contracts end, creating extended security exposure that organizations don't even realize exists until an audit or incident surfaces it.
Compliance and Audit Failures
When offboarding isn't tracked or automated, organizations face serious compliance risks:
The compliance impact:
- No documentation proving access was properly revoked
- Inability to demonstrate SOC 2, ISO 27001, or regulatory compliance
- Missing approval records and verification timestamps
- Critical systems remain vulnerable with no audit evidence of proper deprovisioning
How CloudEagle.ai Automates and Secures the Leaver Process
CloudEagle.ai takes a strategic approach to employee offboarding with automation and AI-powered security across the entire employee lifecycle, ensuring that no access is left unchecked.
Zero-Touch Deprovisioning Automation
Manual offboarding creates dangerous delays between employee departure and actual access revocation.
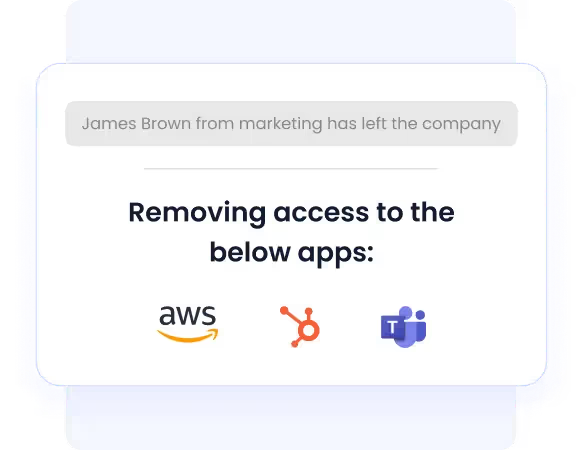
- Challenge: Manual offboarding delays access revocation, leaving ex-employees with active accounts across multiple apps for months, creating serious security risks.
- CE Solution: CloudEagle automates deprovisioning across all SaaS apps, SSO or not, integrating with Okta, Active Directory, and shadow IT tools.
- Outcome: Former employees lose access within moments, eliminating security gaps. IT gains confidence that no lingering accounts remain across all apps and systems.
Complete Visibility Across All Applications
You can't deprovision access to apps you don't know exist, and most enterprises have hundreds of shadow IT tools running outside IT oversight.
- Challenge: Enterprises use hundreds of SaaS apps, many unmanaged, leaving IT blind to shadow IT or unauthorized tools.
- CE Solution: CloudEagle provides visibility and control across 500+ apps, including shadow IT, enabling full offboarding coverage.
- Outcome: IT teams can confidently revoke access everywhere, ensuring no application remains accessible to former employees and preventing blind spots that lead to security breaches.
SOC2-Compliant Audit Trail Management
Proving you properly offboarded employees is just as important as actually doing it, especially during compliance audits.

- Challenge: Manual offboarding lacks detailed audit logs, making compliance difficult and time-consuming during audits.
- CE Solution: CloudEagle automatically generates SOC 2-compliant logs for every action, including approvals, timestamps, and rationale.
- Outcome: Audit preparation becomes effortless as documentation is already available. Organizations can prove proper offboarding and compliance confidently without scrambling for evidence.
AI-Powered Risk Detection and Continuous Monitoring
Offboarding risks don't always surface immediately; sometimes they only become visible through behavioral patterns over time.
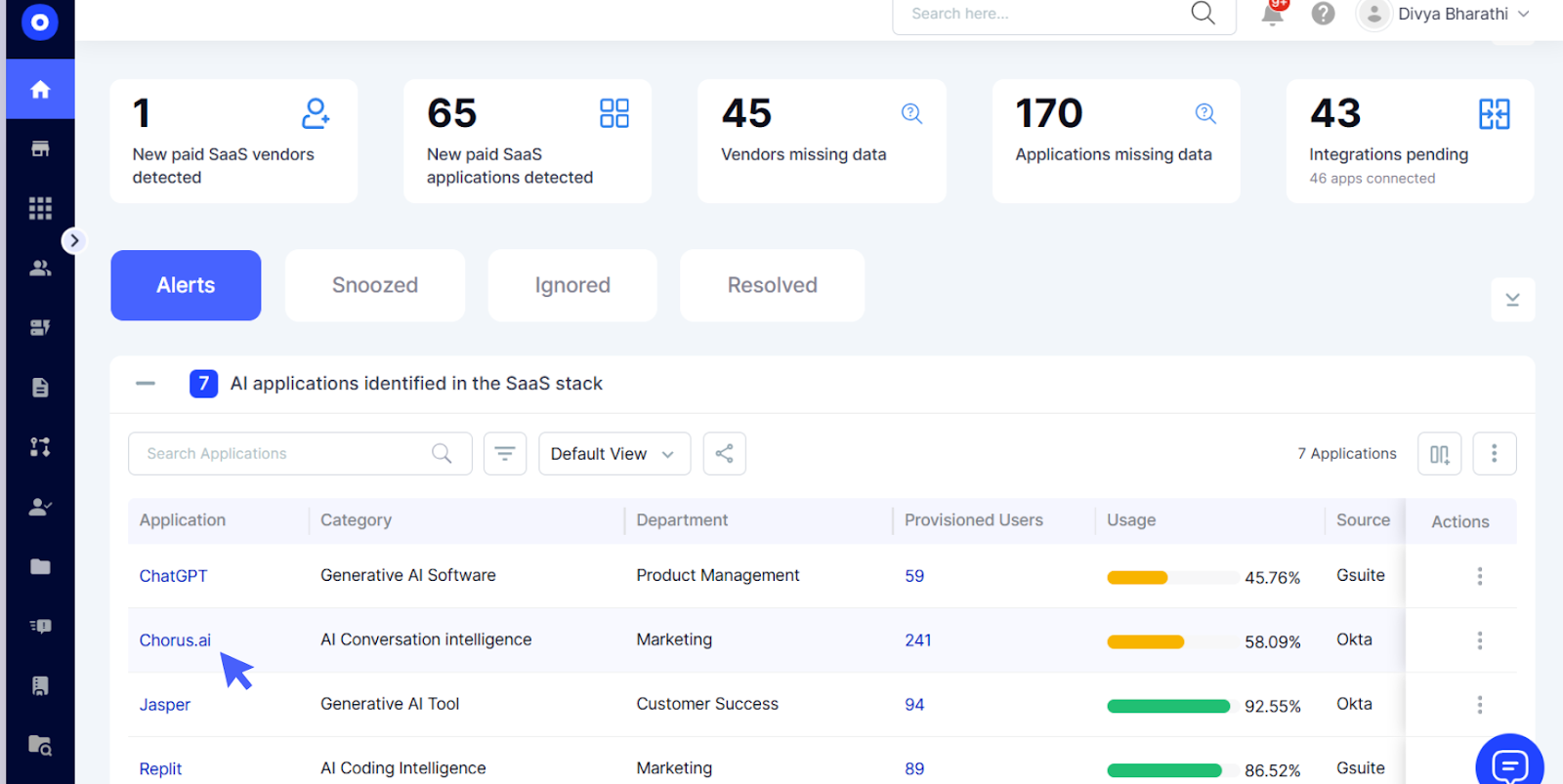
- Challenge: Organizations lack real-time monitoring of former employee access, and 70% of breaches now stem from employees who had authorized access, including former employees whose access was never properly revoked.
- CE Solution: CloudEagle continuously monitors access using AI, detecting anomalies and flagging unusual privileges.
- Outcome: Insider risks are mitigated early, stopping potential breaches before they occur. IT teams can proactively manage security and ensure access control is continuously enforced.
Automated License Reclamation for Cost Optimization
Offboarding isn't just a security concern; it's also a financial opportunity to reclaim wasted software spend.
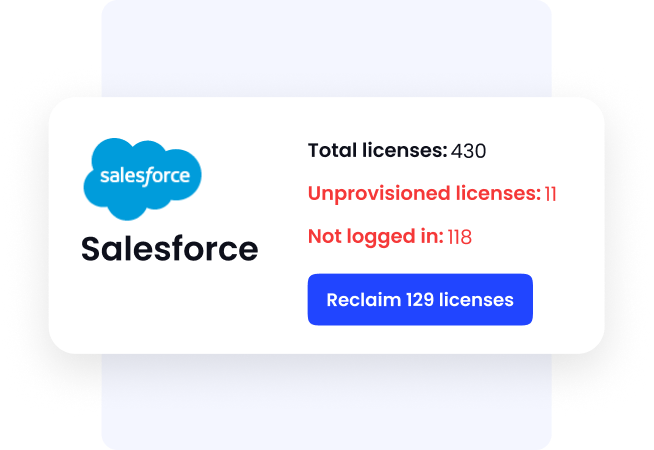
- Challenge: Companies continue paying for licenses assigned to ex-employees, wasting 10–30% of SaaS spend annually.
- CE Solution: CloudEagle automatically identifies unused or low usage licenses and reclaims them across all applications upon employee exit.
- Outcome: Organizations save significant costs while simultaneously improving security, eliminating inactive accounts, and ensuring SaaS spending is optimized without manual tracking or intervention.
Fastest Time to Security
Speed matters when offboarding; every hour of delay is another hour of potential unauthorized access.
- Challenge: Traditional offboarding workflows take days or weeks, leaving sensitive data exposed and creating opportunities for unauthorized access.
- CE Solution: CloudEagle instantly terminates access upon exit, ensuring employee accounts are deactivated across all platforms in minutes.
- Outcome: The risk window shrinks from days to minutes, giving IT teams confidence that no former employee can access business applications or sensitive data.
Why CloudEagle.ai Outperforms Traditional Offboarding Solutions
CloudEagle doesn't just automate offboarding; it redefines the process through comprehensive, AI-powered SaaS management and governance.
Complete Visibility Beyond SSO Perimeter
Unlike traditional IAM tools that only manage access behind SSO or within the corporate perimeter, CloudEagle provides complete visibility into all applications.
Why it's better:
- Traditional IAM tools miss unmanaged applications outside the SSO perimeter
- CloudEagle gives IT a single view of all apps, including shadow IT and unauthorized AI tools
- Proactive security for both managed and unmanaged applications
- Prevents breaches before they happen by closing gaps that other solutions leave open
"Traditional IAM tools can't handle today's SaaS and AI environments, where apps aren't centrally managed. IGA is at a tipping point; enterprises need AI-driven access management to stay secure and compliant." - Nidhi Jain, CEO, CloudEagle.ai
Seamless Integration Eliminates Manual Work
Traditional tools require manual updates, disjointed workflows, and multiple systems to track employee access. CloudEagle integrates with 500+ applications seamlessly.
What this means:
- No manual spreadsheets or separate deprovisioning steps needed
- Automated workflows execute across the entire tech stack instantly
- Syncs real-time data with HR, procurement, and security systems
- IT teams cut manual work by 80%, freeing them for strategic tasks
Unified Security, Compliance, and Cost Optimization
CloudEagle's centralized governance ensures offboarding isn't just a security measure; it's also a compliance and financial tool.
The comprehensive advantage:
- License reclamation optimizes unused licenses during offboarding
- Cuts wasteful spending and drives 10–30% savings in SaaS costs year over year
- Reduces risk of data breaches
- Ensures audit readiness
- Significant cost savings on unused software licenses
Continuous Monitoring for Insider Threat Mitigation
CloudEagle's solution ensures continuous monitoring of employee access across the entire lifecycle, onboarding, employment, and offboarding.
Why continuous matters:
- Unlike manual periodic reviews, CloudEagle automates risk-based access reviews that run continuously
- Catches excessive privileges and risky behavior in real-time
- Mitigates insider threats early
- Prevents breaches that happen when access isn't revoked fast enough
Conclusion
Internal breaches happen more often than you think, and every day a departing employee still has access is a risk you can’t afford. Manual offboarding and hidden apps leave gaps that hackers, or even accidental misuse, can exploit.
CloudEagle.ai turns offboarding into a simple, fast, and reliable process. It gives you real-time visibility across all apps, including shadow IT, automates deprovisioning instantly, continuously monitors for risky access, and reclaims unused licenses.
With CloudEagle.ai, you know for sure that nothing slips through the cracks and your business stays secure.
Take control now, book a free demo and see how CloudEagle.ai can secure your offboarding process from day one.

%201.svg)









.avif)




.avif)
.avif)




.png)









