HIPAA Compliance Checklist for 2025

The growing complexity of modern IT environments, fueled by the surge in SaaS tools, remote workforces, and cloud-based infrastructure, has forced organizations to rethink how they manage access and protect data.
Why does this matter now more than ever? Because every access decision you make, whether it's assigning a role in Microsoft Teams, managing user permissions in Salesforce, or syncing accounts across cloud apps, can either strengthen or weaken your security posture.
With cyberattacks growing in sophistication and internal governance becoming more complex, choosing between centralized vs decentralized management can significantly affect compliance, scalability, and control.
This guide breaks down everything you need to know, comparing the two approaches side-by-side across multiple dimensions and helping you identify the right fit for your organization.
TL;DR
- Centralized vs decentralized access management defines how control, visibility, and access decisions are structured across an organization.
- Centralized models offer stronger oversight and consistency, while decentralized models enable faster, team-level autonomy.
- Key differences include control, scalability, policy enforcement, user experience, and compliance readiness.
- Your ideal model depends on factors like org size, security needs, IT resources, and regulatory requirements.
- CloudEagle.ai supports all models with centralized dashboards, automated workflows, and 500+ app integrations to simplify access management.
What are Access Management Models?
Access management models determine how user access to resources is granted or restricted. They play a vital role in ensuring security by defining who can access specific assets and under which conditions. Common models include DAC, MAC, RBAC, and ABAC.
Access management is the process of defining and controlling who can access your systems, applications, and data. It ensures the right people get the right access at the right time.
This is where the centralized vs decentralized management debate comes into play. Both models aim to streamline access, protect data, and support business productivity, but they do so in fundamentally different ways.
Whether you’re evaluating IAM for the first time or rethinking your current strategy, understanding the underlying frameworks of centralized access management and decentralized identity management is the first step toward making the right choice.
What is Centralized Access Management?
Centralized Access Management is a security model that manages user identities and permissions from a single, unified system. It simplifies administration, improves visibility, and strengthens security, especially for organizations managing a large number of digital tools and resources.
This model provides consistent rules and controls across your ecosystem, making it easier to implement centralized access control, enforce compliance, and reduce risks.
In the context of centralized vs decentralized, centralized systems offer better visibility, especially when managing sensitive access across cloud tools, making it ideal for regulated industries.
Key characteristics of centralized access management:
- Single point of control over all access controls
- Easier to enforce company-wide policies and compliance standards
- Simplifies onboarding/offboarding processes
- Enhances visibility into user activities and access logs
- Strong alignment with centralized vs decentralized cybersecurity principles
- Best suited for large enterprises or regulated industries
What is Decentralized Access Management?
Decentralized Access Management (DAM) is a security model where access decisions are handled independently by various teams or systems, without a central authority. This distributed approach increases flexibility, enhances resilience, and reduces the risks tied to a single point of failure.
This decentralized vs centralized approach enhances agility, and teams can quickly grant or revoke access based on operational needs. It also aligns with modern DevOps and product-led cultures where speed and autonomy matter.
However, it also increases the complexity of governance, making centralized vs decentralized cybersecurity a key discussion in security circles. Without a central view, it becomes harder to detect anomalies, enforce consistent policies, or prove compliance.
Key characteristics of decentralized access management:
- Teams and departments manage access independently
- Increases speed and flexibility in access provisioning
- Encourages autonomy, but can lead to inconsistent policies
- Limited centralized visibility can increase security risks
- Raises questions around centralized vs decentralized risk management
- Ideal for fast-moving startups or distributed teams
Centralized vs. Decentralized Access Management: Key Differences
Centralized access management uses one central system to control access to all resources, whereas decentralized management spreads control across multiple systems or teams. The main difference is where authority resides and how user credentials are managed and enforced.
.png)
Control and Oversight
Centralized systems give IT full visibility and control over user access, reducing blind spots and unauthorized permissions. In contrast, decentralized models distribute control across teams, which can empower productivity but also lead to outdated or excessive permissions, raising concerns in risk management.
Policy Enforcement and Consistency
Centralized models enforce uniform security policies like MFA or password updates across all systems. Decentralized setups often result in inconsistent enforcement, with some teams applying stricter standards than others, creating potential security loopholes.
Scalability and Flexibility
Decentralized systems offer better flexibility and scale easily as teams adopt their tools and processes. However, without centralized oversight, data governance becomes complex, prompting many organizations to adopt hybrid approaches.
Security Posture and Risks
Centralized access control provides a stronger defense through centralized logging, audits, and better anomaly detection. Decentralized models can increase the attack surface due to scattered access points, stale credentials, and limited visibility.
User Experience and Productivity
Decentralized access enables faster access to tools, boosting team productivity. But without proper governance, it can cause chaos. Centralized systems ensure control but may slow down requests unless supported by automation.
Cost and Resource Implications
While centralized management requires upfront investment in tools and maintenance, it reduces long-term risks and audit costs. Decentralized models seem cheaper initially, but often incur hidden costs due to duplicated efforts and security lapses.
Compliance and Audit Readiness
Centralized systems simplify compliance by unifying logs and roles, making audits like SOC 2 or HIPAA easier. Decentralized environments demand more manual effort to prove compliance and track access across fragmented systems.
Centralized or Decentralized Access Management: Which One Is Better?
Neither centralized nor decentralized systems are universally better; the ideal choice depends on your organization’s goals and structure. Centralization brings control, consistency, and cost efficiency, while decentralization supports agility, faster decisions, and greater team autonomy.
Factors That Influence Your Choice
Your organization’s access management strategy should align with your operational reality. There’s no one-size-fits-all answer in the centralized vs decentralized management debate.
Key decision-making factors include:
- Industry regulations: Highly regulated sectors like finance, insurance, and healthcare often mandate centralized access control for better audit trails and compliance.
- Company size and team structure: Larger organizations often choose centralized oversight, whereas smaller teams may lean toward a decentralized vs centralized approach to maintain agility and responsiveness.
- IT resources: Companies with lean IT teams often centralize to maintain better control, while tech-savvy departments might thrive under decentralized identity management.
- Risk appetite: Organizations with low security risks tend to favor centralized over decentralized cybersecurity strategies, as they offer tighter control and monitoring.
- Tool diversity: Businesses using a wide mix of SaaS tools (like Slack, GitHub, Salesforce, Zoom) need flexible management approaches, which often drives hybrid adoption.
Examples of Centralized IAM Use Cases
Centralized IAM shines in environments where control, uniformity, and security are top priorities. These organizations typically operate under tight regulations and need a clear, consistent way to manage access across complex infrastructures.
Real-world use cases include:
- Large financial institutions that need strict access governance for systems like Salesforce, AWS, and internal CRMs, supporting secure and auditable workflows.
- Healthcare networks manage patient data across multiple hospitals and third-party systems, ensuring HIPAA-compliant access through centralized access management.
- Enterprises with global operations where centralized oversight ensures compliance with local and international regulations.
- Government agencies that require a uniform identity verification system, enhanced with centralized vs decentralized risk management to reduce insider threats.
These organizations benefit from stronger oversight, enhanced anomaly detection, and faster incident response, critical factors in centralized vs decentralized cybersecurity evaluations.
Examples of Decentralized IAM Use Cases
Decentralized access management thrives in agile, innovation-driven organizations where speed and autonomy are essential. Teams have more control, often at the cost of uniform policy enforcement.
Examples where decentralized IAM works well:
- Startups or scale-ups using tools like GitHub, Slack, and Notion, where product teams manage access independently to iterate faster.
- Engineering-driven companies where developers need autonomy to provision cloud resources or test environments without central approval.
- Companies with distributed teams across time zones allow local leads to manage access based on immediate operational needs.
- Innovation labs or research arms within enterprises that need a flexible, experimentation-friendly environment favor a decentralized vs centralized model.
However, these setups demand robust internal controls, clear documentation, and training to prevent access sprawl or privilege creep.
Industry Trends Shaping the Future
Modern trends are blurring the lines between centralized vs decentralized systems. While traditional boundaries still matter, many organizations are embracing hybrid models that combine the strengths of both.
Emerging trends to watch:
- AI-driven automation enhances centralized systems by streamlining access provisioning, anomaly detection, and compliance monitoring at scale.
- Blockchain technology enables secure, self-sovereign identities, supporting the shift toward decentralized identity management and reducing reliance on central authorities.
- Zero Trust architecture prioritizes context-aware access, requiring granular control over every session, regardless of whether your system is centralized or decentralized.
- Hybrid IAM models are gaining traction, offering centralized policy engines with decentralized execution points, ensuring both security and flexibility.
These trends are influencing how organizations approach centralized vs decentralized cybersecurity, pushing leaders to rethink rigid models in favor of more dynamic, risk-based access strategies.
Choosing the Right Model for Your Organization
The right model should align with your organization's size, complexity, compliance requirements, and internal capabilities. Some companies thrive with full control via centralized access control, while others need the speed and agility of decentralized identity management. And increasingly, many opt for a hybrid approach, taking the best of both worlds.
Balancing Security with User Experience
Security and usability often pull in opposite directions. Too much restriction frustrates users; too much freedom increases risk. Striking the right balance is key, especially in the centralized vs decentralized cybersecurity conversation.
What to consider:
- Centralized access management enhances security monitoring, role-based control, and incident response, but may slow down access provisioning.
- Decentralized vs centralized environments allow teams to move faster, but can introduce inconsistent security policies.
- Look for IAM tools that support adaptive access controls, integrating contextual risk signals to make dynamic decisions.
For security-first organizations, centralized vs decentralized management models should prioritize visibility and control without hurting user experience.
IT Resources and Budget Considerations
Not every company has the resources to build and maintain complex IAM systems. Your choice depends heavily on the capabilities of your IT team and your available budget.
Key considerations include:
- Centralized models typically require a more robust IAM platform and skilled admins, but provide long-term cost savings through automation and centralized oversight.
- Decentralized identity management may cost less to implement initially, but could lead to inefficiencies and access sprawl if not monitored properly.
- Budgeting for compliance and auditing needs also leans in favor of centralized access control, especially in regulated sectors.
Align your model with what your team can realistically manage, without sacrificing security posture.
Organizational Size and Complexity
Your organizational footprint plays a big role in determining the best model. Complexity increases with more departments, regions, and SaaS tools.
Here’s how size influences your model:
- Large enterprises benefit from centralized vs decentralized data governance approaches that allow global policy enforcement with local nuance.
- Small and mid-sized businesses (SMBs) often prefer decentralized vs centralized models for operational flexibility and lower overhead.
- Companies with multiple subsidiaries or brands might adopt centralized oversight with decentralized execution, especially useful in M&A situations.
The more complex your environment, the more valuable centralized visibility becomes.
Hybrid Approaches: Best of Both Worlds
Many organizations find themselves between two extremes, wanting the control of centralization with the flexibility of decentralization. That’s where hybrid IAM comes in.
Benefits of hybrid models:
- Allow central IT to define policies while giving teams local autonomy to manage day-to-day access.
- Enable centralized vs decentralized risk management strategies that adapt to business units based on sensitivity and risk.
- Ideal for companies scaling rapidly, entering new regions, or managing both cloud-native and legacy systems.
A hybrid strategy provides structure without rigidity, making it a preferred approach for future-ready enterprises.
How CloudEagle.ai Supports Modern Access Management
CloudEagle.ai is more than just a SaaS procurement and optimization platform; it’s your strategic partner in streamlining identity and access management through automation, visibility, and control.
Whether you're leaning toward centralized access management or exploring hybrid strategies, CloudEagle.ai helps you manage access consistently, securely, and efficiently.
Centralized Control With a Unified Dashboard
CloudEagle provides a centralized dashboard where IT admins can:
- Manage all users, roles, and permissions across applications.
- Track who has access to what, and why.
- Streamline provisioning and deprovisioning workflows.
With over 500 integrations across HRIS, SSO, and financial systems, it offers complete control and visibility across your SaaS environment.
This is critical for organizations debating centralized versus decentralized IAM approaches, especially those needing tighter oversight without slowing down operations.
Self-Service App Catalog
CloudEagle strikes a balance between control and autonomy with its self-service app catalog.
- Employees can request access to apps directly through Slack.
- Admins receive real-time notifications via Slack or email.
- The platform flags duplicate app requests and suggests available alternatives.

This reduces procurement redundancy and supports decentralized vs centralized access workflows by giving end users more autonomy, while keeping IT in the loop.
Automated App Access Reviews
When it comes to compliance and audit readiness, CloudEagle helps eliminate manual access reviews:
- Automates SOC 2 and ISO 27001 access audits.
- Centralizes all access review tools in one dashboard.
- Provides instant deprovisioning logs when needed.
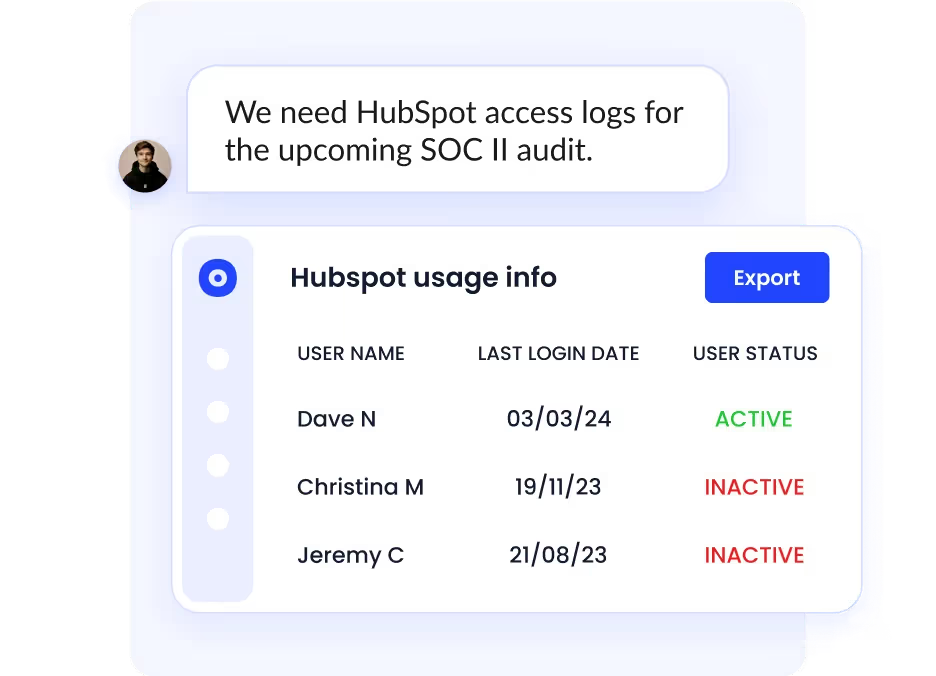
These features support centralized vs decentralized risk management by ensuring every access decision is verifiable, trackable, and compliant.
Time-Based Access Management
Temporary users? No problem.
CloudEagle’s time-based access capabilities help secure sensitive systems:
- Grant access to contractors, freelancers, or internal users for a fixed duration.
- Automatically revoke access after task completion.
- Customize access by user type and department.
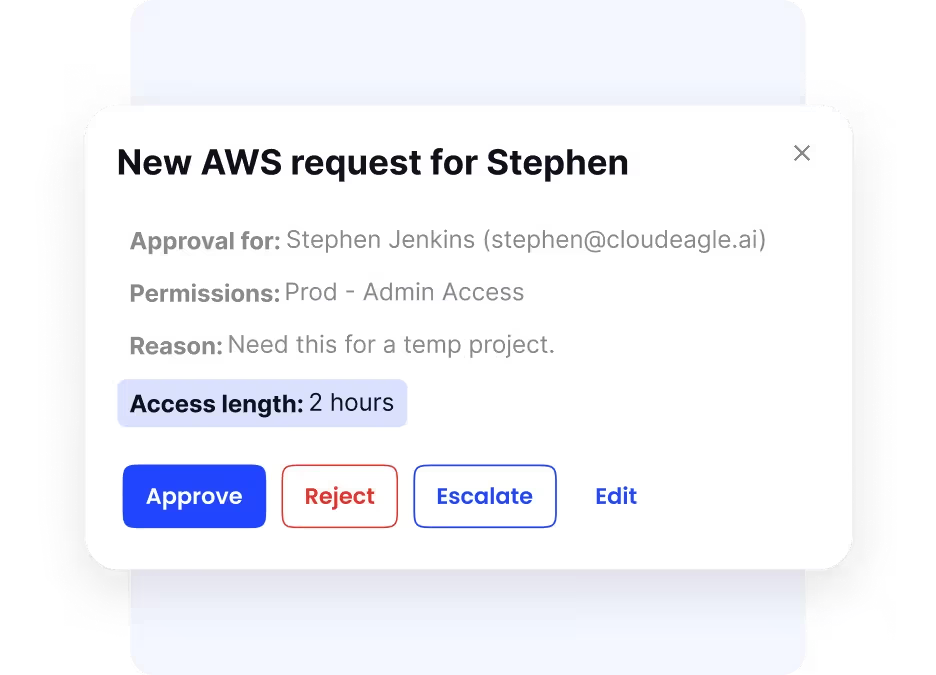
This reduces the risk of standing access and aligns with centralized vs decentralized cybersecurity strategies, where flexibility must meet control.
Seamless Access Control
Manual onboarding and offboarding often lead to delays or security gaps. CloudEagle automates this with:
- Zero-touch onboarding (SCIM and non-SCIM).
- Just-In-Time (JIT) access for role-based permissions.
- Automated triggers to instantly revoke access when employees leave.
For fast-scaling organizations, CloudEagle offers centralized access control that minimizes administrative overhead while strengthening identity and access security.
Privileged Access Management (PAM)
Sensitive systems demand strict controls, and CloudEagle delivers.
- Automates the assignment of privileged roles (e.g., AWS, NetSuite).
- Continuously monitors high-risk accounts.
- Reduces unauthorized usage and human error.
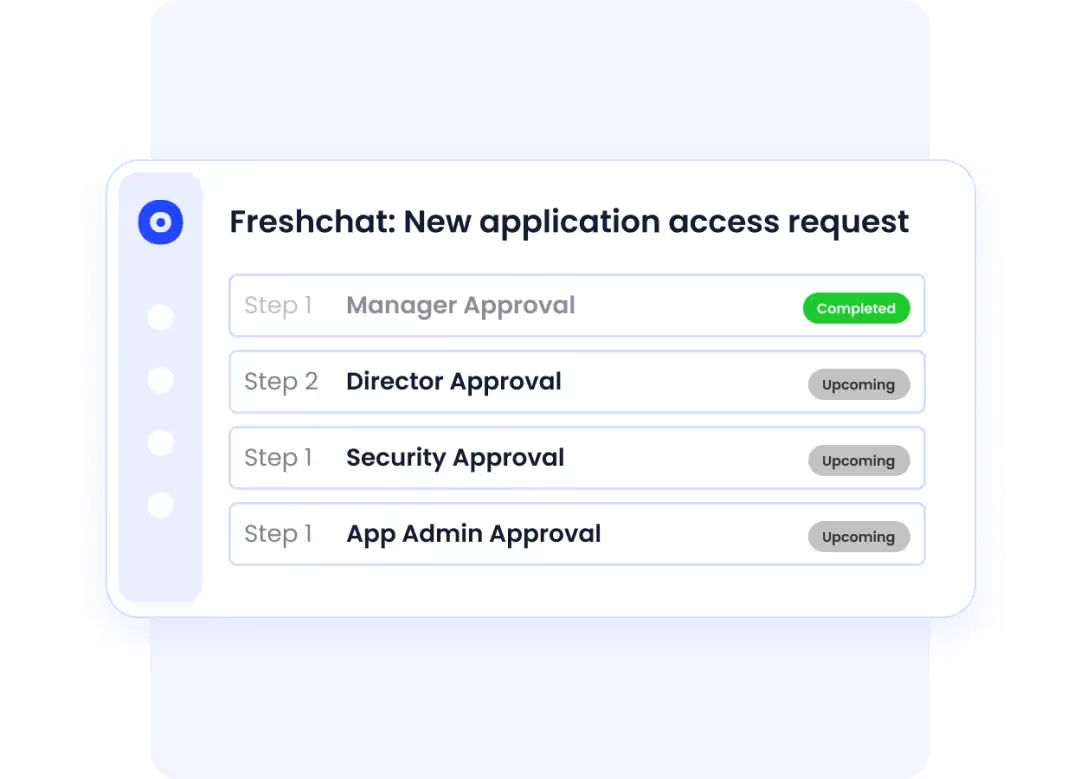
For organizations weighing centralized vs decentralized cybersecurity models, CloudEagle supports a centralized privileged access approach while retaining the flexibility to enable agile, role-specific access when needed.
Streamlined Onboarding and Offboarding
Efficiency isn’t just about automation; it’s about precise timing and control. CloudEagle ensures secure and accurate onboarding and offboarding with:
- Assign access based on department, role, or seniority.
- Auto-revoke access for inactive accounts.
- Ensure no user has lingering permissions.
The platform also offers robust automated user offboarding, reducing the security risks tied to manual access revocation.
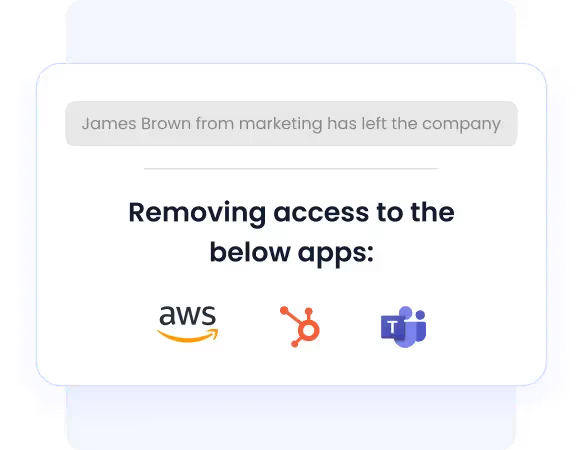
For example, Remediant used CloudEagle.ai to implement smooth automated user provisioning and deprovisioning, boosting their operational efficiency.
Conclusion
The centralized vs decentralized access model debate isn’t about choosing a winner; it’s about aligning your strategy with your business structure, risks, and compliance needs.
While centralized models offer control and oversight, decentralized ones enable speed and autonomy. Many organizations adopt a hybrid approach to achieve both security and flexibility.
CloudEagle.ai simplifies access management with centralized visibility, automated workflows, and seamless app integrations. It empowers you to balance security and agility while reducing manual effort across the user lifecycle.=
Book a free demo today to see how CloudEagle.ai can modernize your access management strategy.
Frequently Asked Questions
- What are the 4 types of access control?
The four main types are: Discretionary Access Control (DAC), Mandatory Access Control (MAC), Role-Based Access Control (RBAC), and Attribute-Based Access Control (ABAC). - What is decentralized key control?
Decentralized key control distributes cryptographic key management across multiple systems or users, reducing single points of failure and improving resilience and privacy. - What is decentralized control?
Decentralized control refers to distributing decision-making authority across departments or teams, enabling local autonomy while reducing dependency on a central authority. - What is centralized access control?
Centralized access control is a system that manages user permissions from a single platform, ensuring consistent, secure access to apps and data across an organization. - What is meant by access management?
Access management refers to the process of controlling who can access specific systems, applications, or data, ensuring the right users have the right access at the right time.

%201.svg)







.avif)




.avif)
.avif)




.png)









