HIPAA Compliance Checklist for 2025

Every day, enterprises collect and process massive amounts of personal and sensitive information. From healthcare records to financial data, if mishandled, can cause lasting harm. Protecting this data is a regulatory and reputational necessity.
Real-world incidents highlight the risks. In 2023, MOVEit’s data breach exposed millions of records across governments and enterprises worldwide. Events like this show how a single vulnerability can ripple across industries and damage trust instantly.
This article explains 10 essential data privacy frameworks every enterprise should know. You’ll learn what IT governance frameworks are, why they matter, and how aligning with them helps protect both customer data and brand reputation.
TL;DR
- Frameworks provide rules, policies, and practices to securely manage personal and sensitive data across its lifecycle.
- GDPR, CCPA, HIPAA, PCI DSS, ISO/IEC 27001, NIST, SOC 2, FedRAMP, GLBA, and COPPA set global and industry-specific privacy standards.
- They reduce breach risks, ensure regulatory compliance, build customer trust, and improve overall risk management.
- Enterprises face overlapping regulations, high costs, evolving threats, employee awareness gaps, and data mapping difficulties.
- Platforms like CloudEagle.ai centralize oversight, automate audits, enforce access controls, and continuously monitor compliance.
What are Data Privacy Frameworks?
Data privacy frameworks offer organized guidelines for protecting personal and sensitive data within organizations. They combine regulations, policies, and practices to manage data collection, use, storage, and disposal securely.
Frameworks focus on principles like transparency, user consent, and accountability in every step of data management. Legal, ethical, and operational requirements shape these frameworks and guide compliance across regions.
Examples include the EU-U.S. Data Privacy Framework, which helps enterprises handle data in various jurisdictions. Using the information security framework lowers risk, protects public trust, and supports global regulatory compliance.
How Does Data Privacy Framework Work?
A data privacy framework sets structured steps for managing personal information through its entire lifecycle. It covers collection, processing, storage, sharing, and safe disposal of data across all systems and departments.
Core principles of data privacy frameworks include transparency, user consent, and accountability for data handling. Enterprises map where data is stored before applying security controls like encryption, access restrictions, and monitoring.
Proper consent is always obtained before using personal data for any purpose. Regular audits and assessments of IT compliance frameworks help verify compliance and address SaaS security risks before they cause problems.
For example, when GDPR took effect in 2018, Microsoft adopted the regulation’s requirements as a company-wide standard. This meant not just updating policies but also embedding privacy-by-design principles into its products. By doing so, Microsoft strengthened customer trust and set a benchmark for global compliance practices.
Why Data Privacy Frameworks are Important?
Data privacy frameworks are essential for protecting people's personal information from misuse or abuse. They help enterprises follow laws like GDPR compliance and avoid costly fines for non-compliance.
The data privacy compliance framework promotes trust by showing responsible data handling to consumers and partners. They support enterprises in preventing identity theft or fraud before problems occur. Here are some reasons why data privacy frameworks are important:
Protecting Sensitive Information
Information security framework ensures customer data is secured against theft, misuse, or unauthorized access. In 2024, IBM reported that the average data breach cost reached $4.4 million globally, showing how high the stakes are.
Regulatory Compliance
Data privacy frameworks help organizations align with laws like GDPR, HIPAA, and CCPA. Without these guidelines, companies risk heavy fines and reputational damage from non-compliance.
Building Customer Trust
Strong IT compliance frameworks practices foster transparency, which directly impacts brand reputation. Customers are more likely to engage with companies that clearly demonstrate data protection.
Improving Risk Management
Frameworks identify potential weaknesses before they turn into causes of data breaches. Proactive management saves enterprises from legal battles, financial penalties, and negative press.
Supporting Global Operations
Multinational companies face varying privacy laws. Frameworks provide consistency, enabling smooth data handling practices across different regions and regulatory environments.
Top 10 Data Privacy Frameworks to be Aware of
With dozens of regulations worldwide, knowing which privacy frameworks matter most can feel overwhelming. However, certain standards consistently shape how enterprises safeguard sensitive data and meet SaaS compliance obligations.
These 10 key frameworks provide enterprises with the structure to protect customer information, minimize risks, and maintain global trust. Understanding them is the first step to building a privacy-first strategy. Here is the security framework list:
1. General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR), enforced in 2018, is the EU’s landmark privacy law. Unlike older data privacy frameworks, it applies extraterritorially, meaning any enterprise handling EU citizens’ data must comply, regardless of where the enterprise operates.
Why It Matters
GDPR changed the global conversation about privacy. It gave individuals more control over their data and pushed companies to adopt privacy-by-design practices. For multinational enterprises, this information security framework sets a new benchmark that influences U.S. laws like CCPA and Brazil’s LGPD.
Core Components
- Lawful Processing: Enterprises must demonstrate a clear legal basis, such as consent or contractual necessity, before handling personal data.
- Expanded User Rights: Data subjects can access, rectify, port, or erase their data, forcing businesses to maintain transparent processes.
- Breach Notification: Enterprises must disclose common causes of data breaches within 72 hours, encouraging faster detection and stronger incident response.
- Privacy by Design: Enterprises are required to embed data protection into technology and processes from the ground up.
- Oversight and Accountability: Some Enterprises must appoint Data Protection Officers (DPOs) to oversee compliance efforts.
Consequences of Non-Compliance
Violations can lead to fines of up to €20 million or 4% of annual global turnover. In 2021, Amazon faced a €746 million fine under GDPR for inadequate consent practices.
As Margrethe Vestager, Executive Vice President of the European Commission, emphasized:
“Privacy is not a luxury, but a fundamental right.”
Non-compliance to data security framework risks devastating financial penalties and long-term reputational harm.
2. California Consumer Privacy Act (CCPA)
The California Consumer Privacy Act (CCPA), enacted in 2018, is one of the strongest data privacy frameworks in the United States. It grants California residents greater control over their personal information and imposes clear obligations on businesses.
Why It Matters
CCPA set the tone for privacy legislation across the U.S., influencing laws in other states. For enterprises, this data privacy compliance framework highlights the shift toward customer-centric privacy practices and creates operational models that may soon become nationwide standards.
Core Components
- Consumer Rights: Enterprises can know what data is collected, request deletion, and opt out of data sales.
- Business Obligations: Enterprises must disclose data practices, update privacy policies, and provide easy opt-out mechanisms.
- Coverage Thresholds: Applies to enterprises meeting criteria like $25 million in revenue or handling 50,000+ records.
- Non-Discrimination: Enterprises cannot penalize consumers for exercising their privacy rights.
- Transparency Requirements: Privacy notices must be clear, accessible, and updated regularly.
Consequences of Non-Compliance
Penalties include fines of up to $7,500 per intentional violation and $2,500 per unintentional violation. Beyond financial costs, non-compliance damages brand trust, especially in a state that leads U.S. privacy conversations, something which compliance risk management cannot rebuild.
3. Health Insurance Portability and Accountability Act (HIPAA)
The Health Insurance Portability and Accountability Act (HIPAA), enacted in 1996, is the primary U.S. law governing healthcare data privacy. This data privacy framework applies to healthcare providers, insurers, and their business associates handling protected health information (PHI).
Why It Matters
HIPAA ensures that sensitive health data remains confidential while still allowing necessary information sharing for patient care. Unlike other data privacy frameworks, it balances the need for security with the practical demands of healthcare operations.
Core Components
- Privacy Rule: Defines standards for safeguarding medical records and patient identifiers.
- Security Rule: Requires administrative, technical, and physical safeguards to protect electronic PHI.
- Breach Notification Rule: HIPAA compliance audit mandates timely disclosure to affected individuals and regulators after data breaches.
- Minimum Necessary Standard: Enterprises must limit data use and disclosure to what is essential.
- Business Associate Agreements: Contracts must ensure third parties follow HIPAA requirements.
Consequences of Non-Compliance
Penalties range from $100 to $50,000 per violation, capped at $1.5 million annually. Non-compliance may also result in legal action and permanent damage to patient trust. HIPAA Journal revealed that 725 data breaches took place in 2023.
4. Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS is a global standard developed by major card brands to secure cardholder data. This data security framework applies to any enterprise that stores, processes, or transmits payment card information.
Why It Matters
With billions of transactions occurring daily, PCI DSS assessment is one of the most common data privacy frameworks that reduces the risk of card fraud and identity theft. Compliance assures customers their payment details are protected across retail, banking, and online platforms.
Core Components
- Secure Network: Firewalls and encryption to protect payment data.
- Access Control: Restricting cardholder data to authorized personnel.
- Monitoring and Testing: Regular system scans, penetration tests, and activity logging.
- Information Security Policy: Formalized policies to guide staff and vendors.
- Vulnerability Management: Ongoing updates and patch management to minimize risks.
Consequences of Non-Compliance
Organizations can face fines of $5,000 to $100,000 per month from payment brands.
5. ISO/IEC 27001 for Information Security
ISO/IEC 27001 is the global standard for information security, structured around establishing, implementing, and continually improving an Information Security Management System (ISMS). This is one of the most important data privacy frameworks enterprises should comply with.
Why It Matters
Achieving certification demonstrates to clients, partners, and regulators that your enterprise operates under rigorous access governance. It’s a foundation for trust building and supports international regulatory alignment.
Core Components
- Risk Assessment & Treatment: Continuously identify, evaluate, and mitigate risks to information assets.
- Comprehensive Controls: Implement 114 controls across security domains like access management, encryption, and incident response.
- Continuous Improvement Cycle: Plan–Do–Check–Act (PDCA) framework ensures ongoing policy, control, and performance enhancement.
- Leadership Commitment: Top management must endorse security strategies and allocate resources for effective ISMS operations.
Consequences of Non-Compliance
Beyond immediate breach costs, this incident led to remediation expenses, lost client contracts, and long-term erosion of trust. For example, despite having ISO 27001 in place, Capita suffered a major breach in 2025, after a ransomware attack exploited an unpatched Exchange server.
6. NIST Privacy Framework
The NIST Privacy Framework is a voluntary tool developed to help enterprises manage privacy risks through structured processes. Like other data privacy frameworks, this is also essential.
Why It Matters
It provides enterprises with a scalable model to identify, assess, and reduce SaaS security risks. This framework aligns with global regulations while offering flexibility for organizations across industries.
Core Components
- Identify-P: Understand data processing activities, systems, and potential privacy risks.
- Govern-P: Define organizational governance structures and responsibilities for privacy management.
- Control-P: Implement technical and procedural controls to manage personal data use.
- Communicate-P: Ensure transparency with stakeholders through policies, notices, and disclosures.
- Protect-P: Safeguard data with measures to minimize unauthorized use or exposure.
Consequences of Non-Compliance
Enterprises failing to use NIST’s model may face unchecked privacy risks, misaligned policies, and reduced regulatory readiness. This can erode customer confidence and increase exposure to enforcement actions.
7. SOC 2 Privacy Trust Principle
The SOC 2 Privacy Trust Principle is part of the SOC 2 framework. This data privacy compliance framework focuses on how enterprises handle personal data responsibly.
Why It Matters
It ensures that enterprises follow strict protocols for collection, use, retention, and disposal of personal data. Customers and auditors of these data privacy frameworks often look to SOC 2 certification as a mark of trust and reliability.
Core Components
- Notice and Consent: Informing users about data use and obtaining their approval.
- Collection and Use: Limiting data gathering to relevant purposes and authorized needs.
- Retention and Disposal: Keeping data only as long as necessary and disposing of it securely.
- Access and Correction: Allowing individuals to review and correct their information.
- Security and Monitoring: Protecting personal data through safeguards and continuous monitoring.
As Satya Nadella, CEO of Microsoft, once said:
“Privacy is a human right. We have to treat it that way.”
This principle reinforces why SOC 2 privacy criteria are vital in protecting user trust.
Consequences of Non-Compliance
Ignoring SOC 2 data security framework can lead to customer distrust, legal scrutiny, and significant business reputation damage.
8. Federal Risk and Authorization Management Program (FedRAMP)
FedRAMP is a U.S. government program that standardizes security assessments for cloud services used by federal agencies. This is one of the hardest data privacy frameworks to comply with in the first place.
Why It Matters
This data privacy compliance framework ensures that government data hosted in the cloud is protected with consistent, rigorous, and approved security controls.
Core Components
- Baseline Security Controls: Standardized requirements based on NIST guidelines.
- Assessment and Authorization: Independent audits for cloud providers seeking government use.
- Continuous Monitoring: Ongoing security checks to maintain authorization status.
- Documentation: Detailed security packages for transparency and trust.
Consequences of Non-Compliance
Failure to meet FedRAMP information security framework blocks providers from serving federal agencies and risks contract loss.
9. Gramm-Leach-Bliley Act (GLBA)
GLBA, also known as the Financial Services Modernization Act, requires U.S. financial institutions to protect consumer data privacy.
Why It Matters
This IT compliance frameworks ensures banks, lenders, and insurance firms safeguard sensitive financial information and explain their data-sharing practices.
Core Components
- Privacy Rule: Requires institutions to disclose how customer data is collected and shared.
- Safeguards Rule: Mandates security measures to protect against unauthorized access or data breaches.
- Pretexting Provisions: Prevents fraudulent access to private financial records.
Consequences of Non-Compliance
Violations can lead to heavy fines, legal penalties, reputational harm, and customer trust erosion. In 2022, the FTC fined mortgage broker Mortgage Solutions for failing GLBA compliance after sensitive loan documents were exposed online. The case highlighted how inadequate safeguards can damage both consumers and a firm’s credibility.
10. Children’s Online Privacy Protection Act (COPPA)
COPPA, enacted in 1998, is a U.S. law designed to protect children under 13 online. It governs how businesses, websites, and apps handle personal information when kids use their services.
Why It Matters
With the rise of gaming apps, social media, and learning platforms, children’s data is more exposed than ever. COPPA ensures enterprises prioritize safety and transparency before collecting or processing that information.
Core Components
- Parental Consent: Websites and apps must obtain verifiable parental permission before gathering data from children.
- Privacy Notices: Businesses must display clear and accessible privacy policies detailing data practices for minors.
- Data Minimization: Companies are restricted from collecting unnecessary data, limiting use strictly to intended services.
- Advertising Restrictions: Behavioral ads targeting children under 13 are strictly regulated to prevent exploitation.
Consequences of Non-Compliance
Failing to follow COPPA can lead to hefty fines and legal scrutiny. For example, in 2019, Google and YouTube was fined $170 million by the FTC for illegally collecting children’s data without parental consent, highlighting the serious risks of ignoring compliance.
Data Privacy Compliance Framework Challenges
Organizations face challenges with data privacy frameworks due to tough and frequently changing global regulations. It is hard to implement complex controls and ensure all data is secure from new threats and errors. Key information security compliance framework challenges Include:
Complex Regulatory Overlaps
Enterprises often operate across multiple regions with conflicting privacy laws. Aligning GDPR, CCPA, and HIPAA requirements simultaneously creates compliance fatigue and resource strain.
High Implementation Costs
Building and maintaining data privacy programs requires investment in tools, training, and audits. For smaller firms, these costs can feel overwhelming, affecting operational budgets.
Evolving Threat Landscape
Cybercriminals continuously adapt, exploiting new vulnerabilities. Information security compliance framework is not enough unless enterprises also prioritize real-time monitoring and security updates.
Employee Awareness Gaps
Even the best data privacy frameworks fail if employees mishandle data. Inconsistent training and awareness can lead to accidental breaches or overlooked risks.
Data Mapping Difficulties
Many enterprises struggle to identify where sensitive data resides across systems. Without proper mapping, compliance documentation becomes incomplete and unreliable.
How CloudEagle.ai Can Secure Data and Compliance?
CloudEagle.ai is a SaaS procurement and management platform that helps organizations efficiently track, optimize, manage, and renew SaaS licenses.
With CloudEagle.ai, you can identify risks, enforce security policies, and generate audit-ready reports with ease. Here’s how the platform supports data privacy frameworks compliance.
Centralized Compliance Oversight
Non-compliance to data privacy frameworks often leads to expensive fines and legal issues, but CloudEagle.ai helps prevent this by maintaining continuous compliance. Real-time alerts highlight violations early, allowing you to act before penalties occur.
The platform centralizes compliance by monitoring user activity, tracking app access, and maintaining comprehensive records. This simplifies oversight, reduces complexity, and enhances operational efficiency.
With built-in coverage for information security compliance framework like SOC 2, ISO 27001, and GDPR compliance, CloudEagle.ai streamlines access control, monitoring, and auditing. This removes the need for multiple tools, making compliance simpler and more effective.
Data Encryption and Protection
CloudEagle.ai ensures that sensitive data is encrypted during transit and while stored, adhering to the rigorous standards of ISO 27001 and HIPAA. This SaaS security measure helps protect against unauthorized access and keeps your data secure at every stage.

Automated Compliance Reporting
Manual compliance reporting in data privacy frameworks is resource-heavy, but CloudEagle.ai automates the process, ensuring audit-ready reports are always available. This saves time while minimizing manual work.
Its real-time audit logs deliver full visibility into access and usage, enabling swift detection and resolution of compliance concerns.
Continuous Monitoring and Risk Mitigation
CloudEagle.ai provides ongoing monitoring of identity and access management and data transactions to ensure controls stay effective. This helps organizations detect and fix security gaps before they escalate.
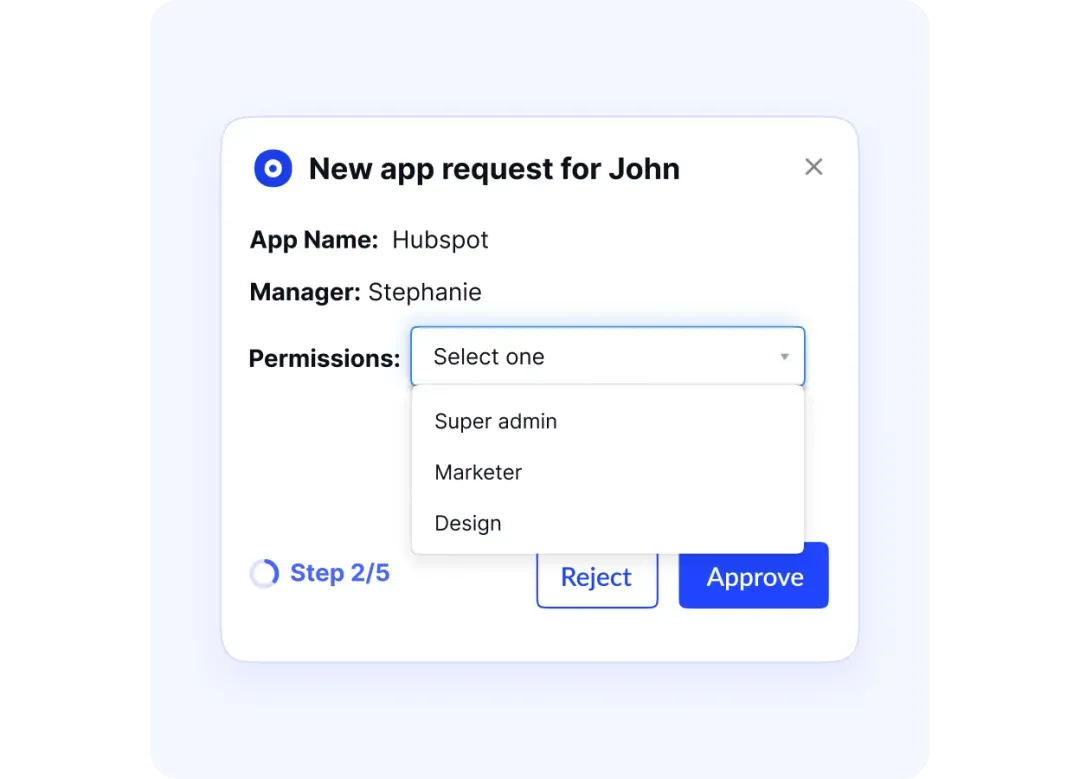
The platform also identifies compliance gaps early, providing actionable insights that strengthen security and reduce risks proactively.
Automated Access Reviews
Regulations such as SOC 2 and ISO 27001 mandate periodic access reviews, which can be tedious without automation. CloudEagle.ai streamlines data privacy frameworks by continuously focusing on app access reviews, ensuring only authorized personnel can reach sensitive data.
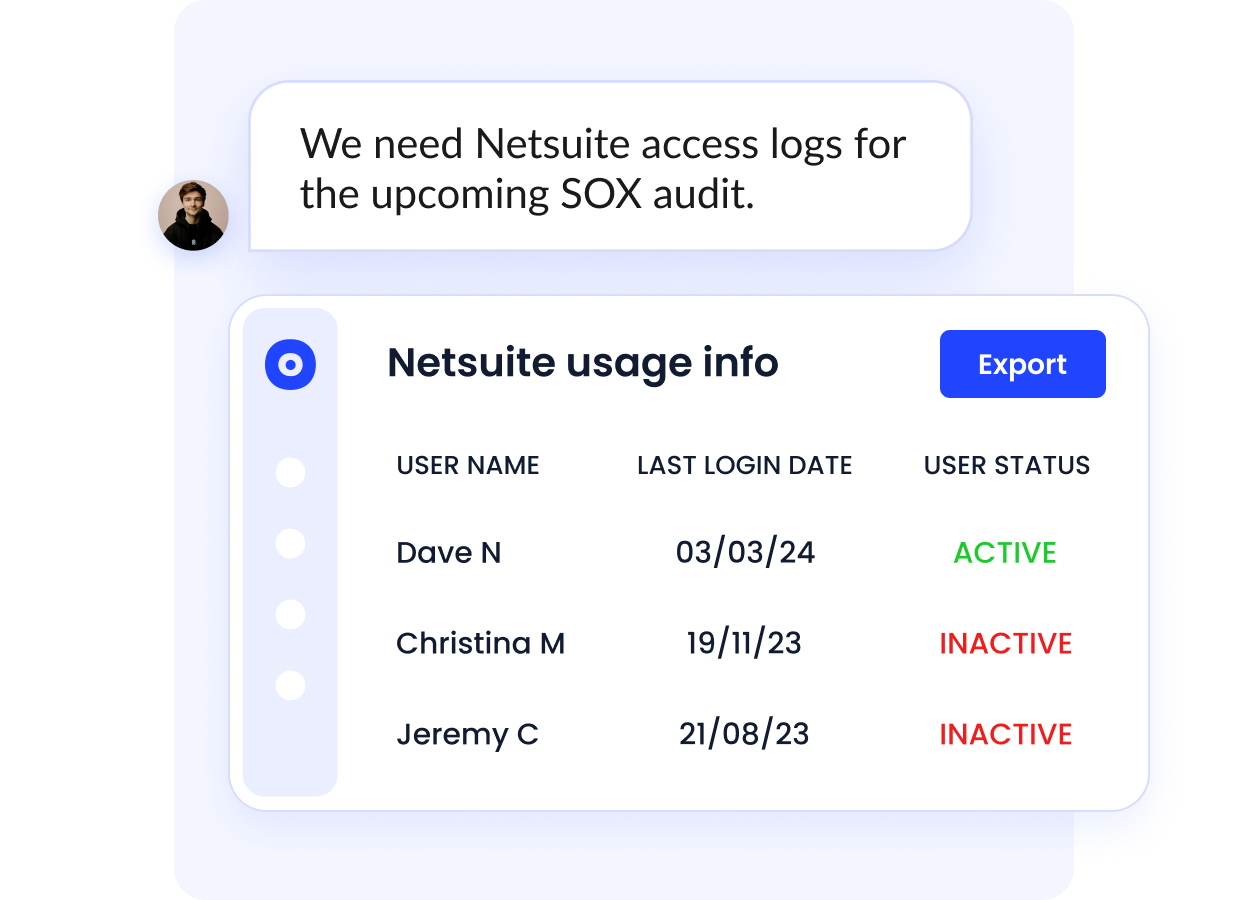
By automating reviews, the platform cuts down manual work, reduces compliance risks, and ensures stronger regulatory alignment.
Detailed Audit Trails
Maintaining audit trails is essential for SOC 2 and ISO 27001 compliance. CloudEagle.ai captures all system activity, preserving data integrity and making audit evidence retrieval simple.
The platform also enforces security policies aligned with SOC 2, ISO 27001, and GDPR, while allowing customizations to meet unique compliance needs. This ensures ongoing adherence with evolving regulations.
Conclusion
Data privacy frameworks are the backbone of trust, compliance, and resilience in a digital-first world. By understanding their importance and addressing common challenges, enterprises can better protect sensitive data and maintain customer confidence.
To simplify compliance and strengthen your data security posture, consider exploring modern solutions tailored for enterprises. CloudEagle.ai can help streamline compliance management and reduce risk across your SaaS ecosystem.
FAQs
1. What is the difference between GDPR and a privacy framework?
GDPR is a legal regulation focused on EU citizens’ data rights. Privacy frameworks provide structured guidance to implement security and compliance measures across organizations.
2. What is the difference between SCC and a data privacy framework?
Standard Contractual Clauses (SCC) are legal tools for transferring data internationally. Privacy frameworks are broader programs guiding overall data protection policies and practices.
3. What is an example of data compliance?
An example is a company following GDPR by obtaining user consent, securing personal data, and documenting access procedures.
4. What is the best data privacy certification?
ISO/IEC 27701 is widely recognized, providing guidance for implementing a privacy information management system aligned with GDPR and global regulations.
5. What are the three types of data security?
The three types are: physical security (protecting hardware), technical security (encryption, firewalls), and administrative security (policies, training, audits).

%201.svg)









.avif)




.avif)
.avif)




.png)









