Prevent SaaS Security Risks with AI-powered Governance
Trusted by CIOs and CISOs To Secure Their SaaS Ecosystem


%20(1).avif)
%201.svg)

.svg)
.svg)
The SaaS Security Platform Built for Modern Threats
Govern, Audit, and Secure SaaS From a Single Dashboard
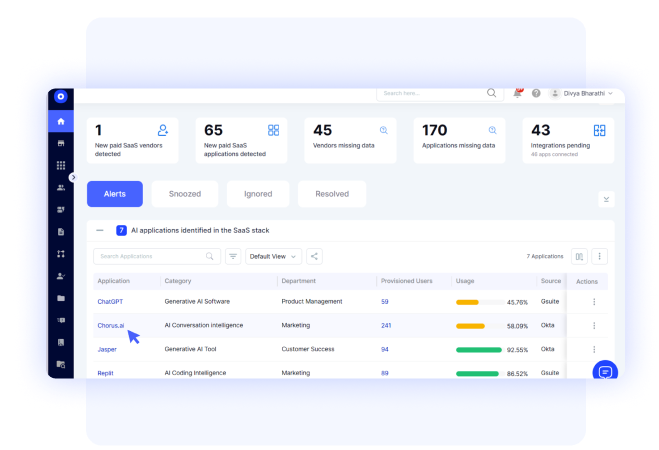
Shadow AI/IT & Risk Management

- Detect unsanctioned apps through SSO logs, browser activity, expense data, and HRIS events
- Flag high-risk AI tools like ChatGPT, Midjourney, DeepSeek, and 1,000+ others automatically
- Reduce duplicate applications that increase cost and weaken SaaS security posture management
- Rationalize unauthorized apps and save on spend.
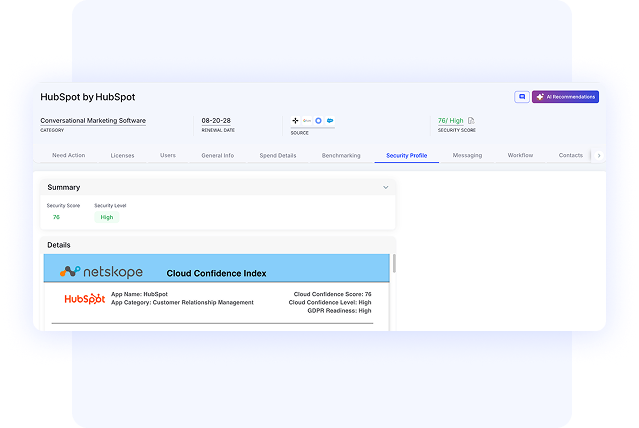
End-to-End Identity & Access Management

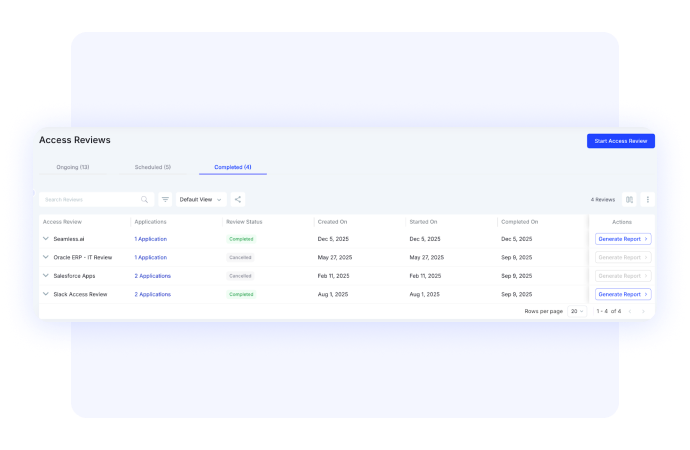
- AI-powered access reviews that run continuously, not quarterly
- Risk-based user scoring that flags risky apps and identities instantly
- Detect access anomalies using behavioral pattern analysis
- Handle apps outside your identity provider, the ones your IAM solutions miss
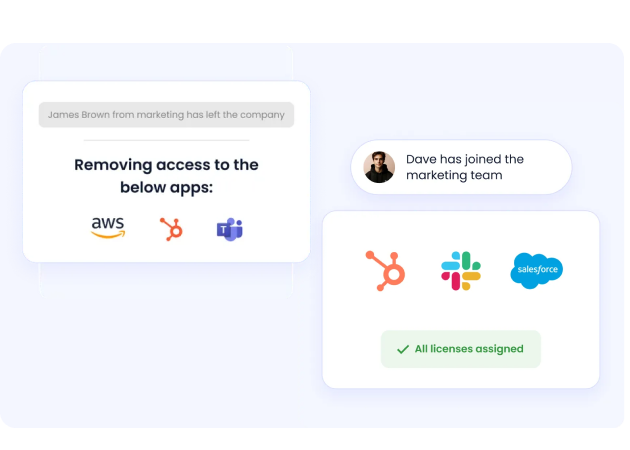
Zero-Touch JML Automation

- Auto-pilot all Joiner, Mover, and Leaver events based on role, department, location, and custom attributes
- Auto-remove access across all apps, even those not connected to Okta or SailPoint
- Reclaim licenses the moment users exit, recovering costs immediately
- Just-in-time privileged access for temporary elevated permissions
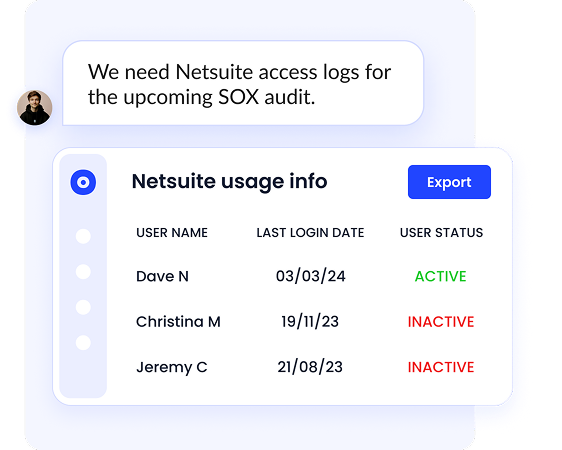
Continuous Compliance & Audit Intelligence

- One-click audit exports with timestamped evidence of every access decision
- Track vendor SOC 2 compliance across your entire SaaS vendor portfolio
- AI-extracted contract metadata monitors security clauses, DPAs, and data retention
- Support for multiple frameworks: SOC 2, ISO 27001, SOX, HIPAA, GDPR
Automated Access Reviews & Secure Privileges

- Automated access reviews across 500+ SaaS connectors
- Behavior-based insights to flag unusual permission usage
- Privilege creep alerts when users retain unnecessary access
- Auto-adjust privileges based on real usage patterns
Frequently Asked Questions
We use multiple detection methods simultaneously, including SSO logs, browser extensions, expense tracking, corporate card data, and HRIS integrations. This multi-signal approach enables stronger SaaS security monitoring and protects against unmanaged AI and SaaS usage. It identifies the AI tools, free trials, and personal accounts your employees use to get work done. If there is a SaaS app in your environment, we find it.
CloudEagle is designed to work alongside your IAM tools like Okta or SailPoint, dramatically extending their capabilities. We cover the SaaS apps and shadow IT your IAM can't reach, automate the governance processes your IAM makes manual, and provide the compliance reporting your IAM doesn't offer. Think of us as the comprehensive layer that makes your existing investments actually work.
Most organizations are operational within days. Our 500+ native connectors mean no custom development, no long implementation cycles, and no disruption to your team. You'll start seeing shadow IT and access risks within hours of connecting. Full automation of provisioning, access reviews, and compliance workflows typically happens within the first week.
CloudEagle generates audit-ready documentation for SOC 2 Type I & II, ISO 27001, HIPAA, SOX, GDPR, and CCPA. Every access decision, provisioning event, and security change is logged with timestamps and approval chains. Auditors get exactly what they need, and your team stops spending weeks preparing evidence.
This is one of our core differentiators. CloudEagle maintains direct connections to applications through API integrations, not just through your identity provider. When someone leaves, we revoke access across all apps, including the shadow IT tools, the standalone systems, and the apps your IT team never knew existed. Thus strengthening SaaS cyber security and SaaS network security.
Yes. Whether you're a 200-person startup or a 10,000-employee enterprise, CloudEagle scales to your needs. Our platform handles everything from basic shadow IT discovery for smaller teams to complex, multi-region, multi-framework compliance for global enterprises. The architecture is built to scale without complexity.
Our AI analyzes behavioral patterns, usage data, access history, and risk signals to make intelligent security decisions. It learns from your organization's patterns to detect anomalies, predict privilege creep, optimize provisioning rules, and prioritize security risks. The result is automation that gets smarter over time, not just rule-based workflows that need constant tuning.
CloudEagle has 500+ native connectors and a flexible API architecture. We integrate with your SSO providers, HRIS systems, ITSM tools, SIEM platforms, cloud infrastructure, and business applications. Data flows bidirectionally so CloudEagle can both consume signals and trigger actions across your entire security ecosystem. If you use it, we probably connect to it.
Your SaaS Stack Isn't Getting Simpler. So Upgrade Your Security






